Stealing crypto-currency is not new to threat actors. Thinner profit margins from mining makes stealing the coins from wallets more lucrative. One of the common techniques is to scrape the clipboard for wallet addresses and replace them with that of the attacker’s own address. The victim is left with no knowledge of the theft happening.
In this blog, we will be looking at one such CryptoClip hijacker malware, that was generally seen to be spammed out via Discord. Discord is one of the ways to stay in touch with people of a common interest. Hence spamming out CryptoClip hijacker malware to Discord servers that discuss crypto trading, mining would mean the malware reaches people who are actively dealing with crypto currency.
An unsuspecting user could download and execute these binaries. This malware could be spammed out via the traditional e-mail attachment technique too. We found one such malware that had the filename CryptoClipWatcher.exe, probably trying to pose as the safe CryptoClipWatcher tool.
Binary Overview
This binary is .NET compiled
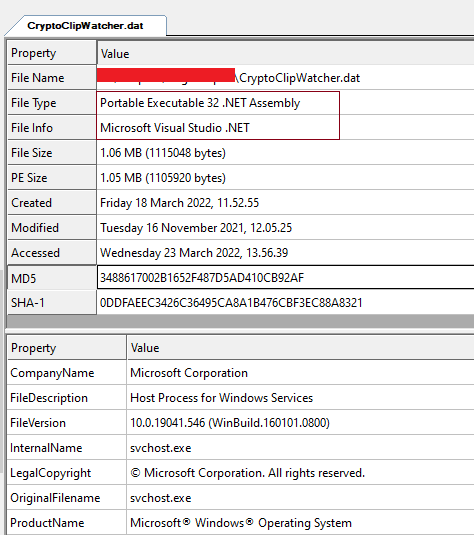
This file’s version information and the internal name was spoofed to be like svchost.exe. Legitimate svchost.exe file would be Microsoft Visual C++ 8 compiled, and not .NET as observed in Figure 1. The file is also signed with a fake digital certificate as shown Figure 3.
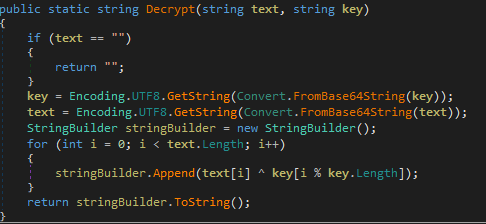
The malware uses a simple decryption logic for all its encrypted data. First the encrypted string and a key ( ‘UUdkUzZTQkFtMXlKTkE3Zw==’) is decoded in base64 format. Then the decoded string is XORed with the decoded key. Figure 3 depicts this decryption process.
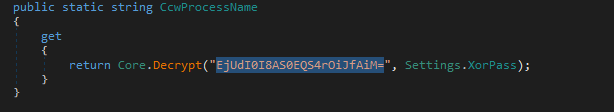
Even the file’s original filename was seen as base64 encoded and XOR encrypted. The decoded value was EjUdI0I8AS0EQS4rOiJfAiM=: crypto clip watcher. which as mentioned earlier is the name of a legitimate crypto tool.
Persistence technique used in this binary file
On statically analyzing the decompiled IL binary we found the reference to a persistence entry in %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup where the malware self copies and executes itself under the guise of svchost32.exe. Adds the same filepath to the run entry as well, under the subkey “Host Process for Windows Services” as shown in Figure 5.
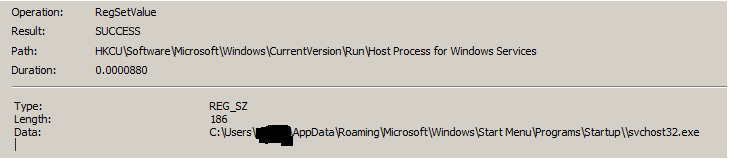
Uses one another standard technique of adding scheduled tasks using cmd.exe.
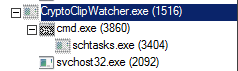
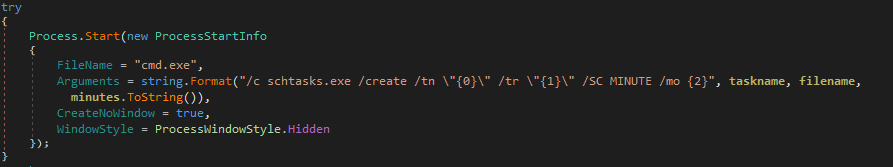
The self-copied file svchost32.exe is scheduled to be executed every minute by creating a job file as shown in Figure 7.
