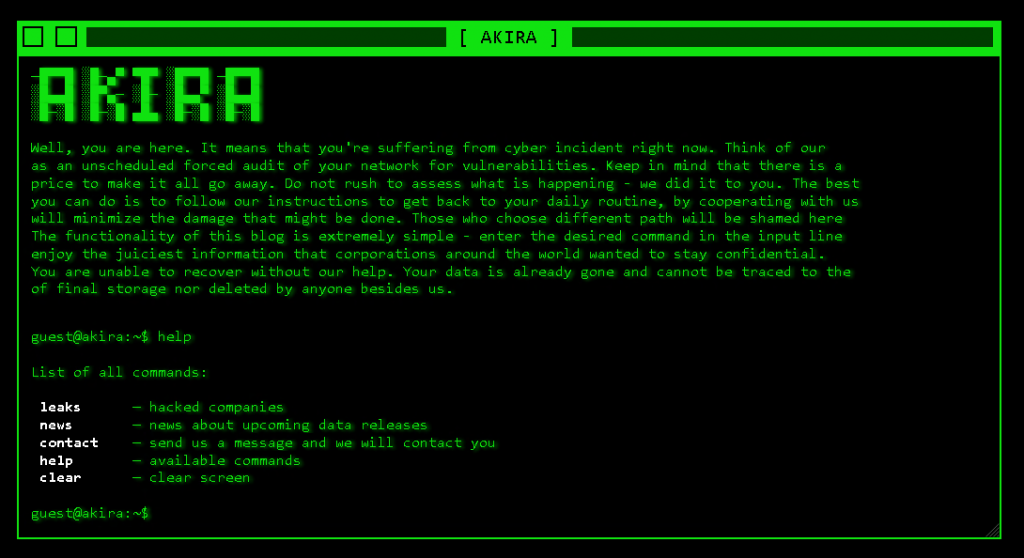
Ransomware attacks have become a serious concern for individuals and organisations alike, and the threat is only growing with the rise of Ransomware-as-a-Service and openly available leaked source code of popular ransomwares. With more threat actors adopting this strategy, it’s important to understand the Tactics, Techniques, and Procedures (TTPs) used by these ransomware affiliates.
Recently we have observed a new emerging ransomware named Akira. It is believed that the ransomware group started their campaign in late March of 2023 and within a short time period they already infected more than 16 organisations worldwide. The ransomware group also have their own retro styled Tor website where they publicly expose stolen data if the victim doesn’t pay the ransom. They also have a chat feature on their website to let the victims communicate with them using the unique ID from the ransom note. In this blog, we’ll delve into the recent Akira ransomware attack and how it is related to Conti ransomware.
Initial Access
Ransomware operators have been known to target vulnerable systems and exploit security weaknesses to gain initial access. They commonly use tactics such as phishing emails, Remote Desktop Protocol (RDP) exploitation, and software vulnerabilities to infiltrate systems and launch their attacks. However, as security measures improve, we have observed that ransomware operators are also employing other methods to gain access, such as brute-forcing poorly managed MsSQL servers.
In the case of Akira ransomware it was found by researchers that the ransomware operators primarily exploited poorly configured Remote Desktop Protocol (RDP) connections that were exposed to the internet with MFA bypass and weak passwords.
Dwell Time (Network discovery, Installing tools, Persistence)
The attackers created Windows services to dump the memory from lsass.exe for credential stealing and created scheduled tasks to perform remote directory listing.
It is noted that attackers are also using tools like AdvancedIP Scanner to find all the systems connected in the network and access it by installing another remote access tool, Radmin. They have also used PChunter to find all the running processes.
For evasion they added a registry to bypass real time scanning in Windows Defender HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths\C:\ and used the following path C:\programdata to run most of their tools and the final ransomware.
It has been observed that most of the ransomware gangs will install spyware, rootkits and coin miners and run it for some days in the infiltrated system before infecting the system with ransomware but Akira threat actors are only focused on infecting a large number of systems in the infrastructure.
For exfiltration of data the threat actors use tunnelling softwares like chisel, cloudflare free tunnel to bypass the firewall and mask their IP.
For persistence the threat actors usually install tools like cobalt strike, Meterpreter but the Akira threat actors utilised the famous remote access tool AnyDesk by installing it in multiple systems
Ransomware Analysis
We got our hands into multiple samples obtained from VT all of them were compiled using visual C++ as console applications in 64 bit Architecture.
All the samples we analysed had a different Public RSA key and Unique ID (created by the attacker to let the victim to communicate with the ransomware gang) hardcoded in its data section.
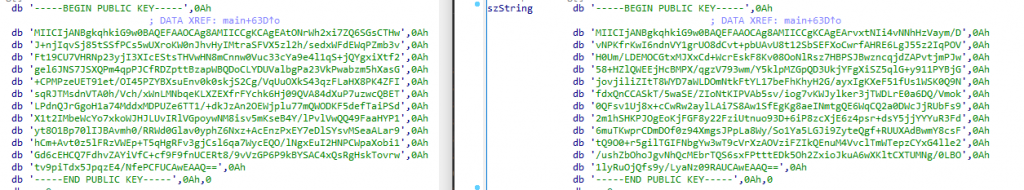
It seems like the ransomware operator builds the ransomware on the go with a new public RSA key to infect each of its victims where a Unique ID is also generated and appended in the ransomware note, this unique ID will help the attacker to check which ransomware build had infected the customer and which private key will be needed to decrypt the files.
