For its distinctive attack techniques, but a lot more for the damage it causes, ransomware counts as one of the most popular types of malware since its inception. Besides new ransomware, cyber attackers are often refashioning the old ransomware to inveigle more ransom from victims and execute more lethal attacks.
Since the advent of ransomware, K7 Labs has been tracking it and has analyzed significant changes in terms of its kill chain including the payload, code changes (use of APIs, obfuscation and so on), and encryption routines. In this blog we’ll summarise the organic evolution of some recent high-profile ransomware which have had a significant impact on the cyber world, and also dissect a new ransomware family called LockerGoga to find out what nasty surprises it has up its sleeve.

LockerGoga has had high-profile victims, some of the recent ones being Altran Technologies, a French company, and Norsk Hydro, headquartered in Oslo. Once an intrusion is successful, LockerGoga spreads through the company’s network and encrypts all the user files (docs, images, etc.). As a result, Altran Technologies had to shut down their entire network, and Norsk Hydro had to switch to manual production. These two incidents are not isolated cases; many other enterprises are forced to pay ransom demands when they find their networks have been compromised.
The name LockerGoga comes from the source code path string found in the Portable Executable (PE) file. As the word ‘Goga’ is popular in Romanian, many experts believe the ransomware originates in Romania. Interestingly, LockerGoga uses a digital signature issued to a UK-based IT consulting firm, MIKL Limited. The digital certificate has since been revoked.
After infiltrating the network, the ransomware executes, copying itself to the %temp% directory, and then encrypts all user files that exist on the system, changing their extension to .locked. LockerGoga encrypts each file with the argument ‘-w’ and spawns a new process for each file that it encrypts.
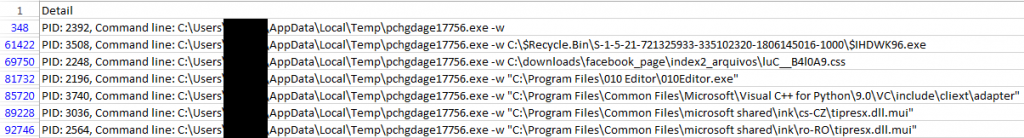
LockerGoga also uses other encryption parameters for encrypting the user’s files. It uses arguments such as ‘-k’, ‘-m’, ‘-l’, ‘-e’ through a switch statement. Spawning a new process for every encryption cycle seems like a new evasion technique, but it actually causes a hogging of the system memory and so a long time is taken to encrypt all the relevant files on the system. Another significant point to notice about LockeGoga is the presence of a file called ‘Wipe.’ The file gets created in a shared folder, and it consumes a noticeable amount of storage space.
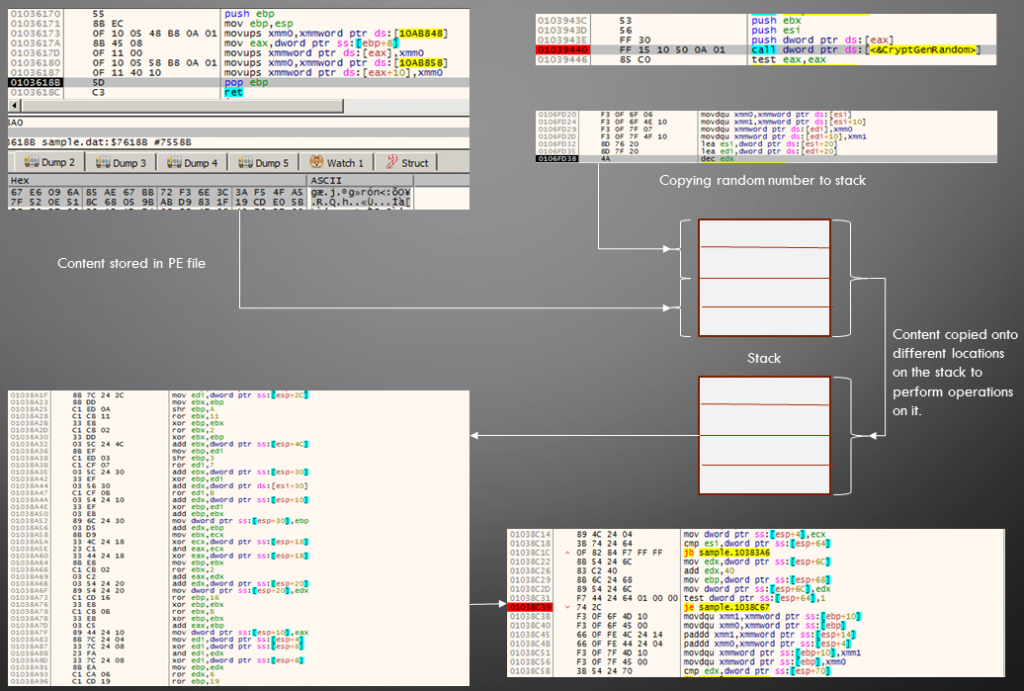
The encryption process begins with the generation of the key used for encrypting the files.
