Mobile apps these days, by default, are meant to be updated to be in line with the latest trend. Be it a mobile’s app or software update or even the latest news update, “Notifications” play a major role.
In this blog, we are going to talk about how hackers are taking advantage of users’ mentality to be up-to-date by promising fake updates that spread via notification reply.
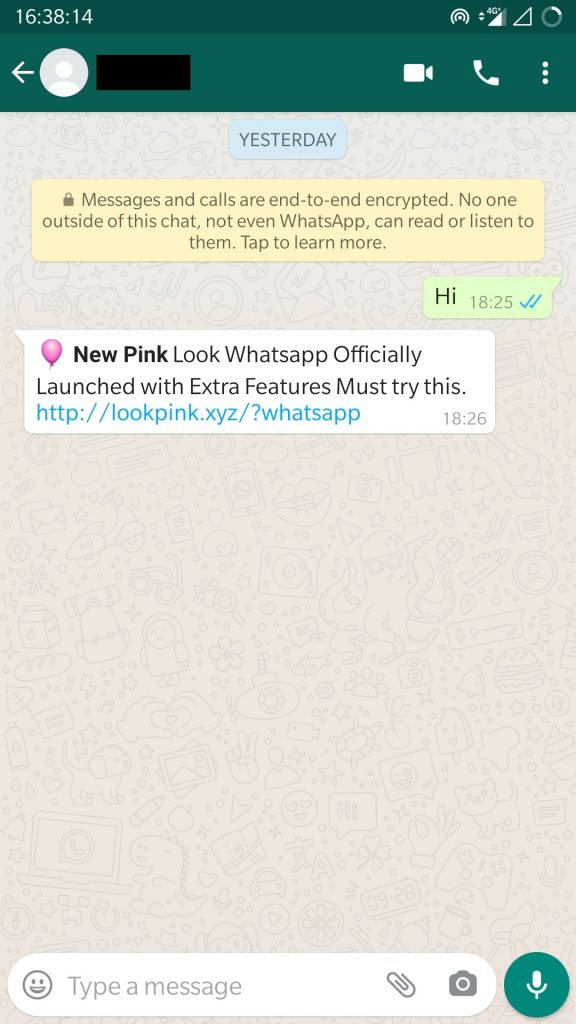
One of my colleagues received a message as shown in Figure 1 from a friend stating “New Pink Look Whatsapp Officially Launched with Extra Features Must try this. hxxp[://lookpink.xyz/?whatsapp”. Upon clicking the link, WhatsappPink.apk is downloaded.
Installing the downloaded APK didn’t show any visible suspicious behaviour, but analysing the app statically showed that the app looks for notifications from a predefined list of applications, including Viber, Telegram, WhatsApp, Skype etc., and auto responds to the sender with the reply “New Pink Look Whatsapp Officially Launched with Extra Features Must try this. hxxp[://lookpink.xyz/?whatsapp” for them to download the app, spreading like a worm. Unfortunately the link in the message was down at the time of writing this blog.
The predefined list of chat apps is as shown in Figure 2.

Chat apps in the list are:
- com.viber.voip
- com.skype.raider
- com.skype.insiders
- org.thoughtcrime.securesms
- com.whatsapp.w4b
- com.whatsapp
- org.telegram.messenger
- com.gbwhatsapp
- com.whatsapp.plus
- com.og.whatsapp
- com.yowhatsapp
- com.retro.whatsweb
- com.FmWhatsApp
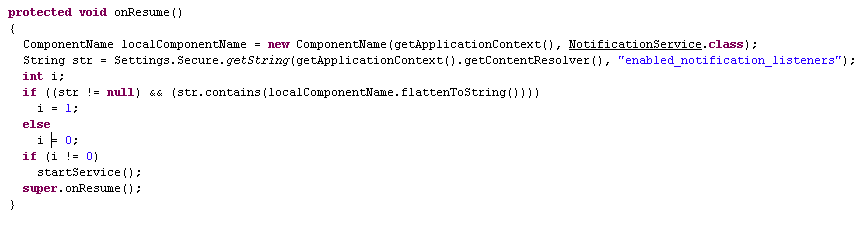
Also the app confirms if it has the permission to listen to the notifications by either verifying if it is listed under “enabled_notification_listeners” or by requesting for the permission as shown in Figure 3 and Figure 4.
