The current unpatched Microsoft Internet Explorer (6 && 7 && 8 && 9) vulnerability was being actively exploited in the wild even before it was assigned a CVE. 0-day indeed. Microsoft is due to release an Out-Of-Band patch for this exploit shortly, but unfortunately some damage has already been done via targeted attacks currently emanating from China. All of this follows in the wake of the Java vulnerability written about recently.
As MAPP partners we were privy to extra information from Microsoft about how to go about detecting attempts to exploit the vulnerability. However it turns out that the Carnivore technology embedded in K7 security products already blocked any attempt to exploit this vulnerability, as it did in the Java vulnerability case a few weeks back.
Here is an attempt to exploit the currently unpatched Use-After-Free Internet Explorer vulnerability:
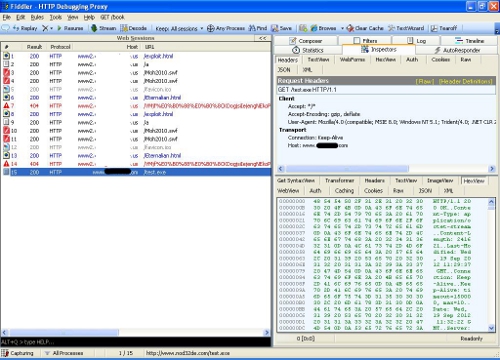
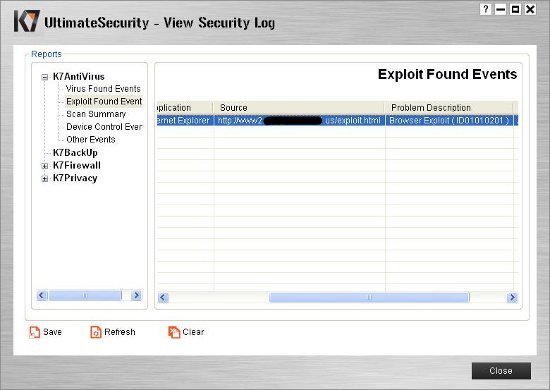
No patches were required, no HTML/JavaScript heuristic detection, no nothing. Note, that is not to say that you do not need to install patches. Please install the patches, especially OS-related ones, as soon as possible.
Targeted attacks are becoming more and more prevalent, and a common feature of these is the use of exploits, some of them ‘0-day’, to deliver the malicious payloads. Carnivore provides an early warning and blocking safety mechanism whether the modus operandi involves a browser, a document, or something else in the future. Carnivore may not be perfect, but it certainly is a powerful maintainer of border security.
Samir Mody
Senior Manager, K7TCL
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed







