K7 Labs was established in 1998 to accelerate the process of cyberthreat discovery and reduce the window of opportunity for cyberattacks. The state-of-the-art research facility analyses hundreds of thousands of threat samples every day and distributes threat definition updates multiple times a day to ensure all K7 users are protected against the latest threats, and provides the K7 Threat Intel Feed Service that powers threat detection in Security Operations Centres (SOCs), and Security Information and Event Management (SIEM) and Network Security solutions.
K7 Labs is the first discoverer of several malware and is the first winner of the Real Time Threat List Contributor of the Year award from the Anti-Malware Testing Standards Organization (AMTSO).
Ecosystem Threat Intelligence
At the heart of all K7 Security solutions is K7 Labs’ Ecosystem Threat Intelligence (K7ETI) which ensures that all K7 solutions utilise the best telemetric data about an adversary’s capabilities and tactics, enabling the proactive prevention of cyberattacks.
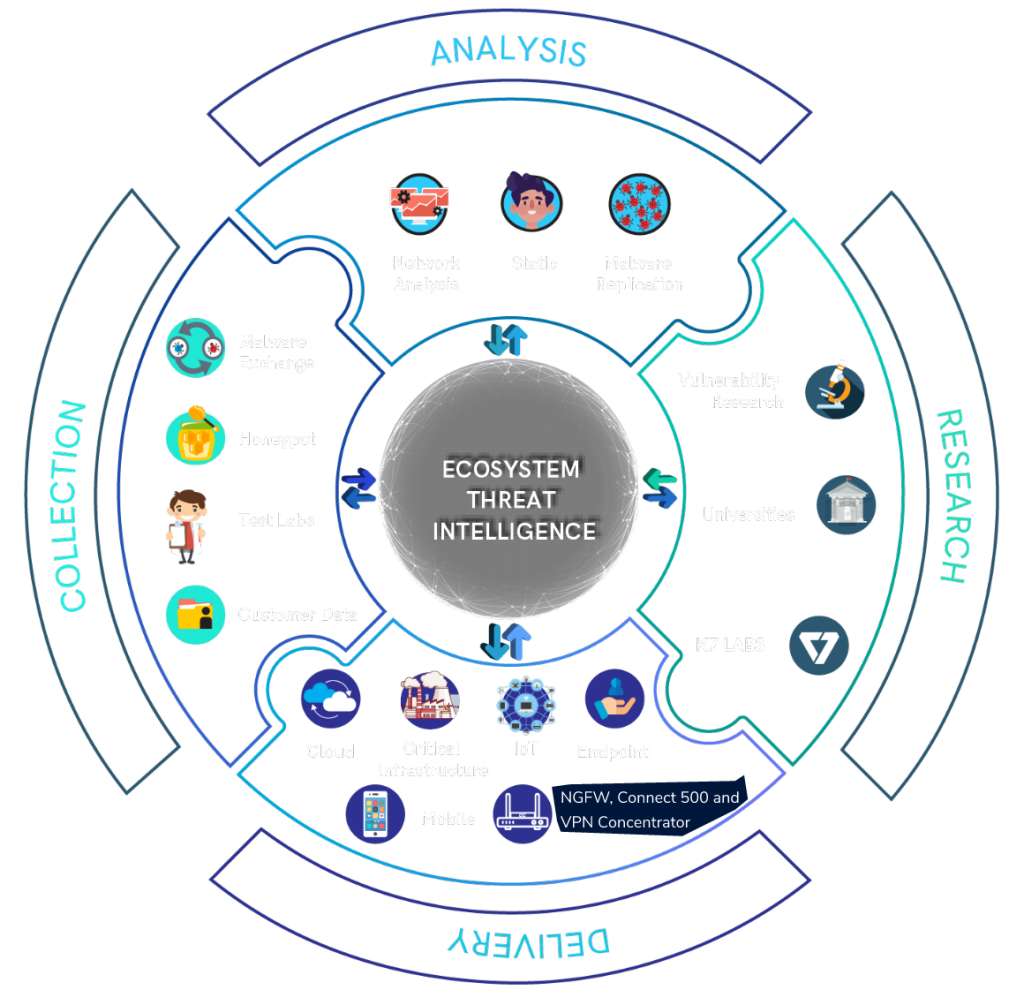

Enables prevention, detection, and mitigation
of future cyberthreats and attacks

Aggregates threat-related metadata from globally distributed
sources, including live threat event telemetry via
K7 Security solutions and honeypot networks

Identifies outbreaks and fast-moving
infections aiding security researchers in
developing automated security responses

Proactively identifies and remediates potential false
positives using intelligent automation, reducing the
misclassification of legitimate objects as malware
Threat Research
K7 Labs’ researchers regularly speak and present at leading global threat research conferences such as Virus Bulletin, CARO, AMTSO, AVAR, and the International Anti-virus conference, among others.
Publications

Cyber Threat Monitor Report

Research Blogs

Vulnerability Information

Top Threats

