In this man-eat-man world, threat actors don’t want to be left behind in the rat race; they wish to make the most out of the crisis situation owing to the COVID-19 pandemic. Each one of them is trying to use different attack models to prove their mettle and to trap innocent victims; they employ even the not-so-complicated and old attacks and have been successful at it. This blog is about SMiShing or SMS Phishing, a prevalent threat vector which has increased during this pandemic crisis and in specific about threats which originated within India and targeting Indian users.
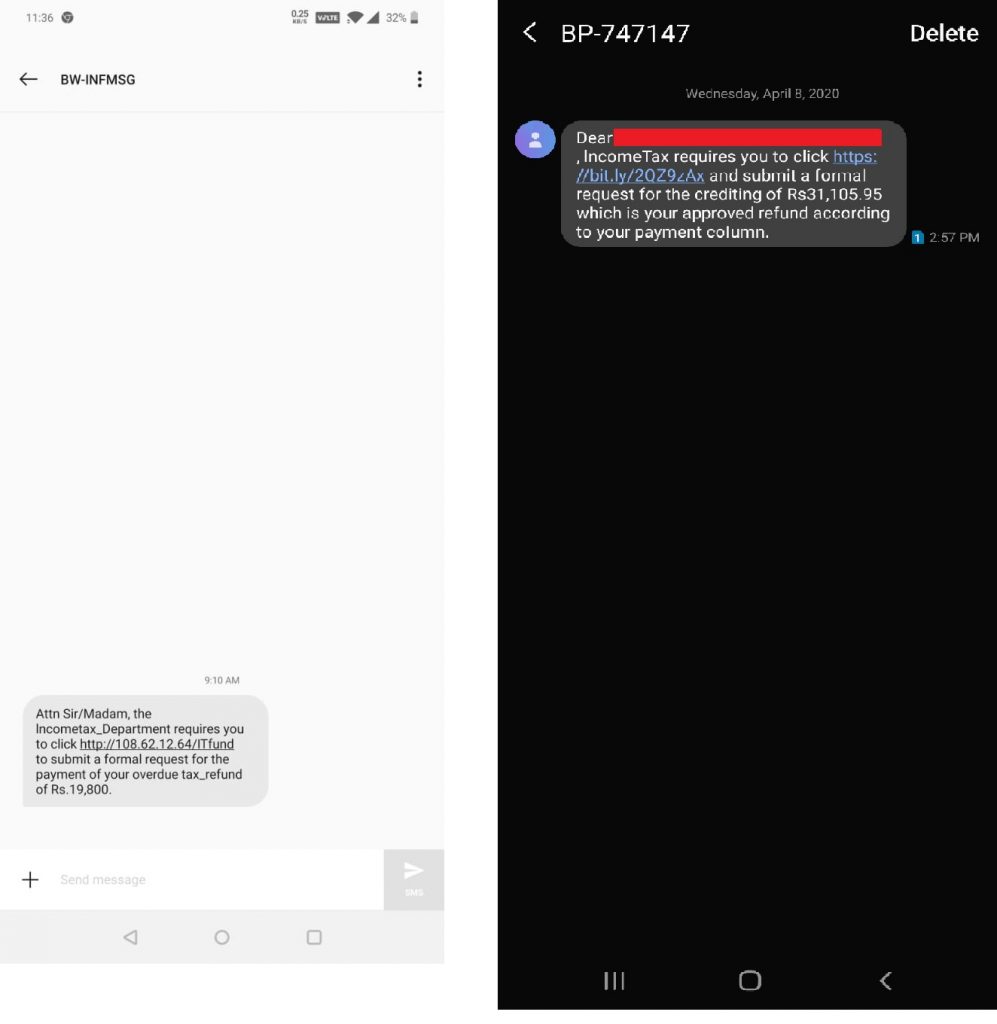
Recently, one of our colleagues received a text message masquerading to be from the Income Tax Department of India. However, the sender’s address read “BW-INFMSG” and the message read “Attn Sir/Madam, the Incometax_Department requires you to click “hxxp[:]//108.62.12.64/ITfund to submit a formal request for the payment of your overdue tax_refund of Rs.19,800” as shown in Figure 1 (with few example text messages) below.
