WannaCry ransomware, a security disaster has already infected thousands of computers all over the world, especially in Russia, India and China, and has hit emergency services in various countries, e.g. the UK. There have been images of infected ATMs, gigantic billboards, etc., making this attack a high-profile event.
This attack is a macabre reminder of the ill effects of
- exploiting a critical vulnerability in the Windows OS
- using a pirated version of an operating system
- leaving computer unpatched and connected to the internet, in other words highly vulnerable
In most of the attack scenarios tracked, WannaCry ransomware infects a computer by using the “EternalBlue” exploit (developed by the NSA and released to the public by Shadowbrokers in April 2017), which exploits a critical vulnerability in Microsoft SMBv1 server (CVE-2017-0143 to CVE-2017-0148) by sending a specially-crafted packet. There was a Microsoft patch MS17-010 available to fix this vulnerability released in March 2017. It is also alleged, although without any concrete evidence, that this malware may enter a computer by the common email-borne route.
Please note that K7 security products contains heuristic anti-ransomware functionality which is capable of stopping WannaCry in its tracks without any signatures updates (please read the Virus Bulletin blog which includes a video of K7’s talk from 2015 about fighting back against ransomware). However to ensure stopping all variants of the ransomware before any encryption starts, we at K7 Threat Control Lab have taken the necessary steps to block it at all of its possible execution points. Users of K7 Security products are protected against this ransomware and the detection names at the time of writing are as follows:
Trojan (0050db011)
Trojan (0050d8371)
Trojan (0050d7201)
In addition, K7 blocks this multi-component malware with the behavioral detection as
Suspicious Program ( ID21236 )
Suspicious Program ( ID21237 )
Suspicious Program ( ID21238 )
Before we look at the technical details of this malware and explore how it works we must urge users to apply the latest Windows patches which Microsoft has made available even for the unsupported Windows XP, and may be applicable on pirated versions of Windows too (note, using pirated software is an extremely bad idea). In order to better protect the computer against being exploited from an external source, blocking in-bound connections on TCP ports 139 and 445 and UDP ports 137 and 138 might be an option to carefully consider. The client firewall in K7 Security Products can be configured to restrict traffic as described on the mentioned ports.