The key is generated by making use of instructions like AESKEYGENASSIST, PEXTRD and AESENC on a blob of data of size 0x40 bytes. This is obtained by concatenating a 0x20 byte length output of a call to the ADVAPI32.dll_CryptGenRandom API and 0x20 bytes of data fetched from the ransomware executable.
Although most of the PE info tools identify the ransomware sample as a ‘Microsoft Visual C++ 8’ compiled file, it might have been coded in a different language.
Upon comparison with a legit VC8 compiled file, the ransomware sample differs in the way that it calls ADVAPI32.dll_CryptGenRandom even before the user code starts. After generating the encryption key, the malware encrypts the user’s file. A handle is retrieved for a file that is to be encrypted by calling the MapViewOfFileEx API, and the key generated is appended to the file before encrypting its contents.

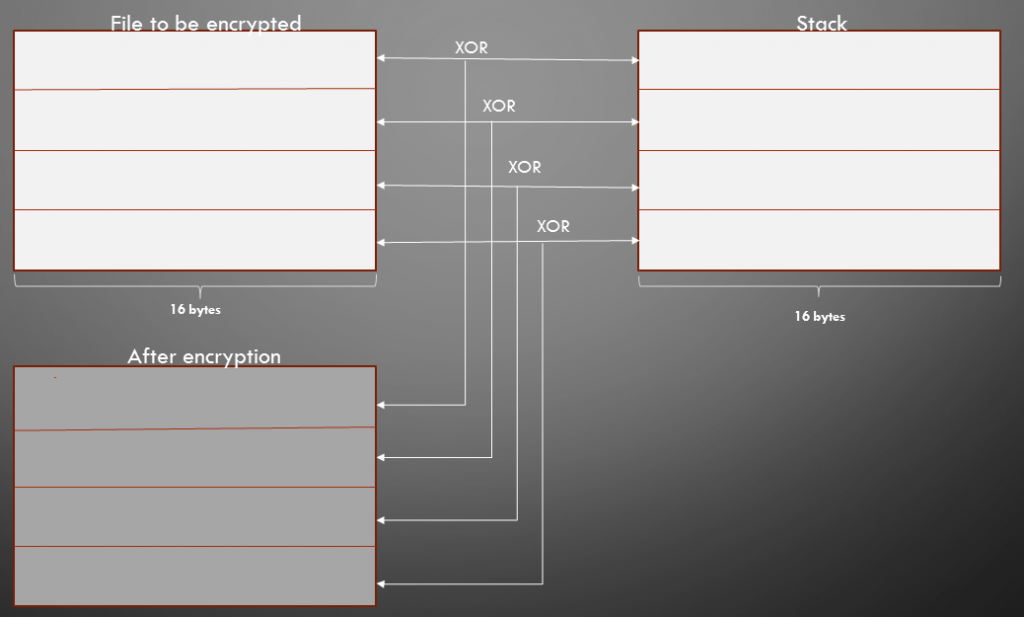
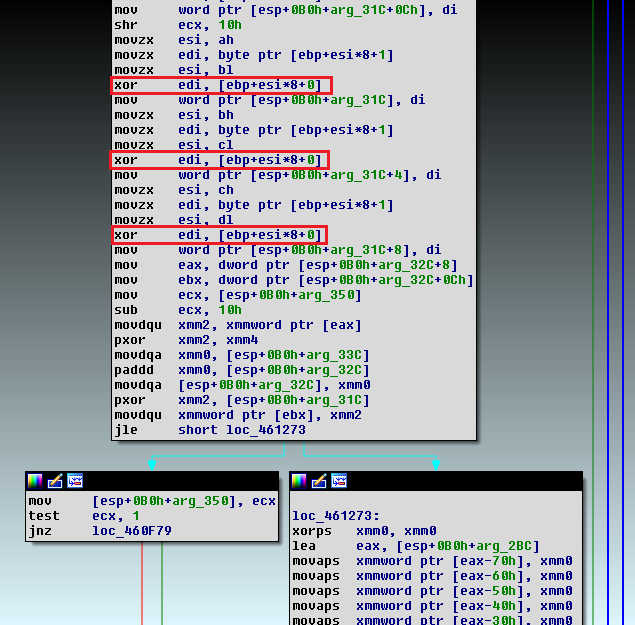
The author uses the XOR operation for encrypting all the files on the system as depicted in Figure 5 and the code snippet of the same is depicted in Figure 6.