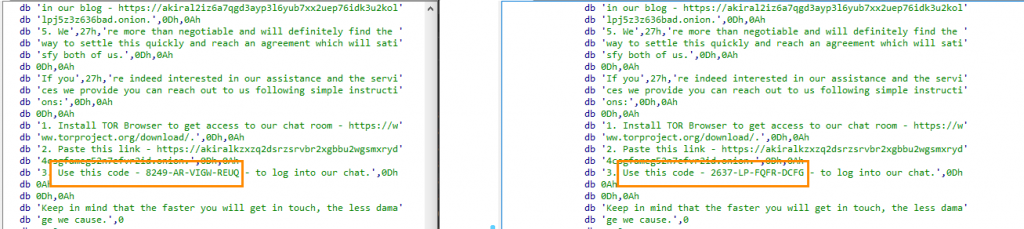
The ransomware had three functions related to string operations which were declared as Static functions. Whenever a program is executed, these functions will be called automatically by the ‘initterm’ API which is a C Runtime library function that is responsible for calling the resources of the global and static objects before the program’s main function is executed.
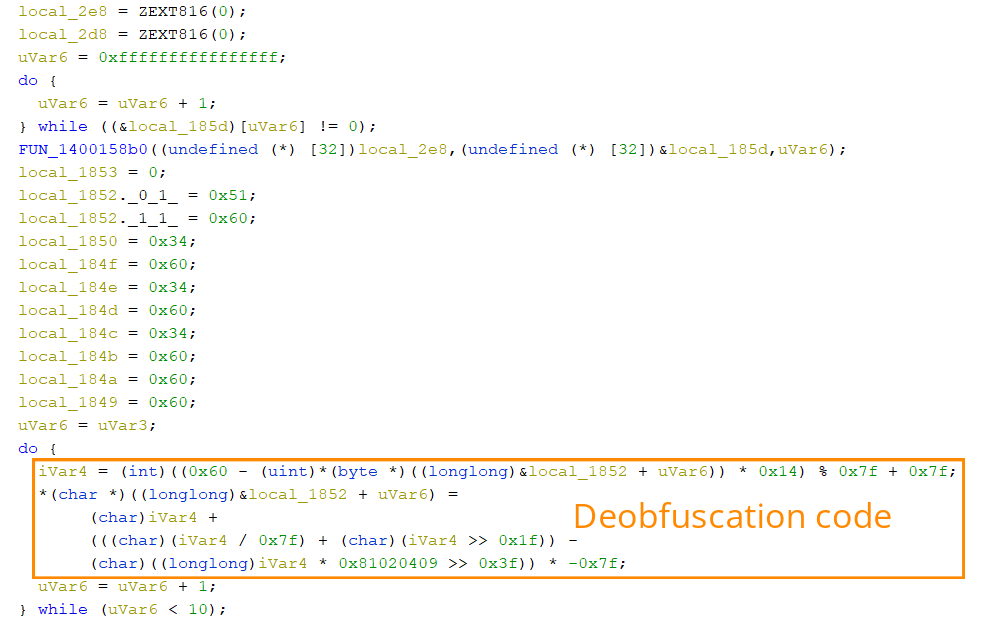
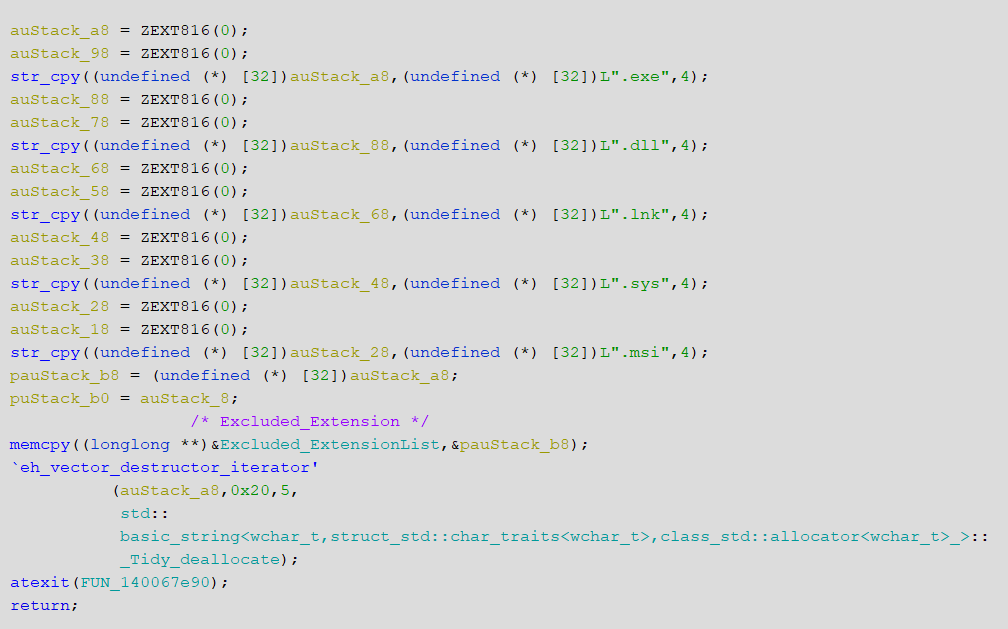
These static functions are responsible for deobfuscating strings in the stack. The first function will populate all the file extensions that need to be encrypted, the second one will populate all the system related process names that need to be whitelisted from getting killed, the third one will populate all the virtual harddisk extensions that need to be encrypted.
We did find all these strings in the rdata section as well, but they were never referred or used in the runtime suggesting that the attacker who copied the leaked code unknowingly created it.
