We came across a tweet about a lock screen app which installs ransomware by faking itself as a legitimate app, so that users are tricked into falling prey. This approach by the threat actor was quite interesting considering the fact that there were no ransom demands and the key to unlock the device has been hardcoded in the app. In this blog, we will be explaining the technical aspects of the app which was developed by an attacker to lock the screen of a user’s device.
Technical Details
Once the app “gbwhatsapp.apk“ ( Hash: 70273ee146260bafb1cc136a0249e2a2 ) is installed as shown in Figure 1, it seems to execute a shell command in its class ADRTLogCatReader. In the code shown in Figure 2, we can see it uses the command “logcat -v threadtime”. The shell command adb logcat -v threadtime displays the date, invocation time, priority, tag, and the PID and TID of the thread issuing the message.

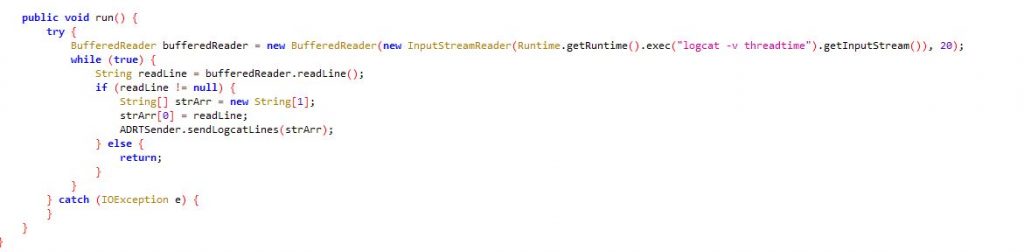
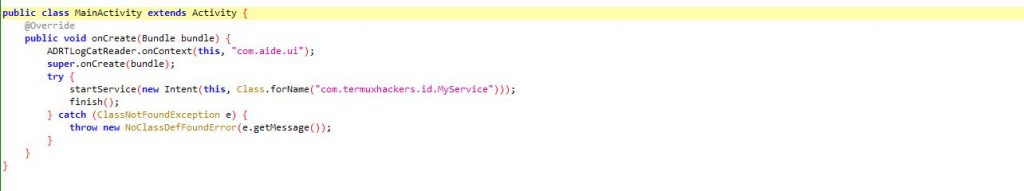
In the main activity, it looks like this app was developed on AIDE “com.aide.ui”, a tool to develop Android apps directly on an Android device as shown in Figure 3, and the main activity starts a service named MyService.
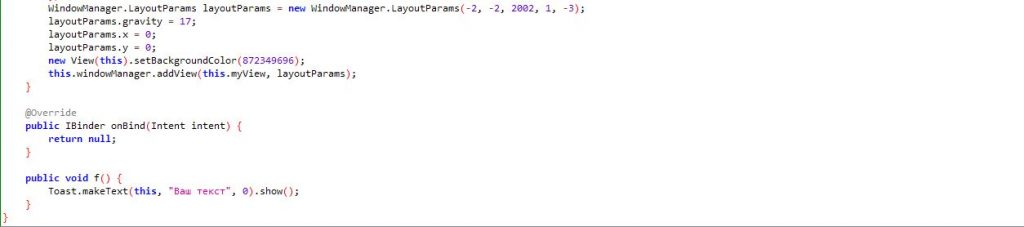
MyService invokes the malicious behaviour of the app. The idea behind this is displaying a lock screen window which cannot be exited until the correct key is entered. WindowManager displays a window on top of the screen and makes it persist using the function Toast.makeTest().show() as shown in Figure 4.
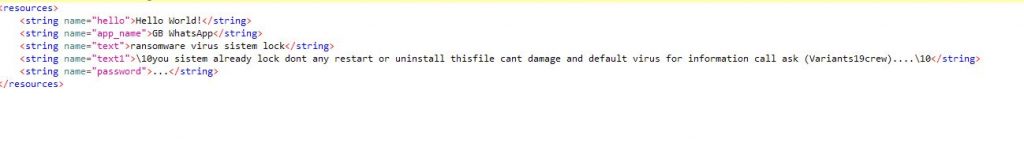
The lock screen consists of a note which can be seen from resource field “ransomware virus sistem lock” and “you sistem already lock dont any restart or uninstall thisfile cant damage and default virus for information call ask (Variants19crew)….” as shown in Figure 5 and Figure 6.