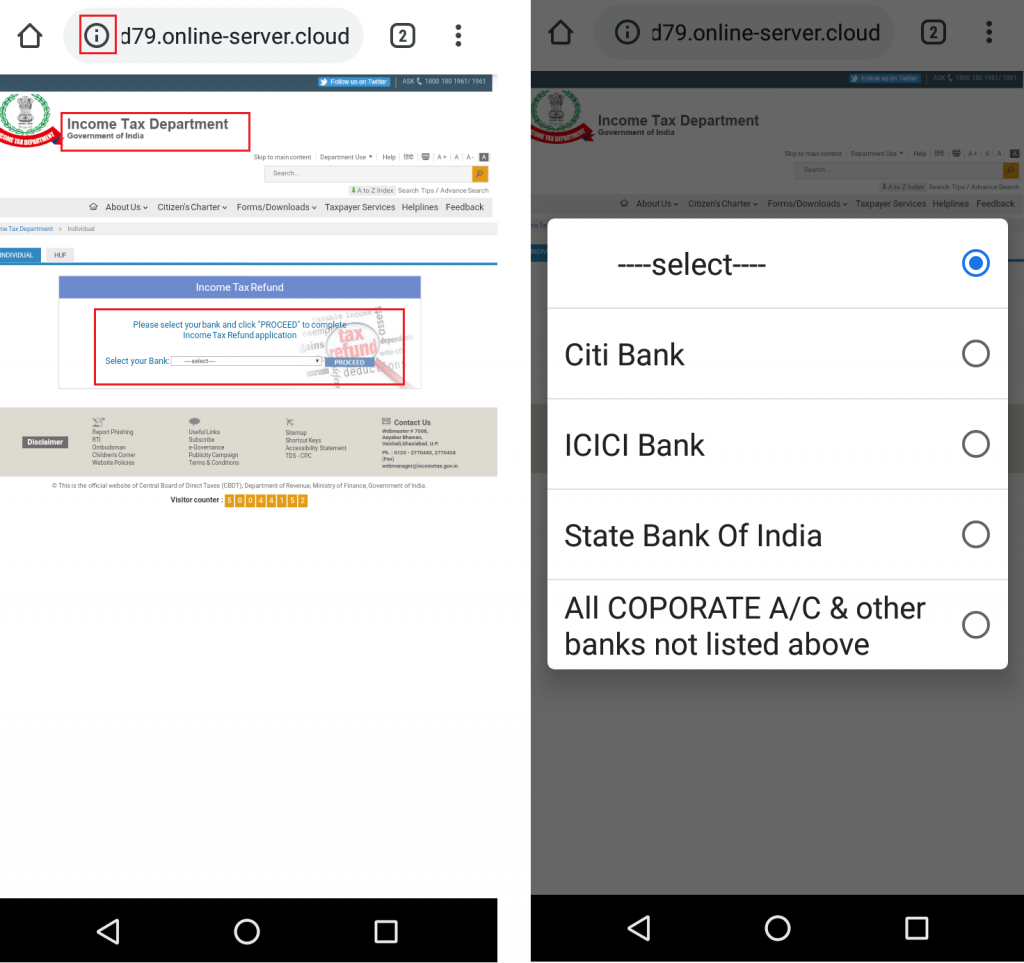
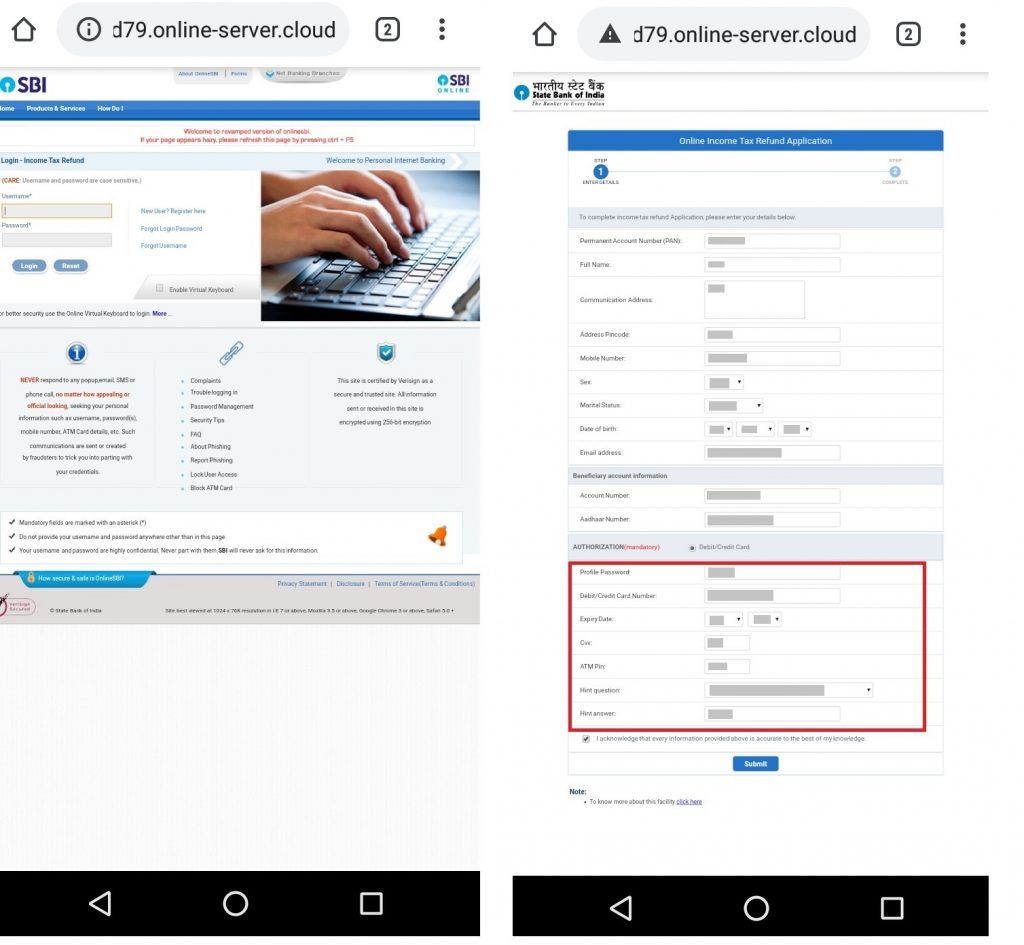
Upon clicking the link “hxxp[:]//108.62.12.64/ITfund”, it redirects the user to “hxxp[:]//f789d79.online-server.cloud/wp-content/1331213445/y9a38.php?RefundStatus=APPROVED&id=YWJjQDEyMy5jb20%3D” that appears to be a phishing page of the Income Tax Department of India as shown in Figure 2 below.
It is to be noted that these redirected URLs are not related to the legitimate Income Tax Department links and the URLs themselves do not include any term related to the Income Tax Department except the term “RefundStatus” which could refer to any refund. Few other URLs that are used in this campaign for redirection are listed below:
hxxp[:]//156.96.46.126/1292851528/1b6.php?RefundStatus=APPROVED&id=YWJjQDEyMy5jb20%3D hxxp[:]//54.38.120.210/2007779141/rxmc3yqn.php?RefundStatus=APPROVED&id=YWJjQDEyMy5jb20%3D hxxp[:]//107.172.57.12/1193980529/sdpz08u1.php?RefundStatus=APPROVED&id=YWJjQDEyMy5jb20%3D hxxp[:]//107.172.57.12/222605496/w2d71bc.php?RefundStatus=APPROVED&id=YWJjQDEyMy5jb20%3D
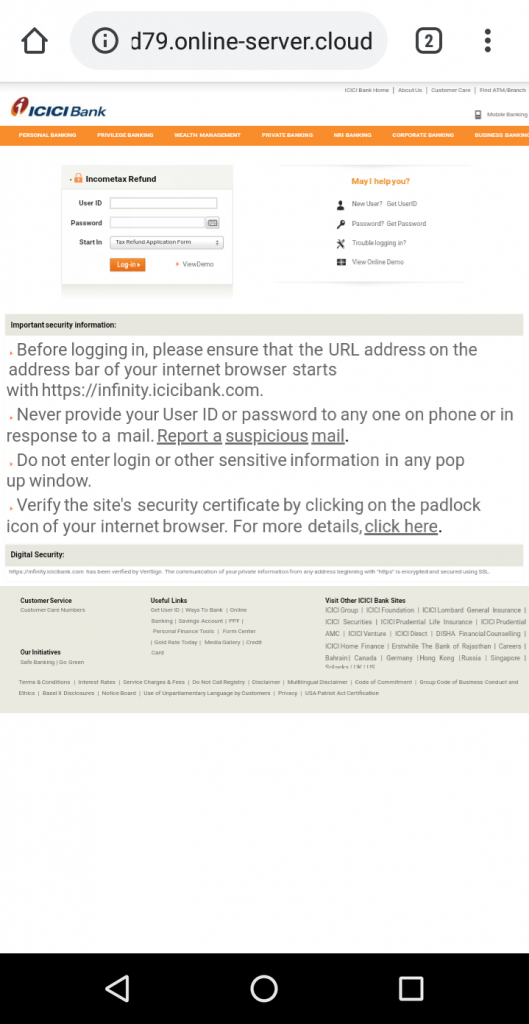
Taking a closer look at Figure 2, it can be seen that the redirected URL is not secure i.e., “http://”. We strictly recommend users to verify the lock symbol in the address bar that represents “https://”; to establish a secure connection to the bank’s server and carry out a safe transaction.
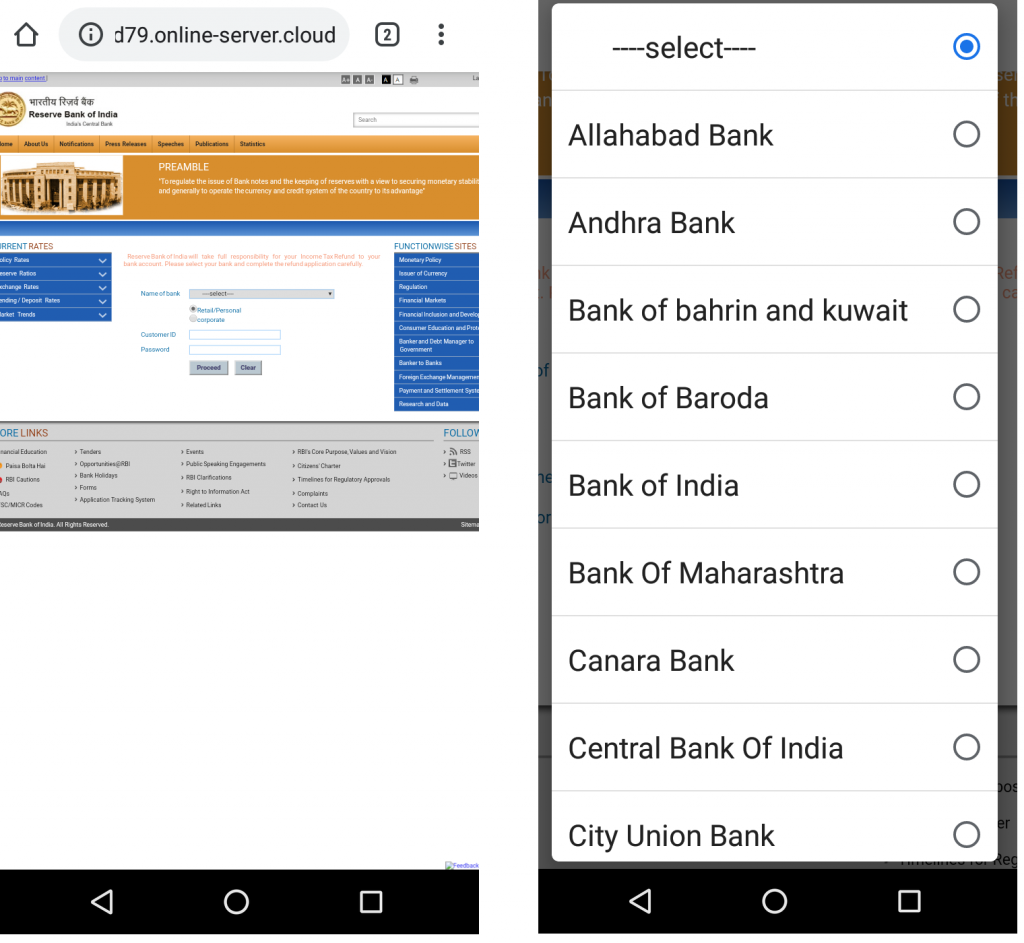
Once the user selects a bank from the default list, the victim is prompted to enter the User ID and password for the selected bank as shown in Figure 3. In case, the victim opts to select a bank that is not listed in the default list, it redirects the victim to a fake page as shown in Figure 4. In our case, State Bank of India (SBI) was chosen as a test case from non-default banks list.
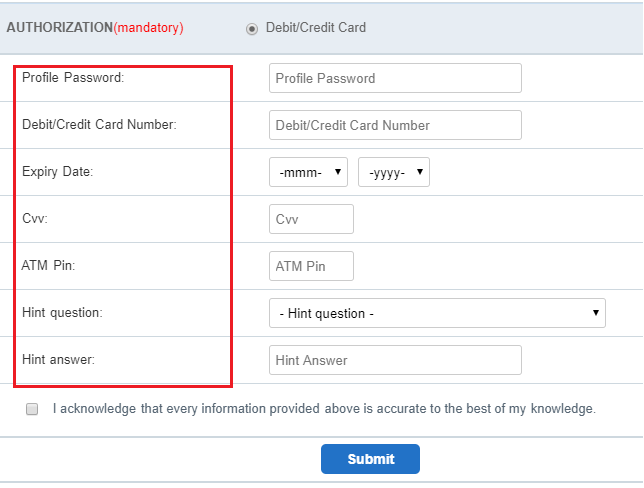
Interestingly, when the user selects any bank, the redirected URL never changes and it just loads the HTML page (URL does not contain any term related to the bank) according to the selected bank. Here again, the victim is asked to enter more personal and sensitive information as shown in Figure 5A.
Figure 5B clearly depicts that the author has asked for all the information related to the selected bank’s online transaction like ATM Pin, CVV, Expiry date of card, etc. Also, for each of the banks listed, all of the specific information related to that bank’s online transaction are also collected. For example, if ICICI bank is selected, the fraudsters even collect all the grid numbers in the victim’s debit card. It is to be noted that these phishing pages do not have any validation for the fields entered by the victim as it accepts any value for a field.
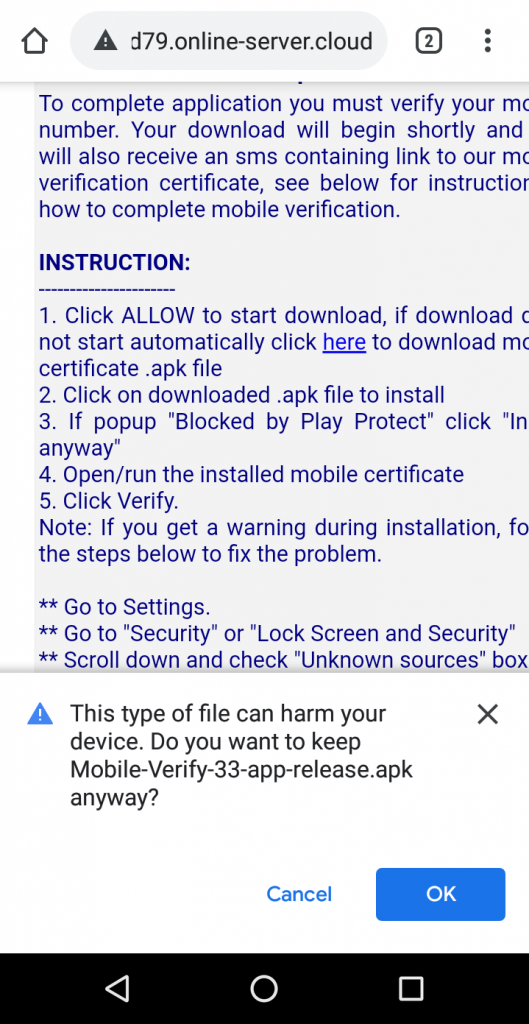
Once the victim completes the process and clicks on “Submit”, the victim is taken to a web page as shown in Figure 6 and recommended to install an APK. Hackers here successfully complete the first step, which is collecting the banking credentials of the victim. In Figure 6, the downloaded app name has been changed to “Mobile-Verify-33-app-release.apk” at the time of writing this blog.
Eager to receive the Income Tax refund which could be an additional monetary benefit in this tough period, let’s see what happens when the victim installs the downloaded apk.
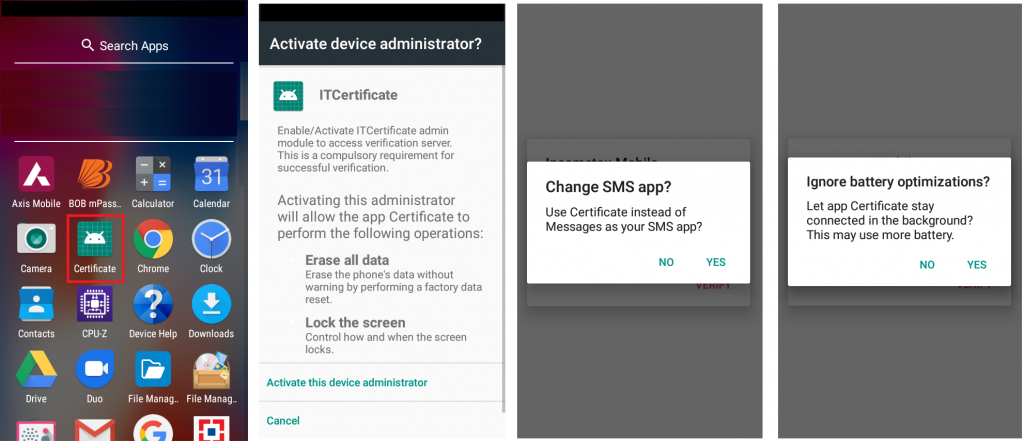
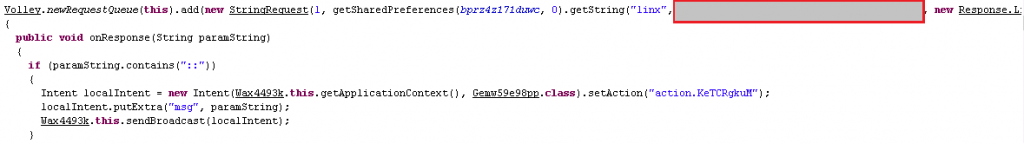
This app installs in the name of “Certificate” and requests for certain permissions: “REQUEST_IGNORE_BATTERY_OPTIMIZATIONS” to stay stealthy. This permission when enabled does not show the apk in the notification bar. This app also requests user’s permission to be the default SMS app and SMS permissions such as to send and receive SMS without any obstruction and without the user’s knowledge as shown in Figure 7.
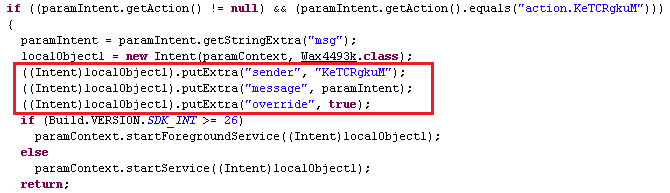
It then registers a broadcast receiver for “android.provider.telephony.SMS_RECEIVED” with “priority: 999”. Hence, whenever the hacker logs in with the victims’ stolen banking credentials and carries out a transaction remotely with this registered broadcast receiver; being the default SMS app, this app silently forwards the OTP message to the hacker without any noise and hides the SMS broadcast from the victim’s knowledge and the victim would not even know of an online banking transaction going on in their banking account.
This app also checks for the subscription information of the currently active SIM(s) as shown in Figure 8.
Also this app checks for the devices’ admin status and collects the device model as shown in Figure 9.
Upon digging further into the application, it is observed that this app accesses the URL “hxxp[:]//f**.*****n[.]org/**/B***5/mc.php” registered in the ip address “*1*.***.***.**4” as shown in Figure 10.
The user information that was harvested like email address, device model, device admin status are forwarded to the above accessed URL “hxxp[:]//f**.*****n[.]org/**/B***5/mc.php” as shown in Figure 11.
