Like how there are health risks in sharing towels, there are security risks when you share USB sticks across systems, especially if you are not protected by a robust security product.
Some of the risks associated with these are data theft and malware installation.
Let’s look at the most prevalent old USB worms and virus artefacts that have been reported to us via our telemetry system time and time again and see what the data tells us.
USB Worms vs Viruses
While USB worms (aka autorun worms) spread by taking advantage of the plug-and-play feature available for USB devices, which allows data transfer without user intervention; viruses (aka “file infectors”) attach themselves to executable programs and spread whenever you run the infected program.
And if the AutoRun feature is enabled, it would automatically launch installers and other programs when the device is merely plugged in. However, an embedded virus in a file could still infect the system when the file is opened, even if AutoRun is disabled.
Now, let us look at the reasons why USB sticks are a convenient mode of malware transfer for the threat actors.
USB Advantages
The popularity of USB based worms has not waned since USB storage devices are convenient and used by many people, easy to handle due to their small size, easily available, portable, and inexpensive. It is relatively trivial to distribute malware on these devices. It is also easy to spread the infection to a clean USB drive from an infected computer.
USB drives could also be infected while loading it with default software, if proper quality control measures are not taken.
Sophisticated USB Attacks
Nowadays, USB sticks carry crypto mining malware too. USB malware spreads exclusively through devices that plug into the USB port of computers. These could be used for targeted attacks on systems disconnected from the internet, e.g. power plants, nuclear facilities, etc. The infamous Stuxnet worm that targeted Iranian organizations via an infected USB drive is a prime example of how USBs can be used to deliver malware across air gaps.
Telemetry
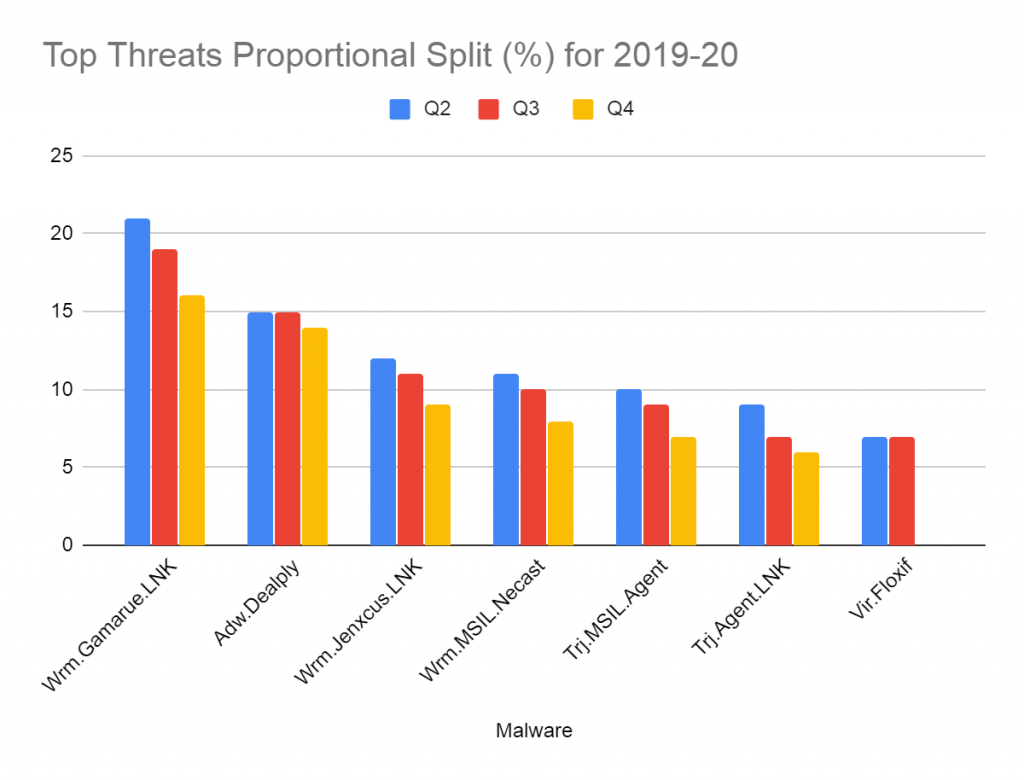
Telemetry stats from the quarters Q2, Q3 and Q4 2019-20 reveal that the proportion of users who had an encounter with the same families of USB worms and viruses across quarters has remained consistently high. Among the top 10 malware listed in our quarterly reports, the USB worm families of Gamarue and Jenxcus were among the top 5 and the Floxif virus was among the top 10.
We also gleaned that among the most prevalent worms and viruses, the percentage of users who have shown repeated infections of the same malware was around 30%.
On looking deeper into the metadata related to these threat events, we believe that many users are not following satisfactory security hygiene practices. Many appear to be plugging in their USBs on their system after perhaps using it on an infected system with no security product installed or sharing their USBs with others who are not very security conscious.
In the case of viruses we have observed that some users’ backups themselves contain infected files, and each time the backup is accessed, the files get reported by the security product, again and again.
As can be seen from our stats, the USB worms Gamarue and Jenxcus have been prevalent across all the 3 quarters as shown in Figure 1 above. However, we can see that the Floxif virus has fallen off the radar in Q4 2019-20, possibly due to users practicing better security hygiene.
Few tips to stay safe
- Ensure AutoRun feature is in a disabled state, and manually launch programs in the flash drive only after a complete scan of the drive by a reputed and robust Anti-Virus product like K7 Total Security
- Keep your Anti-Virus up-to-date
- Backup your critical data
- Ensure that all your backups, including cloud-based ones, are malware free
- Avoid sharing your USB sticks
- Do not use your USB sticks on untrusted systems
- Physical security needs to be in place so that random USB devices are not plugged into air-gapped systems. Also block unused USB ports on such systems
- Train your employees and make them aware of common threat vectors
- Follow the principle of least privilege and restrict access to critical systems
Practicing good cyber hygiene, including restrictions for removable devices and installing a reputable security product, is the best way to minimize security risks that could attack your systems.