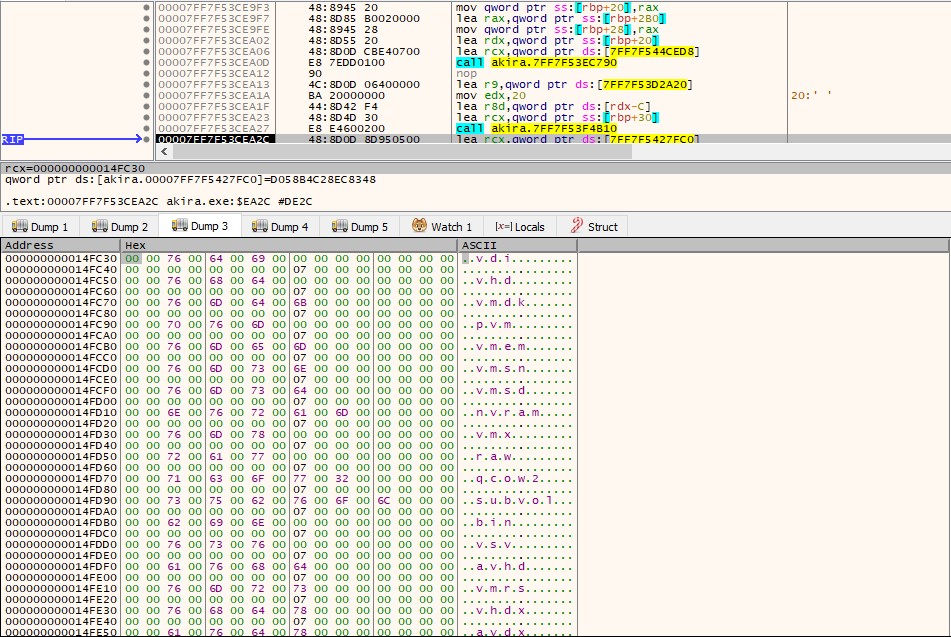
Targeted File Extensions:
.4dd, .accdb, .4dl, .accde, .accdc, .accdt, .accdr, .adb, .accft, .adf, .ade, .arc, .adp, .alf, .ora, .btr, .ask, .cat, .bdf, .ckp, .cdb, .cpd, .cma, .dad, .dacpac, .daschema, .dadiagrams, .db-shm, .db, .db3, .db-wal, .dbf, .dbc, .dbt, .dbs, .dbx, .dbv, .dct, .dcb, .ddl, .dcx, .dp1, .dlis, .dsk, .dqy, .dtsx, .dsn, .eco, .dxl, .edb, .ecx, .exb, .epim, .fdb, .fcd, .fmp, .fic, .fmpsl, .fmp12, .fp3, .fol, .fp5, .fp4, .fpt, .fp7, .gdb, .frm, .gwi, .grdb, .his, .hdb, .idb, .ib, .itdb, .ihx, .jet, .itw, .kdb, .jtx, .kexic, .kexi, .lgc, .kexis, .maf, .lwx, .mar, .maq, .mav, .mas, .mdf, .mdb, .mrg, .mpd, .mwb, .mud, .ndf, .myd, .nrmlib, .nnt, .ns3, .ns2, .nsf, .ns4, .nv2, .nv, .nyf, .nwdb, .oqy, .odb, .owc, .orx, .p97, .p96, .pdb, .pan, .pnz, .pdm, .qvd, .qry, .rctd, .rbf, .rodx, .rod, .rsd, .rpd, .sbf, .sas7bdat, .sdb, .scx, .sdf, .sdc, .spq, .sis, .sqlite, .sql, .sqlitedb, .sqlite3, .temx, .te, .tps, .tmd, .trm, .trc, .udl, .udb, .v12, .usr, .vpd, .vis, .wdb, .vvv, .wrk, .wmdb, .xld, .xdb, .abcddb, .xmlff, .abx, .abs, .adn, .accdw, .fm5, .db2, .icg, .hjt, .kdb, .icr, .maw, .lut, .mdt, .mdn, .vhd, .vdi, .pvm, .vmdk, .vmsn, .vmem, .nvram, .vmsd, .raw, .vmx, .subvol, .qcow2, .vsv, .bin, .vmrs, .avhd, .avdx, .vhdx, .iso, .vmcx
It’s also noted that the ransomware won’t encrypt the files having .exe, .dll, .lnk, .sys, .msi file extension.