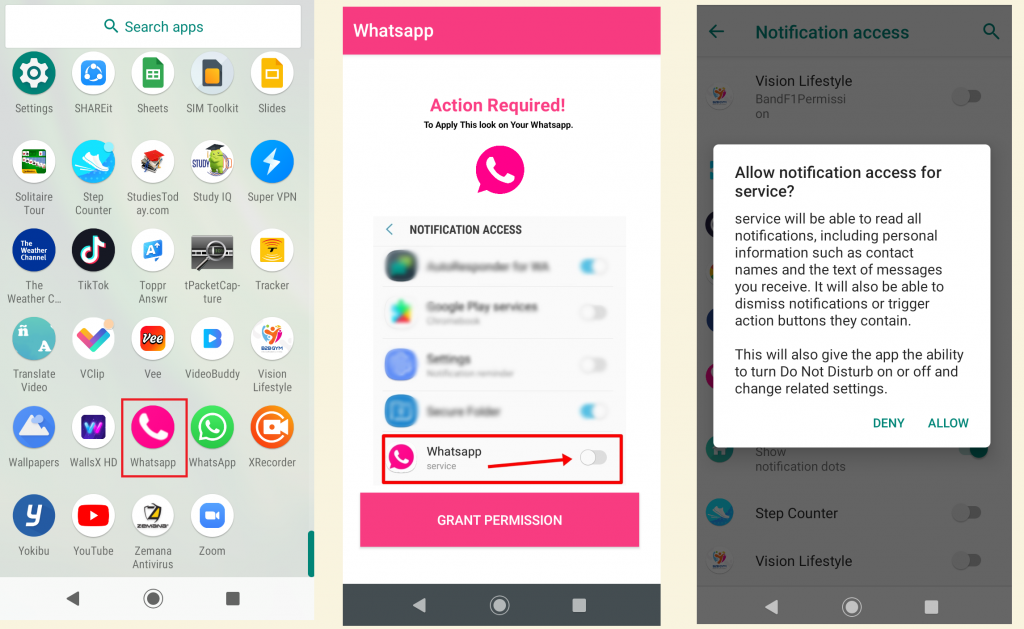
Once the service is listed under notification listeners, the service starts and keeps monitoring for any posted notification. If any notification is posted, this app verifies if the notification is meant for any of the apps in the predefined list. If yes, it collects the phone number as shown in Figure 5.
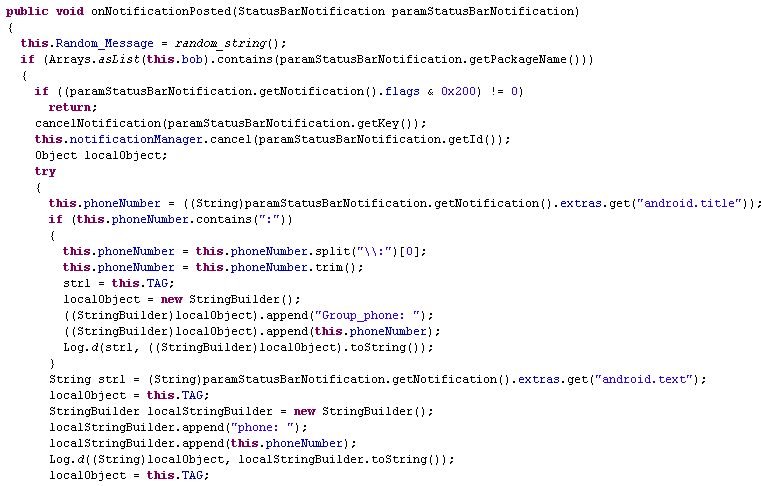
After which it auto responds to the phone number using sendReply as shown in Figure 6.
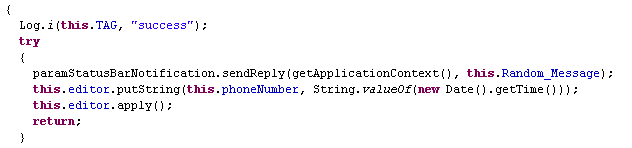
Random_Message is the string variable that carries the message and the link to download malicious Whatsapp app.
Also, we noted that the malware author has not suppressed notifications or messages from those chat apps. Instead the spam message auto sent via notifications is visible to the user in the chat message screen of the sender. This suggests that the app could still be under the development stage or just a start of an attack as the app just auto replies to the notifications and no other malicious activities have been identified at the time of writing this blog.
This attack may not sound new, however, users are falling prey to such attacks because of curiosity and eagerness to be trendy at the earliest. We strongly recommend users to refrain from believing in such messages and stay away from such attacks by downloading apps only from trusted Google Play Store. Also install K7 Mobile Security for Android to stay protected against such attacks.
Indicators Of Compromise (IOCs)
| File Name | Hash | K7 Detection Name |
| WhatsappPInk.apk | 9a902d186c948e72af6b269862c27055 | Trojan ( 0057b1c11 ) |
| WhatsappPInk.apk | e1870d613d54239e8fb5f09b6a4e880d | Trojan ( 0057b20e1 ) |
| WhatsappPInk.apk | 90cfcde60b6cd57a2e9b2047cff51fb7 | Trojan ( 0057b20e1 ) |
URLs
hxxp[://lookpink.xyz/?whatsapp
hxxp[://whatsapp.profileviewz.com/?whatsapp
hxxp[://whatsapp.wwwy.xyz/?pinklook