Malware Mechanism
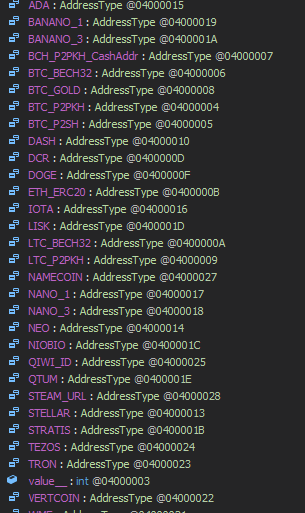
This file has 38 crypto wallet addresses of the attacker, few of the shown in Figure 8. This addresses are also encoded with base64 and XORed with the key.
Some of the transactions to this wallet are shown below in Figure 9.
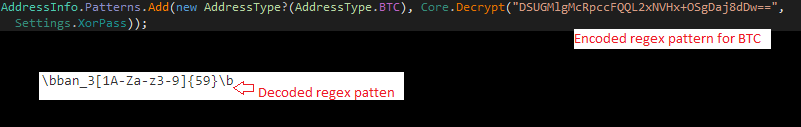
A regex pattern(“\b(79|380)[0-9]{9}\b”) is used by this malware to scrape for crypto wallet addresses. Once that is done the malware validates to which currency the scraped wallet is relevant to, using the currency wallet specific regex. These regexes are also encoded as shown in Figure 10.
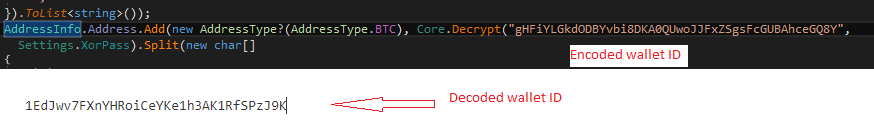
The user wallet address in the clipboard is replaced with the malware author’s wallet address. The code snippet to find and replace the clipboard content is shown in Figure 11.
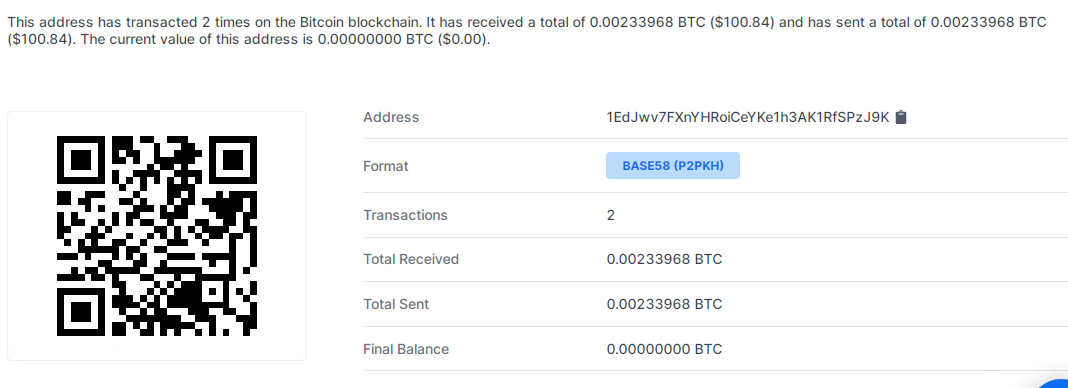
We checked one of the attacker’s crypto wallet addresses and found a couple of transactions being made to it, which roughly translates to about 100$.
Transactions
It is always advisable to download tools or applications from reputable sources and exercise caution while using any such binaries. It is also always advisable to use a security software like K7 Total Security.
Indicators Of Compromise (IOCs) and Detections
Hash 3488617002B1652F487D5AD410CB92AF
Detection Name Trojan(00545fd01)
Original File Name crypto clip watcher.exe
Mutex 2c092895c2e64adb
Behavior suspicious program (ID 700018)