The ransomware accepts command line arguments as shown below –
| Arguments | Description |
| -p | Encryption Path used to only encrypt files in the given path |
| -s | Path to file containing list of shares to include in the encryption |
| -n | Encryption percentage on how much content of the files needs to be encrypted |
| -l | Display logs or not (by default it displays logs) |
It will also generate logs about errors faced during encryption and the time taken to complete encryption in m/s with the help of an API called ‘QueryPerformanceCounter’.
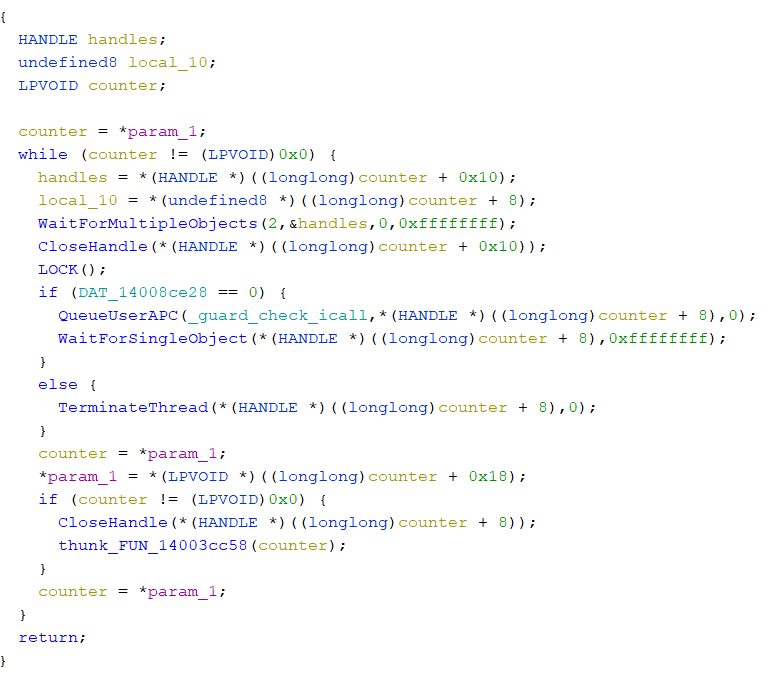
The Boost.Asio C++ library was used to create multiple of (4*processor_count) number of threads for asynchronous operation where the functions of the ransomware will be queued into the threads for further execution, with the help of ‘QueueUserAPC’ and ‘WaitForMultipleObjects’ APIs.
Removing Shadow Copies
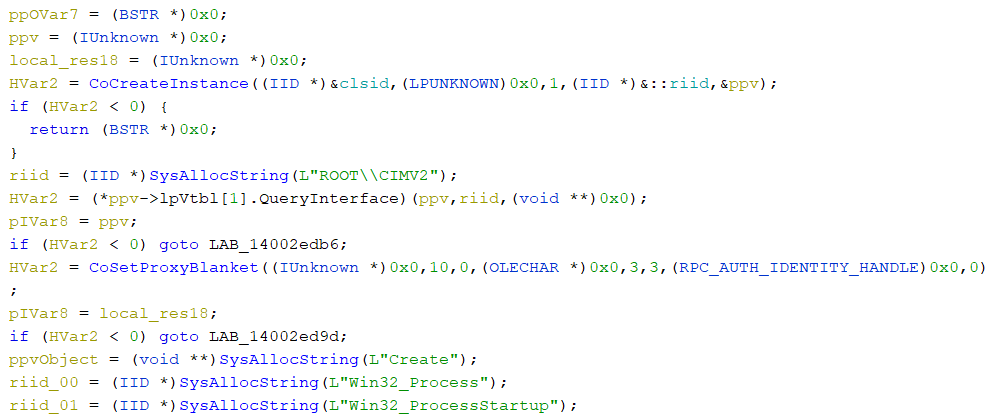
Another function containing a list of obfuscated characters will be deobfuscated into a powershell command powershell.exe -Command “Get-WmiObject Win32_Shadowcopy | Remove-WmiObject” which will be used to remove the Volume Shadow copies with the help of WMIC by creating a WebmLocator object to ROOT\\CIMV2 using ‘CoCreateInstance’ API.
