The sensational, massive theft of critical data from Indian debit card holders, and the subsequent abuse of card data in China and USA, have been widely reported in the Indian media.
Unfortunately the information available seems to be largely based on hearsay and conjecture, some of it even contradictory. The following Donald Rumsfeld (ex-United States Secretary of Defense) quote from February, 2012 comes to mind:
“Reports that say that something <redacted for effect> happened are always interesting to me, because as we know, there are known knowns; there are things we know we know. We also know there are known unknowns; that is to say we know there are some things we do not know. But there are also unknown unknowns – the ones we don’t know we don’t know.”
We may use the above quote to analyse the facts or lack thereof:
- Known knowns – The critical details of lots of cards (32 lakh may be a paranoid extrapolation of the real figures) have been potentially compromised, many of which have been abused in China and USA
- Known unknowns – How exactly was the data stolen? Was there really ATM malware or some skimming device? Or was there a breach on the backend ATM infrastructure either via malware or via direct database hacking? How was the stolen data relayed back to the cyber criminals?
- Unknown unknowns – Given the nature of this breach, what other parts of the ATM and banking networked infrastructure are vulnerable to attack? What will those scary headlines read in the future?
We are still in the hunt for real technical detail relevant to this particular breach. Malware samples or hashes would be very useful.
ATM and Point of Sale (PoS) malware are not a recent phenomenon. ATMs can be considered to be computers with some customised hardware, e.g. card reader, attached. They tend to:
- run Windows XP as the OS hosting the ATM services
- have no Anti-Virus software installed
- perhaps employ inadequate encryption mechanisms to prevent the leakage of transaction data
Obviously these factors are not conducive to the maintenance of data security on ATM networks. Windows XP is known to be vulnerable and has been unsupported by Microsoft since 2014! Regardless of the true nature of the current breach it seems clear that the banking industry does need to take ATM security more seriously than employing security guards outside terminals who may doze, if even present, or worse. A good place to start would be to address the vulnerabilities highlighted above, i.e.:
- Upgrade the host OS to a more secure, light-weight one, and ensure that it is adequately patched
- Install customised Anti-Virus software with slim, relevant security updates
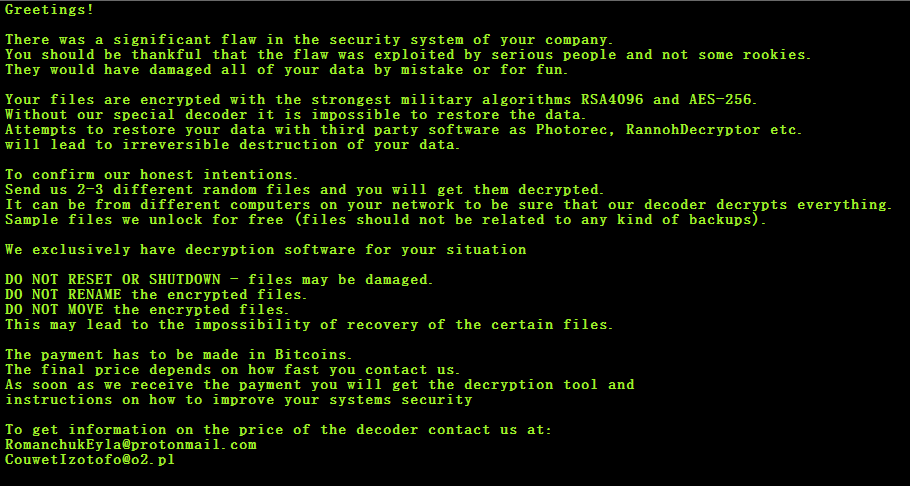
- Employ industry-standard encryption (AES/RSA/ECDH, etc.) across critical data transfer channels and storage areas
- Get the whole infrastructure vetted by competent third-party agencies through black-box (vulnerability assessment, pen testing, etc.), and white-box (code review) mechanisms
We shall keenly monitor developments in this case, especially if samples are forthcoming.
Image by Karl Hilzinger courtesy of:
http://www.smh.com.au/it-pro/security-it/credit-card-fraud-8-ways-your-details-can-be-hijacked-20150119-12ttwn.html
Samir Mody
AVP, K7TCL