A few weeks ago it was mentioned that perhaps Rogue AV malware was less common in India than in other parts of the world. That is not to say that Indian users are completely immune to the scourge of Rogue AV. Even if the Rogue AV is designed to target users from the Western hemisphere, it is unfortunately possible for users in India to become collateral damage in a drive-by Rogue AV attack.
One family of Rogue AV which is doing the rounds in India calls itself “XP Anti-Virus 2011”. This family exhibits the usual characteristics of Rogue AV as shown below:
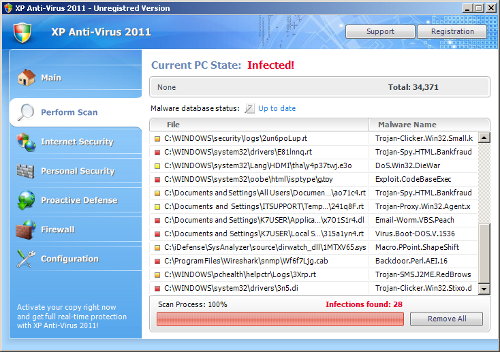
Fake infection report
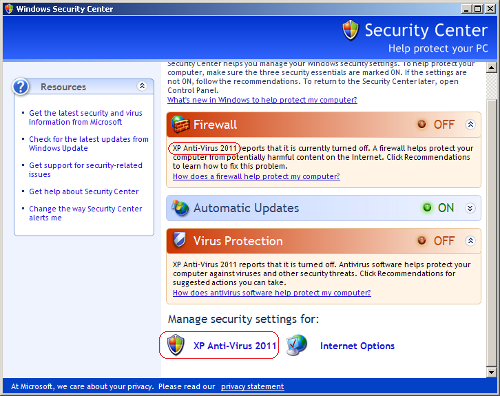
Fake security center warning
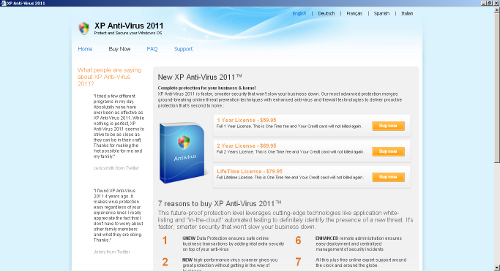
Online payment site (unfortunately very real)
Compare the above images with those here to notice a striking similarity, not least the presence of the string “2011” in both.
Interestingly the “XP Anti-Virus 2011” family also comes with malware descriptions for each of the entries in the fake infection report. Consider the following image:
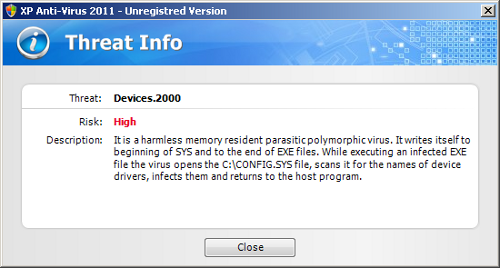
The above malware description has been plagiarised verbatim, as per a Google query, from our IT security colleagues at Kaspersky.
Of course, the purveyors of Rogue AV clearly rely on expected levels of technical ignorance on the part of the victim. There is a mismatch between the reported threat name and the corresponding file type, e.g. “Macro.PPoint.ShapeShift” is highly unlikely to be found in a SYS file. It also seems very strange to find so much DOS malware on what is clearly meant to be a Windows XP system more than a decade later. However, the average victim is unlikely to pick up on these nuances, especially when reeling under the fear tactics of Rogue AV.
Many families of Rogue AV, including the “XP Anti-Virus 2011” variety, make themselves extremely difficult to remove. They may block the running of other applications, including OS tools such as Regedit and Taskman, and common browsers such as Firefox. Unusually, “XP Anti-Virus 2011” even blocks new instances of Microsoft Internet Explorer, generally left clear to allow victims to pay up, opting for its own IE-like interface (please see the payment page image above). Needless to say the links to alternative language content do not work.
It is important to resist panic attacks when confronted with Rogue AV. Fear leads to online payment, which subsequently gives impetus to further instances of ransomware because the incentive is maintained. Therefore please do not part with your hard-earned cash. If the river of easy money is made to try up in this way it will certainly lead to the demise of ransomware in general.
In addition please keep your legitimate Anti-Virus software up-to-date with dynamic protection features such as HIPS configured appropriately to provide a robust phalanx to the burgeoning number of threats out there. Prevention is better than cure.
Samir Mody
Senior Manager, K7TCL