All the logical drives are populated by calling the API ‘GetLogicalDriveStringsA’ and the ransomware uses ‘FindFirstFileW’ and ‘FindNextFileW’ to parse all directories and place the ransom note ‘akira_readme.txt’.
Process Killing
The ransomware is also capable of killing process which are registered resources with the windows restart manager, to encrypt the files used by them uninterruptedly, to achieve this it does the following:
First it calls ‘wtsenumerateprocesses’ to find all the running processes and retrieve the PIDs which will then be compared with the list of Whitelisted process names and stores the PIDs of the whitelisted process.
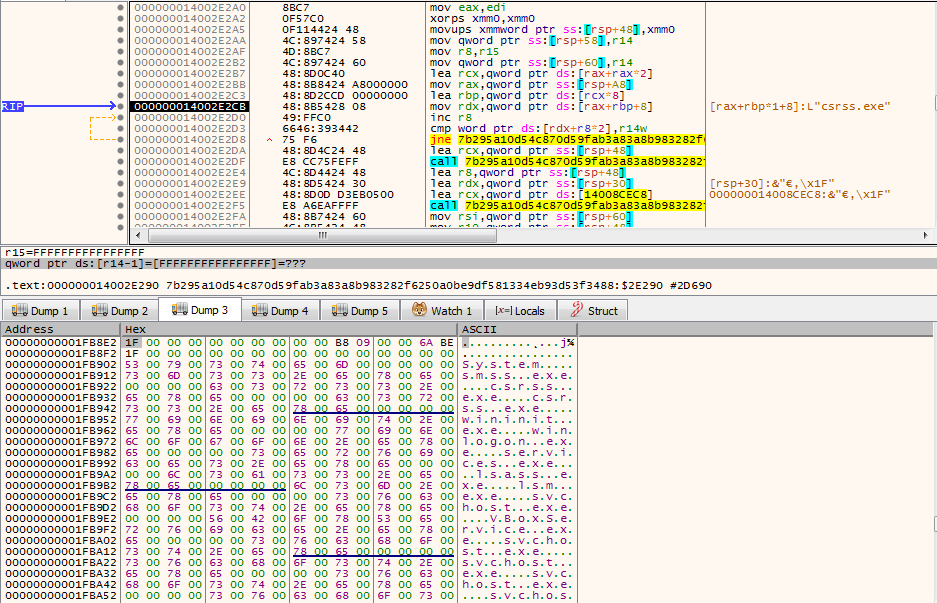
Each file will be passed to a function which will start a restart manager session and register those files to restart manager, where ‘RmGetList’ will be called which will return the list of process and services information that are using the file.
