Threat actors impersonating a Government entity, and using their fake authority and trustworthiness to coerce the victims to divulge their personal or banking details through a Phishing page or an App or a direct voice call is a well-known trend. In India, “Digital Arrest” is the new fad in this trend, and our government is actively working to educate citizens on how to protect themselves.
A particularly alarming aspect of this is when the targets are employees of government institutions and agencies. There have been several instances of advanced persistent threats (APTs) and external parties targeting military personnel, research institutes, and even educational institutions. This targeting is sometimes long-drawn and reuses the tools, framework, and other infra. In this blog, we will present two recent examples of such attacks in which the threat actors masquerade as Government and Judicial entities. We recently came across a tweet, in which was mentioned a few fake Indian government sites.
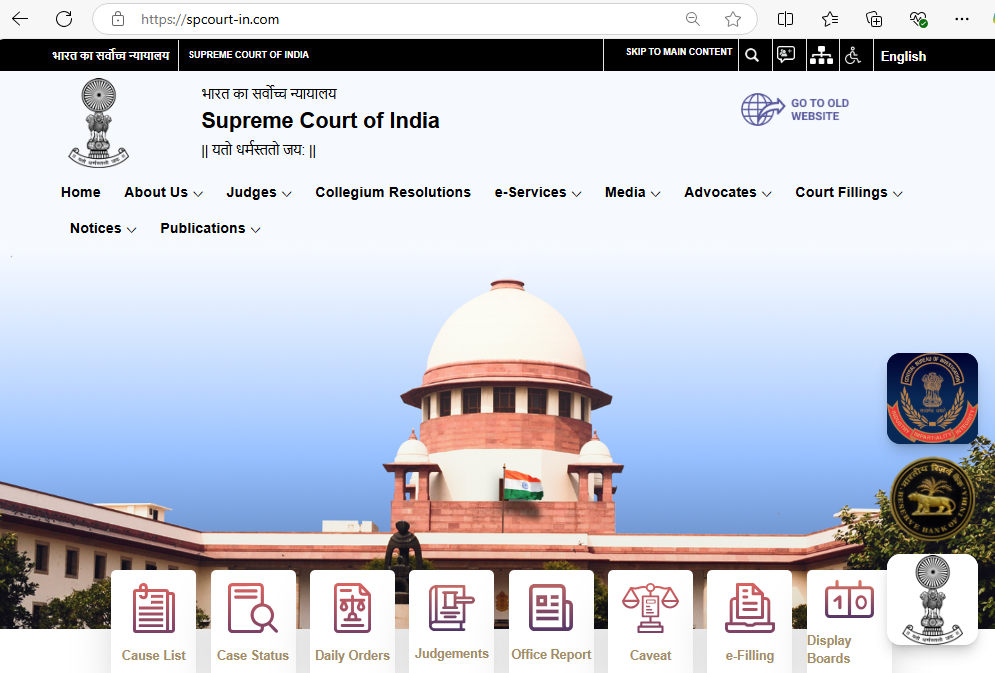
Let’s take a look at the domain “spcourt-in[.]com.”. This phishing site is designed to closely resemble the official website of the Supreme Court of India. This fake site collects PII (Personally Identifiable Information), bank account details, etc.
The major difference between the fake and the original site is the presence of those three logos at the bottom right, where the site harvests user data.
On the bottom right part of the page, three clickable icons appear to represent official organizations, including the “Central Bureau of Investigation,” “Reserve Bank of India,” and “Supreme Court of India,” just to provide some ‘fake’ authenticity to their site.
