This is the seventh part of our series on cyber security, and the second part on Digital Signing. This blog post aims to inform readers about the misuse and exploitation of digital signatures.
The previous installment on Digital Signing discussed the security role of digital signatures in today’s era of internet communication and computerisation. Though designed for authentication and tamper-proofing of digital content, digital signatures and certificates are also exploited and misused to a fair extent.
Consider the case of Stuxnet (2010) wherein the device drivers of the rootkit component were digitally signed, and were actually loaded without any notification on infected systems. These drivers were signed by certificates which were actually stolen, and which were ultimately revoked by the CA which issued them.
The signed malware trend has been on the rise since then. To give some insight on the scale of the issue, let us consider a scenario in our own K7TCL. We pulled out data that represents the total number of malware signatures released over certain discrete chunks of time.
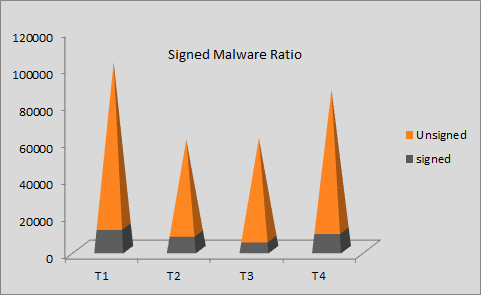
Graph 1: Ratio between signed malware and unsigned malware
The above graph depicts that on average at least one-tenth of automated detections released are for files carrying a valid digital signature. The signing certificates could either have been stolen or legitimately acquired for mala fide purposes. Unwanted Programs/Applications/Adware are examples of those that use “legitimately acquired” certificates. It is widely acknowledged that the Potentially Unwanted Programs (PUP)/Potentially Unwanted Applications (PUA) have been posing a serious problem in the AV community for some time.
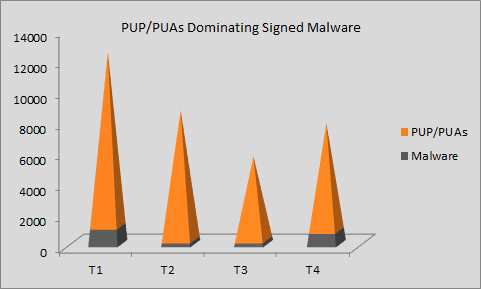
To understand this better we further refined our stats data and found that it is PUP/PUAs that dominate the number of digitally-signed-file detections at more than 90%.
Graph 2: Ratio between signed PUP/PUAs and signed malware
These PUP/PUAs can more easily circumvent the security policies of recent versions of Windows that restrict unsigned executables from loading into memory. Thus digital signatures, though they make it possible to keep tabs on what gets executed, they can also lend themselves to nagging PUP/PUAs. There has been a huge increase in signed PUP/PUAs over the past couple of years, indicating a potential dilemma faced by CAs. This is apart from the very serious issues that are caused by malware authors signing their creations with paid-up, as well as stolen, digital certificates. Thus the automatic trust factor associated with digital signatures is being eroded on a daily basis.
The CAs also feel the heat since they are required to revoke or blacklist certificates that have been misused. CAs update what is called a Certificate Revocation List (CRL), wherein revoked certificates are published on a regular basis, but the CRL method had its own shortcomings. Hence Online Certificate Status Protocol (OCSP) was deployed, such that it overcame the difficulties that the CRL scheme had with respect to PKI standards.
Nevertheless, Digital Signing, plays a major role in securing digital content, despite the above-described shortcomings.
K7 Threat Control Lab
If you wish to subscribe to our blog, please add the URL provided below to your blog reader: https://labs.k7computing.com/feed/