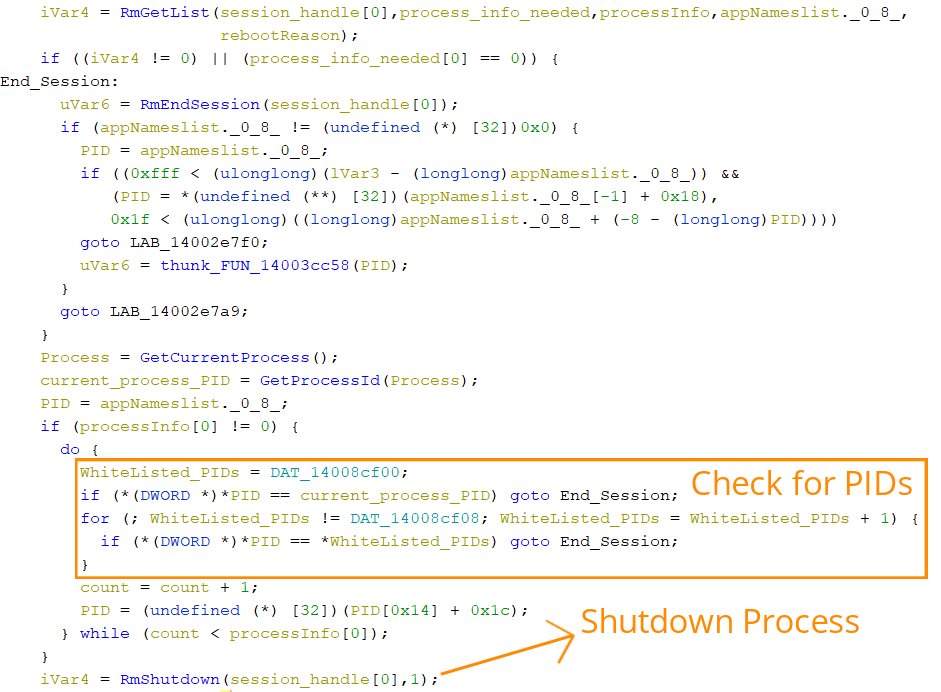
It then compares the PID of the current process and the whitelisted processes with the PID of the Process obtained from ‘RmGetList’, if there is a match found it will end the restart manager session, otherwise, it will forcefully shut down all registered processes that are using the file by calling ‘RmShutdown’ with the ‘RmForceShutdown’ flag.
Encryption
The files are encrypted using the ChaCha encryption algorithm where it uses ‘CryptGenRandom’ API to generate a 32 byte ChaCha key and 8 byte ChaCha nonce. Both of these will be encrypted using the hardcoded RSA Publickey using ‘CryptEncrypt’ and will be appended to the encrypted files with additional information of what mode of encryption is used and how much size of the file was encrypted.
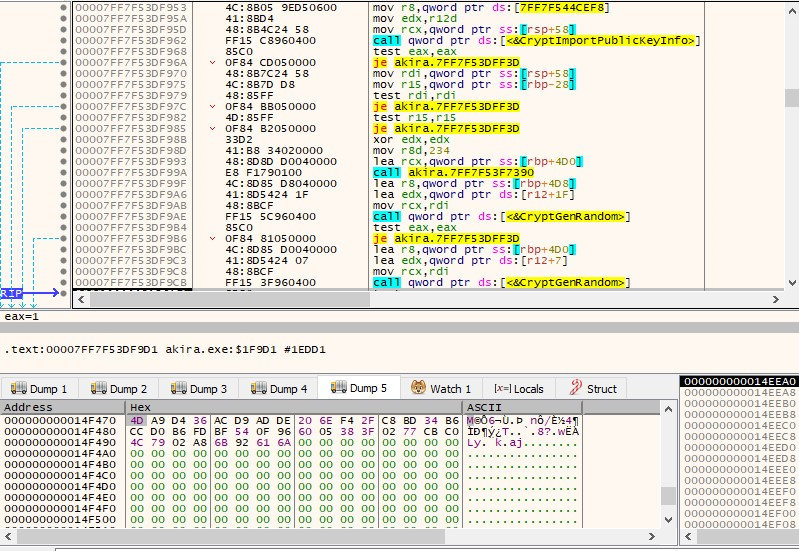
We have also observed that for the file extensions obtained earlier the whole content of the file will be encrypted. And for the files having extensions not in the list only partial data will be encrypted.