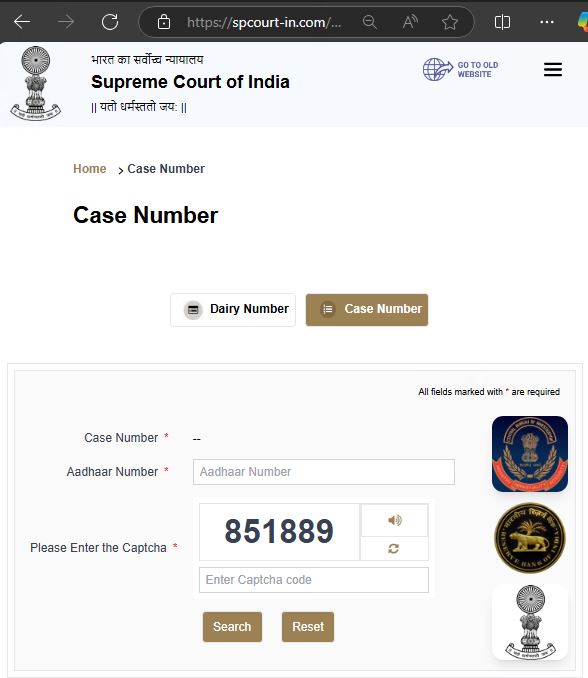
Clicking on the CBI logo (the first logo) takes the user to a page where they are prompted to enter details, such as their Aadhar number.
Clicking on the RBI logo (the second logo) leads the user to a page where they are asked to verify personal information. During this process, the site collects details such as date of birth, Aadhaar number, contact information, and bank account details (including passwords). At a later point in this blog, we will discuss what happens to the data that is being collected via these forms.
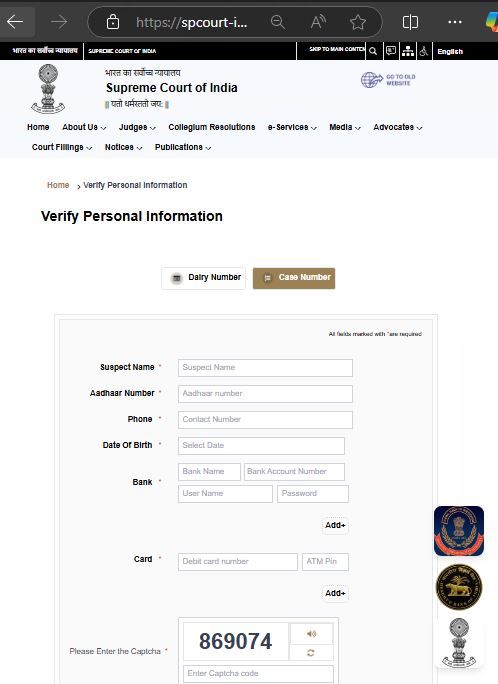
Detailed Analysis on Spcourt-in[.]com
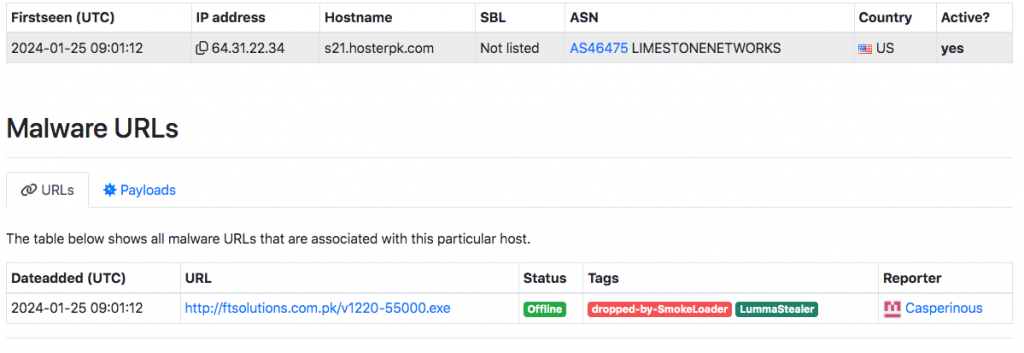
The IP address of the phishing site is “64.31.22.34” was registered on 27-01-2025 and has validity for a year. The website is hosted on servers provided by Hosterpk[.]com, a web hosting company based out of Pakistan. This information further suggests that the site is likely to be managed from outside India.