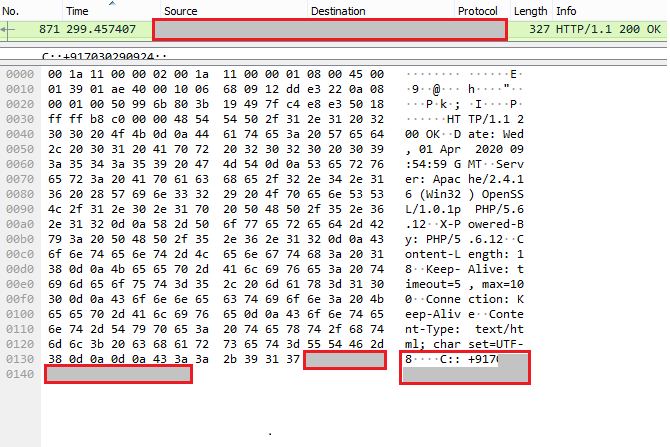
Looking at the network traffic, the response from the URL contains the string “C::+917*********” as shown in Figure 12.
Though the phone number “+917*********” from Figure 12 had no transaction so far with the victims’ device, the app is under vigilance for any malicious activity with that phone number. URL response along with the app’s signer certificate itr556.apk, hinted us about the hacker that the author of this app is from India.
Signer name: Prakash
Country: India
Also based on the response from the URL accessed as shown in Figure 10, the same service is initiated to retrieve the same users’ information like email address, device info as shown in Figure 13 at regular intervals.
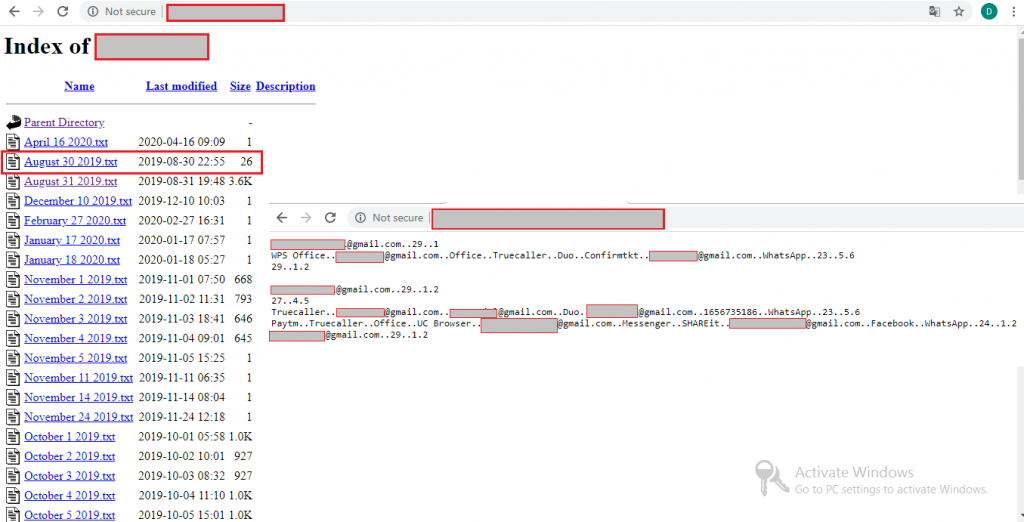
From the phishing page and the banks targeted, it goes without saying that the hackers’ targets are within India and on further investigation we can see that the poorly managed ip address *1*.**.***.**4 contains many text files named after dates along with few other text files. These text files contain the victims’ information that were collected so far as shown in Figure 14.
From the server details seen in Figure 14 this attack has been in live since August 30, 2019 and we at K7 Labs are constantly monitoring this and such phishing campaigns. Though phishing attacks sound old and quite familiar, consequences of these attacks have serious monetary impacts and are still dangerous. K7 Mobile security users are protected against such malware.
Smartphone users must be geared to handle such unhealthy scenarios by following the best practices of downloading apps only from the official Google Play Store, avoid believing in such scams and not installing any app from any external sources.
Indicators of Compromise (IoCs)
| Package Name | Hash | Detection Name |
| Itr556.apk | 6482f67d627545bfb4b20623706149b9 | Trojan ( 00563b2d1 ) |
| Itr835.apk | E9B540ECAB33CFF1B1D60ECBDAF52574 | Trojan ( 0056439b1 ) |
| Mobile-Verify-22-app-release.apk | D9AD281DD9CD044A8F6DC6D2E9638F3A | Trojan ( 005643891 ) |
| Mobile-Verify-22-app-release.apk | 61CC5BA926D589E3171414926BAFF6D2 | Trojan ( 005643891 ) |
| Mobile-Verify-33-app-release.apk | 33D5382ED0183194FA0C42D59EBB61DF | Trojan ( 005643891 ) |