In addition there has been some misinformation aggressively disseminated on social media and the news that using a certain password which is embedded in the code can be used to decrypt the encrypted data. This is far from the truth. WannaCry uses the embedded password to decrypt its internal embedded ZIP containing ransomware components. Users are strongly advised to ignore any mention about this password and avoid being influenced by a whole lot of scaremongering junk information being released irresponsibly. There is currently no way to retrieve all the encrypted data barring use of the cyber criminals’ own decryption service at a cost of US$300-US$600.
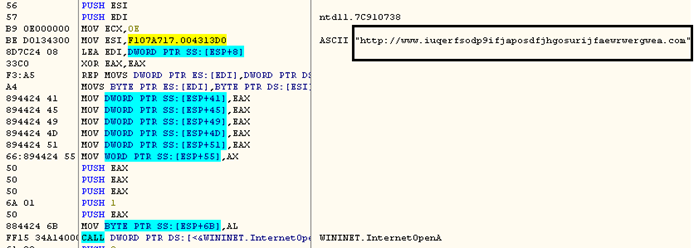
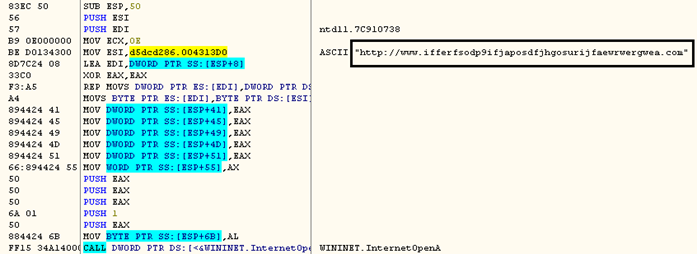
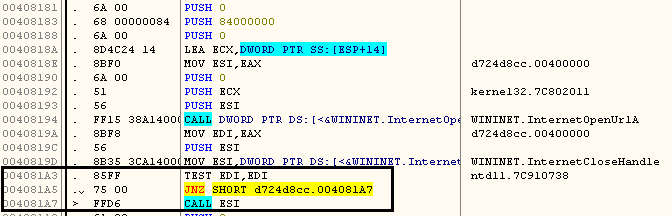
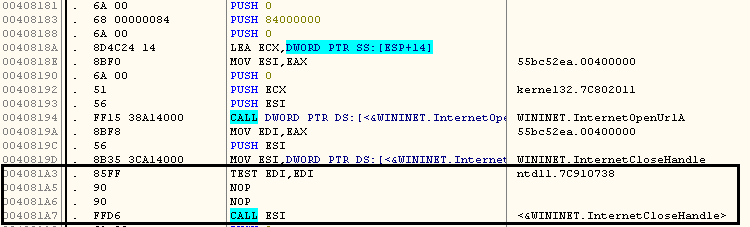
WannaCry involves multiple executable files to infect an end user. The main dropper EXE accesses the URL as shown in the images below,
This URL is now known as the “kill switch” since if it is accessible the dropper stops execution. Such a “kill switch” is unprecedented in the history of ubiquitous run-of-the-mill ransomware and raises interesting questions about the true purpose of the attack. Interestingly the above domain has now been registered by researchers, thus stopping the attack at the dropper stage in many situations. There are few recent samples which ignores whether or not the URL connection is successful.
MD5: d724d8cc6420f06e8a48752f0da11c66
MD5: E8089341EE0442A2ECF82E4B70829143
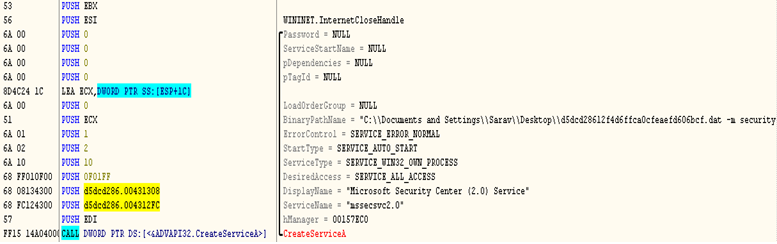
Anyway, let’s assume the executable proceeds with its malicious behavior. The dropper EXE starts itself as a service with the security parameters as “-m security”, service name “mssecsvc2.0” and display name as “Microsoft Security Center (2.0) service”
Then it tries to load the payload executable which it carries within itself under the resource named “R” in the sample which we analyzed (d5dcd28612f4d6ffca0cfeaefd606bcf).
In any PE parsing tool, it shows that the resource contains an embedded PE
It extracts the file with the name “tasksche.exe” under the directory called “windows\<randomname>” as shown below. Note, we have also seen occurrences of this file being dropped under “ProgramData\<randomname>.”
After which the dropper starts the payload “tasksche.exe” using CreateProcessA. The payload tasksche.exe (84C82835A5D21BBCF75A61706D8AB549) contains the required functionality for encrypting data on the computer, and the files to display the ransom notes, etc. It carries within itself a password-protected ZIP in .resource section, as mentioned earlier. Interestingly, the password for the ZIP is plain text and not encrypted.
Upon further research we found that even though the password is in plain text, the password keeps changing. Sample 4da1f312a214c07143abeeafb695d904 uses the password “wcry@123”.
Unzipping the password-protected ZIP drops the following files in the desktop directory,
Folder “msg” contains the rtf files with extension .wnry for different languages.