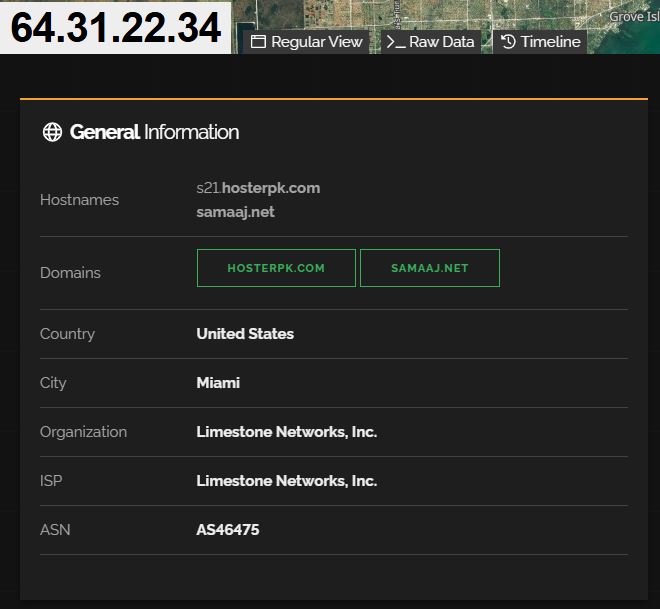
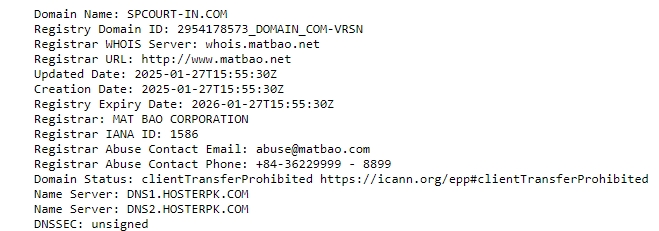
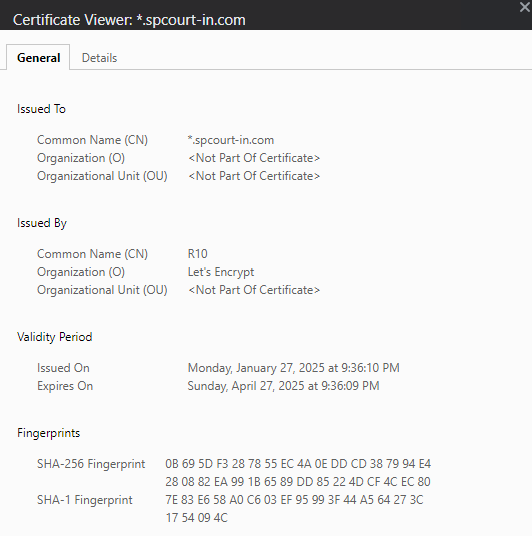
TLS details
The certificate is issued by the organization “Let’s Encrypt”. While Let’s Encrypt is known for providing free SSL certificates to secure websites, its use here indicates that the attacker is attempting to give the phishing site a legitimate and secure appearance, which could give a false sense of security to users into trusting this site with their PII.
The below image shows a list of PHP scripts used for processing the collected data.