Each encrypted file will be appended with additional data of 0x216 bytes which will have the following structure,
<0x20C bytes points to RSA encrypted chacha nonce and key><0x1 byte points to which mode of encryption is used ><0x9 bytes points to the size of data that got encrypted>
The ransomware has three modes of encrypting files
| 0x0 | FULL_ENCRYPT |
| 0x1 | PARTIAL_ENCRYPT |
| 0x2 | HEADER_ENCRYPT |
Relation with Conti Ransomware
From the extensions the ransomware uses, we were able to correlate it with the Conti ransomware. Further analysis revealed that the threat actors copied the leaked version of the Conti ransomware source code as most of the functions are similar to the Conti ransomware.
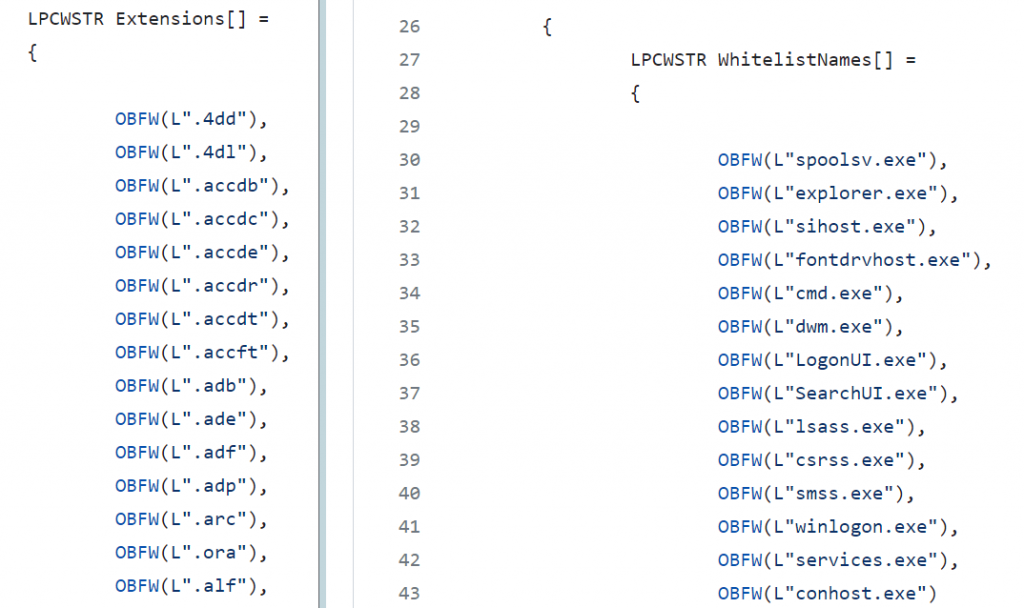
The ‘OBFW’ in front of the strings is a macro used to obfuscate the strings.
It is also to be noted that earlier the leaked source code was also used by other ransomware gangs that includes ONYX Ransomware, ScareCrow Ransomware, BlueSky ransomware, Meow Ransomware and Putin Ransomware.
Conclusion
The frequency of attacks involving the replication of leaked source code to develop new ransomware is increasing, indicating a potential rise in similar incidents in the future. These attackers specifically focus on exploiting vulnerabilities in systems. Considering this trend, it is crucial to take proactive measures to enhance security and safeguard your systems. To learn more about effective security practices, continue reading this blog post.
IOCs
Tor Website
https[:]//akiralkzxzq2dsrzsrvbr2xgbbu2wgsmxryd4csgfameg52n7efvr2id[.]onion
| Hash | Detection Name |
| C7AE7F5BECB7CF94AA107DDC1CAF4B03 | Trojan ( 005a430d1 ) |
| E44EB48C7F72FFAC5AF3C7A37BF80587 | Trojan ( 005a55941 ) |
| AF95FBCF9DA33352655F3C2BAB3397E2 | Trojan ( 005a430d1 ) |
| 431D61E95586C03461552D134CA54D16 | Trojan ( 005a430d1 ) |
| D25890A2E967A17FF3DAD8A70BFDD832 | Trojan ( 005a430d1 ) |