Here are the details of the other files that are unzipped:
1. b.wnry – BMP image file (desktop background mentioning the decryptor tool @WanaDecryptor@.exe to receive ransom payment)
2. c.wnry – contains Tor browser download link
3. r.wnry – Text Message
4. s.wnry – ZIP file with has tor.exe along with its dependent DLLs
5. t.wnry – Encrypted data which then decrypts itself in memory (it’s a DLL file)
6. u.wnry
7. taskdl.exe
8. taskse.exe
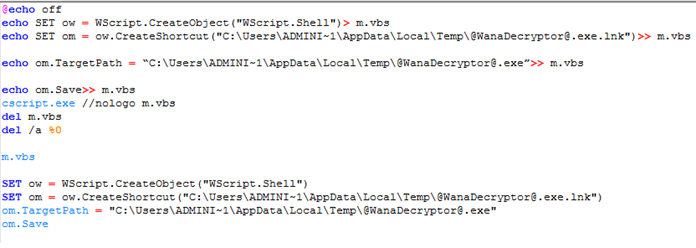
It also unzips a batch file that writes a VBScript file m.vbs, that points to an LNK file to run “@WanaDecryptor@.exe” a shown below,
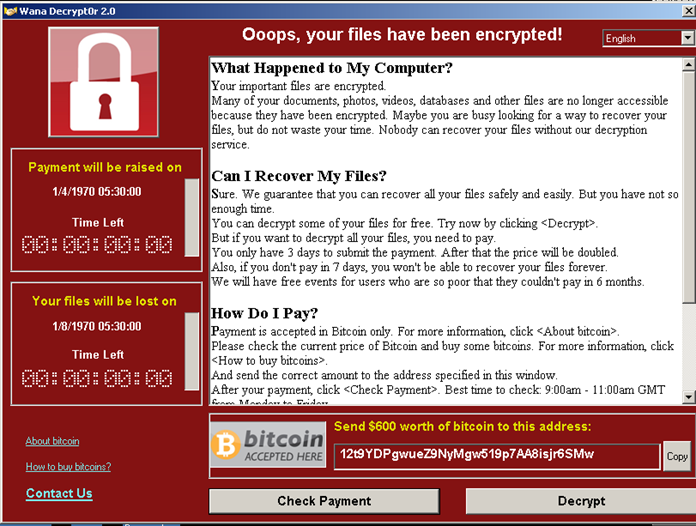
This @WanaDecryptor@.exe, once run, calls taskdl.exe and displays the below screen to the user,
It also copies itself to other locations like
C:\ProgramData\<randomfolder>\@WanaDecryptor@.exe
The following file extensions are susceptible to encryption:
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .ott, .sxw, .stw, .uot, .3ds, .max, .3dm, .ods, .ots, .sxc, .stc, .dif, .slk, .wb2, .odp, .otp, .sxd, .std, .uop, .odg, .otg, .sxm, .mml, .lay, .lay6, .asc, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .dbf, .odb, .frm, .myd, .myi, .ibd, .mdf, .ldf, .sln, .suo, .cpp, .pas, .asm, .cmd, .bat, .ps1, .vbs, .dip, .dch, .sch, .brd, .jsp, .php, .asp, .java, .jar, .class, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .3gp, .mkv, .3g2, .flv, .wma, .mid, .m3u, .m4u, .djvu, .svg, .psd, .nef, .tiff, .tif, .cgm, .raw, .gif, .png, .bmp, .jpg, .jpeg, .vcd, .iso, .backup, .zip, .rar, .tgz, .tar, .bak, .tbk, .bz2, .PAQ, .ARC, .aes, .gpg, .vmx, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .602, .hwp, .snt, .onetoc2, .dwg, .pdf, .wk1, .wks, .123, .rtf, .csv, .txt, .vsdx, .vsd, .edb, .eml, .msg, .ost, .pst, .potm, .potx, .ppam, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotx, .dotm, .dot, .docm, .docb, .docx, .doc
Encrypted files would have extension .wncry appended to the user file name, e.g. if the file name is user_pic.jpg, after encryption it would be user_pic.jpg.wncry. The bytes of encrypted file at offset zero would be ‘0x57 0x41 0x4E 0x41 0x43 0x52 0x59 0x21’ (ASCII “WANACRY!”)
In all the folder locations in which encryption occurs there also two additional files dropped:
@WanaDecryptor@.exe.lnk which points to @WanaDecryptor@.exe and @Please_Read_Me@.txt, which contains the ransom note.
As with all ransomware, and to guard against data loss in general, it is important to maintain regular backups of critical data to be able to retrieve it in the case of file or disk corruption.
What is in store for the world now with respect to WannaCry? Are we going to see a different infection strategy, will the binaries be custom-packed, will strings be encrypted? Or will the attack lie low for a while? We’ll be monitoring the twists and turns in the WannaCry saga over time, and will publish new information as and when required.
K7 Threat Control Lab