This is the fifth part of a six-part blog based on the paper submitted by my colleague Gregory and myself on Advanced Persistent Threats (APT), for AVAR 2014.
Continuing from the fourth part of our paper…
Expanding Access and Strengthening Foothold
The device that falls first is usually not the primary target of the APT. This backdoored computer is instead used as a base to search and compromise more devices that likely contain credentials to other workstations, application servers, etc. The assailants move laterally within the network, gaining access to these machines, strengthening their foothold, all the while hunting for valuable target information which was the objective of the attack.
Expansion Methodology
The initial infected host connects back to a command and control (C2C) infrastructure controlled by the bad actors. It sends critical information such as password details, privileges of the currently logged user, mapped drive information, etc. and awaits further instructions. The following techniques are used by the attackers to expand their access:
Privilege Escalation
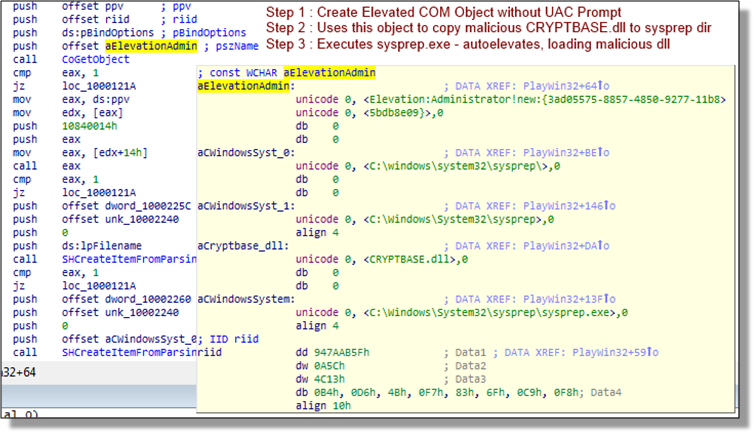
The attackers exploit privilege escalation vulnerabilities to escape the confines of a limited user’s account. The objective here is to gain “root” on the infected machine which enables them to perform tasks that require elevated privileges such as creating/deleting system services, accessing critical process’ memory space, mapping internal networks, etc.
Fig.13: Privilege escalation code used from the Council for Foreign Relations Watering Hole attack
Remote Exploitation
Malware components can exploit network vulnerabilities to compromise systems accessible in the local network. The Stuxnet malware exploited a 0day Print Spooler (CVE-2010-2729) remote code execution vulnerability to propagate itself into new machines.
Installing More Tools
During the initial compromise, the malware authors use custom zero-day code that exploits vulnerabilities in common applications. In the expansion stage of the APT though, to avoid having to re-write code, the bad actors tend to use standard tools.
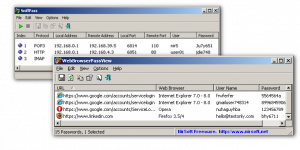
These tools could include system utilities like PsExec [9], network packet sniffers like tcpdump [10], password extracting tools like gsecdump [11], Cain&Abel [12], etc.
Obtain Credentials
With the help of the tools installed, the attackers brute-force login credentials to workstations and servers that likely contain sensitive data.
They could establish remote desktop sessions to these machines and eventually make their way onto domain controllers that have unrestricted access to the entire network. They then begin their hunt for the target data to be extracted, if they haven’t found it already, that is.
Indicators of Compromise
Once the assailants possess domain level credentials, their movement within the network resembles that of legitimate traffic and so becomes very difficult to track. The following behaviors on the other hand could indicate a compromise and are relatively easy to track:
Presence of Unwarranted Files
Unauthorized use of kernel modules to elevate ones privileges could imply a compromise. The presence of unapproved software, modified versions of existing drivers containing trojanized code, tools like port scanners, password crackers, network sniffers, etc. could also indicate a compromise.
Login Irregularities
Repeated failed login attempts using non-existent user accounts, successful login attempts to machines that deviate from established baseline logins, login activity at odd hours, etc. could mean something is amiss.
Anomalies in Security Settings
Unauthorized disabling of security software, tampering of exclusion lists in firewalls and Anti-Virus, even for a brief period of time, could indicate a compromise.
Anomalies in User Account Activity
Changes in behavior of a user account such as time of activity, type of information accessed, systems accessed, etc. could indicate a compromise.
Prevention/Detection
Along with multi-factor authentication for sensitive accounts, updated Anti-Virus software that detects unwanted tools, a strong password policy, etc. the following solutions can be implemented to augment the network’s security:
Unified Extensible Firmware Interface (UEFI) and Secure-Boot
Privilege escalation attempts can be significantly reduced by using UEFI/secure-boot enabled machines that provide a level of trust from boot-up time.
Early Launch Anti-Malware (ELAM)
Security solutions with early loading components that are capable of detecting and blocking unauthorized kernel code should be installed throughout the network.
Click here to read the final part of this blog
References:
[9] http://technet.microsoft.com/en-us/sysinternals/bb897553
[10] http://www.tcpdump.org
[11] http://www.truesec.com/Tools/Tool/gsecdump_v2.0b5
[12] http://www.oxid.it/cain.html
Lokesh Kumar
K7 Threat Control Lab
If you wish to subscribe to our blog, please add the URL provided below to your blog reader:
https://labs.k7computing.com/feed/