This is the third part of the blog series on cyber security, continuing from its second part on mobile security, focussing on the malware type that utilizes a user’s fear of data loss to extort monetary benefits, and a few precautionary steps to follow to avoid being a victim of this type of malware.
Scareware
In the modern day most malware are written for monetary gain. Scareware is a generic term to describe a category of malware which use the strong emotion of fear to force alarmed victims of an attack to pay an amount of money, typically tens to hundreds of US Dollars, to the attacker to restore normality on their computer/device.
Examples of scareware include malware which:
- display fake messages to the user about virus infections or system errors on the computer for which the fixing solution requires payment of a sum of money
- lock-down or claim to have locked-down access to some aspects of computer functionality such as use of the screen or personal documents, for which regaining access involves payment of a sum of money
Scareware typically infect users’ computers through downloading malicious attachments or clicking links in spam, or through accidentally visiting hacked websites.
As always it is important to ensure that you:
- Do not open emails from strangers, including fake messages from well-known companies such as FedEx or DHL
- Keep your operating system and third-party software, e.g. browsers and document readers, completely up-to-date with security updates. Avoid pirated software
- Use top-rate, genuine, up-to-date Anti-Virus software such as K7 Internet Security with strong Internet Security features such as malicious spam blocking, malicious website-blocking and browser-exploit protection
Scareware can affect both PCs (typically with a Windows operating system) as well as mobile devices (typically with an Android operating system which can be protected by K7 Mobile Security).
Rogue AV
Rogue AV or Fake AV is a subset of the scareware category of malware. Rogue AV pretends to be a legitimate Anti-Virus program which proceeds to display fake warnings of numerous virus infections on the computer. The fake warning window may steal the computer’s focus and then remain persistent with the malware preventing attempts to close it. Users are made to believe that only if they fork out a sizeable sum of money would the virus infections be cleaned up and the computer restored to a good state.
The fake warning window may steal the computer’s focus and then remain persistent with the malware preventing attempts to close it. Users are made to believe that only if they fork out a sizeable sum of money would the virus infections be cleaned up and the computer restored to a good state.
Historically Rogue AV has been associated with the use of Search Engine Optimization (SEO) poisoning which ensured that hacked websites controlled by the attackers ranked highly when trending topics were searched for in a web search engine such as Google. When the user clicked on one of these attacker-controlled links the user’s computer would get infected. Rogue AV is most commonly found on Windows PCs, but has also been known to infect MacOS computers.
Ransomware
Ransomware is a type of malware, becoming more common by the day, which denies access to your computer resources until a hefty sum is paid to the criminal gang which caused the infection.
The typical resources held to ransom are as follows:
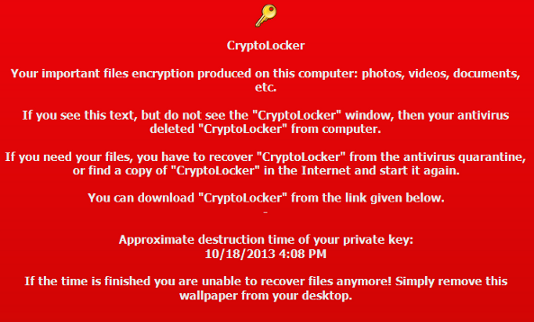
- Personal documents, images, and other files – In this case the files are encrypted so that they become unusable. After the files are encrypted the ransomware displays a splash screen informing the victim of this action and demanding a ransom payment to restore the files. Recovering these files requires obtaining the decryption key from the malware syndicates for a fee amounting to hundreds of US Dollars. Payment is made through guaranteed anonymous channels such as the BitCoin network. The first major ransomware family of this type was called Cryptolocker.
- Device screen – In this case the screen is frozen by the malware with a ransom demand visible. The user is allowed to make the payment to unlock the screen. One prevalent family of ransomware which locks the screen is called Reveton.
Users are advised to avoid paying this type of ransom demand for the following reasons:
- Generating income for cyber crooks would only serve to incentivise their criminal activities, and would fuel their future attacks
- There is absolutely no guarantee that paying up the ransom of potentially hundreds of dollars would actually restore your files or unlock your screen
In addition to the recommendations above, to guard against Scareware in general, it is also important to ensure that you back up your important files in a disciplined fashion on external media and/or on online repositories. If you are not in the habit of backing up your files, this practice is highly recommended since data loss from a failed hard disk at a future date is a probable event, far likely than a ransomware infection.
Happy New Year!
…to part4: Passwords – Hashes to Ashes
Images courtesy of:
Adeevee.com
Huffingtonpost.com
Cloudave.com
K7 Threat Control Lab
If you wish to subscribe to our blog, please add the URL provided below to your blog reader: https://labs.k7computing.com/feed/