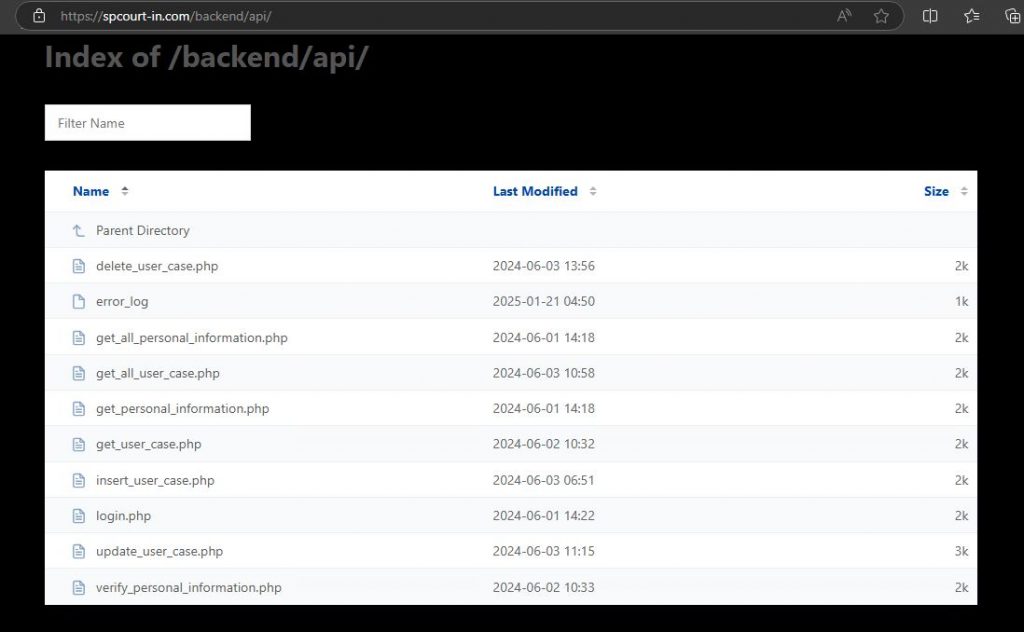
The forms on the site collecting the personal data and bank details are processed through the “get_all_Personal_information.php” and the data submitted are stored in JSON format.
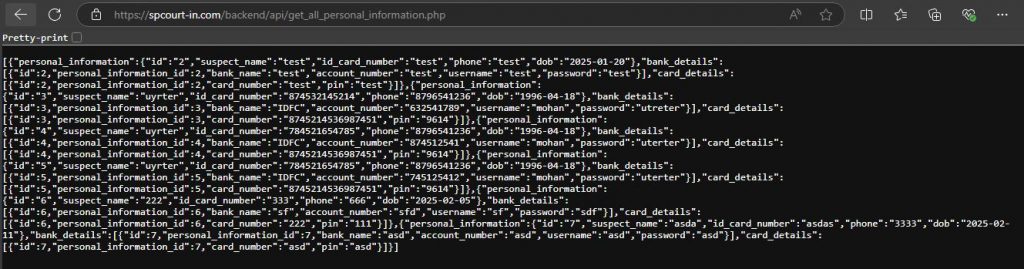
This domain hosts several JavaScripts as shown below.
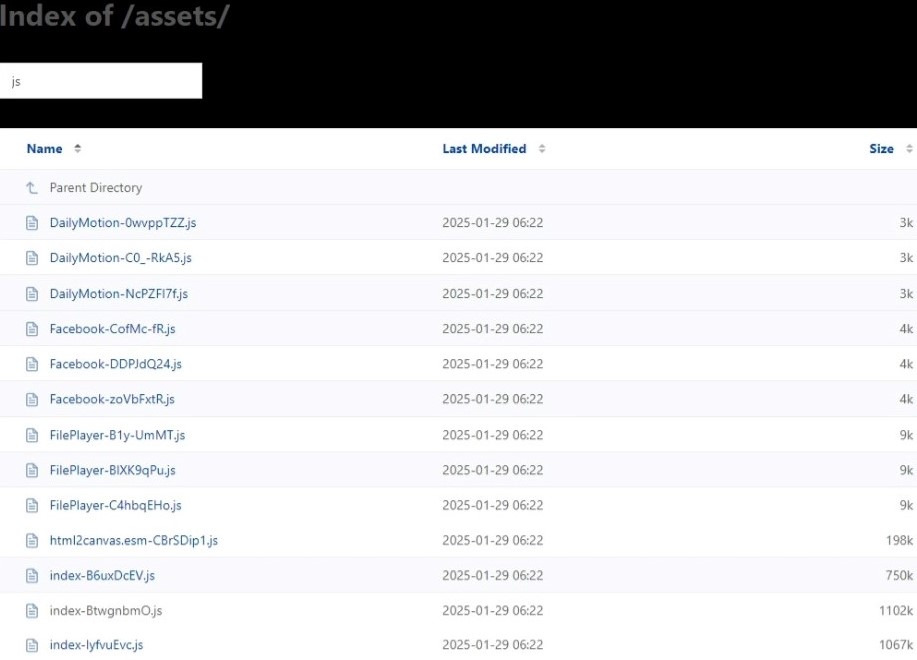
We also checked for signs of any IP abuse and discovered that the IP address associated with the Phishing site had been involved in a WordPress brute force attack.
There is also a history of Lumma Stealer being hosted on this site at an earlier point in time.
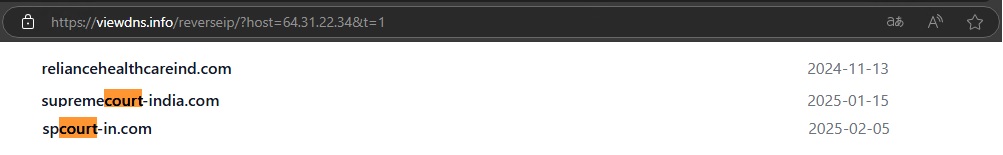
While performing a reverse IP lookup for the address 64.31.22.34, we discovered that another domain, supremecourt-india[.]com, was also hosted on the same server. This further suggests that multiple phishing sites may be operating from the same infrastructure, potentially targeting users by impersonating government entities in an attempt to harvest user data.
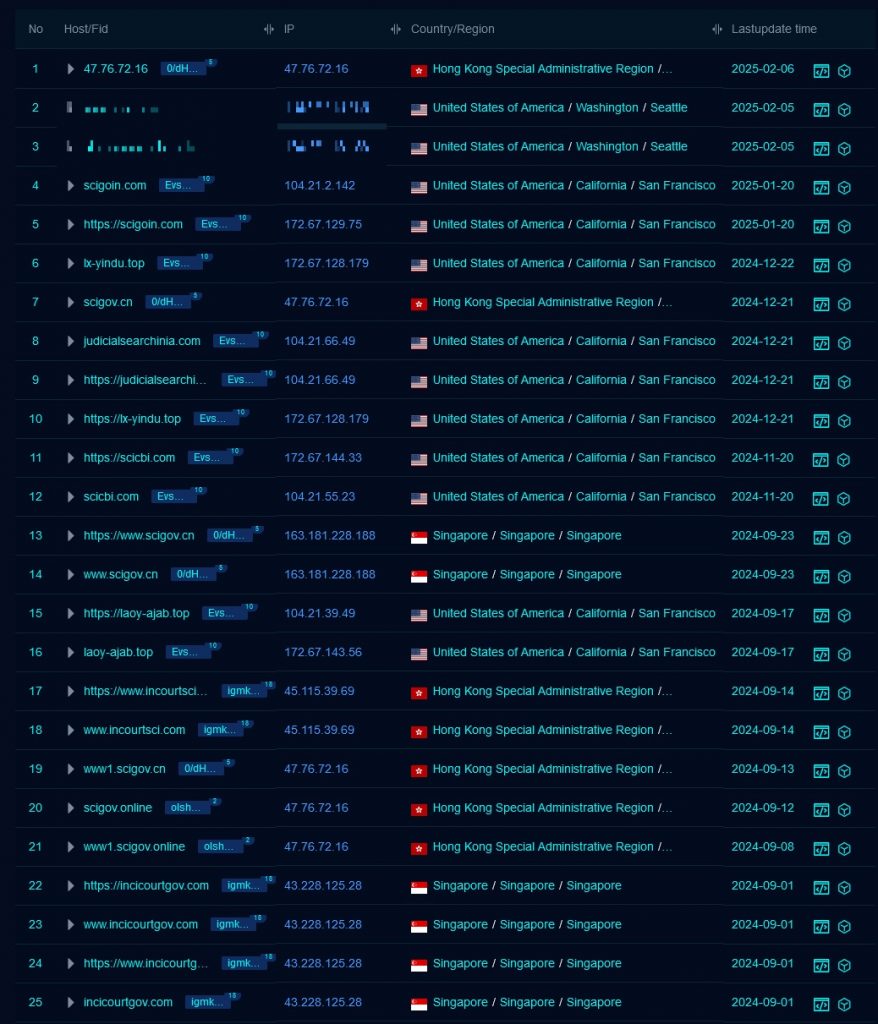
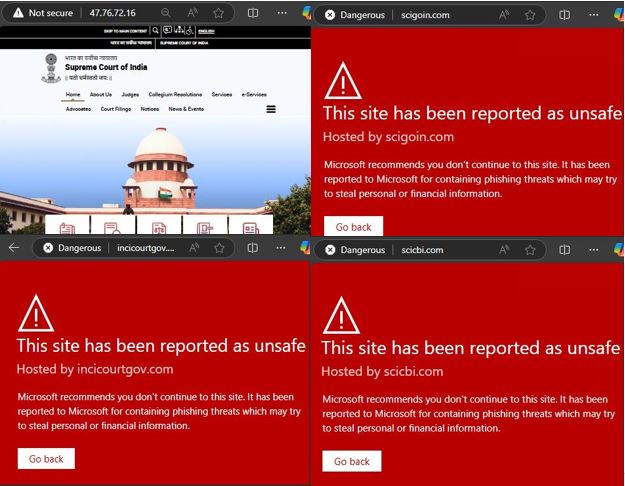
By searching with the filter for the website title “The Supreme Court of India | India” and specifying that the hosting country is not India, we obtained several results showing fake sites, some of which were already on the block list as shown in Fig 16. From these findings, it’s clear that these Phishing sites have been active for quite some time, indicating a prolonged campaign. However, the exact modus operandi of the attacker remains unclear. Specifically, it is unknown how the attacker plans to approach users and convince them to divulge their PII on these fraudulent sites.
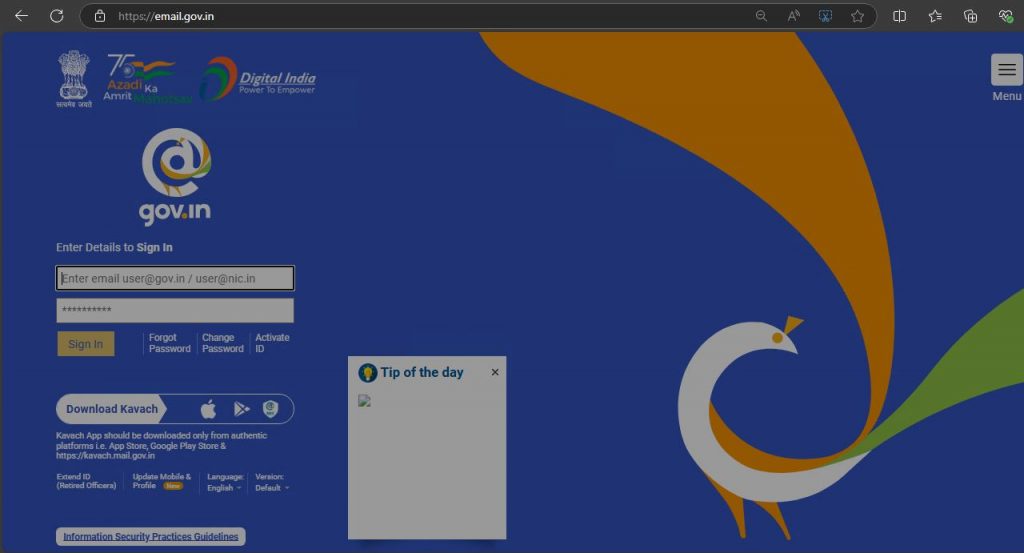
Now let’s examine the second site mentioned in the tweet, which is “email[.]gov[.]in[.]defenceindia[.]link”. This also is a phishing domain impersonating an official Indian government site.

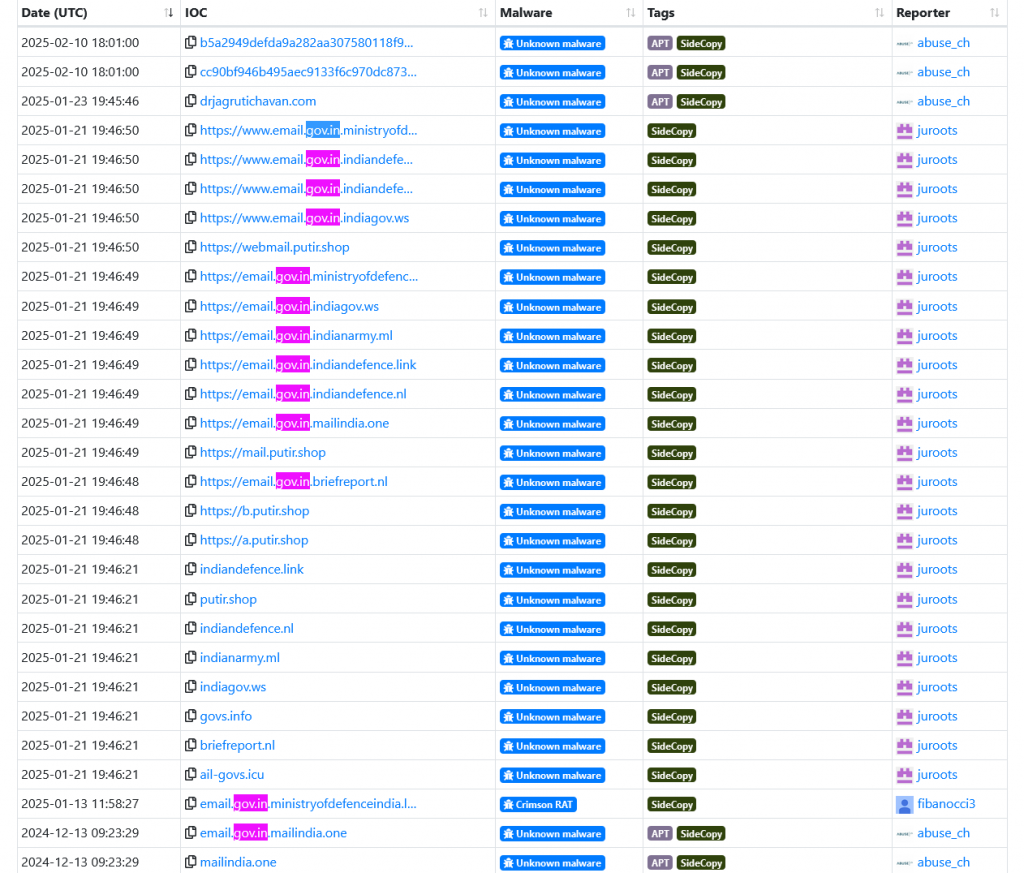
Of late, many impersonators of “email.gov.in” have been seen in the wild, searching on Malware Bazaar, we can see tags like Malware and RATs associated with them, all linked to SideCopy, a well-known APT operating out of Pakistan.
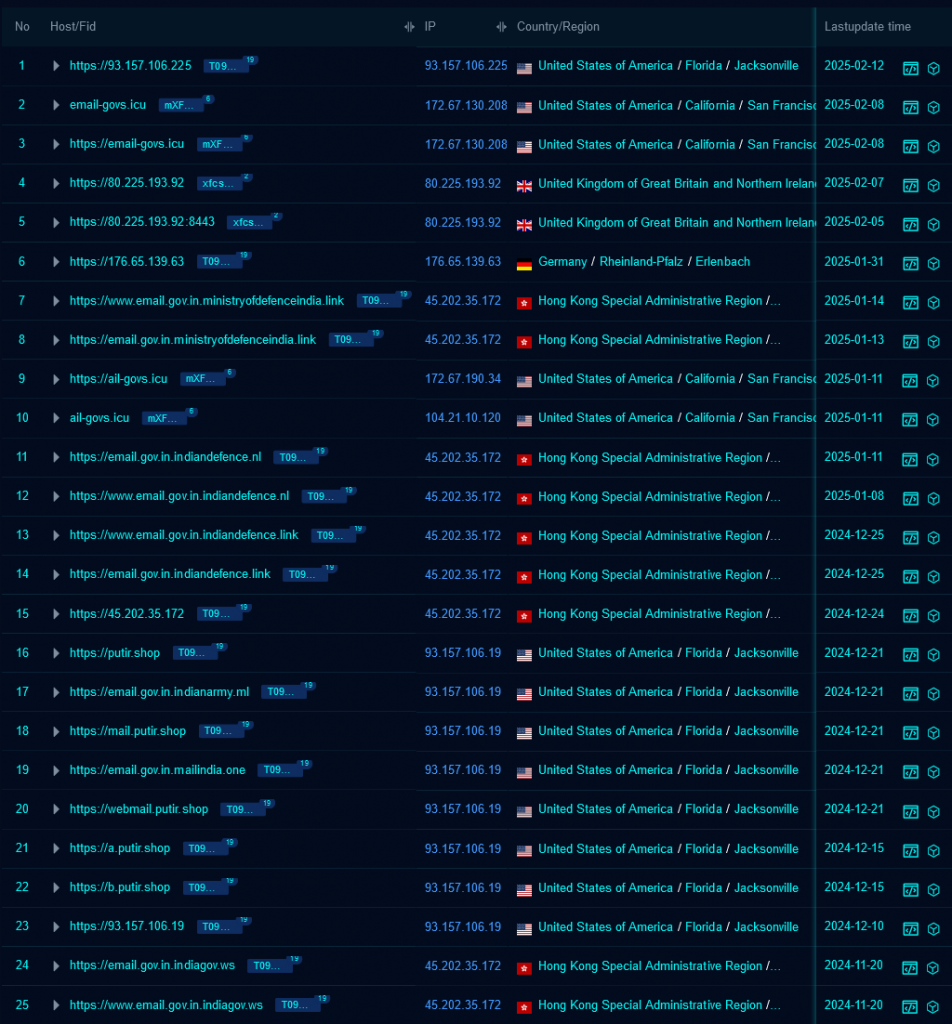
The data shown in the image below was obtained by applying the filter for the website title “Email Web Client Sign In” with the hosting country, not India.
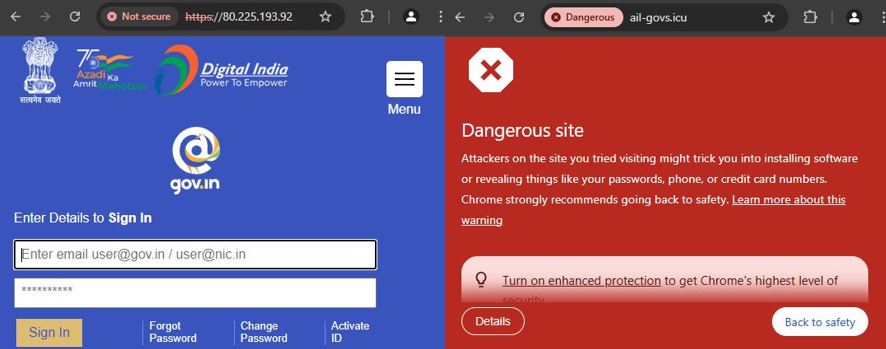
Phishing-based traps have become more and more sophisticated of late, making it difficult for users to discern. Netizens should be cautious of the links they are clicking and do some basic checks to make sure they are being redirected to the right channel. They should also be cautious of the data that they are revealing and should discern if such information is definitely needed for their query to be solved. Cybersecurity awareness and having a reputed malicious website blocker such as “K7 Total Security” can help users stay protected from such online scams.
References
- https://x.com/500mk500/status/1887282887331901851
- https://x.com/Cyberteam008/status/1881174353376874861
- https://github.com/stamparm/maltrail/blob/master/trails/static/malware/apt_transparenttribe.txt








