The Nuclear Power Corporation of India recently issued a statement acknowledging a security breach within the Kudankulam Nuclear Power Plant. As per the press release, none of the critical infrastructure was affected and the attack was restricted to terminals used for administrative purposes. Prior to the press release, the news media reported this incident based on tweets made by two cyber security analysts. One of the analysts shared the Virustotal link to a sample, allegedly related to the security breach. The analyst shared some artefacts of the malware which associated it to the power plant. In this blog we present a technical analysis of this malware.
Based on certain artefacts embedded in the malware, covered later in the blog, we found it to be associated with a RAT (Remote Access Trojan) that is popularly known as Dtrack. This malware is from the arsenal of the infamous Lazarus APT group believed to be North Korean. Prior to this breach, the group was held responsible for a massive campaign targeting financial institutions and ATMs across the Indian sub-continent using Dtrack malware. The standard Dtrack malware has a variety of functionalities for reconnaissance, key logging, gathering network information and other data exfiltration, with anti-analysis techniques and a highly obfuscated payload. The Dtrack malware mentioned in the tweets regarding the Kudankulam Nuclear Power Plant has similar functionalities to the ones mentioned above, but lacks the sophistication, meaning it does not have any complex anti-analysis techniques or code obfuscation. Perhaps it was never expected to have been discovered.
The malware starts with a simple anti-sandboxing technique with a 10 second execution delay. The file contains many hardcoded API and DLL name strings prepended with “CCS_” as shown in Figure 1. We had witnessed the same artefact before associated with Dtrack malware.
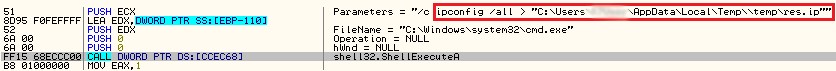
The malware collects information from the victim’s machine using the following OS commands and stores the output as separate files in a temporary folder.
- ipconfig /all
- tasklist
- netstat –naop tcp
- netsh interface ip show config
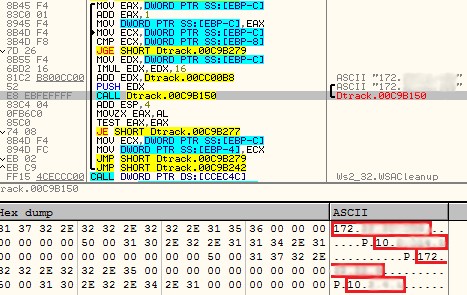
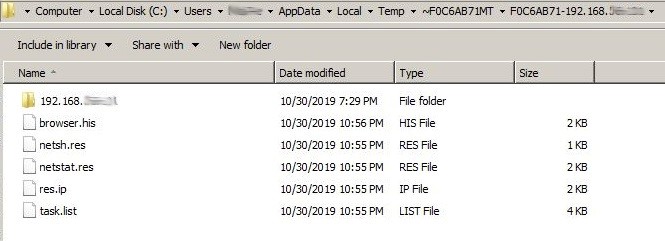
The malware tries to connect to 4 internal IP addresses from the victim’s machine as shown in figure 3. If the connection is established the results are stored in the file “browser.his”. This might be used to map the victim’s network setup or they are trying to find a way to connect to these machines.
The malware collects the victim’s browser history for Chrome and Firefox and stores it in the same file “browser.his” as shown in Figure 4.
A code snippet from the malware depicting the collection of browser history from Chrome and Firefox is shown in Figure 5.
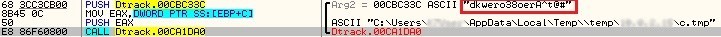
The malware then collects information on all the files on the system. For each file the filename, size and last modified date are stored. This information is collected for all the drives mapped on the victim’s PC. Each of these data files is compressed/archived and password protected using the password shown in Figure 6.
There are files created for every available drive on the system as shown in Figure 7. Once all drive information is collected, the files created until now are zipped with the password “abcd@123”.
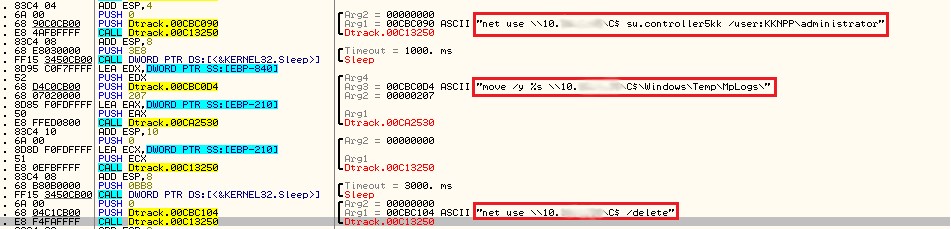
Now, a network share on an internal IP is mapped to the victim’s machine as shown in Figure 8. We could see the user name “KKNPP\administrator” is hardcoded in the file. This is one of the main artefacts that was used to associate this malware with the Kudankulam Nuclear Power Plant (KKNPP).
The archive file is moved to a fixed location and then the mapped share is released as shown in Figure 8.
The malware process is terminated after deleting the mapped share. The malware contains hardcoded IP addresses, shown in Figures 8 and 3, that are internal. The malware seems to be tailor-made for a specific infrastructure. This implies that the hackers must have already established a foothold within the victim’s network before deploying the malware.
Currently we have analyzed only the file that was shared via twitter allegedly related to the Kudankulam Nuclear Power Plant breach. The complete scope of the infection would require auditing the infected systems. We intend to give further analysis of the incident as and when more information about the breach becomes available.
Indicators of Compromise:
4F8091A5513659B2980CB53578D3F798 Spyware ( 0055a5f71 )