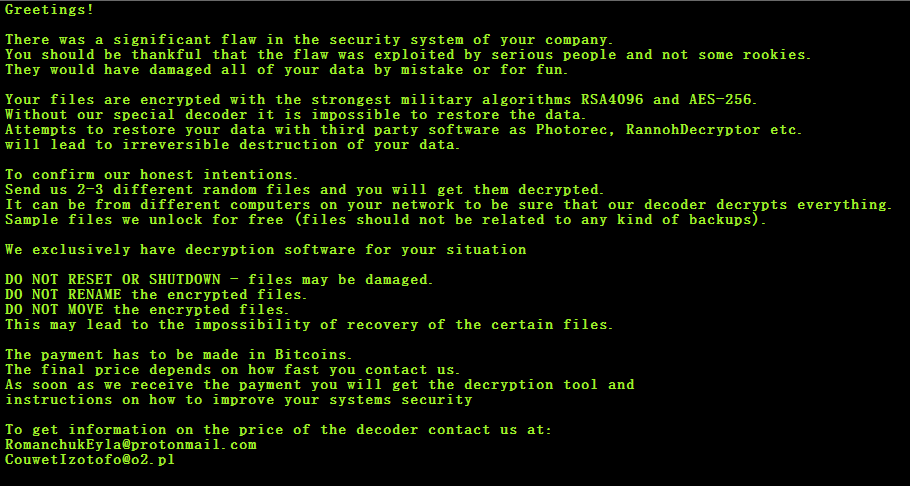
After successfully encrypting the user data, the ransomware drops its ransom note in a file named READ-ME-NOW.txt mentioning the contact details of the actor. Interestingly, unlike other ransomware, LockerGoga doesn’t mention the exact ransom amount. We suspect this might have been left blank since an open negotiation can be put forth for the ransom, assuming the victim connects with them, or just some dumb mistake.
Over the years ransomware has improved its arsenal in all aspects evolving from an irritating ‘screen locker’ to the ‘machinator of an irreparable mess’. But fear not, K7 Security is here to protect you from such malware attacks. We ensure you have the toughest defense there is against ransomware at all security levels from URL to file-based to behavioural protection, including a heuristic Anti-Ransomware product feature.
Indicators of Compromise:
B3D3DA12CA3B9EFD042953CAA6C3B8CD Trojan ( 005470f61 )
52340664FE59E030790C48B66924B5BD Trojan ( 005474b11 )





