Much has already been written about Win32/Poweliks, the touted fileless persistent malware.
The malware uses an embedded NUL within the key under the following registry path:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
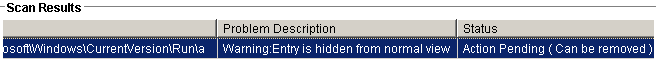
This non-standard use of NUL as part of the key name is not new. A similar trick was likely used by variants of more advanced malware such as ZeroAccess, when creating helper files on disk. Regedit, a usermode process, is unable to read this keyname, but it doesn’t mean the entry is invisible. In fact K7’s rootkit scanner reveals the key with ease:
The other important point is that the infection chain involves a malicious Microsoft Office document containing a dropper Windows executable file, both of which must exist on disk as normal files, albeit ephemerally, and executed before the above-mentioned registry entry can be created. This provides a fleeting opportunity to detect these vital components easily, and detect them we do as
Trojan ( 0001140e1 )
and
Trojan ( 0049882d1 )
respectively.
The techniques used by the malware to execute a JS-decoded DLL via a registry entry are indeed interesting, but there are still quite a few opportunities to flag the infection at various stages of the infection chain, including at the entry spam email stage itself. It remains to be seen if the malware evolves to employ more sophisticated techniques in future.
Samir Mody
Senior Manager, K7TCL
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed