Criminal activities using the Internet’s underworld as a source have increased manifold during recent times and have therefore garnered a lot of attention too. Cybercriminals use underground forums on the Dark Web to operate anonymously thereby not only posing a major threat to organizations and users alike but also equally to make it difficult to trace them. In this blog, we will be getting into the nuances of “Matiex”, a Keylogger which is being sold in the underground forums for the buyers to use it for their own advantage.

Apart from recording everything typed on the keyboard and recovering passwords like any other Keylogger, Matiex also has other features like 4 Delivery, Unicode keystroke, Startup & Installation, +60 Password Recoveries, Self Destruction & Remote, Multi Binder and more as shown in Figure 2, making it different from the other Keyloggers.
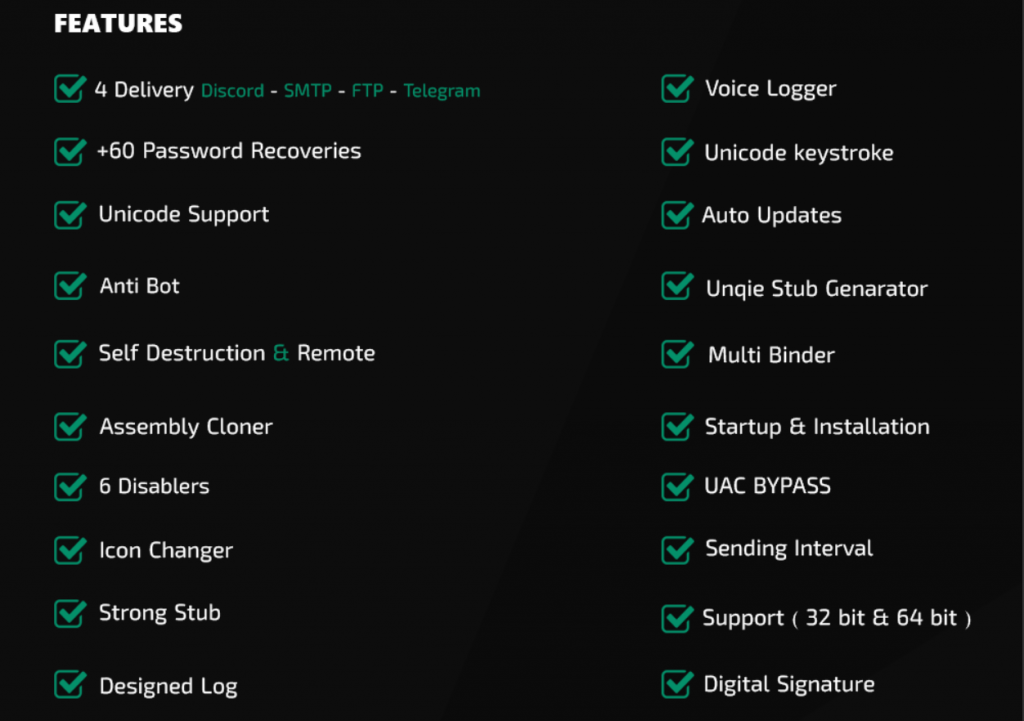
Let’s look into few of the features mentioned above
4 Delivery
The Keylogger offers 4 delivery methods – FTP, SMTP, Telegram or Discord, using which the logged data can be retrieved by the threat actors.
Unicode keystroke
Unlike ASCII which represents English characters, Unicodes are meant to support characters from different languages around the world. The Matiex Keylogger supports Unicode characters which makes it possible to record keystrokes that include characters from other languages.
Self Destruction & Remote
Another very important feature is Self Destruction & Remote. Keylogger has capabilities to upload information to a remote server from which confidential data can be retrieved anytime. Once the job is done and the threat actor’s goal is accomplished, the Keylogger can automatically uninstall itself with no clue left behind and the users will have no idea that their system has actually been monitored by a Keylogger.
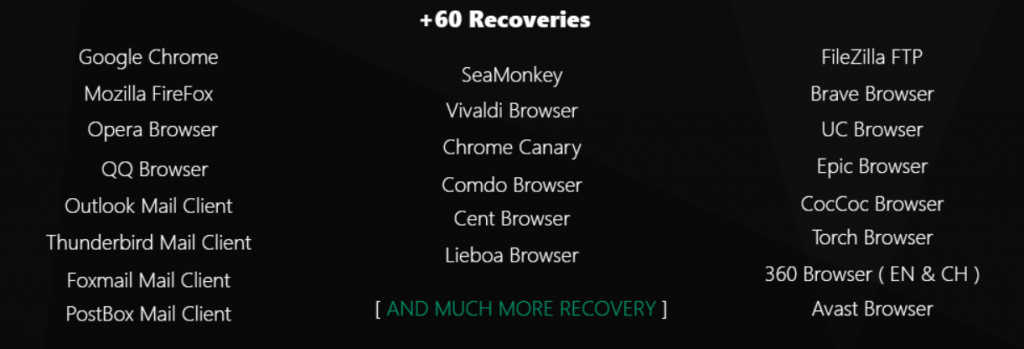
+60 Password Recoveries
This feature helps to recover confidential information like passwords and other sensitive information from more than 60 browsers that are supported as given in Figure 3.
Startup & Installation
Authors give threat actors the freedom to choose the installation process and startup. In other words, this is where this Keylogger can be customized for the convenience of each threat actor using it.
Multi Binder
With this feature, the threat actor has the ability to bind Matiex Keylogger with multiple files so that the Keylogger will run every time those files are opened without the user being aware of its presence. In this way this Keylogger can monitor the system for multiple documents.
Authors of the Keylogger also have their own Terms of service (TOS) and packages that provide limited voucher copies as shown in Figure 4.
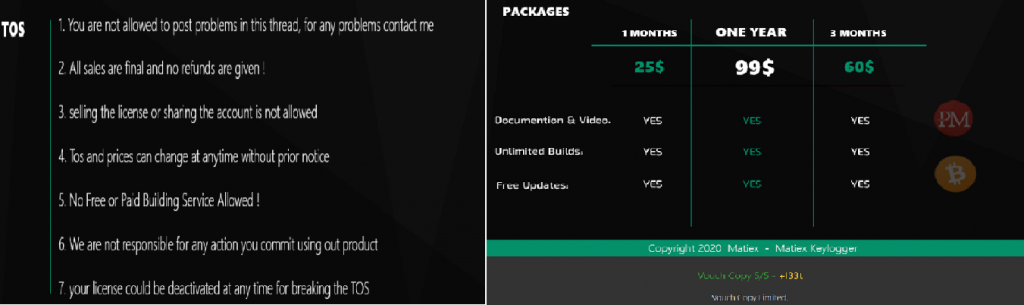
They allow their buyers, “threat actors”, to contact them through Skype with the contact details given below.
Delivery
On further analysis, we found that the Indicators of Compromise (IoCs) were mostly .NET files. The mode of delivery is through spam emails where users will be easily tricked to open the attachment which delivers the payload. Now let’s reverse a .NET file which was extracted from a legitimate looking zip file “window-defender-update.zip” with dnSpy to see some of the prominent features that this Matiex Keylogger promises to offer which attracts the threat actors towards it.
The people involved in distributing this malware have included the “MATIEX” string in it as shown in Figure 6.
KeyboardLoggerTimer
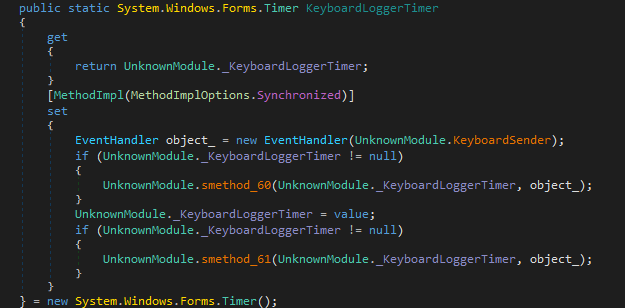
This KeyboardLoggerTimer is the basic feature that all the Keyloggers have. This is used by the malware to record any interaction with the keyboard without the victim’s knowledge.
ScreenshotLoggerTimer
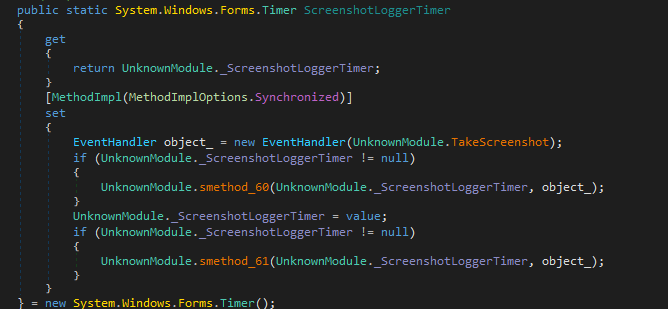
Another important feature is the ScreenshotLoggerTimer which can take screenshots of your system automatically at specified time intervals. The screenshots are stored as low resolution images so that they consume less storage at rest and less bandwidth during transmission. In Matiex Keylogger, the frequency of screenshots can be adjusted by the attacker to one photo per minute or a time interval more than that.
ClipboardLoggerTimer
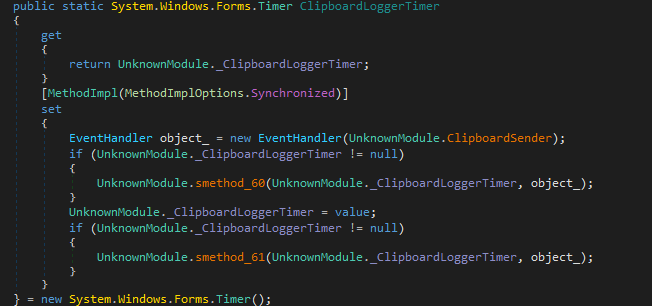
The Clipboard is a buffer which is used to store any changes made during a cut, copy and paste operation in the system. The ClipboardLoggerTimer in Matiex Keylogger is one of the key features as important pieces of information such as complex login credentials are copied and pasted in registration forms, login pages and using this feature confidential information can be retrieved from the victim’s system.
VoiceRecordLogger
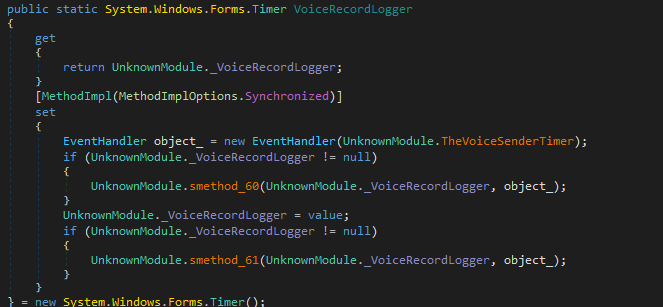
VoiceRecordLogger is another very important feature of Matiex Keylogger as it can record conversations via the computer’s microphone.
ThePSWDSenders
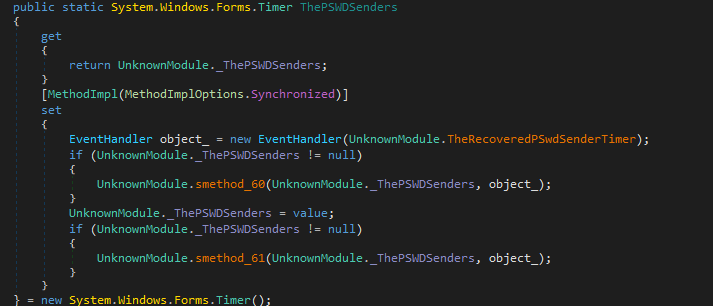
Keyloggers will usually save information like username, passwords, bank credentials, applications opened and websites visited. All these data will be encrypted and uploaded to the remote, attacker controlled servers via FTP, HTTP or Email. ThePSWDSenders feature is used to send all this information to the threat actors.
AddToStartup
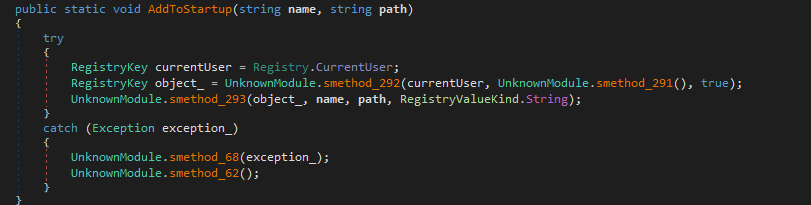
This Keylogger also has the feature of adding itself to the Windows Startup to maintain persistence and keep doing its job even after reboot. This is done using the AddToStartup feature.
telegramsender
This Keylogger has another feature of stealing information through Telegram. Telegram being a popular chat application, threat actors can use its legitimacy to steal information with ease.
IPLogger
Using the IPLogger feature, the threat actors obtain the victim’s IP.
Conclusion
Matiex Keylogger is being sold in the underground forums, due to their gained popularity, and can also be used as MaaS (Malware-as-a-service) because of their ease of use, competitive pricing and immediate response from support. We at K7 Labs keep monitoring underground forums as well and give early detection to protect customers from being victims to the attackers.
Indicators of Compromise (IoCs)
| Hash | Filename | K7 Detection Name |
| 5521B99B3FDDFD85D4E3DEECD76CA528(file analyzed) | Q.exe | Spyware ( 004bf6371 ) |
| 376944ae1de8e4181797668fb81022da | window-defender-update.zip | Spyware ( 004bf6371 ) |
| 6186934D6EBCBD2761413698113233CF | iOpEx.exe | Trojan ( 0056ae001 ) |
| BD6F2EF0D491D749705CFE12CD8BABE6 | BwJzCRNDwH.exe | Trojan ( 0056af741 ) |