The recent outbreak of the Xpaj virus in India due to the mass distribution of certain infected software provided me with an incentive to look at the virus code in a bit more detail.
Xpaj is not a new virus. It is at least a couple of years old and it has already been written about by my security industry colleagues. However there may be some space for me to provide my views on some of the technical aspects of this virus.
Xpaj is a midinfecting, polymorphic virus with a difference. Most viruses, including the common ones like Virut and Sality, leave behind clear, tell-tale signs, sometimes infection markers, in the infected host to indicate that there is something amiss. For example the entrypoint being modified to point to the last section which has rwx attributes smells somewhat rotten. Xpaj, however, is very clever in making all the modifications in the host whilst remaining extremely well camouflaged.
Changes to the code and data sections have been managed so that all looks normal:
- The original EP remains unchanged. Xpaj is a midinfector which patches certain relative calls in the host file’s code.
- There are no changes made to the attributes of any section. The required page permission changes are invoked dynamically via a call to ZwVirtualProtectMemory.
- Sections after the one containing the bulk of the virus are shifted down with ease, and corrections are made in the metadata areas, including relocating the resources, if any.
- Xpaj has no problems infecting DLLs with relocations, and can infect SYS files which run in kernel mode.
- Even the clusters of polymorphic virus code in the host file’s code section looks like bona fide High-Level Language (HLL) code.
Here is an example of some of the Xpaj code pointed to after judicious host-call-patching:
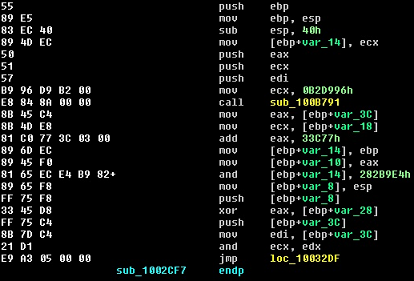
The above snippet conforms to HLL patterns in certain files compiled with Microsoft Visual C++ 8.
The virus code goes on to execute a mini virtual machine which does the decryption and makes the call to ZwVirtualProtectMemory before transferring control to the bulk of the virus code.
The Xpaj virus authors went through a lot of trouble, including a fair amount of QA, to develop their “product”. Xpaj is indeed a sophisticated virus. Of that there is no doubt. It demonstrates the lengths to which malware authors are prepared to go to spread obfuscated malicious code. Interestingly, a denuded Xpaj, divested of its obfuscatory vestments, is nothing more than a clicker.
Well before the outbreak, K7 customers who had their real-time scanner active would, of course, have already been protected. K7 products detect and clean Xpaj-infected files as “Virus ( 700000051 )”.
Samir Mody
Senior Manager, K7TCL
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed/