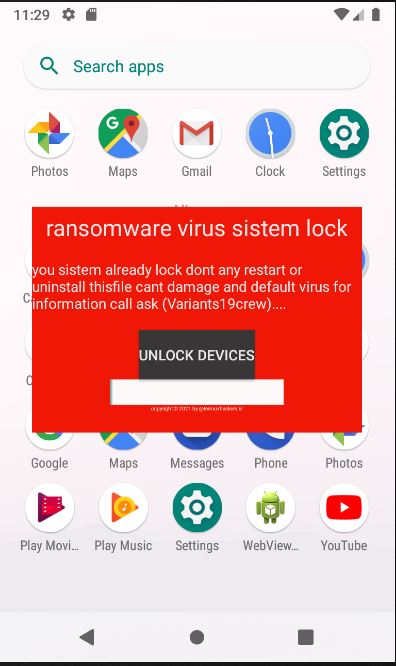
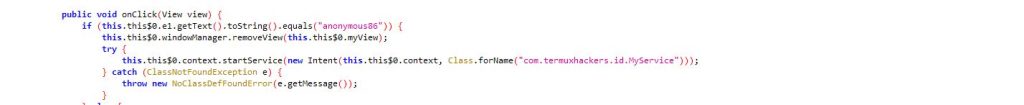
Fortunately, there were no ransom demands and the key to unlock the device has also been hardcoded which can be used to get rid of this window as shown in Figure 7. When the user unlocks the device by entering the string “anonymous86”, it will kill the app.
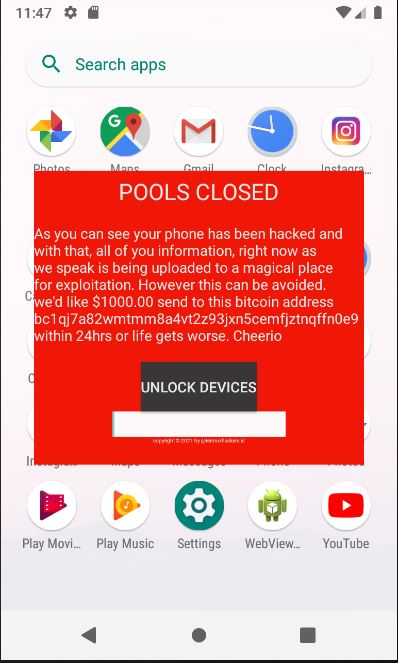
There are scenarios where the malware author demands a ransom for the app “instagramgold.apk” as shown in Figure 8. The lock screen consists of a note which can also be seen from resource field “POOLS CLOSED” and “As you can see your phone has been hacked and with that, all of you information, right now as we speak is being uploaded to a magical place for exploitation. However this can be avoided. we’d like $1000.00 send to this bitcoin address bc1qj7a82wmtmm8a4vt2z93jxn5cemfjztnqffn0e9 within 24hrs or life gets worse. Cheerio”
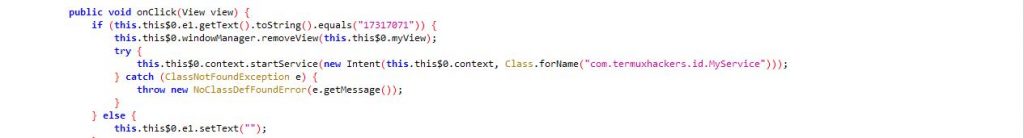
Fortunately, the key to get rid of this lock screen window is hardcoded. The device can be unlocked by entering the string “17317071” as shown in Figure 9 which kills the app.
This malware author is spreading a fake lock screen app resembling legitimate apps such as WhatsApp, GitHub, Netflix, Instagram Gold, Spotify, etc. However, while some of the apps of this type demand a ransom to unlock the device’s screen, a few others don’t. That said, we at K7 Labs are constantly monitoring such campaigns. We recommend users to avoid believing in such third party apps and break the chain in spreading these fake apps.







