ESXiArgs Ransomware targeting exposed ESXi servers has been making headlines since the start of Feb 2023. VMWare has also requested their customers to upgrade ESXi servers to the latest version. In this blog, we will briefly discuss details of the ongoing cyber attacks.
ESXiArgs Ransomware has been reported to be exploiting CVE-2021-21974. In Feb 2021, VMWare patched [2] CVE-2021-21974 in multiple versions of ESXi and Cloud Foundation servers.
Vulnerable ESXi Version 6.5, 6.7 and 7.0
Vulnerable Cloud Foundation Versions 3.x, 4.x
Service Location Protocol (SLP) is a protocol which allows devices to discover other services and devices in the network they are connected to. It works on port 427.
CVE-2021-21974 is a heap overflow vulnerability in the SLP implementation of VMWare resulting in Remote Code Execution. The vulnerability exists in the SLPParseSrvUrl() function.
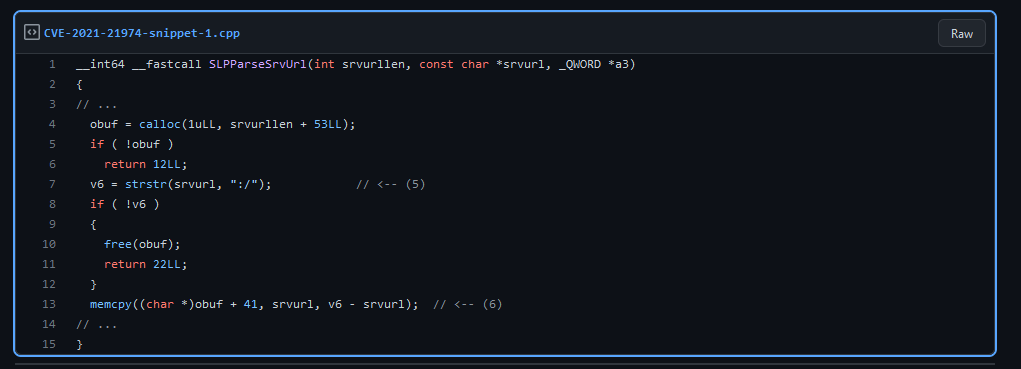
Recommendations
- Keep your ESXi servers patched and up-to-date
- Block port 427 if SLP service is not required
Are you a Victim?
CISA has released this script to help decrypt files which might be helpful.






